CMMC relationship (mapping) to other frameworks
Today, we are continuing our Infosec series on the new U.S. Department of Defense Cybersecurity Maturity Model Certification (CMMC). This article will focus on how the new Defense Industrial Base (DIB) procurement gate builds on and links to the other well-known cybersecurity and procurement frameworks.
At its core, the CMMC is a new method that the US government will be using to introduce and enforce a tiered evaluation system to audit contractor and supplier compliance with the cybersecurity best practices, principles and controls. In practice, the CMMC is structured around five different levels of maturity when it comes to applying these cybersecurity principles.
Most of the CMMC is based on the US Department of Commerce’s National Institute of Standards and Technology's (NIST’s) Special Publication 800-171 Revision 2 (NIST 800-171 r2), which the Department of Defense (DoD) required suppliers to comply with in order to conduct work on their behalf.
However, due to the complexity of implementation, low rates of adoption, the ability of organizations to evaluate their own compliance and an understanding of the fact that different DoD projects require different levels of cybersecurity “maturity,” the CMMC model seeks to forge a new path forward. Most notably for many members of the DIB, the DoD is expecting independent, third-party audits for compliance with the CMMC and NIST 800-171 requirements. Given the sheer size of the DIB and the role that subcontractors play in securing Controlled Unclassified Information (CUI), the DoD hopes the “trickle-down” impact to cybersecurity and compliance will dramatically improve.

Earn your CMMC certification
CMMC model overview
Going forward, a DoD contractor must have a valid CMMC certification to even be eligible to bid on, be awarded or even participate as a subcontractor on a project involving CUI.
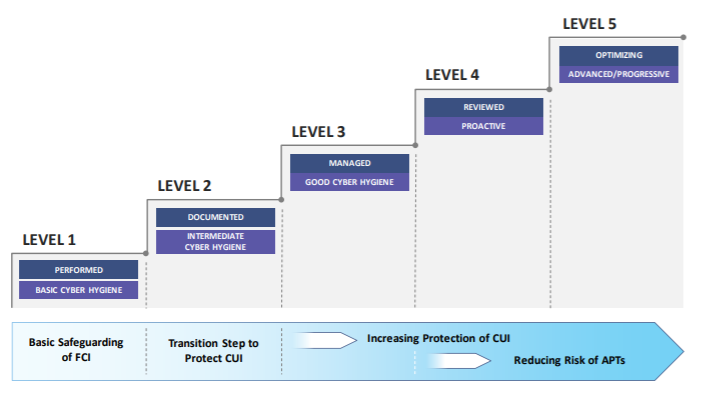
As seen below, contractors are just required to “perform” the practices outlined in the CMMC to be certified as a Level 1 supplier. At Level 3, the organization should be “managing” their compliance with the necessary processes and resources in place, while Level 5 requires ongoing, proactive cybersecurity controls to be in place. [CLICK IMAGE TO ENLARGE]
Source: Cybersecurity Maturity Model Certification
In addition to levels of maturity, the CMMC is organized into domains, capabilities, practices and processes. These are summarized below and are important to understand in any discussion about how the CMMC maps to other cybersecurity frameworks.
Mapping the CMMC to other frameworks
The NIST 800-171 is the primary foundation of the CMMC, which itself is 100 percent mapped to the NIST 800-53. However, based on particular needs and requirements for the DoD, the CMMC does add some security controls on top of those outlined in the NIST 800-171. These appear in the Level 4 and Level 5 maturity certifications. In other words, Levels 1 through Level 3 include controls and principles found in the NIST 800-171.
In addition to building on those controls from Level 3, the CMMC includes controls that link back to the following frameworks:
- NIST 800-53, Rev. 4
- CIS CSC 7.1
- NIST Cybersecurity Framework
- CERT RMM v1.2
Note: For a more detailed capability, domain, practice, and process-level mapping of the CMMC to these other cybersecurity frameworks, you can refer to this downloadable Excel document.
Comparison to the NIST 800-53 standards
The NIST 800-53a, Rev. 4 (NIST 800-53, Rev. 5 is currently in final draft form) is the cybersecurity standard for all government-owned IT networks. Its derivative, NIST 800-171, was designed for non-government computer networks that protect government-related CUI data. Organizations were required to comply with NIST 800-171 Revision 5 in December 2017, while government-owned networks themselves were required to achieve NIST 800-53 certification.
As shared in Infosec’s overview of the CMMC article, the NIST 800-53 consists of 110 controls divided into 14 groups called the NIST 800-53 control families. The CMMC directly carries over these concepts of families — called domains — and controls across the five levels of maturity.
In practice, the CMMC will replace NIST 800- 171 as a measure for non-government owned networks and will be the scoring mechanism to be enforced by the DoD. However, while the domains and security controls are present in the CMMC, the CMMC has five levels of maturity that a supplier can achieve. These levels will determine a supplier’s ability to bid and/or perform the work of different contracts.
A notable difference with the NIST 800-53 controls, however, is that the CMMC now expects organizations to obtain independent, third-party audits to ensure compliance and determine their level on the scale. Alternatively, the NIST documentation allowed organizations to perform self-assessments to score compliance.
Comparison to the CIS Critical Security Controls model
The Center for Internet Security created and maintains their Critical Security Controls model with input from the National Security Agency, the US Department of Energy, law enforcement organizations and public and private incident response experts. In light of complex, persistent and advanced cyberthreats known as Advanced Persistent Threats (APTs), the CIS security controls provide specific and actional ways to stop known attack vectors.
However, instead of a list of common security controls that may not apply to every organization or every situation, the CIS Security Controls allows an organization to prioritize and focus on a more limited number of actions that have a broader range of defensive outcomes. In addition, the CIS Security Controls model is continuously evolving and maturing as new threat reports and attacks are identified, with input from the organization’s many public and private partners.
Level 5 of the CMMC focuses on these principles of continuous improvement as a means to prepare for and combat APTs, especially given the impact that they can have on CUI from DoD-related work.
Comparison to the NIST CSF
The NIST Cybersecurity Framework provides voluntary guidance for organizations to follow, providing an assessment based on existing standards, guidelines and practices. The results of this NIST CSF assessment provides organizations with methods to better manage and reduce cybersecurity risk. In addition to the CSF assessment, the NIST CSF is designed to help organizations have a more holistic understanding of how to identify, manage and reduce risk across the organization’s management chain.
The NIST CSF consists of three main parts: the core, the implementation tiers and the profiles.
The framework’s core provides a summary of desired cybersecurity activities and related outcomes written with terminology and concepts that IT leaders and senior business executives can understand. The implementation tiers assist organizations by identifying an appropriate level of risk avoidance and acceptance that it can handle, with the CSF as a way to facilitate discussions about budget needs, priorities and risk. Finally, profiles are used to align the NIST CSF categories to industry-based scenarios so organizations can see desired end states in practice.
The CMMC pulls these facets of management buy-in, tiers of implementation and a comprehensive assessment from the CSF. The CMMC, much like the CSF, can be used as a way to help organizations talk about risk, increase cybersecurity communication with management and better engage internal and external stakeholders in the delivery of security controls with tangible data and metrics.
Comparison to the CERT Resilience Maturity Model (CERT RMM)
The CERT Resilience Management Model, or CERT-RMM, was developed by Carnegie Mellon University’s Software Engineering Institute (SEI), which has deep expertise in “resilience and cybersecurity.” The CERT-RMM model was developed to provide organizations with a comprehensive way of looking at cybersecurity, especially as it intersects with business continuity, management, security and IT operations, helping to provide continuity of operations. The first CERT-RMM was released in 2010.
The CERT-RMM is known for its process-based design, which includes elements of continual process improvement. These principles translated into Level 4 and 5 of the CMMC, where organizations aren’t just implementing security controls but proactively improving and optimizing them. In other words, organizations should not just implement a security control or piece of software but instead have institutional processes in place to continually refine their performance.
The CERT-RMM and the CMMC also share a similar model structure. The CERT-RMM and CMMC organize technical practices into groups and seek to “institutionalize” them over time through different levels of maturity. In this way, the CERT-RMM and CMMC seek to ensure an organization’s cybersecurity and resilience activities are not only in place but ingrained into the culture of the organization.

Earn your CMMC certification
Bringing it all together
The CMMC is designed to ensure that the DoD — and organizations themselves — have a way to measure the degree to which suppliers are employing and institutionalizing cybersecurity best practices. As with the other cybersecurity models, the CMMC seeks to have organizations ensure that practices are consistent, repeatable, documented and constantly improved as the complexity of their work and the organization evolves to implement DoD engagements.
Additionally, the CMMC builds on the concept that cybersecurity is not just an IT function: business process owners, managers and front-line staff need to understand their role in securing CUI, especially as the threat from APTs increase. These concepts are shared across all of the models that form the foundation of and were woven into all of the maturity levels of the CMMC.
Sources
- Cybersecurity Maturity Model Certification (CMMC) Part 2: Process Maturity's Role in Cybersecurity, Software Engineering Institute (Carnegie Mellon University)
- The 20 CIS Controls & Resources, CIS
- Cybersecurity Maturity Model Certification (CMMC) v1.02 & NIST 800-171 rev2 Compliance, Compliance Forge
- Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations, NIST
- Minimum Security Requirements for Federal Information and Information Systems, NIST
- New to Framework, NIST
- Cybersecurity Maturity Model Certification, CMMC