MONEY HEIST: 1.0.1 VulnHub CTF walkthrough
This capture the flag's (CTF) goal is to gain root access on the target machine and read the flag files. Prerequisites would be knowledge of Linux commands and running some basic pentesting tools.
The torrent downloadable URL is also available for this VM; it's been added in the reference section of this article.
For those who are not aware of the site, VulnHub is a well-known website for security researchers which aims to provide users with a way to learn and practice their hacking skills through a series of challenges in a safe and legal environment. Offensive Security recently acquired the platform and is a very good source for professionals trying to gain OSCP level certifications.
Please note: I have used Oracle Virtual Box to run the downloaded machine for all of these machines. I am using Kali Linux as an attacker machine for solving this CTF. The techniques used are solely for educational purposes, and I am not responsible if the listed techniques are used against any other targets.

What should you learn next?
The steps
The summary of the steps required in solving this CTF is given below:
- Getting the target machine IP address by using Netdiscover utility
- Getting open port details by using the Nmap tool
- Identifying vulnerabilities on running application
- Cracking JSON token with John the Ripper
- Creating JWT Token and accessing admin resource
- Logging in into SSH and getting other flags
So, as we have all the information we need to start, let us get started with the challenge.
The walkthrough
Step 1
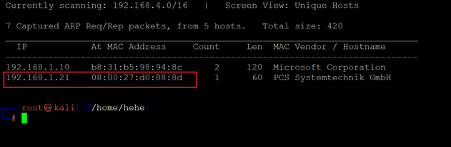
The first step to solving any CTF is to identify the target machine's IP address; since we are running a virtual machine in the same network, we can identify the target machine's IP address by running the Netdiscover command. The output of the command can be seen in the following screenshot.
Command used: << netdiscover >>
In the above screenshot, we see that we have identified the IP address of all the devices connected to our router. Still, we have hidden the MAC address of my personal connected devices due to security reasons. Our target machine IP address that we will be working on throughout this challenge is 192.168.1.21 (the target machine IP address). We will be using 192.168.1.22 as the attacker's IP address.
Note: The target machine IP address may be different in your case, as the network DHCP is assigning it.
Step 2
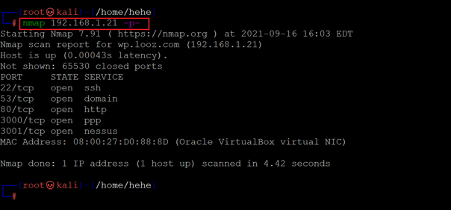
After getting the target machine's IP address, the next step is to find out the open ports and services available on the machine. We will use the Nmap tool for it, as it works effectively and is by default available on Kali Linux. The results can be seen below:
Command used: << nmap -sV -p- 192.168.1.25 >>
We used the '-p-' option for a full port scan in the Nmap command. It tells Nmap to conduct the scan on all the 65535 ports on the target machine. By default, Nmap conducts the scan only on known 1024 ports. So, it is especially important to conduct a full port scan during the pentest or solve the CTF for maximum results.
In the Nmap results, five ports have been identified as open. The open ports are ports 22, 53, 80, 3000 and 3001, which are used for SSH, domain service, HTTP, PPP and Nessus.
Step 3
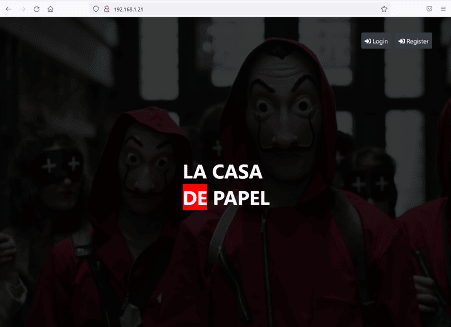
Let us start enumerating the target machine by exploring the HTTP port 8080. We opened the target machine IP address on the browser.
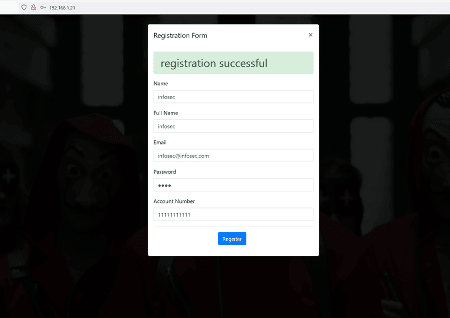
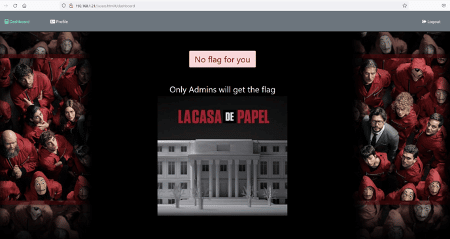
The target application has a nice money heist-themed image on the home page. There were login and signup functionality available. So, we decided to create a new user to login into the target application. The registration form as filled by us during registration can be seen below.
We set the username as 'infosec' and the password as '1234' during registration. The registration was successful. Let us login into the target application.
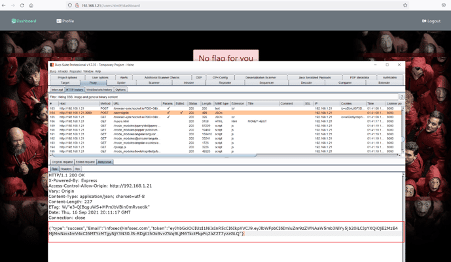
After being logged into the application on the dashboard, we got a message that there are no flags for non-admin accounts. Since we are not admin, we cannot access the flag. We started analyzing the target application through Burp suite proxy, as seen below.
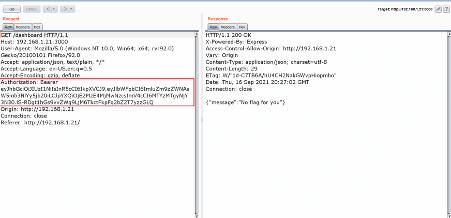
While analyzing the login page request, we noticed that the application creates a token during user sign-in. The token can be seen highlighted in the above screenshot. We checked the dashboard request to identify the parameters based on which the application rejects flag access to the user.
In the above screenshot, we can see the dashboard page request and response in the burp repeater. By analyzing the request and response from the target application, we understand that the token (as created during sign-in) is being used as the session token. The token value seems to be encoded, so we tried to decode the same using a burp decoder, as seen in the following screenshot.
In the above screenshot, we can see that the token value got partially decoded. The few parameters extracted through decoding are given below.
- Alg HS256
- Typ JWT
- Email infosec@infosec.com
- ita
- exp
We understand that this is a JSON Web Token (JWT) from the above details. As we know that JSON Web Tokens are encoded as a JSON object that is digitally signed using a JSON Web Signature or encrypted using JSON Web Encryption. So, in the next step, we will try to brute force the JSON token to identify the key.
Step 4
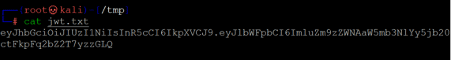
To launch the attack, we have to save the JSON token into the text file, which can be seen in the following image:
Command used: << cat jwt.txt >>
The above screenshot shows that the JWT has been saved as 'jwt.txt' in the 'tmp' directory on our attacker machine. We will try to crack the password for the JWT using the brute force technique.
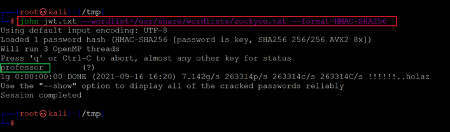
Command used:
<< john jwt.txt --wordlist=/usr/share/wordlists/rockyou.txt --format=HMAC-SHA256 >>
In the above screenshot, we used the 'john the ripper tool to identify the passphrase used as a signature for the JWT. The format was set to HMAC-SHA256, and we chose the default wordlist 'rockyou.txt.' After some time, the password hash was cracked as 'professor.' Now we know the key which is being used for signing the JWT token. In the next step, we will create a customized JWT token to access the admin user data.
Step 5
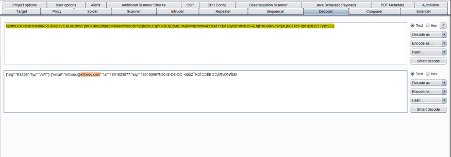
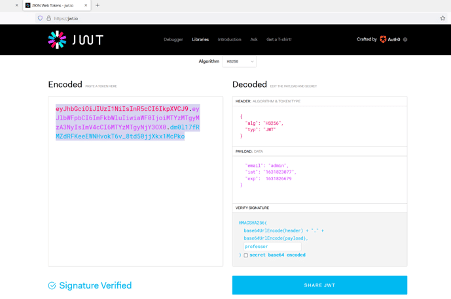
To bypass the access restriction, we can change the email parameter in the JWT to 'admin.' This shall grant us access to the restricted resource. We used the JWT encoder for this purpose, as shown in the screenshot below.
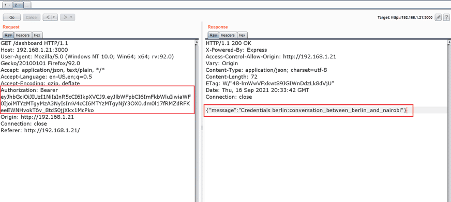
In the above screenshot, we created a new JWT using the same header details as identified in the previous token and used the valid signature 'professor.' We changed the email address in the payload data section to 'admin.' Let us replace the token in the cookie section of the dashboard request. This is shown below in the burp repeater snapshot.
The authorization was successful, and we got a response from the server. In the response from the server, we got credentials for the user berlin. The credentials are given below for reference-
Credentials berlin:conversation_between_berlin_and_nairobi
As we know from the port scanning step, the SSH port is open on the target machine. Let us login into the target machine through the SSH port.
Step 6
As we already know the password, so we logged in to the target machine as follows:
Command used: << ssh berlin@192.168.1.21 >>
We used the identified credentials for logging into the target machine as user berlin. The login was successful, and we can access the target machine as user berlin. We checked the current directory contents and found the first flag as given in the screenshot that follows.
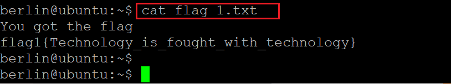
Command used: << cat flag 1.txt >>
We read the first flag named 'flag1.txt' using the cat command. There was a pcap file named 'convo2.pcapng' in the same directory. We already know that files with pcapng format contain a "dump" of data packets captured over a network. This can help us give some interesting information about the captured packets. Let us first download the file on our attacker machine for further analysis.
Commands used:
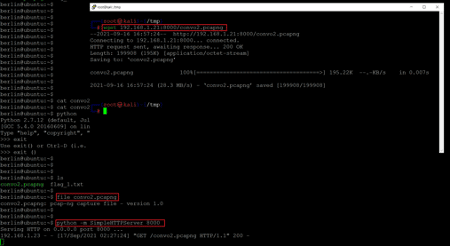
- << File convo2.pcapng >>
- << python –m SimpleHTTPServer 8000 >>
- << wget 192.168.1.21:8000/convo2.pcapng >>
We used python to allow the file to be downloaded through port 8000 on the target machine. After that, we used the wget command to download the file on our attacker machine for file analysis.
We opened the file into Wireshark and analyzed all the captured packets for any meaningful clue but could not find anything useful in our case. We again went back to the target machine SSH console and started exploring the files and folders available.
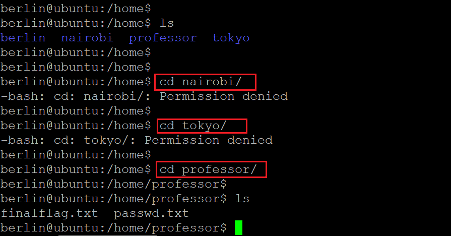
Command used: << cd professor >>
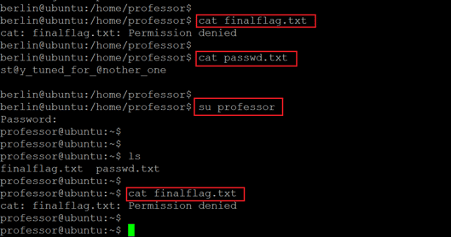
As can be seen above, there were four user folders in the home directory which means there are three other users on the target machine. We tried accessing the contents of the folders, but the access was denied for users Nairobi and Tokyo. We were allowed to see the contents of the folder 'professor.' The folder had another flag file named 'finalflag.txt.' However, when we tried opening the file using the cat command, we were denied access. This is shown below.
Command used:
- << cat finalflag.txt >>
- << cat passwd.txt >>
- << su professor >>
- << cat finalflag.txt >>
Another text file was available in the same folder named 'passwd.txt.' The file gave us a password that can be used for further login. We tried reading the flag file, but again the access was denied. We decided to check the sudo permissions for the current user by using the sudo –l command. We used the sudo command to change the current user to 'professor,' and the credentials worked, as the user was switched to 'professor.' The output gave us some joy which can be seen below.
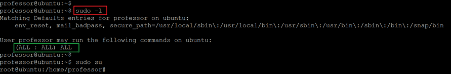
Command used: << sudo -l >>
The user professor had full sudo permissions on the target machine, which means it does not require a root password for sudo. We used this weakness to escalate user privilege to root by using the 'sudo su' command. The target machine switched the current user to root without asking for the password. Let us read the root flag.
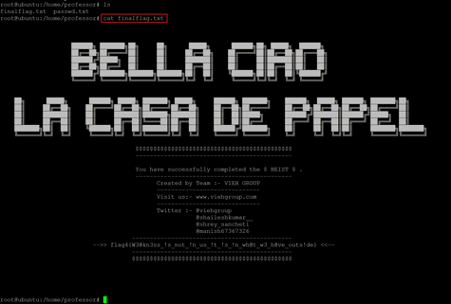
Command used: << cat finalflag.txt >>
The root flag can be seen in the above screenshot. Let us visit other user folders as more user flags need to be read to complete the challenge.
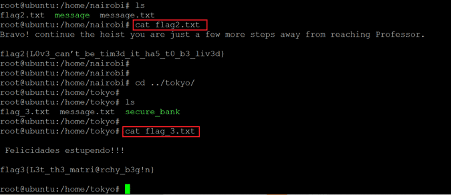
Command used:
- << cat flag2.txt >>
- << cat flag3.txt >>

What should you learn next?
In the screenshot above, we read the user flags by visiting the user' Nairobi and 'Tokyo folders.
This marks the completion of this CTF as we have gained access to the root user and read both the flags. I hope you enjoyed this money heist-themed CTF. Stay tuned for many more challenges and solutions.
Sources:
- Money Heist, Vulnhub
- Money Heist, Vulnhub
- Money Heist, Vulnhub
- JSON Web Tokens