LOOZ 1 VulnHub CTF Walkthrough
As per the information provided by the author, the goal of the capture the flag (CTF) is to gain root privileges on the target machine and read the root flag. The difficulty level of the machine has been mentioned as a medium. Pre-requisites would be knowledge of Linux commands and running some basic pentesting tools.
The torrent downloadable URL is also available for this VM; it's been added in the reference section of this article.
Please note: I have used Oracle Virtual Box to run the downloaded machine for all of these machines. I am using Kali Linux as an attacker machine for solving this CTF. The techniques used are solely for educational purposes, and I am not responsible if the listed techniques are used against any other targets.

What should you learn next?
The steps
- Getting the target machine IP address by running the ARP scan
- Getting open port details by using the Nmap tool
- Enumerating HTTP and identifying vulnerability in WordPress
- Brute forcing and logging in into SSH
- Escalating privileges to root user
So, now we have all the information we need, Let's get started with the challenge.
The walkthrough
Step 1
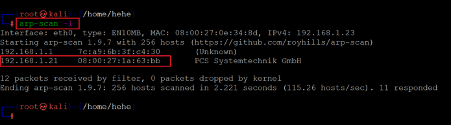
The first step in solving any CTF is to identify the target machine's IP address; since we are running a virtual machine in the same network, we can identify the target machine's IP address by running any network scanning tool. We used the Arp Scan tool for this purpose. The output of the command can be seen in the following screenshot.
Command used: << arp-scan -l >>
In the above screenshot, it can be seen that we have identified the IP address of all the devices connected to our router. Our target machine IP address that we will be working on throughout this challenge is 192.168.1.21 (the target machine IP address). We will be using 192.168.1.22 as the attacker's IP address (if required).
Note: the target machine IP address may be different in your case, as the network DHCP is assigning it.
Step 2
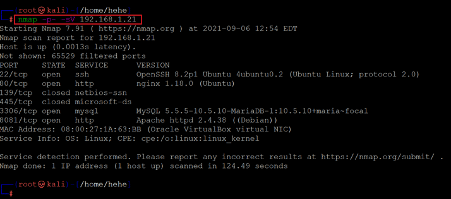
After getting the target machine's IP address, the next step is to find out the open ports and services available on the machine. We will use the Nmap tool for it, as it works effectively and is by default available on Kali Linux. The results can be seen below:
Command used: << nmap -sV -p- 192.168.1.21 >>
From the Nmap results, we identified six open ports available on the target machine. Port 22 is being used for the SSH service. Port 80 and 8081 are being used for the HTTP service. Port 3306 is being used for the MySQL service. Other open ports are 139 and 445. We will explore each port and service one by one till we gain root access to the target machine.
We used the '-sV' switch for version enumeration in the Nmap command. We also used the '-p-' option for a full port scan. It tells Nmap to conduct the scan on all the 65535 ports on the target machine. By default, Nmap conducts the scan only on known 1024 ports. So, it is especially important to conduct a full port scan during the pentest or solve the CTF for maximum results.
Step 3
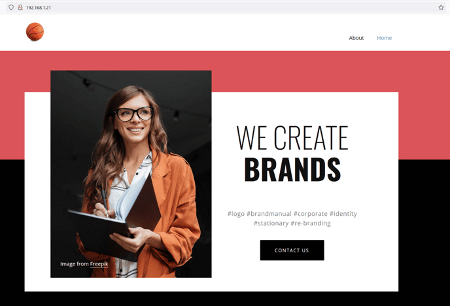
So, let us start by exploring the open port and services on the target machine. We will start the enumeration by the HTTP port. After opening the IP address in the browser, we found an application running on it, which can be seen in the screenshot given below.
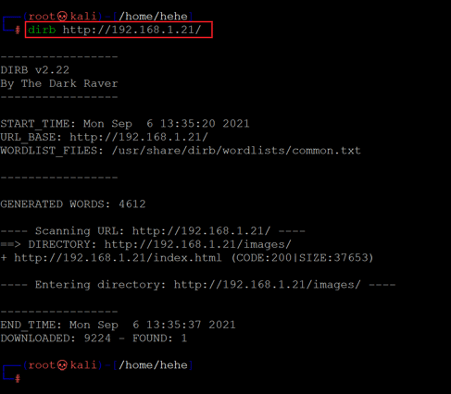
We can see the target application homepage in the above screenshot. There were a few pages, and a 'contact us' form. However, none of those could give us any direction to exploit the target application. So, we decided to dig further into the target application by enumerating the hidden files and folders. We used the Dirb tool for this purpose, a default utility in Kali Linux and the most widely used web application file enumeration tool. The Dirb scan command and results can be seen below.
Command used: << dirb http://192.168.1.21/ >>
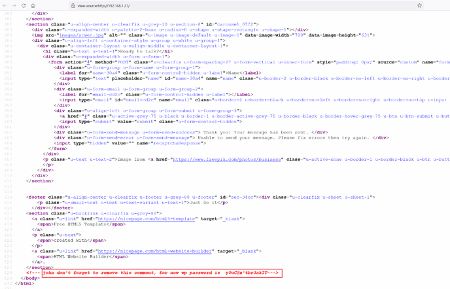
The Dirb scan could not generate any interesting information in the output. So, we started analyzing the HTML source code of the target application homepage. We found something interesting hidden in the comments, as seen in the screenshot given below.
As we can see in the highlighted area of the above screenshot, there is a hidden message in the comments section. We can identify a WordPress username and password from the message, which can be seen below for reference:
- Username: john
- Password: y0uC@n'tbr3akIT
We have already explored HTTP port 80, but we know another HTTP port is open on the target machine. We opened the wp-login.php in the browser through port 8081, but it did not load properly. So, we intercepted the request in Burp Suite for analysis which can be seen below.
When we analyzed the request in Burp Suite, we found that it redirected to a different URL with a hostname. To access the website on our attacker machine, we have to add the host to our host's file, as shown in the screenshot.
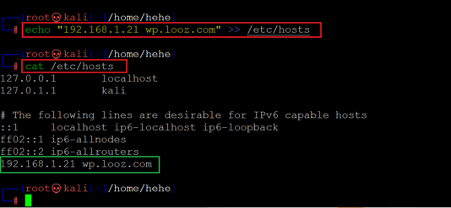
Command used: << echo “192.168.1.21 wp.looz.com” >> /etc/hosts >>
In the above screenshot, first, we have added the hostname "wp.looz.com" into the hostfile '/etc/hosts' with the help of the echo command. Then we verified the change by opening the host's file, and the output confirms that the target machine host has been added.
We'll now open the WordPress login page to check whether it is displayed properly.
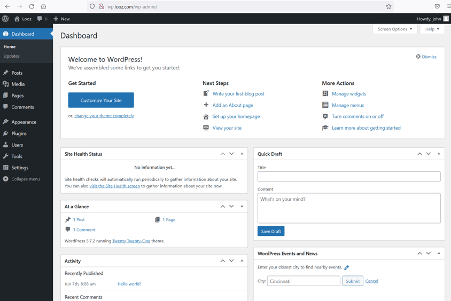
The Wp-login page can be accessed. Let's login into the admin section using the identified credentials.
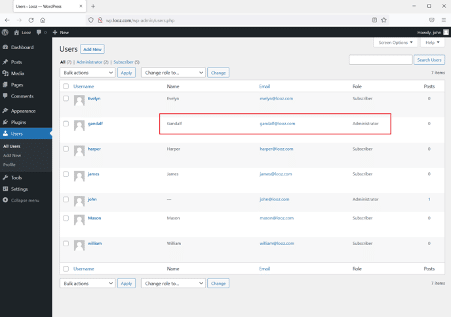
The login was successful, and now we are logged into the WordPress admin panel as user john. Let's check the current user privilege.
We checked the user privilege and found that user john has admin rights. User 'Gandalf' also has administrator rights; this could be a legitimate user, which could be used for further logging into the system! However, one more user in the system has admin rights, which can be seen highlighted in the above screenshot.
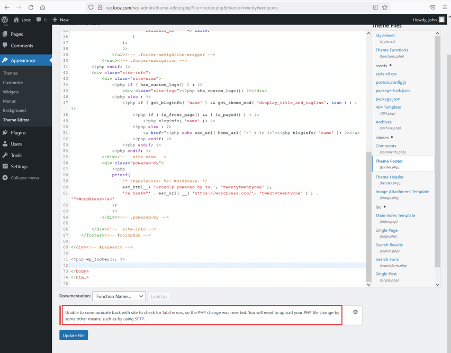
As this is an admin account, we have permission to edit the code in the target application. We can add a php shell by editing files in the target application. But when we tried editing the code, it showed an error message that the changes were reverted. The error can be seen below.
So, we cannot upload a reverse shell directly on the target machine, but we have identified a username that can be used to log in through various other interfaces. As the SSH port is also open, we will execute brute force on the SSH port in the next step.
Step 4
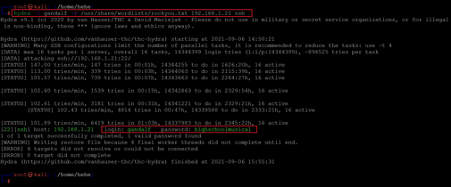
We used the hydra tool for brute-forcing the SSH user password. The hydra tool is by default available in Kali Linux. We configured the default wordlist 'rockyou.txt' for the brute force scan, which can be seen below.
Command used:
<< hydra -l gandalf -P /user/share/wordlists/rockyou.txt 192.168.1.21 ssh >>
The scan took more than an hour to complete and crack the password. The following password was identified for logging into the SSH port:
- Username: gandalf
- Password: highschoolmusical
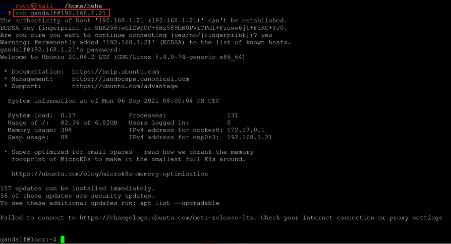
So, let's login into the SSH port using the above credentials.
Command used: << ssh gandalf@192.168.1.21 >>
The login was successful, and we are now logged into the target machine as user' Gandalf.' However, our target was to get root access, so we will try to get root in the next step.
Step 5
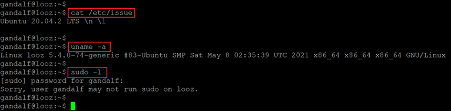
Till now, we have user access on the target machine. Now, let's run some commands to know the running operating system version and the kernel information. The commands and their output can be seen in the following screenshot:
Command used:
- << cat /etc/issue >>
- << uname -a >>
- << sudo -l >>
The command's output shows that it is running Ubuntu 20.04, which seems to be the latest version of ubuntu. However, we searched over the web for an available local exploit for the installed versions, but none could be found useful for our case. After that, we tried checking the current user's sudo permissions, but the user had no sudo permissions.
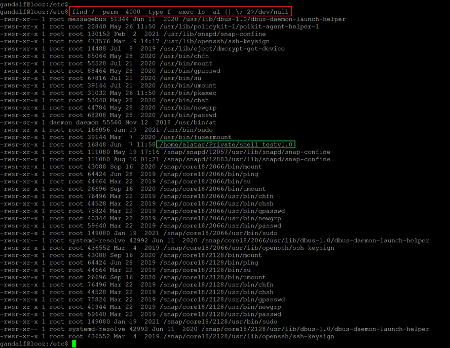
We continued checking and analyzing configurations on the target machine and explored various files and folders for further clues. During this process, when we checked the SUID binaries, we found an interesting binary which can be seen in the following screenshot.
Command used:
- << find / -prem -4000 -type f -exec ls -al{} \; 2>/dev/null >>
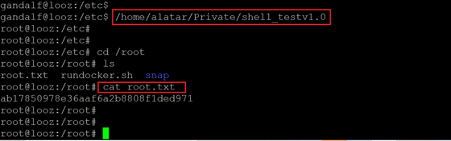
The binary named 'shell_testv1.o' has executable permissions for all users, so let us execute the binary on the target machine by copying the path. This should give root access to the target machine.
Command used:
- << /home/alatar/Private/shell_testv1.0 >>
- << cat /root/root.txt >>

What should you learn next?
The binary was executed, and we got the root shell on the target machine. Soon, we also found the root flag in the '/root' folder. The flag can be seen in the above screenshot.
This completes the challenge. We have gained root access to the target machine and read the root flag.