Understanding the CMMC model
The threat of cybercrime has always been a concern for businesses of every size and across all industries, especially with losses linked to cybercrime are expected to exceed $5 trillion by 2024. And perhaps nowhere is the threat the largest and most complex than across the United States’ Defense Industrial Base, a network that includes more than 300,000 organizations that range from universities to specialized weapon systems engineers producing cutting-edge technology for the United States military.
To better protect every phase of the procurement cycle and each link of the supply chain from low-level cybercriminals to advanced nation-state threats, the US Department of Defense (DoD) began, in 2018, requiring organizations with controlled unclassified information (CUI) to follow the 110 security controls outlined in National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171.
Unfortunately, data leaks and systems breaches still occurred at a rate and scale that the DoD decided that more needed to be done to mitigate the security risk to the country. Therefore, in March 2019, the DoD launched the Cybersecurity Maturity Model Certification (CMMC), which outlined the required cybersecurity standards needed to better protect CUI.

Earn your CMMC certification
CMMC overview
The CMMC model was developed in coordination with Johns Hopkins University’s Applied Physics Lab, the Carnegie Mellon University’s Software Engineering Institute, the DIB Sector Coordinating Council, the Office of Small Business Programs and many other stakeholders. At a high level, the CMMC model spans 17 domains that range from access control, configuration management, authentication and identity management, incident response and more.
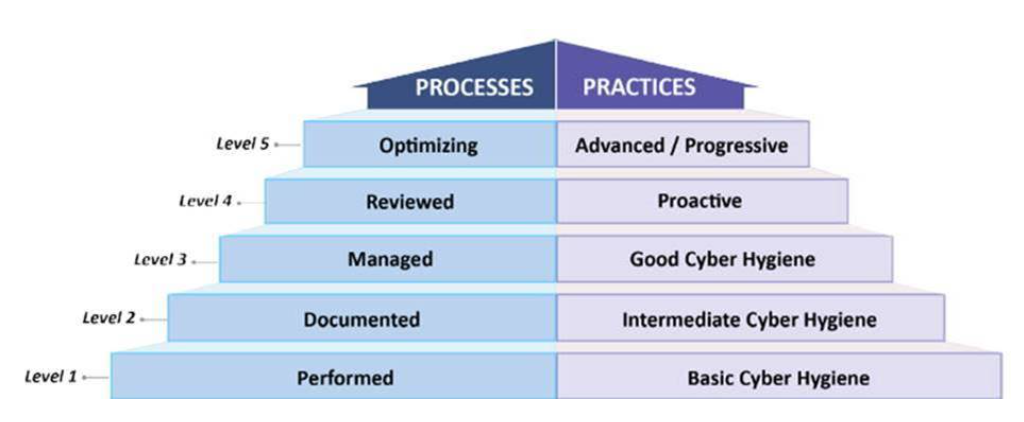
Within each domain, the CMMC model lays out capabilities, which then break out into processes and practices that are needed to manage the technology environment that contains CUI. Additionally, the CMMC attempts to classify information further into different levels of sensitivity, understanding that not every user or system interacts with the same types of data. These levels translate into five certification levels that reflect an organization’s ability to safeguard sensitive information through the use of technology and policies.
In practice, the DoD will identify the minimum level that an organization will have to be at in order to qualify to bid and be awarded a DoD contract. The level that an organization is at will be attested to by an accredited and independent third-party certification organization. This results from a CMMC assessment. During the assessment, an organization will have to demonstrate their practices, controls and capabilities to the evaluator in order to be certified.
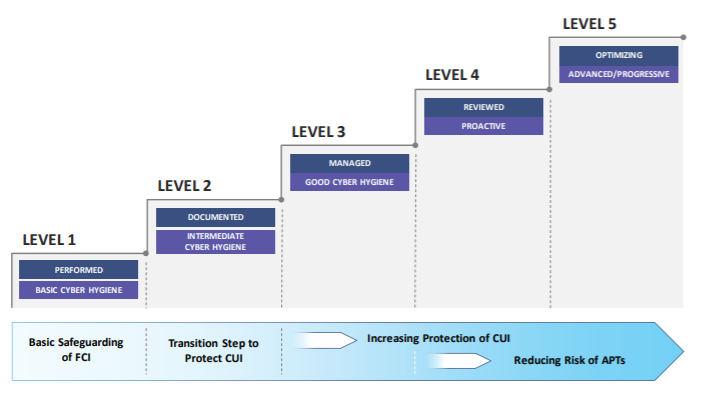
CMMC levels
As mentioned before, the CMMC model’s levels build on each other, tiered in a way that each level uses the technical, process and policy requirements of the previous level as prerequisites for the next.
The following is an overview of the different CMMC levels:
Source
Level 1: Safeguarding Federal Contract Information (FCI)
An organization must perform basic cyber hygiene practices, including using antivirus software, strong password controls and having measures in place for employees to protect FCI. More specifically, FCI is "information, not intended for public release, that is provided by or generated for the Government under a contract to develop or deliver a product or service to the Government."
Organizations at Level 1 may only be performing these security practices on an ad hoc basis or may not rely on documented processes.
Level 2: Transition step to protect controlled unclassified information
An organization must establish documented practices that allow for the repeatable implementation of the CMMC to protect any Controlled Unclassified Information (CUI). These practices will be from the US Department of Commerce’s National Institute of Standards and Technology's (NIST’s) Special Publication 800-171 Revision 2 (NIST 800-171 r2) security requirements.
Level 2 is the transition step where intermediate cyber hygiene practices should become the norm.
Level 3: Protect controlled unclassified information
At Level 3, an organization must “establish, maintain, and resource” security controls so that they are standardized in an “institutionalized management plan.” This plan should focus on implementing "good cyber hygiene" practices to safeguard CUI, including all the NIST 800-171. Finally, as part of this plan, organizations must be able to demonstrate how they are resourcing and budgeting for the security controls defined in the plan.
Level 4: Proactive protection of controlled unclassified information
Level 4 requires an organization to have implemented processes for reviewing and measuring the effectiveness of their security practices. These include the ability to detect and respond to threats as well as the tactics, procedures, and techniques utilized by advanced persistent threats (APTs).
An APT, as defined by NIST, is defined as an adversary that possesses sophisticated levels of expertise and significant resources that allow it to create opportunities to achieve its objectives by using multiple attack vectors.
Level 5: Advanced protection of controlled unclassified information
The final maturity level means that an organization must have “standardized and optimized processes in place across the organization,” as well as additional enhanced practices that add more depth to their ability to detect and respond to APTs.
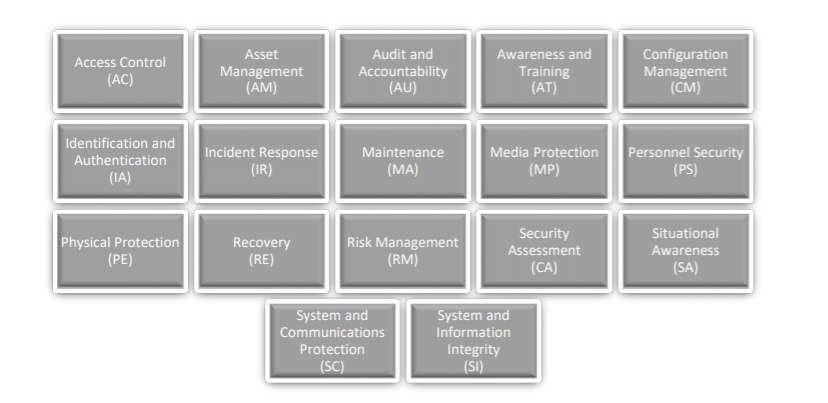
CMMC domains
Using the above levels as a guide to measure maturity, the CMMC seeks to introduce and provide a framework for the implementation of cybersecurity within an organization that is part of the DIB sector. The CMMC includes 17 domains of technical capability, each with their own five levels of certification and their own assigned processes and processes.
Fourteen of the 17 domains addressed by the CMMC are pulled from two existing security policies:
- The Federal Information Processing Standards (FIPS) Publication 200, which outlines minimum security requirements for federal information and information systems
- NIST SP 800-171: Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations’ security requirement families
The CMMC model adds Asset Management (AM), Recovery (RE) and Situational Awareness (SA) to the domains from FIBS and NIST SP 800-171.
These domains are shown below:
Source
CMMC capabilities
Furthering the break-out of the CMMC, the model identifies a set of capabilities and processes that should be in place for each domain across the five levels of maturity. The CMMC documentation organizes the 43 capabilities across the 17 domains according to the following table:
Domain
Capability
- Establish system access requirements
- Control internal system access
- Control remote system access
- Limit data access to authorized users and processes
- Identify and document assets
- Manage asset inventory
- Define audit requirements
- Perform auditing
- Identify and protect audit information
- Review and manage audit logs
- Conduct security awareness activities
- Conduct training
- Establish configuration baselines
- Perform configuration and change management
- Grant access to authenticated entities
- Plan incident response
- Detect and report events
- Develop and implement a response to a declared incident
- Perform post incident reviews
- Test incident response
- Manage maintenance
- Identify and mark media
- Protect and control media
- Sanitize media
- Protect media during transport
- Screen personnel
- Protect CUI during personnel actions
- Limit physical access
- Manage backups
- Manage information security continuity
- Identify and evaluate risk
- Manage risk
- Manage supply chain risk
- Develop and manage a system security plan
- Define and manage controls
- Perform code reviews
- Implement threat monitoring
- Define security requirements for systems and communications
- Control communications at system boundaries
- Identify and manage information system flaws
- Identify malicious content
- Perform network and system monitoring
- Implement advanced email protections
CMMC processes
Having training in and an understanding of these domains and what it takes to move up the maturity model, but integrating them into an organization’s business practices, roles and systems is quite another. This is the impetus behind the CMMC’s model’s delineation of Processes; that organizations institutionalize the activities laid out within the CMMC model during everyday practice and during times of stress.
To aid with this institutionalization, the CMMC model provides additional guidance across the five maturity levels in the form of processes. These processes and how they align with the maturity model of the CMMC is as follows:
Maturity Level
Processes
- There are no maturity processes assessed at Maturity Level 1
- An organization performs Level 1 practices but does not have process institutionalization requirements
- Establish a policy that includes [DOMAIN NAME]
- Document the CMMC practices to implement the [DOMAIN NAME] policy
- Establish, maintain, and resource a plan that includes [DOMAIN NAME]
- Review and measure [DOMAIN NAME] activities for effectiveness
- Standardize and optimize a documented approach for [DOMAIN NAME] across all applicable organization units
In other words, this structure assists an organization in assessing the extent that their cybersecurity practices are a core part of the business, with higher levels equating to how much a process is integrated into their business operations. These processes are shared across the domains, and as noted below, the practices that an organization uses. This means that the desired outcomes — in this case, protecting CUI — will be more consistent, repeatable and of higher quality.
CMMC practices
At the end of the day, the CMMC model is about the integration of sound cybersecurity practices into the daily operations of an organization. Therefore, the CMMC model also measures the implementation level of practices, which also align with processes along the maturity levels.
The model has 171 practices that are mapped across the five levels, spread out across all of the capabilities and domains. As with the maturity level descriptions, the CMMC model’s practices demonstrate a progression from basic cyber hygiene up through proactive controls and protections against advanced persistent threats. Visually, the CMMC model puts all of the pieces together into an integrated model:
Source
The 171 practices are described in detail in the CMMC publication, organized by domain and maturity level. In summary, the practices and processes are organized across the maturity levels as follows:
The majority of the practices, 110 of 171, were sourced from existing DoD security practices, the FAR Clause 52.204-21 [3] and DFARS Clause 252.204- 701, and are designed to build on one another as an organization evolves up the maturity levels. On an evaluation or in a DoD proposal, you may see a practice outlined using the CMMC naming convention of:
[DOMAIN].[LEVEL].[PRACTICE NUMBER] where:
- DOMAIN is the two-letter domain abbreviation
- LEVEL is the level number
- PRACTICE NUMBER is the identifier assigned to that practice

Earn your CMMC certification
Conclusion: Looking ahead
The introduction of the CMMC model and its associated certification is a big change for the thousands of organizations that make up the DIB sector, but the investment in time and effort can reap big rewards when it comes to reducing the risks to the multi-trillion-dollar industry.
Along the way, organizations will face new challenges, initiate new processes and practices, and change the way they define and demonstrate compliance in a fundamental way. However, these efforts will be instrumental in establishing a strong cybersecurity foundation for the next generation of DoD acquisitions and programs.
Sources
- Cybersecurity Maturity Model Certification (CMMC), Exostar
- Business Losses to Cybercrime Data Breaches to Exceed $5 trillion by 2024, Juniper Research
- Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations, NIST
- Minimum Security Requirements for Federal Information and Information Systems, NIST
- Cybersecurity Maturity Model Certification (CMMC), acq.osd.mil