ActiveX Security Model
Abstract
Modern browsers act as a thin client by executing untrusted or portable code called Mobile
Code. For example, windows media player too could be used to run a song file in the browser. However, it is a trusted code to be executed in browsers. Moreover, it becomes malicious when hackers run it without the consent of end user. It typically includes ActiveX, worms, applets, virus, scripts, and rogue code to intentionally modify the default behavior of a system or coerce the end user to run the vicious code. Throughout this article, one of the essential components of mobile code referred as ActiveX control internals will be demystifying in deep modes regarding security perspective.
Essentials
ActiveX is not a programming language. Instead, it is a group of Microsoft software development tools that let the various windows programs to work across networks. Thus, despite familiar the internals of ActiveX technology, the researcher must have the prowess to develop ActiveX control using VB, NET, and VC++ technology. Moreover, knowledge about COM and COM+ will add an extra advantage.

11 courses, 8+ hours of training
Introduction
Software engineering term modular programming enables to compose a particular routine or function that to be used multiple times, spare the hassles of writing large shared program libraries. In the routine, the shared format of input and output data allows interoperability between shared code where other programmers can re-use or call into this interface. But sometimes, reverse engineers can backdoor into such interface or utilize the shared libraries in a way not envisioned by the coder. Before delving into ActiveX mobile code risk or security, this papers briefly review ActiveX technology to streamline the understanding of various risk associated with it.
Mobile Code
Mobile code
is expressed as any code that walks through a network and executes either on a browser or in an e-mail message. The offense can take the form of malicious mobile code wandering along diverse networks eyeing for a vulnerable source for exploitation. An assailant may even use an automated program to find vulnerable hosts and then manually attack the victims. There are three generally recognized variants of malicious mobile code: viruses, worms, and Trojans. The mobile code first, seeks the vulnerable victim, then exploit it in its next phase, later infect it to fulfills its goal, and finally viral that process, to make more zombies. Mobile code is sent to a computer embedded within the body of HTML code along with JavaScript and VBScript also included. Active X controls, however, typically reside on another server somewhere on the Internet.
Active-X Fundamental
ActiveX technology is somewhat identical to Component Object Model object that enables inter-process communications through various parts of the OS and its applications. ActiveX objects allow a program to self-register, add registry/file system entries, and automatically run. ActiveX control components are downloaded to user's browser/operating system and integrate with a web application. ActiveX is often used when a rich set of functionality is required, such as multimedia, patch installation, and much more. The following steps describe how a control is installed on a user's machine:
- First, client explores a web application that contains an ActiveX control.
- The website refers to its class CLSID (class identifier) and URL and prompts the user to download the particular control.
- If the user agrees to download and install it, then installation process initialized.
- After installation, the ActiveX control can be invoked without prompting the user in the future.
Each ActiveX control has a 128-bit value called CLSID which uniquely identify the ActiveX control. The CLSID typically used a special algorithm to ensure uniqueness. Malicious mobile coders might write control with the same CLSID as a popular control to intercept calls intended for original ActiveX control. Right clicking could find ActiveX control code in the browser view
source property. Consider the following HTML code as;
<HTML>
<BODY>
<object
classid="clsid:6BF52A52-394A-11D3-B153-00C04F79FAA6">
</object>
</BODY>
</HTML>
There are other ways of loading ActiveX control besides using <OBJECT> too. The preceding code is a draft to load media player in the browser (IE). IE doesn't have built-in functionality to load Media Player.
Suppose what happen if ActiveX control is not installed or the Browser is unable to find that particular ActiveX control CLSID. IE reaction would as following when it looks for the program with the code for CLSID 6BF52A52-394A-11D3-B153-00C04F79FAA6 and unable to found it.
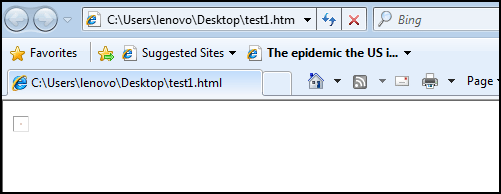
Figure 2: When ActiveX is not installed on the computer
An ActiveX control has also set of essential parameters to change its behavior. ActiveX objects contain a number of methods and properties. The following section provides a brief description of ActiveX essentials:
- Method: A method is a function call that may or may not be implemented. It contains parameters, like a function call.
- Interface: An interface is usually a grouping of functions that expose related functionality. Here, the definition of the methods and properties available
- Object: An object has methods, properties, and interfaces that can be invoked
- Property: Properties are also applied as function calls along with Get/Set convention.
Consider the following code in which PARAM, Properties, Methods, and Events parameter are being used along with scripting code as.
<object
id=Editor1
classid="clsid:0C3C509F-111A-4E6C-B270-1D64BCFD26F9" height=1 width=1>
<param
name="RTFEditorOverrideKey"
value="SOFTWAREMicrosoftWindowsCurrentVersionInternet SettingsCacheSpecial PathsCookies">
<param
name="RTFEditorOverrideValue" value="Directory">
</object>
<input
id=Btn1 value="Edit" type=button onclick="myFun()">
<input
id=txt value="" type=text>
<script>
function myFun()
{
Editor1.RTFEditor = txt.value;
Editor1.InvokeRTFEditor(false);
}
</script>
Installing Active-X Control
ActiveX control final file extension could be both *.OCX or *.DLL as it depends on the platform where it is compiled. Before installing an ActiveX, it is important to identify which control your application ships. Here are the steps as;
- Copy the *.OCX file into the system directory.
- Open Command prompt with Admin right.
-
Then run Regsvr32.exe to register the *.OCX file as.
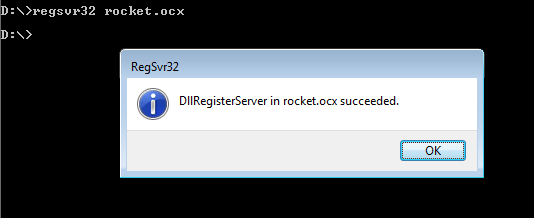
Figure 3: ActiveX registration
- You can confirm about the registration of control from registry by viewing the path of rocket.ocx from HKEY_CLASSES_ROOTCLSID {0C3C509F-111A-4E6C-B270-1D64BCFD26F9}.
You can also view the classes, method, the interface implemented by particular ActiveX control resorting to AXDetails.Exe tool. The following figure displays the contents of preceding install ActiveX control as;
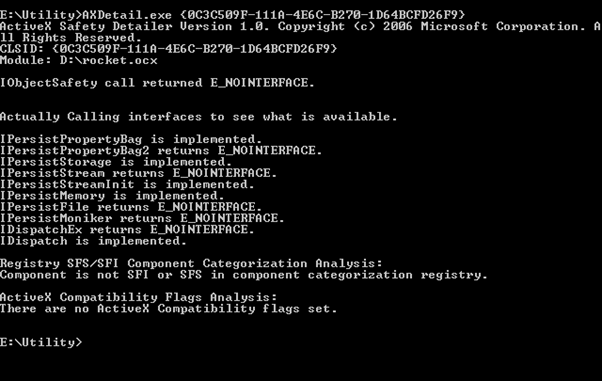
Figure 3: Listing ActiveX control contents
Active-X Security Model
The Internet allows for many different types of HTML code-based attacks that can be malevolent when it breaks browser default security zones to perform the unanticipated act. It often includes script languages with more functionality like JavaScript and VBScript can easily access local resources without a problem and complex active content such as ActiveX controls, Java applets, and media files. ActiveX controls can be almost any type of hostile program, including Trojans and viruses.
ActiveX is easily embedded in HTML using the <OBJECT> tag, and controls can be loaded from remote sites or the local system.
ActiveX controls offer many purposes, from methods to download a program to sanctioning web applications to access information on a local operating system. They are often implemented in C++ but can be implemented in other languages as well like VB or.NET. There are four integral components to the security model of ActiveX controls as
-
InstallationIt takes place when the ActiveX control copied to the computer and registry entries are duly created. Attackers could remotely install his malicious control from their server using codebase attribute of the <OBJECT> tag. IE encounters a digital signature security check before installing a control and never check again once it is installed. That's the hack. Attackers could perform repurpose attack resorting to this vulnerability.
-
InstantiationThe browser loads the control program files and runs the associated code when a control is instantiated via <OBJECT> tag. This phase involves using the registry entries to locate it, copy it into memory, and call routines in the control.
-
InitializationThe next phase is to initialize the control once it is instantiated. Initialization refers to an initial setting, properties of controls like Height, Width, Folder, and Data Source, etc… Initialization happens through IPersist* interface.
-
ScriptingTo invoke methods, handling events, getting and setting property values, it is mandatory to manipulate the control using untrusted scripts, but IE does not provide support for a script running. Instead, a separate scripting engine for which is delegated by IE. Scripting is a switch that enabled or disabled all scripting in HTML in IE. Once the browser directs the script engine about the control, it talks directly to the control and malicious scripts too, from the web page can directly call methods, properties, parameters.
When the client explores a particular website, ActiveX controls are installed on the machine automatically or manually, in case, setting of ActiveX disabled by default in the browser. Microsoft's Internet Explorer has for many years been the most widely used web browser. In particular, other browsers do not natively support ActiveX controls. However, ActiveX control won't install or run automatically, as they are disabled by default in IE too as following.
When a website request to install an ActiveX control, the browser reflects a security warning and asks the user for his consent to process further. Then, this is totally up to the user whether he trusts the website is issuing the control and allow it to be installed accordingly.
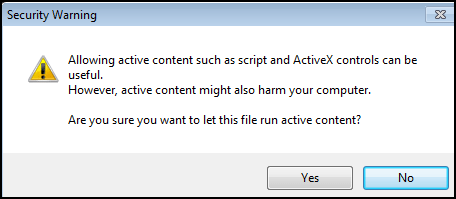
Figure 5: Security warning during loading an ActiveX
Conclusion
ActiveX technology offers plenty of benefits for web programmers as it can add, delete, modify, or update information outside the user's web browser and straight into the operating system.

11 courses, 8+ hours of training
We have examined a variety of possibility in which defects in a web application in the context of using ActiveX technology may leave its users exposed to malicious attack. Initially, this article explored essential details about the mobile code and its various components, in fact, ActiveX is one of them. Then, detail discussion about the ActiveX technology including installation and registration through Regsvr32.exe utility and listing the interface, methods using Axdetails.exe utility. Before delving into ActiveX security model, it is mandatory to duly walk through or understand each internal aspects of this technology, so that vulnerability could be pinpoint and exploitation could be subverted. Finally, elaborate the loading phases of an ActiveX control into memory.
References
- /active-x-exploitation/
- http://surfthenetsafely.com/activex/
- www.sans.org/reading-room/whitepapers/malicious/plain-english-risks-java-applets-microsoft-activex-controls-134
- http://searchenterprisedesktop.techtarget.com/definition/ActiveX-control
- http://www.howtogeek.com/162282/what-activex-controls-are-and-why-theyre-dangerous/






