Hackable ||| VulnHub CTF Walkthrough Part 1
You can find a link to take on this medium-level capture the flag (CTF) below:
You can download the machine and run it on VirtualBox. The torrent downloadable URL is also available for this VM and has been added in the reference section of this article.
Please note: for all these machines, I have used Oracle VirtualBox to run the downloaded machine. I am using Kali Linux as an attacker machine for solving this CTF. The techniques used are solely for educational purposes, and I am not responsible if the listed techniques are used against any other targets.
The steps
- Getting the IP address with the Netdiscover utility
- Identifying open ports with Nmap
- Enumerating HTTP Service with Dirb utility
- Enumerating of the FTP service
- Logging into SSH and reading the first flag
- Getting the root by using the local exploit
So, as we have all the information to start, let's get started with the challenge.
The walkthrough
Step 1
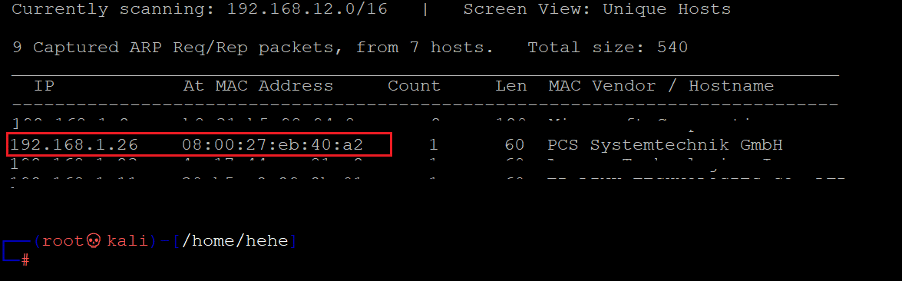
The first step is to run the Netdiscover command to identify the target machine's IP address. In the screenshot given below, we can see the Netdiscover command, which lists all the available IP addresses. [CLICK IMAGES TO ENLARGE]
Command used: << netdisvoer >>
In the above screenshot, we see that we have identified the IP address of all the devices connected to our router. Still, due to security reasons, we have hidden the MAC address of my personal connected devices. The target machine IP address is 192.168.1.26, and I will be using 192.168.1.27 as the attacker's IP address.
Note: the target machine IP address may be different in your case, as the network DHCP is assigning it.
Step 2
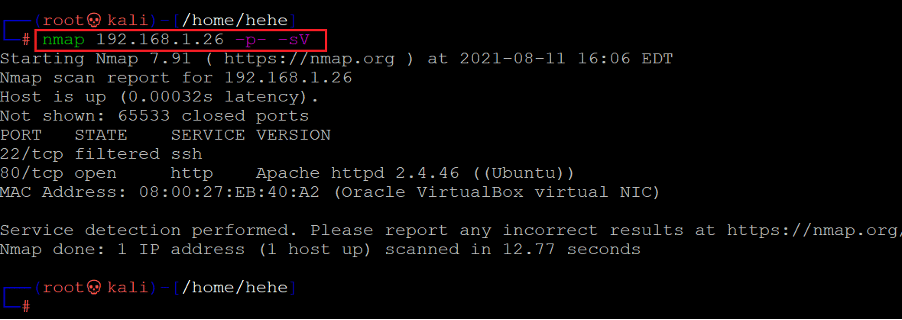
The second step is the starting step of the CTF. In this step, we will run a port scan to identify the open ports and services on the target machine. I will use the Nmap tool for port scanning, as it works effectively and is available on Kali Linux by default. You can use any port scanning method or tool which gives proper results. In the highlighted area of the following screenshot, we can see the Nmap command to scan the ports on our target machine. The identified open ports can also be seen in the screenshot given below.
Command used: << nmap -sV -p- 192.168.1.26 >>
In the output, we can see two ports were identified on the target machine by Nmap. Port 80 is open, which is being used for the HTTP service. Port 22 is shown as filtered and is being used for the SSH service.
In the Nmap command, We used the '-sV' switch for version enumeration. We also used the '-p-' option for the full port scan. It tells Nmap to conduct the scan on all the 65535 ports on the target machine. By default, Nmap conducts the scan only on known 1024 ports. So, it is especially important to conduct a full port scan during the pentest or solve the CTF for maximum results.
Let us start solving the CTF with the HTTP port 80.
Step 3
We opened the target machine IP address on the browser to see the web application. It can be seen in the following screenshot.
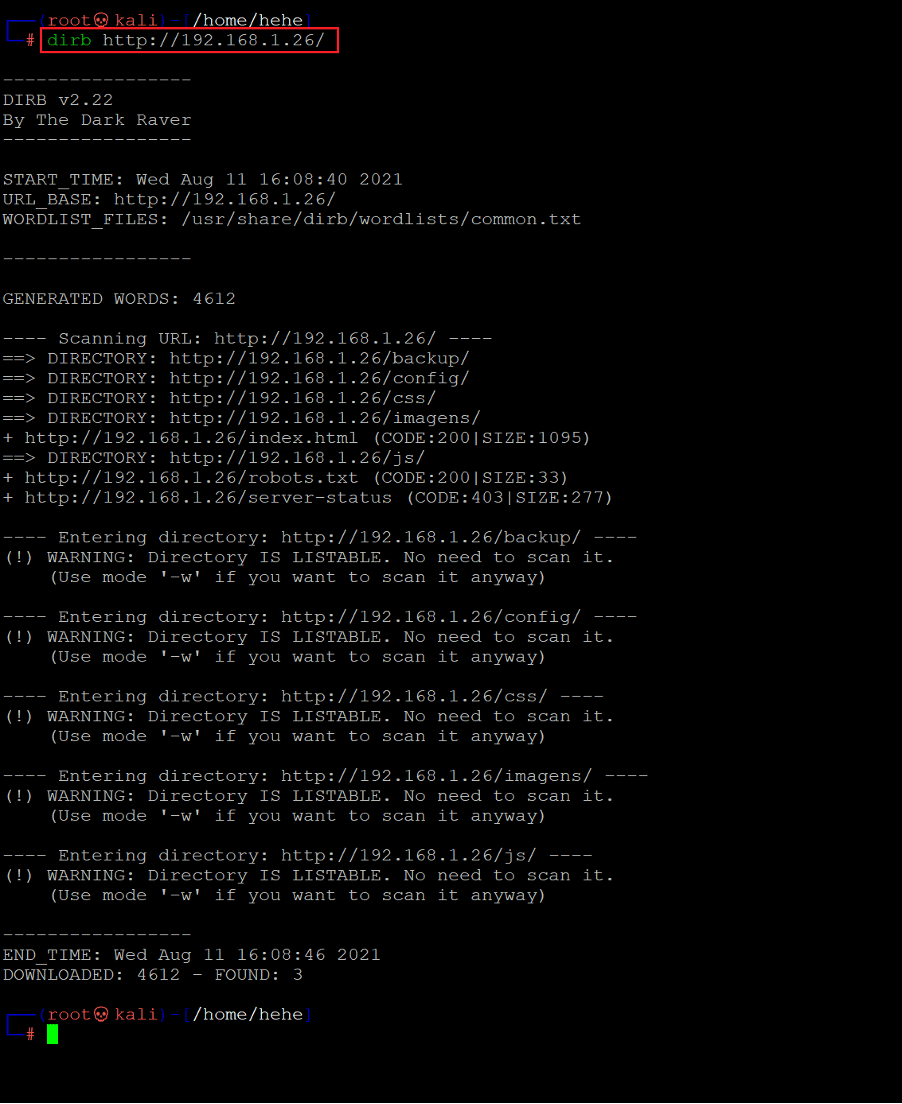
As we can see, there is just a simple image file on the homepage. But as the port is open, there must be some application folder in the 'HTML directory. Let's run brute force to identify any hidden directories or files. We used the Dirb tool for this purpose. It is a very popular and efficient web application brute-forcing tool. The command used and the scan results can be seen highlighted in the below screenshot.
Command used: << dirb http://192.168.1.26 >>
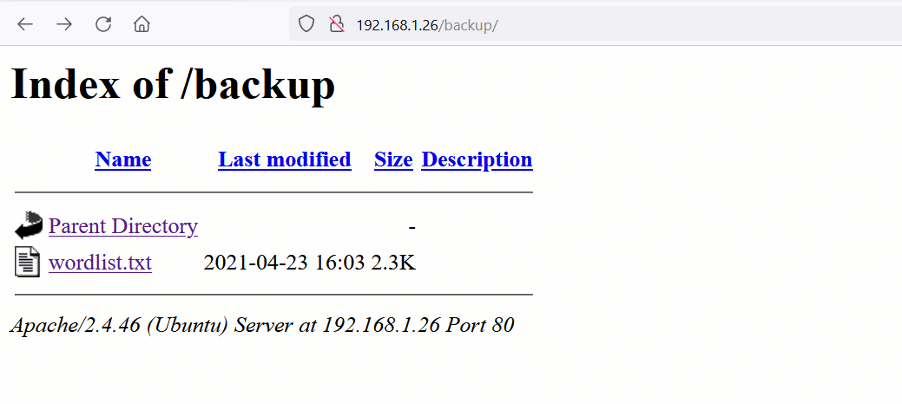
We found a lot of directory paths on the target application, as can be seen from the scan results. We also identified that directory listing is enabled on the target machine, making it easier to access internal content. We will explore and analyze each of these directories one by one. Let us open the backup directory on the browser to check the contents.
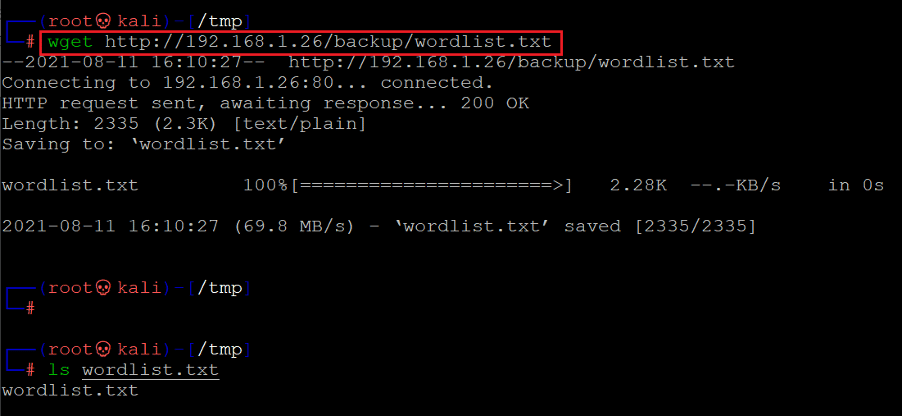
The backup folder had a text file named 'wordlist.txt.' Let's download the file on our attacker machine for further analysis, which can be seen below.
Command used: << wget http://192.168.1.26/backup/wordlist.txt >>
We downloaded the wordlist.txt file on our attacker machine using the 'wget' utility. The wordlist.txt file has a list of strings that can be used for brute force. We saved this file, and let's move to the next to identify the directory, as seen in the following screenshot.
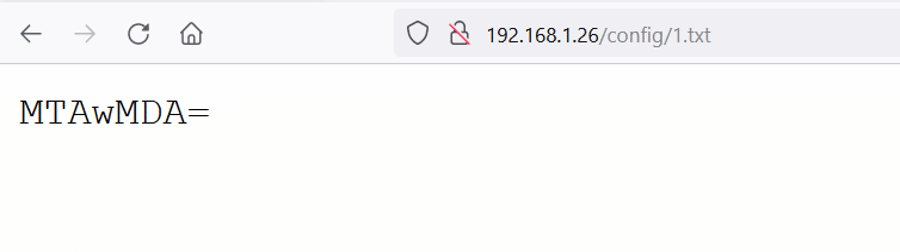
In the config directory, the file named '1.txt' had a string that seemed to be base64 encoded. Let us decode the string to find out the clear text information.
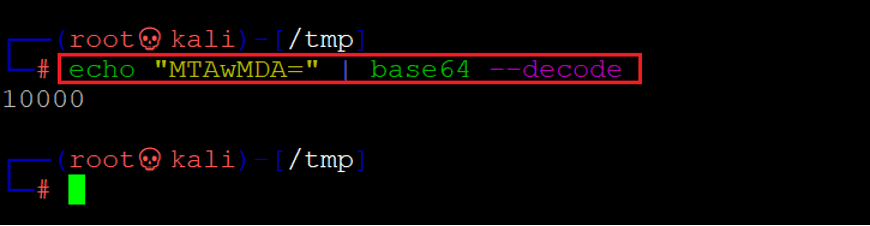
Command used: << echo “MTAwMDA=” | base64 --decode >>
We used the echo command to decode the string into clear text. The clear-text value is 10000. We checked the HTML source of the index.html page, which can be seen below.
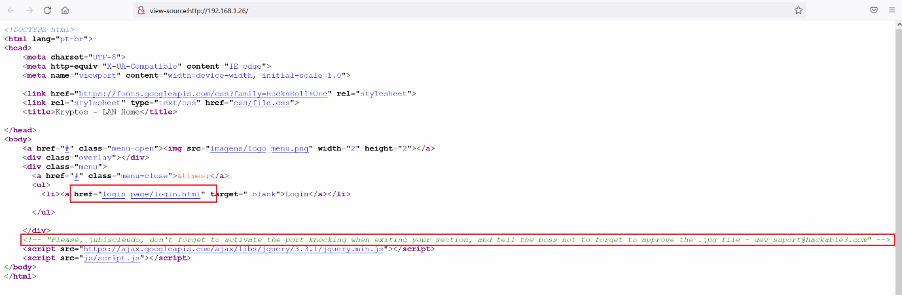
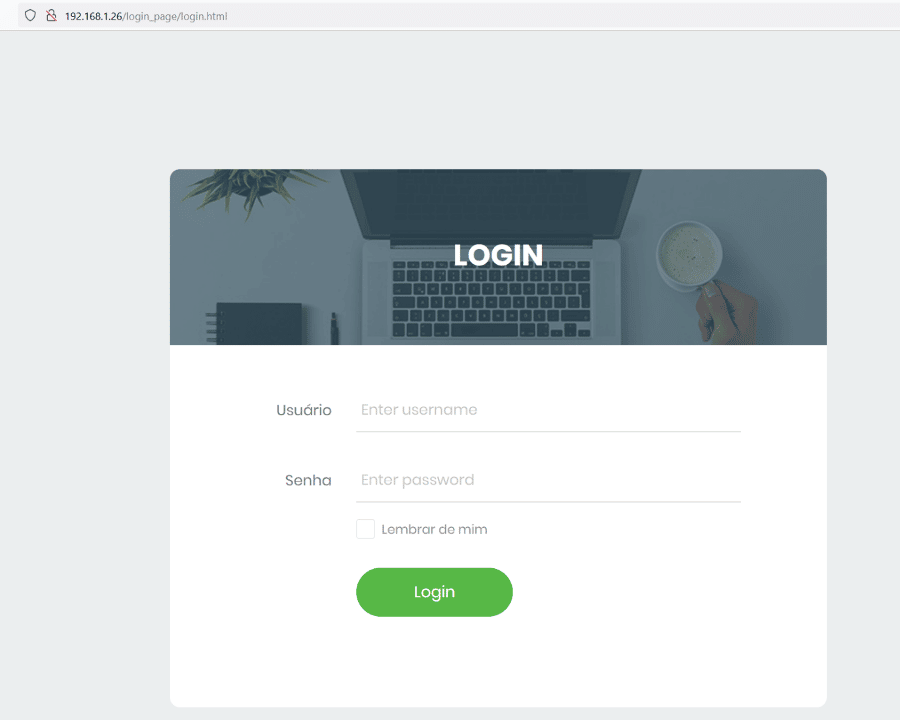
In the HTML source, we found a login page on the target application named 'login.html.' There was a hint mentioned on the website, which can be seen below.
Hint: Please, jubiscleudo, don't forget to activate the port knocking when exiting your section, and tell the boss not to forget to approve the .jpg file - dev_suport@hackable3.com"
We identified a username on the target machine from the above message, which can be used in later steps. We also found out through the message that port knocking is activated on the target machine and mentions a '.jpg' file. Let us try the login page first, which can be seen below.
On the login page, we tried a few random usernames and password combinations, which redirected to a blank page which can be seen below.
As there was nothing on the blank page, we decided to check the HTML content of the page, and it had some interesting information, as can be seen below.
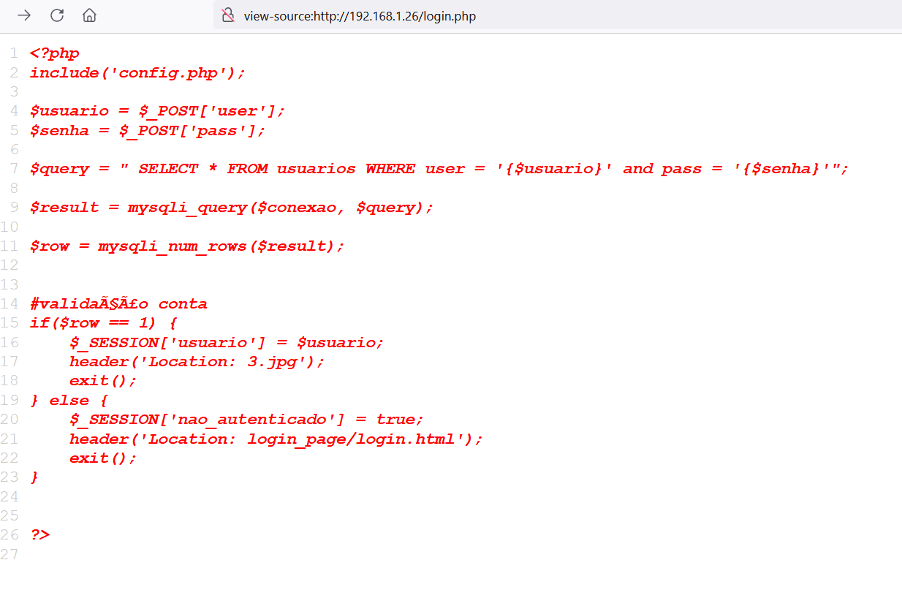
By analyzing the source code, we found that the page is vulnerable to SQL Injection. As it was showing the PHP code in the browser, we did not test SQL injection. There was an interesting image file mentioned in the code. Let's open it into the browser.
The image file can be seen above, but it does not give any further hint. We decided to download the image file to analyze the code.
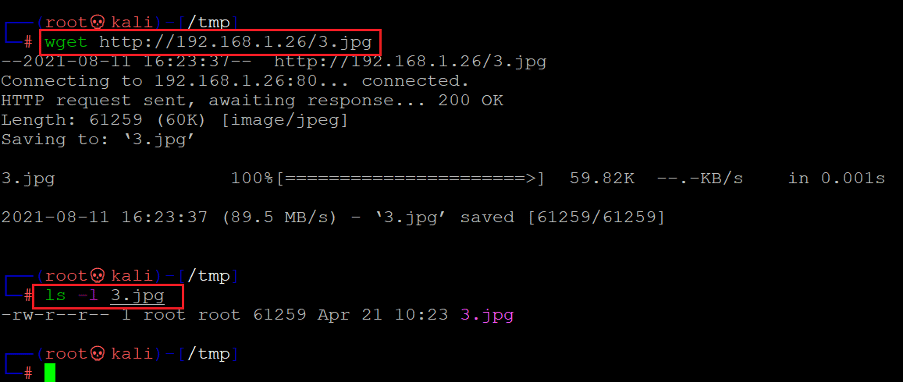
Command used: << wget http://192.168.1.26/3.jpg >>
The above screenshot shows that we have downloaded the image file '3.jpg' on our attacker machine by using the wget utility.
Step 4: Analysing and getting the hidden messages from the Image file
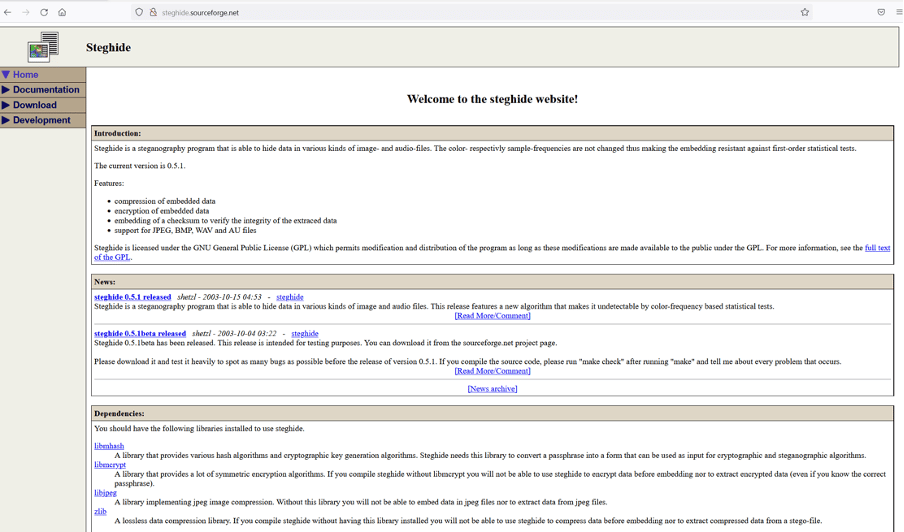
To further analyze the image file's contents, we researched over the internet for some useful utilities and found a tool named steerhide. The information given on the official website can be seen below.
Steghide is a tool that is used to hide data in image and audio files. We can extract the hidden information in the image file with the help of this tool. This is not a default utility in kali Linux, let's first download it on our attacker machine.
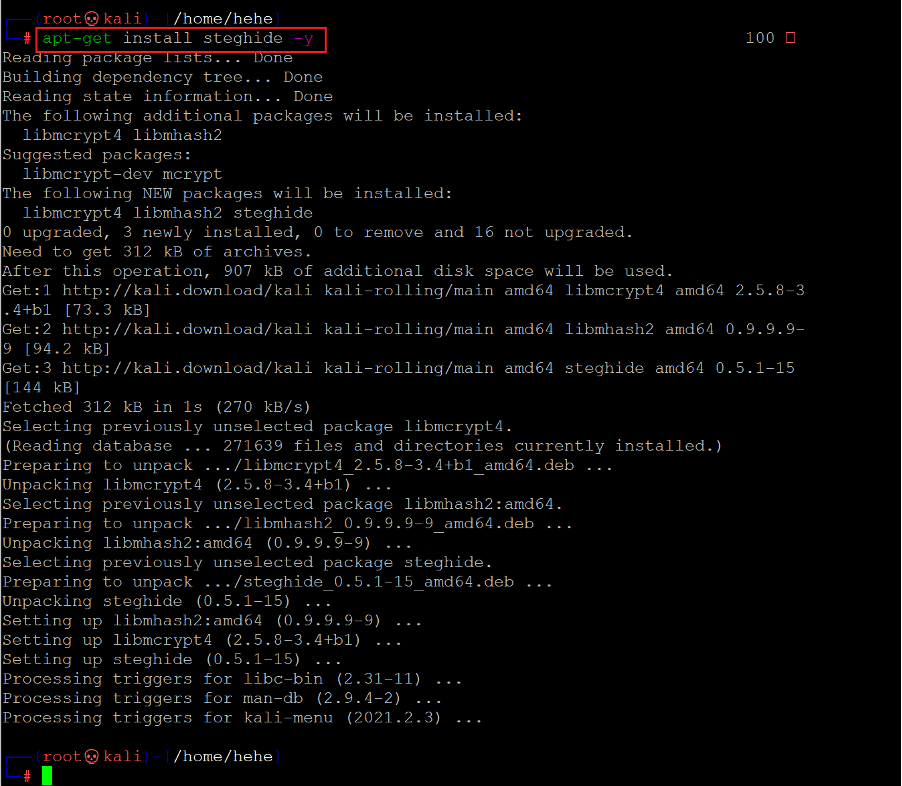
Command used: << apt-get install steghide -y >>
In the above screenshot, we have downloaded the 'steghide' tool with the help apt-get command. We spent some time learning about the tool usage and commands on the official website. Let us now extract the image file data using the steghide command, which can be seen below.
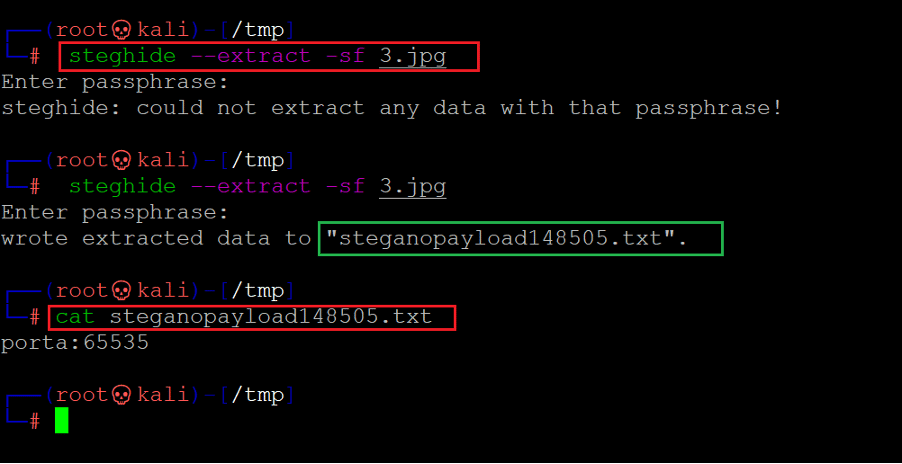
Command used: << steghide --extract -sf 3.jpg >>
At first, it seemed that the data was not extracted since it asked for a passphrase. We did not know any passphrase but provided any default value, and it gave a failed message. We tried again, and this time we left the passphrase value empty and just hit the enter button. The data was extracted successfully, as can be seen in the above screenshot. We used the cat command to open the file, and as a result, we got another number. Now, we know two numbers found through various hints on the target machine.
The numbers are — 65535 and 10000
As of now, we do not know how and where to use them on the target machine. Let's go back to the identified directories on the target application and explore them for further clues.
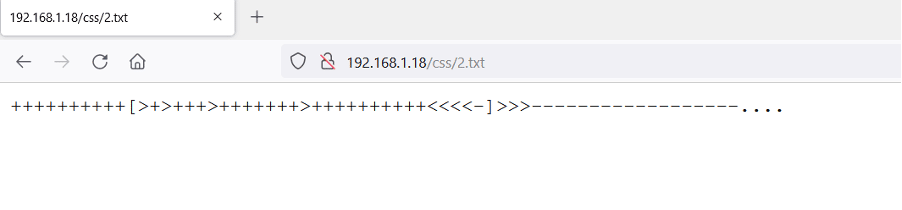
In the 'css/' directory, we found one more text file named '2.txt.' Let's open it into the browser.
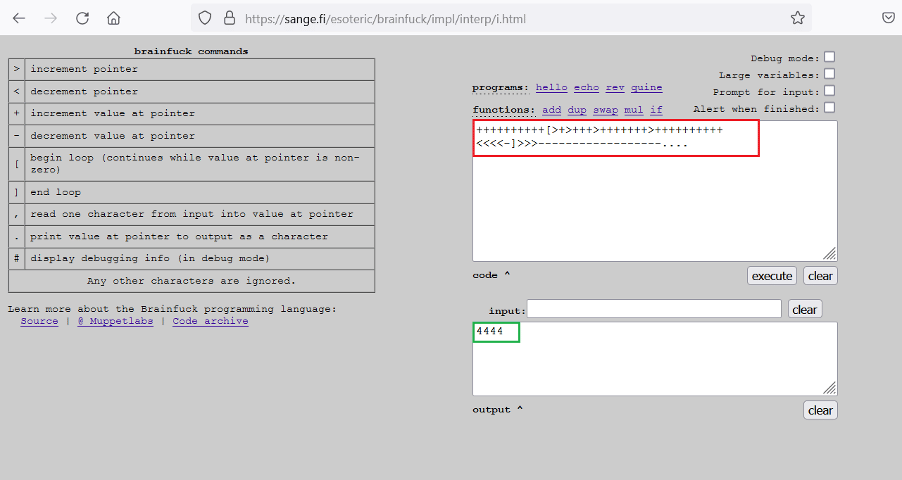
++++++++++[>+>+++>+++++++>++++++++++<<<<-]>>>------------------....
Here we found one more encoded message. This seems to be encoded using brainfuck programming language. We found an online decoder that supports the brainfuck algorithm, which can be seen below.
The string was successfully decoded, and we got one more numeric value. The hints that have been identified so far are given below:
- 65535
- 10000
- 4444
We know from the message given on the target application that there is some use of the port knocking technique. So in the next step, we will be using the port knocking technique.
Step 5: Opening port with port knocking technique
So, let's set up our system for running a port knocking scan on the target machine. Port knocking opens ports on a firewall by generating a connection attempt on a set of prespecified closed ports. Once a correct sequence of connection attempts is received, the firewall rules are dynamically modified to allow the host which sent the connection attempts to connect over a specific port.
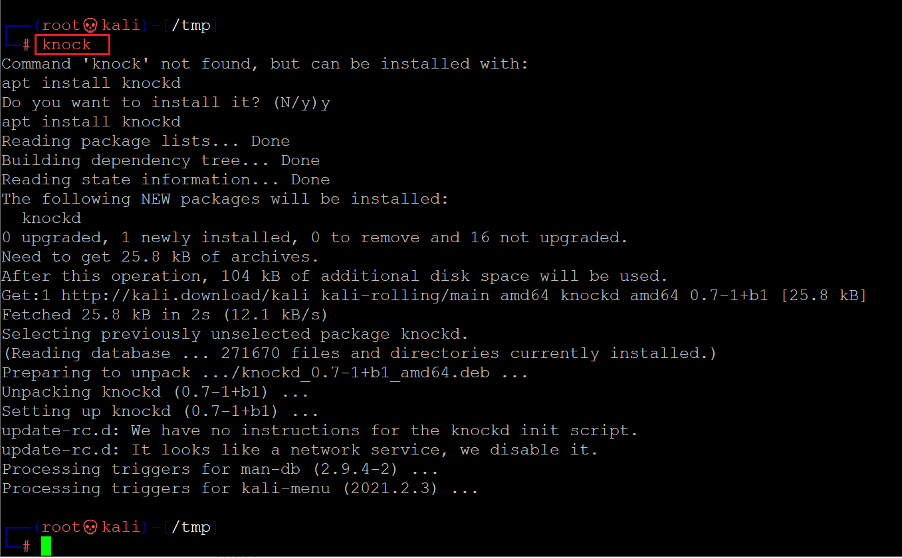
Command used: << knock >>
The Knock utility was not pre-configured in Kali Linux, but when we typed the knock command on the terminal, it automatically gave an option to install it. We typed y for yes, which installed the knock utility on our attacker machine. Kali automatically identified the utility package and installed it as we are using the latest kali Linux version. In the previous versions, it can be installed by using the apt-get install knock command.
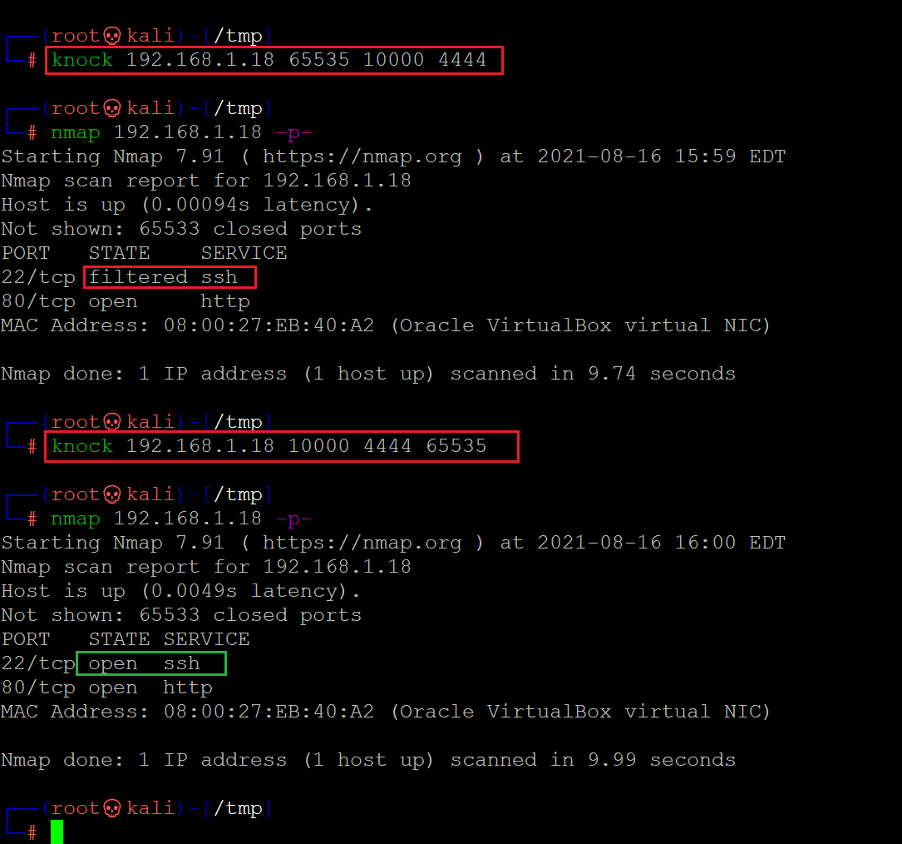
Let us run the tool with the identified numbers as the knock sequence, which can be seen below.
Command used: << knock 192.168.1.18 10000 4444 65535 >>
We ran the knock sequence on the target machine to open the state of the ports. After that, we conducted a port scan, and port number 22 was still shown as filtered. We again ran the port knocking command, but this time we changed the sequence of the numbers. After that, we conducted the Nmap scan to check the open ports, and the SSH port was now changed to open. This shows that port knocking was successful, and we can now enumerate the target machine through port 22.

What should you learn next?
So far, we have identified a wordlist file by enumerating the running website, username, and port knocking technique Port number 22 is also open.
In this next part of this CTF, we will be using this information for exploitation.
Until then, I encourage you to try to finish this CTF! There are enough hints given in the above steps.
Sources:
- Hackable III, VulnHUB
- Hackable III, VulnHUB
- Hackable III, VulnHUB
- Interpreter, Sange.fi
- Steghide, Sourceforge