Android app security: Over 12,000 popular Android apps contain undocumented backdoors
Many Android apps contain hidden secrets
When many people think about malware and other malicious or suspicious software, they focus on computers. It is common best practice to have an antivirus program installed and regularly running on these machines.
Smartphones are rapidly becoming the most common and popular device for computation and Internet access. An “always connected” culture means that many people are constantly checking their devices and have entrusted them with access to their online accounts and sensitive data via installed applications.

11 courses, 8+ hours of training
The growing popularity of smartphones and other mobile devices has made them a focus of cybercriminals as well. About 24,000 malicious mobile apps are blocked every day. However, a recent study of popular Android apps revealed that many of the most-used apps have hidden secrets.
The Android app security study focused on two different types of backdoors:
- Authentication bypasses: Authentication bypass backdoors are designed to allow someone to gain access to the app while bypassing the app’s access control mechanism. The report further broke these authentication bypasses down into secret access keys, master passwords and secret privileged commands.
- Hidden blocklists: Blocklists are designed to filter user input to deny undesirable input. If the contents of these blocklists are not made clear to the user (i.e., “invalid characters” rather than denying !@#), they are considered to be hidden.
Study results
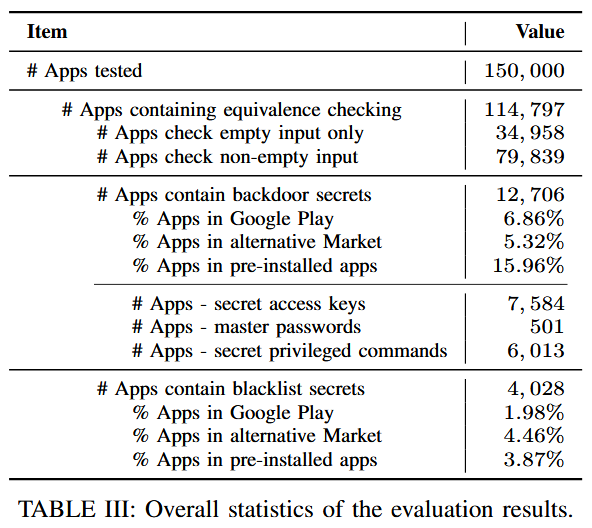
The study of Android app security contained a dataset of 150,000 popular Android apps. These are broken down as follows:
- The top 100,000 most-downloaded apps from the Google Play Store
- The top 20,000 most-downloaded apps from alternative app stores
- 30,000 pre-installed apps extracted from the firmware of Samsung devices
The image above shows the findings of the research. Over 11% of the applications studied contained either authentication bypasses or hidden blocklists. A few other important takeaways include:
- Preinstalled apps are the most likely to contain hidden secrets. These are also the apps that are hardest to remove since they are often not deletable without rooting a device
- A significant percentage of the apps containing authentication bypasses had multiple different types (secret access keys, master passwords, secret privileged commands)
- Google Play apps are more likely to have authentication bypasses, but apps from alternative app stores are more likely to have hidden blocklists
Not all hidden content is malicious
The result of this study is the revelation that many Android applications contain some form of hidden functionality. In many cases, this hidden functionality is malicious or at least suspicious and dangerous.
One example of a hidden authentication bypass found during the study was for a file encryption app. Knowledge of a hardcoded password would allow access to all files encrypted by the app. While this backdoor might have been included in the app for a legitimate purpose, such as providing access to data in response to a warranted request by law enforcement, it is also easily abused. The app developer or anyone who discovered the hidden password could use it to gain unauthorized access to all of a user’s sensitive data.
However, not all hidden secrets within an Android app are necessarily malicious. For example, a large percentage of the hidden blocklists discovered in the study are likely to be benign. Their purpose could be to ensure that user input does not contain any characters that could cause the application problems (such as comment characters that would be used in an SQL query) or to filter out hateful messages from a username or other publicly-posted data. While the study revealed that a significant percentage of popular Android applications contained hidden functionality, not all of this functionality is necessarily malicious.
Implications of mobile device security for business
As organizations increasingly support remote work and bring-your-own-device (BYOD) policies, an understanding of the potential threats posed by mobile devices is essential. As demonstrated by this research, popular and widely-used mobile apps can contain undocumented functionality that is potentially harmful to the user. For example, if an organization is using the file encryption application discovered to contain a hardcoded backdoor, then sensitive company data may be at risk of theft or exposure.
This study also underscores the importance of providing employee training regarding the potential threats of mobile applications. Mobile devices are a growing target of malware and other cybercrime since they are in near-constant use and are widely trusted. Employee training is necessary to ensure that the amount of sensitive and personal data that could be exposed to backdoored or otherwise suspicious applications is minimized.
The bottom line on app security
The recent study explored the security of a small set of popular Android applications and found that a significant percentage of them contained some form of hidden content. However, this likely only scratches the surface as it was limited to:
- The Android OS (iOS also has a large market share and is a common target of attacks)
- Samsung’s pre-installed applications (preinstalled apps made up the majority of apps containing hidden secrets)
- Some of the most commonly downloaded apps (less popular apps are more likely to be malicious)
Mobile devices are like any other devices when it comes to security. Using an antivirus, installing apps only from reputable sources and limiting online data sharing are essential to security.
Sources
- Thousands of Android apps contain undocumented backdoors, study finds, Naked Security
- Qingchuan Zhao, Chaoshun Zuo, Brendan Dolan-Gavitt, Giancarlo Pellegrino, Zhiqiang Lin, "Automatic Uncovering of Hidden Behaviors From Input Validation in Mobile Apps"
- 15 (CRAZY) Malware and Virus Statistics, Trends & Facts 2020, SafetyDetectives