Fundamentals of blockchain security
Introduction
The goal of blockchain is to create a fully decentralized, trustless digital ledger. This is an ambitious goal since most ledger systems in use today, such as those used to track bank balances, rely upon a centralized authority to maintain the consistency, correctness and integrity of the ledger.
Blockchain is designed to replace this trust in a centralized authority with trust in cryptographic algorithms and protocols. The blockchain is designed so that all of its “guarantees” are reliant upon the correctness and security of protocols and cryptographic algorithms, rather than any of the individuals operating the network.
Structure of the blockchain
The blockchain gets its name from its two main structural components. A blockchain is a series of “blocks” that are “chained” together. The combination of these two features creates a digital ledger with built-in integrity protections.
The blocks
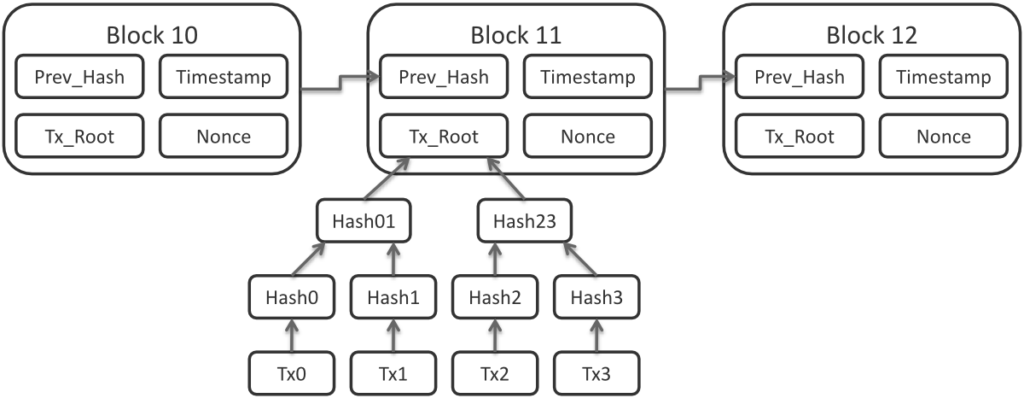
The blocks of a blockchain are what provides the data storage. A block is composed of a block header containing important metadata and a body containing the actual transactions stored in the block.
Source: Wikimedia Commons
Block 11 in the image above shows the structure of a notional block. The block header contains a previous block hash (more on this in a minute), a timestamp, a transaction root and a nonce (important for the Proof of Work consensus algorithm).
The block body is structured as a Merkle tree, which provides a number of different benefits. One of these is the fact that, due to the properties of hash functions, the root value of the tree can be used to summarize the entire tree. Anyone with a list of the transactions contained in the block can regenerate the tree, but it is computationally infeasible to find a different version of the transaction tree with the same root value. This means that a block can contain an infinite number of transactions but maintain a fixed-size block header; however, most blockchains have a maximum limit on block size for protection against Denial-of-Service (DoS) attacks.
The “chains”
The previous block hash value in a block header implements the blockchain’s “chains.” Each block header contains the hash of the previous block in the blockchain.
With a strong hash function, it is infeasible to find another version of a block that has the same hash value as is stored in the header of the next block. This is vital to the integrity protections of the blockchain. If an attacker wants to create a fake version of a given block, they must create a fake version of every block that follows it as well.
Blockchains are also governed by the longest chain rule. This says that, in the event that two conflicting versions of the blockchain exist, whichever one is “longer” wins. This means that an attacker not only needs to create a new, fake version of every block after the one that they want to change, but they also need to do so faster than the rest of the network creates the legitimate version. This makes creating a fake version of the blockchain exponentially more difficult than faking a single block.
Basic blockchain cryptography
The design of the blockchain and the protocols that define how it works are new. However, the cryptography that provides blockchain’s security guarantees existed long before Bitcoin. Under the hood, blockchain technology is very dependent on public-key cryptography and hash functions.
Public-key cryptography
Public-key or asymmetric cryptography is designed to use a pair of related keys. The public key is designed to encrypt messages and to verify digital signatures, while the private key performs message decryption and signature generation.
The distributed and decentralized nature of the blockchain makes digital signature technology essential to the integrity of the digital ledger. Blockchain is implemented so that each node in the network stores and updates their own copy of the ledger.
Digital signatures are what keep these nodes honest. Every transaction and block in the blockchain is signed by its creator. This ensures that a malicious node cannot create a fake transaction or block and attribute it to someone else unless they can generate a valid digital signature for that user.
In theory, this is impossible since current public key cryptography algorithms are secure until quantum computers and Shor’s algorithm are a feasible attack vector. In practice, use of weak private keys for blockchain accounts have enabled cryptocurrency thefts on blockchains.
Hash functions
Hash functions are used for a variety of purposes in blockchain systems. Their benefit comes from the fact that they are guaranteed to be both collision resistant and one-way functions.
Collision resistance means that it should be infeasible to find two inputs to a hash function that produce the same output. While the Pigeonhole Principle guarantees that it is possible to find two such inputs (in fact, an infinite number of inputs produce the same output), a hash function should be designed so that the only way to guarantee that you find a match is to search the same number of inputs as there are possible outputs (which is a lot).
In order to be a cryptographically secure one-way function, hash functions must have a number of different properties. They not only need to be one-way functions but also must have a large state space (number of possible outputs) and be non-local (similar inputs produce dissimilar outputs).
As collision-resistant, one-way functions, hash functions are ideally suited to ensuring the integrity of data within a distributed digital ledger. As discussed above, they’re used to both “lock in” the values of previous blocks in the chain and to securely and concisely summarize a block’s transaction list within a single value in the block header.
Bottom-layer blockchain security
The blockchain is a multi-layer system. At the bottom layer, every blockchain protocol boils down to a collection of data structures and cryptographic algorithms. These structures and algorithms are the building blocks that enable the blockchain to do its job and provide many of its security guarantees.
At this level, the security of the blockchain is mainly dependent on the security of the algorithms and how they are used. To date, every blockchain attack targeting this level has taken advantage of algorithm misuse or implementation errors rather than a vulnerability in the protocols themselves.
Sources
‘Blockchain Bandit’: How a Hacker Has Been Stealing Millions Worth of ETH by Guessing Weak Private Keys, Cointelegraph
Mathematics | The Pigeonhole Principle, GeeksforGeeks