DEATHNOTE: 1 VulnHub CTF walkthrough
In this article, we will solve a capture the flag challenge ported on the Vulnhub platform by an author named HWKDS. As per the description, this is a beginner-friendly challenge as the difficulty level is given as easy. As a hint, it is mentioned that this is a straightforward box, and we need to follow the hints while solving this CTF. Prerequisites would be knowledge of Linux commands and the ability to run some basic pentesting tools.
The torrent downloadable URL is also available for this VM; it has been added in the reference section of this article.
For those who are not aware of the site, VulnHub is a well-known website for security researchers which aims to provide users with a way to learn and practice their hacking skills through a series of challenges in a safe and legal environment. Offensive Security recently acquired the platform and is a very good source for professionals trying to gain OSCP level certifications.
Please note: I have used Oracle Virtual Box to run the downloaded machine for all of these machines. I am using Kali Linux as an attacker machine for solving this CTF. The techniques used are solely for educational purposes, and I am not responsible if the listed techniques are used against any other targets.

What should you learn next?
The steps
- Getting the IP address with the Netdiscover utility
- Identify open ports through Nmap
- Enumerating HTTP service
- Running WPScanner and Dirb
- Running brute force through Hydra
- Escalating privileges to get the root access
The walkthrough
Step 1
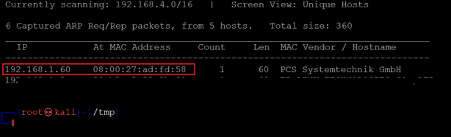
The first step is to run the Netdiscover command to identify the target machine's IP address. In the screenshot given below, we can see that we have run Netdiscover, which gives us the list of all the available IP addresses. It can be seen in the following screenshot.
Command used: << netdiscover >>
In the highlighted area of the above screenshot, we can see an IP address, our target machine IP address. The target machine IP address is 192.168.1.60, and I will be using 192.168.1.29 as the attacker's IP address.
Note: the target machine IP address may be different in your case, as the network DHCP is assigning it.
Step 2
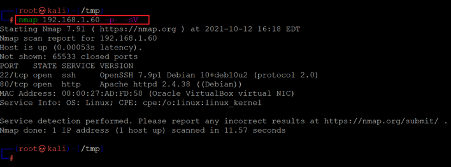
The second step is to run a port scan to identify the open ports and services on the target machine. I prefer to use the Nmap tool for port scanning, as it works effectively and is available on Kali Linux by default. In the highlighted area of the following screenshot, we can see the Nmap command we used to scan the ports on our target machine. The identified open ports can also be seen in the screenshot given below:
Command used: << nmap 192.168.1.60 -sV -p- >>
In the Nmap Command, we used '-sV' option for version enumeration and '-p-'for full port scan, which means we are telling Nmap to conduct the scan in all 65535 ports. By default, Nmap conducts the scan only known 1024 ports. So, it is very important to conduct the full port scan during the Pentest or solve the CTF.
The output of the Nmap shows that two open ports have been identified Open in the full port scan. Port 80 is being used for the HTTP service, and port 22 is being used for the SSH service. So, in the next step, we will start solving the CTF with Port 80.
Step 3
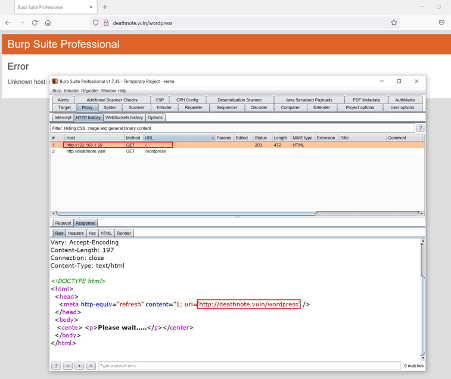
Let us start the CTF by exploring the HTTP port. We opened the target machine IP address on the browser.
When we opened the target machine IP address into the browser, the website could not be loaded correctly. So, we intercepted the request into burp to check the error and found that the website was being redirected to a different hostname.
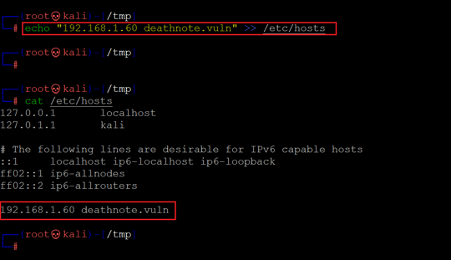
So, we need to add the given host into our, etc/hosts file to run the website into the browser.
Command used: << echo “192.168.1.60 deathnote.vuln” >> /etc/hosts >>
In the above screenshot, we can see that we used the echo command to append the host into the 'etc/hosts' file. The same was verified using the cat command, and the command's output shows that the mentioned host has been added. So, let us open the URL into the browser, which can be seen below.
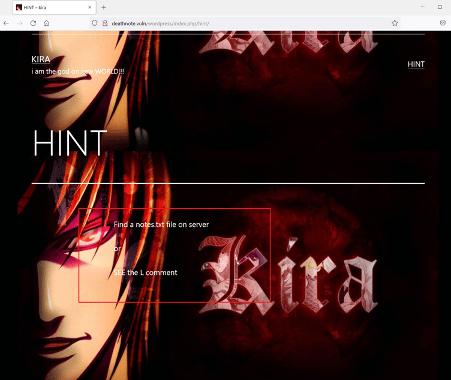
The target application can be seen in the above screenshot. On the home page, there is a 'hint' option available. So, we clicked on the 'hint' and found the below message.
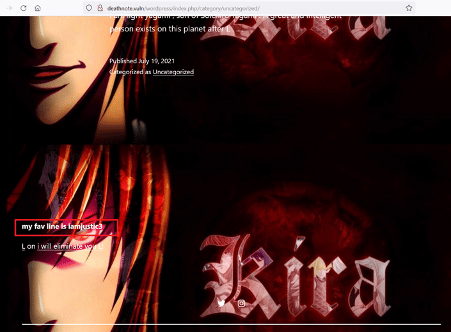
The message states an interesting file, 'notes.txt', available on the target machine. It also refers to checking another comment on the page. The 'l' comment can be seen below.
The comment left by a user names' L' contains some hidden message which is given below for your reference –
my fav line is imjustice3
We do not understand the hint message. This could be a username on the target machine or a password string. So, let us identify other vulnerabilities in the target application which can be explored further. In the next step, we used the WPScan utility for this purpose,
Step 4
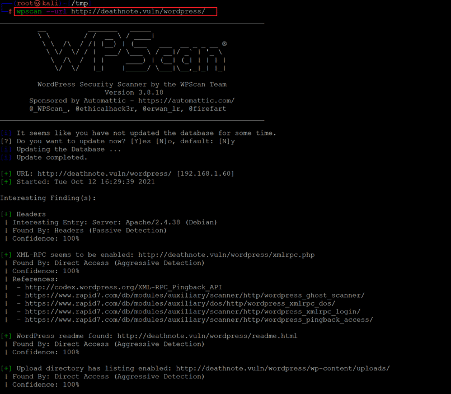
WPScanner is one of the most popular vulnerability scanners to identify vulnerability in WordPress applications, and it is available in Kali Linux by default. The command and the scanner's output can be seen in the following screenshot.
Command used: << wpscan --url http://deathnote.vuln/wordpress/ >>
As we know that WordPress websites can be an easy target as they can easily be left vulnerable. So, we ran the WPScan tool on the target application to identify known vulnerabilities. However, the scan could not provide any CMC-related vulnerabilities. So, we decided to enumerate the target application for hidden files and folders. We used the Dirb tool for this purpose which can be seen below.
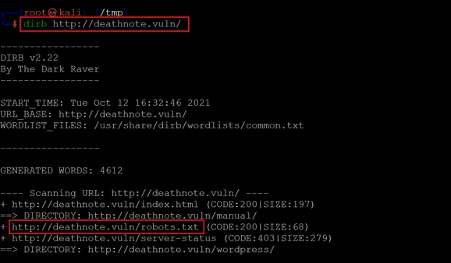
Command used: << dirb http://deathnote.vuln/ >>
In the above screenshot, we can see the 'robots.txt' file on the target machine. The file was also mentioned in the hint message on the target machine. So, let us open the file on the browser to read the contents.
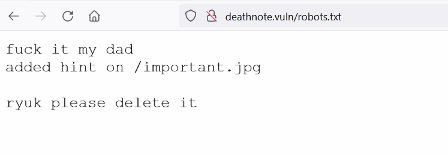
We found another hint in the robots.txt file. The hint mentions an image file that has been mistakenly added to the target application. So, let us open the file 'important.jpg' on the browser.
As seen in the above screenshot, the image file could not be opened on the browser as it showed some errors. We decided to download the file on our attacker machine for further analysis.
Command used:
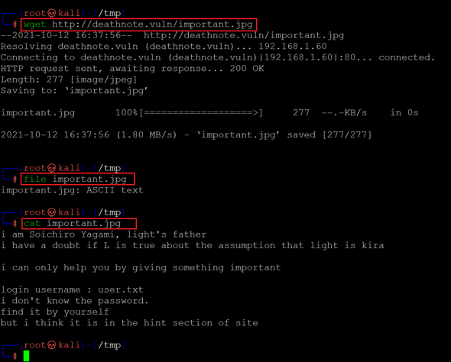
- << wget http://deathnote.vuln/important.jpg >>
- << file important.jpg >>
- << cat important.jpg >>
We used the wget utility to download the file. After that, we used the file command to check the content type. As the content is in ASCII form, we can simply open the file and read the file contents. We used the cat command for this purpose. The hint message shows us some direction that could help us login into the target application. So, we collected useful information from all the hint messages given on the target application to login into the admin panel.
- Password: iamjustic3
- Username: kira
After a few attempts, the username 'Kira worked on the login page, and the password was also easily guessed from the hint messages we had read earlier. We have WordPress admin access, so let us explore the features to find any vulnerable use case.
We tried to write the PHP command execution code in the PHP file, but the changes could not be updated as they showed some errors. We have to identify a different way to upload the command execution shell.
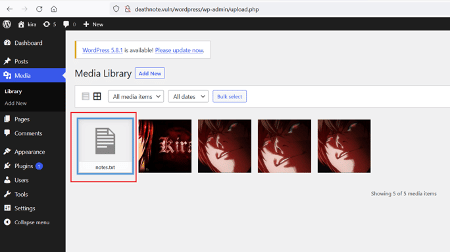
While exploring the admin dashboard, we identified a 'notes.txt' file uploaded in the media library. Let us open the file on the browser to check the contents.
The notes.txt file seems to be some password wordlist. Let us use this wordlist to brute force into the target machine.
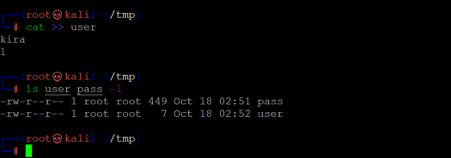
Command used: << ls user pass -l >>
We created two files on our attacker machine. We added all the passwords in the 'pass' file. We have enumerated two usernames on the target machine, 'l' and 'kira.' We have added these in the 'user' file. In the next step, we will be running Hydra for brute force.
Step 5
Hydra is one of the best tools available in Kali Linux to run brute force on different protocols and ports. Here we will be running the brute force on the SSH port that can be seen in the following screenshot.
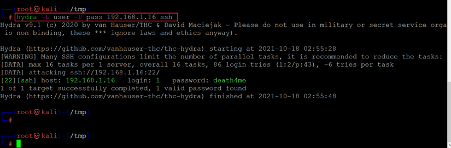
Command used: << hydra -L user -P pass 192.168.1.16 ssh >>
The hydra scan took some time to brute force both the usernames against the provided word list. After some time, the tool identified the correct password for one user. The identified username and password are given below for reference:
Username- l
Password- death4me
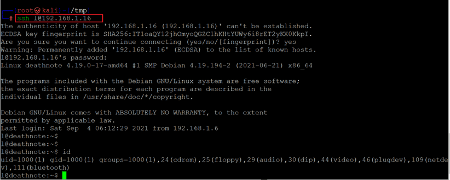
Let us try the details to login into the target machine through SSH.
Command used: << ssh l@192.168.1.16 >>
Username: l
Password: death4me
The login was successful as the credentials were correct for the SSH login. We are now logged into the target machine as user 'l.' We ran the id command output shows that we are not the root user. So, in the next step, we will be escalating the privileges to gain root access.
Step 6
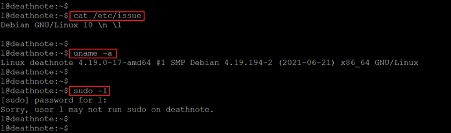
After logging into the target machine, we started information gathering about the installed operating system and kernels, which can be seen below.
Command used:
- << cat /etc/issue >>
- << uname -a >>
- << sudo -l >>
After getting the version information of the installed operating system and kernel, we searched the web for an available exploit, but none could be found. So, we used the 'sudo –l' command to check the sudo permissions for the current user. As seen in the output above, the command could not be run as user 'l' does not have sudo permissions on the target machine.
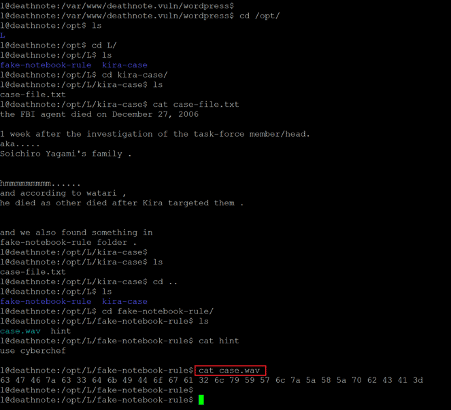
So, we continued exploring the target machine by checking various files and folders for some hint or loophole in the system. Soon we found some useful information in one of the directories.
Command used: << cat case.wav >>
In the '/opt/' folder, we found a file named 'case-file.txt' that mentions another folder with some useful information. We opened the 'case.wav' file in the folder and found the below alphanumeric string.
63 47 46 7a 63 33 64 6b 49 44 6f 67 61 32 6c 79 59 57 6c 7a 5a 58 5a 70 62 43 41 3d
This seems to be encrypted. Let us try to decrypt the string by using an online decryption tool.
In the above screenshot, we can see that we used an online website, cyber chief, to decrypt the hex string using base64 encryption. This worked in our case, and the message is successfully decrypted. We got the below password —
Password: kiraisevil
As we already know from the hint message, there is a username named 'kira'. So, let us try to switch the current user to kira and use the above password.
Command used:
- << su kira >>
- << sudo -l >>
- << sudo su >>
We used the su command to switch to 'kira' and provided the identified password. The password was correct, and we are logged in as user 'kira.' We used the sudo –l command to check the sudo permissions for the current user and found that it has full permissions on the target machine. This means that we do not need a password to root. So, we used to sudo su command to switch the current user as root.
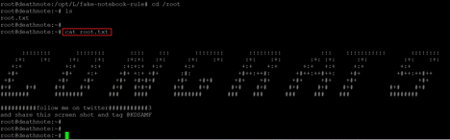
Command used: << cat root.txt >>

What should you learn next?
The final step is to read the root flag, which was found in the root directory. The root flag can be seen in the above screenshot. This completes the challenge. Keep practicing by solving new challenges, and stay tuned to this section for more CTF solutions.
Sources: