How cybercrime exploits digital certificates
What is a digital certificate?
The digital certificate is a critical component of a public key infrastructure. It is an electronic document that associates the individual identity of a person to the public key associated with it.
A certificate can then be associated with a natural person, a private company or a web service as a portal. The certificate is issued by an organization, dubbed Certification Authority (or CA), recognized as "trusted" by the parties involved, and is used ordinarily for the operations of public key cryptography.
The Certification Authority issues a digital certificate in response to a request only after it verifies the identity of the certificate applicant.
The process of telematics verification of certificates can be done by anyone since the CA maintains a public register of digital certificates issued and a register related to revoke the ones (Certification Revocation List or CRL).
Each digital certificate is associated with a time period of validity, so certificates may be revoked if expired.
Other conditions that could cause the revocation of a digital certificate are the exposure of its private key, and any change of the relationship between the subject and its public key, for example the change of the mail address of the applicant.
In the process of asymmetric cryptography, each subject is associated with a pair of keys, one public and one private. Any person may sign a document with its private key. Everyone with intent to verify the authenticity of the document can verify the document using the public key of the signer, which is exposed by the CA.
Another interesting use linked to the availability of the public key of an entity is the sending of encrypted documents. Assuming you want to send an encrypted document to Pierluigi, it is sufficient that you sign them with his public key exposed by the CA. At this point, only Pierluigi with his private key, associated with the public key used for the encryption, can decrypt the document.
The public key of each subject is contained in a digital certificate signed by a trusted third party. In this way, those who recognize the third party as trustworthy just have to verify its signature to accept as valid the public key it exposes.
The most popular standard for digital certificates is the ITU-T X.509, according to which a CA issues a digital certificate that binds the public key of the subject to a Name Badge (Distinguished Name), or to an Alternative Name (Alternative Name) such as an email address or a DNS record.
The structure of an X.509 digital certificate includes the following information:
- version
- serial number
- ID algorithm
- body emitter
- validity
- subject
- information on the public key of the subject
- signature algorithm of the certificate
- signature of certificate
It is likely you'll come across the extensions used for files containing X.509 certificates, the most common are:
- CER - Certified with DER encoded, sometimes sequences of certificates.
- DER - DER encoded certificate.
- PEM - Base64-encoded certificate to a file. PEM may contain certificates or private keys.
- P12 - PKCS # 12 certificates and may contain public and private keys (password protected).
Another classification of digital certificates is the intended use. It is useful to distinguish authentication certificates and subscription certificates.
A subscription Digital Certificate is used to define the correspondence between an individual applying for the certificate and its public key. These certificates are the ones used for the affixing of digital signatures that are legally valid.
A Certificate of Authentication is mainly used for accessing web sites that implement authentication via certificate, or sign up for e-mail messages in order to ensure the identity of the sender. An authentication certificate is usually associated with an email address in a unique way.
A digital certificate in the wrong hands
Security experts recognize 2011 as the worst year for certification authorities. The number of successful attacks against major companies reported during the year has no precedent, many of them had serious consequences.
Comodo was the first organization to suffer a cyber attack. High managers at Comodo revealed that the registration authority had been compromised in a March 15th, 2011 attack and that the username and password of a Comodo Trusted Partner in Southern Europe were stolen. As consequence, a Registration Autorithy suffered an attack that resulted in a breach of one user account of that specific RA. Its account was then fraudulently used to issue nine digital certificates across seven different domains, including: login.yahoo.com (NSDQ:YHOO), mail. google.com (NSDQ:GOOG), login.skype.com, and addons.mozilla.org. All of these certificates were revoked immediately upon discovery.
In August of the same year, another giant fell victim to a cyber attack: the Dutch Certification Authority DigiNotar, owned by VASCO Data Security International. On September 3rd, 2011, after it had become clear that a security breach had resulted in the fraudulent issuing of certificates, the Dutch government took over the operational management of DigiNotar's systems. A few weeks later, the company was declared bankrupt.
But the list of victims is long. KPN stopped issuing digital certificates after finding a collection of attack tools on its server likely used to compromise it. The company informed the media that there wasn't evidence that its CA infrastructure was compromised, and that all the actions to respond the incident had been started as a precaution.
Experts at KPN discovered the tools during a security audit: they found a server hosting a DDoS tool. The application may have been there for as long as four years.
Unfortunately, the defeat is not finished, because in the same period, GemNET, a subsidiary of KPN (a leading telecommunications and ICT service provider in The Netherlands), suffered a data breach, and according to Webwereld, the hack was related to CA certificates.
The list of victims is reported in the following table published by the expert Paolo Passeri on his blog hackmageddon.com. It includes also other giants like GlobalSign and DigiCert Malaysia.
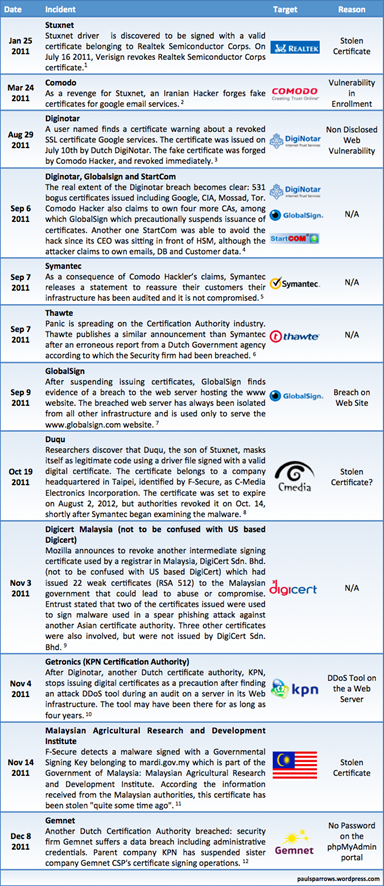
Figure - CA incidents occurred in 2011 (Hackmageddon.com)
Why attack a certification authority?
Cybercriminals and state-sponsored hackers are showing a great interest in the PKI environment, and in particular they are interested in abusing digital certificates to conduct illicit activities like cyber espionage, sabotage or malware diffusion.
The principal malicious uses related to the digital certificates are:
Improve malware diffusion
Installation of certain types of software (e.g. application updates) its code to be digitally signed with a trusted certificate. For this reason, cyber criminals and other bad actors have started to target entities managing digital certificates. By stealing a digital certificate associated with a trusted vendor and signing malicious code with it, it reduces the possibility that a malware will be detected as quickly.
Security experts have estimated that more than 200,000 unique malware binaries were discovered in the last couple of years signed with valid digital signatures.
The most famous example is represented by the cyber weapon Stuxnet used to infect nuclear plants for the enrichment of uranium in Iran. The source code of the malware was signed using digital certificates associated to Realtek Semiconductor and JMicron Technology Corp, giving the appearance of legitimate software to the targeted systems.
Stuxnet drivers were signed with certificates from JMicron Technology Corp and Realtek Semiconductor Corp, two companies that have offices in the Hsinchu Science and Industrial Park. Security experts at Kaspersky Lab hypothesized an insider job. It is also possible that the certificates were stolen using a dedicated Trojan such as Zeus, meaning there could be more.
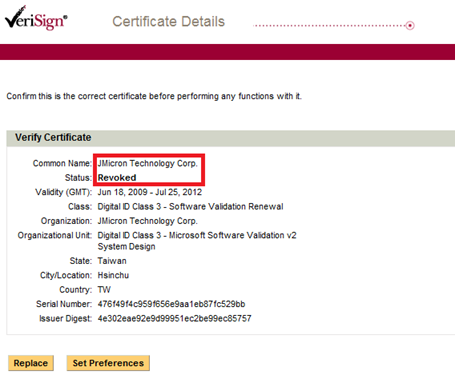
Figure - Digital certificate used to sign Stuxnet
In September 2013, cyber criminals stole digital certificates associated with Adobe. According to security chief Brad Arkin, a group of hackers signed a malware using an Adobe digital certificate, compromising a vulnerable build server of the company. The hacked server was used to get code validation from the company's code-signing system.
"We have identified a compromised build server with access to the Adobe code signing infrastructure. We are proceeding with plans to revoke the certificate and publish updates for existing Adobe software signed using the impacted certificate … This only affects the Adobe software signed with the impacted certificate that runs on the Windows platform and three Adobe AIR applications* that run on both Windows and Macintosh. The revocation does not impact any other Adobe software for Macintosh or other platforms … Our forensic investigation is ongoing. To date we have identified malware on the build server and the likely mechanism used to first gain access to the build server. We also have forensic evidence linking the build server to the signing of the malicious utilities. We can confirm that the private key required for generating valid digital signatures was not extracted from the HSM," reported the company advisory (written by Arkin).
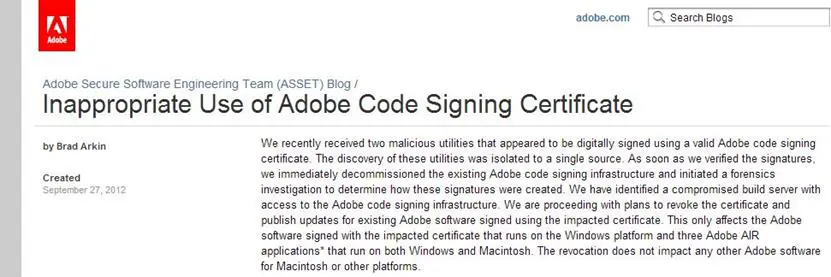
Figure - Adobe Breach Advisory
The hackers signed with a valid and legitimate Adobe certificate at least a couple of malicious codes, a password dumper, and a malicious ISAPI filter. The two malicious programs were signed on July 26, 2012.
In April 2014, security researchers at Comodo AV Labs detected a new variant of the popular Zeus Trojan, enhanced with a digital signature of its source code to avoid detection. This instance is digitally signed with a stolen digital certificate, which belongs to Microsoft Developer.
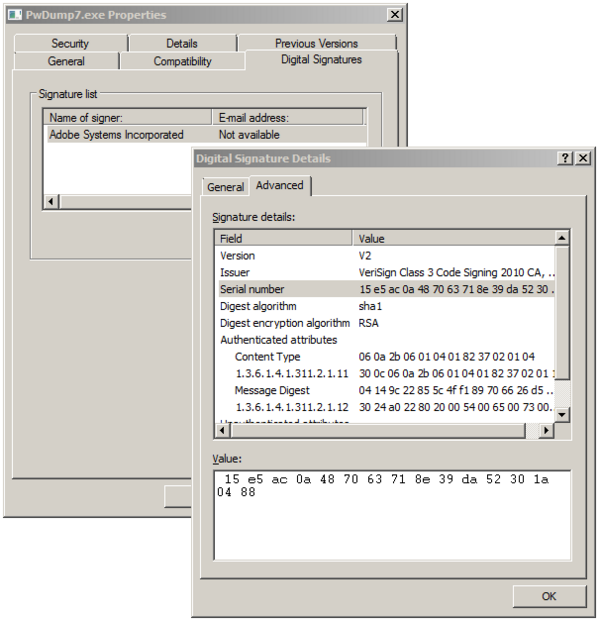
Figure - Adobe Digital Certificate abused by cyber criminals
Economic frauds
A digital signature gives a warranty on who signed a document and you can decide if you trust the person or company who signed the file and the organization who issued the certificate. If a digital certificate is stolen, victims will suffer an identity theft and related implications.
Malware authors could design a specific malicious agent that could be spread to steal digital certificates. In the case of certificates associated with a web browser, it is possible to trick victims into thinking that a phishing site is legitimate.
Cyber warfare
Cyber espionage conducted by cyber criminals or state sponsored hackers are the activities most frequently carried out with stolen certificates. Digital certificates are used by attackers to conduct "man-in-the-middle" attacks over the secure connections, tricking users into thinking they were on a legitimate site when in fact their SSL/TLS traffic was being secretly tampered with and intercepted.
One of the most blatant case was the DigiNotar one, when different companies like Facebook, Twitter, Skype, Google and also intelligence agencies like CIA, Mossad, and MI6 were targeted in the Dutch government certificate hack.
In 2011, Fox-IT security firm discovered that the extent and duration of the breach were much more severe than had previously been disclosed. The attackers could have used the stolen certificates to spy on users of popular websites for weeks, without their being able to detect it.
"It's at least as bad as many of us thought … DigiNotar appears to have been totally owned for over a month without taking action, and they waited another month to take necessary steps to notify the public," said Chester Wisniewski, a senior security advisor at Sophos Canada, in a blog post.
Fox-IT was commissioned by Diginotar to conduct an audit, dubbed "Operation Black Tulip," and discovered that the servers of the company were compromised.
Another clamorous case was discovered in December 2013 by Google, which notices the use of digital certificates issued by an intermediate certificate authority linked to ANSSI for several Google domains.
ANSSI is the French Cyber Security agency that operates with French intelligence agencies. The organization declares that an intermediate CA is generating fake certificates to conduct MITM attacks and inspect SSL traffic. Be aware that an intermediate CA certificate carries the full authority of the CA, and attackers can use it to create a certificate for any website they wish to hack.
"ANSSI has found that the intermediate CA certificate was used in a commercial device, on a private network, to inspect encrypted traffic with the knowledge of the users on that network."
Google discovered the ongoing MITM attack and blocked it. Google also declared that ANSSI has requested to block an intermediate CA certificate.

Figure - Digital certificate warning
"As a result of a human error which was made during a process aimed at strengthening the overall IT security of the French Ministry of Finance, digital certificates related to third-party domains which do not belong to the French administration have been signed by a certification authority of the DGTrésor (Treasury) which is attached to the IGC/A.
"The mistake has had no consequences on the overall network security, either for the French administration or the general public. The aforementioned branch of the IGC/A has been revoked preventively. The reinforcement of the whole IGC/A process is currently under supervision to make sure no incident of this kind will ever happen again," stated the ANSSI advisory.
The ANSSI attributed the incident to "Human Error" made by someone at the Finance Ministry, sustaining that the intermediate CA certificate was used in a commercial device, on a private network, to inspect encrypted traffic with the knowledge of the users on that network.
Misusing digital certificates
Digital certificates have been misused many times during recent years. Bad actors abused them to conduct cyber attacks against private entities, individuals and government organizations. The principal abuses of digital certificates observed by security experts:
Man-in-the-middle (MITM) attacks
Bad actors use digital certificates to eavesdrop on SSL/TLS traffic. Usually these attacks exploit the lack of strict controls by client applications when a server presents them with an SSL/TLS certificate signed by a trusted but unexpected Certification Authority.
SSL certificates are the privileged mechanism for ensuring that secure web sites really are who they say they are. Typically, when we access a secure website, a padlock is displayed in the address bar. Before the icon appears, the site first presents a digital certificate, signed by a trusted "root" authority, that attests to its identity and encryption keys.
Unfortunately web browsers, due to improper design and lack of efficient verification processes, accept the certificates issued by the trusted CA, even if it is an unexpected one.
An attacker that is able to obtain a fake certificate from any certification authority and present it to the client during the connection phase can impersonate every encrypted web site the victim visits.
"Most browsers will happily (and silently) accept new certificates from any valid authority, even for web sites for which certificates had already been obtained. An eavesdropper with fake certificates and access to a target's internet connection can thus quietly interpose itself as a 'man-in-the-middle', observing and recording all encrypted web traffic traffic, with the user none the wiser."
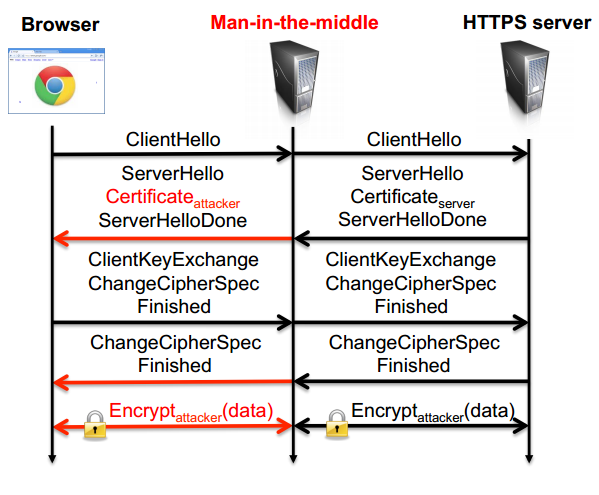
Figure - MITM handshake
Cyber attacks based on signed malware
Another common cyber attack is based on malware signed with stolen code-signing certificates. The techniques allow attackers to improve avoidance techniques for their malicious codes. Once the private key associated with a trusted entity is compromised, it could be used to sign the malicious code of the malware. This trick allows an attacker to also install those software components (e.g. drivers, software updates) that require signed code for their installation/execution. One of the most popular cases was related to the data breach suffered by security firm Bit9. Attackers stole one of the company's certs and used it to sign malware and serve it. The certificate was used to sign a malicious Java Applet that exploited a flaw in the browser of targeted browser.
Malware installed illegitimate certificates
Attackers could use also malware to install illegitimate certificates to trust them, avoiding security warnings. Malicious code could for example operate as a local proxy for SSL/TLS traffic, and the installed illegitimate digital certificates could allow attackers to eavesdrop on traffic without triggering any warning. The installation of a fake root CA certificate on the compromised system could allow attackers to arrange a phishing campaign. The bad actor just needs to set up a fake domain that uses SSL/TLS and passes certificate validation steps. Recently, Trend Micro has published a report on a hacking campaign dubbed "Operation Emmental", which targeted Swiss bank accounts with a multi-faceted attack that is able to bypass two factor authentication implemented by the organization to secure its customers. The attackers, in order to improve the efficiency of their phishing schema, used a malware that installs a new root Secure Sockets Layer (SSL) certificate, which prevents the browser from warning victims when they land on these websites.
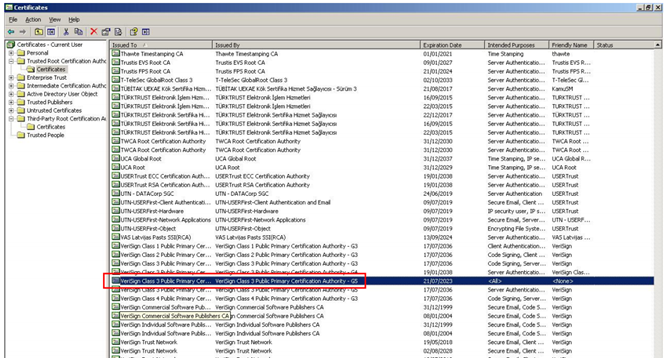
Figure - Certificate installed by malware in MS store
CAs issued improper certificates
Improper certificates are issued by the CAs and hackers use them for cyber attacks. In one of the most blatant cases, DigiCert mistakenly sold a certificate to a non-existent company. the digital certificate was then used to sign malware used in cyber attacks.
How to steal a digital certificate
Malware is the privileged instrument for stealing a digital certificate and the private key associated with the victims. Experts at Symantec tracked different strains of malware which have the capability to steal both private keys and digital certificates from Windows certificate stores. This malicious code exploits the operating system's functionality. Windows OS archives digital certificates in a certificate store.
"Program code often uses the PFXExportCertStoreEx function to export certificate store information and save the information with a .pfx file extension (the actual file format it uses is PKCS#12).The PFXExportCertStoreEx function with the EXPORT_PRIVATE_KEYS option stores both digital certificates and the associated private keys, so the .pfx file is useful to the attacker," states a blog post from Symantec.
The CertOpenSystemStoreA function could be used to open certificates stored, meanwhile the PFXExportCertStoreEx function exports the content of the following certificate stores:
- MY: A certificate store that holds certificates with the associated private keys
- CA: Certificate authority certificates
- ROOT: Root certificates
- SPC: Software Publisher Certificates
Invoking the PFXExportCertStoreEx function with the EXPORT_PRIVATE_KEYS option, it is possible to export both digital certificates and the associated private key.
The code in the following image performs the following actions:
- Opens the MY certificate store
- Allocates 3C245h bytes of memory
- Calculates the actual data size
- Frees the allocated memory
- Allocates memory for the actual data size
- The PFXExportCertStoreEx function writes data to the CRYPT_DATA_BLOB area that pPFX points to
- Writes content of the certificate store.
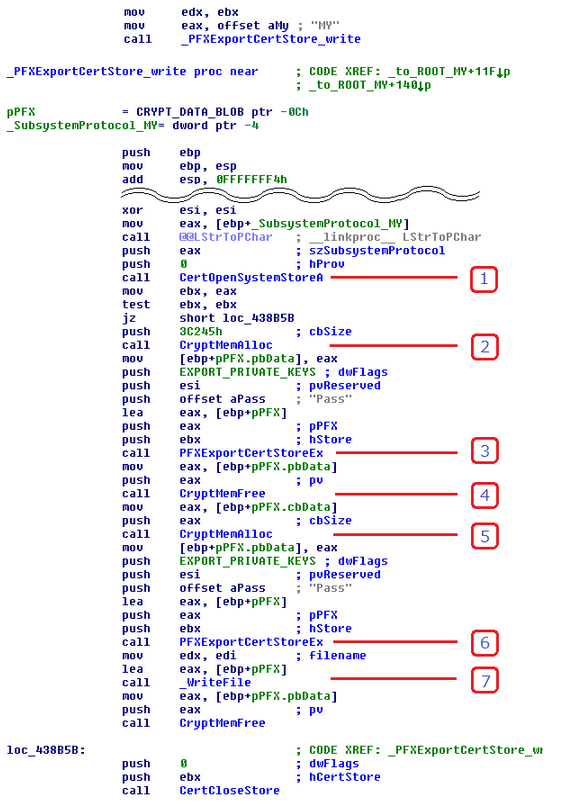
Figure - Malware code to access certificates info
The experts noticed that a similar process is implemented by almost every malware used to steal digital certificates. Malicious code is used to steal certificate store information when the computer starts running.
Once an an attacker has obtained the victim's private key from a stolen certificate, it could use a tool like the Microsoft signing tool bundled with Windows DDK, Platform SDK, and Visual Studio. Running Sign Tool (signtool.exe), it is possible to digitally sign every code, including malware source code.
Abuse prevention
I desire to close this post introducing a couple of initiatives started to prevent the abuse of digital certificates. The first one is started by a security researcher at Abuse.ch, which has launched the SSL Black List, a project to create an archive of all the digital certificates used for illicit activities. Abuse.ch is a Swiss organization that was involved in the last years in many investigations on the principal major banker Trojan families and botnets.
"The goal of SSLBL is to provide a list of bad SHA1 fingerprints of SSL certificates that are associated with malware and botnet activities. Currently, SSLBL provides an IP based and a SHA1 fingerprint based blacklist in CSV and Suricata rule format. SSLBL helps you in detecting potential botnet C&C traffic that relies on SSL, such as KINS (aka VMZeuS) and Shylock," wrote the researcher in a blog post which introduces the initiative.
The need to track abuse of certificates has emerged in recent years, after security experts discovered many cases in which bad actors abused digital certificates for illicit activities, ranging from malware distribution to Internet surveillance.
Authors of malware are exploiting new methods to avoid detection by defense systems and security experts. For example, many attackers are using SSL to protect malicious traffic between C&C and infected machines.
Each item in the list associates a certificate to the malicious operations in which attackers used it. The abuses include botnets, malware campaigns, and banking malware.
The archive behind the SSL Black List, which actually includes more than 125 digital certificates, comprises SHA-1 fingerprints of each certificate with a description of the abuse. Many entries are associated with popular botnets and malware-based attacks, including Zeus, Shylock and Kins.
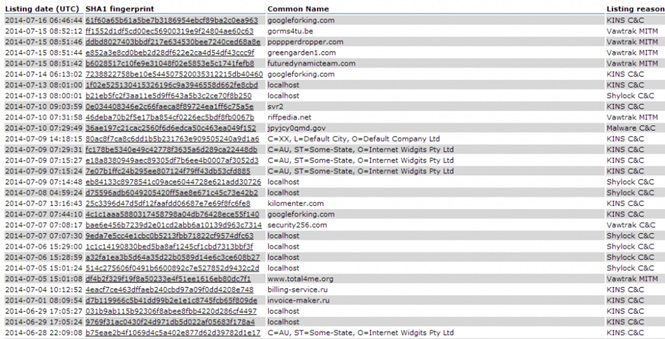
The SSL Black List is another project that could help the security community to prevent cyber attacks. When the database matures, it will represent a precious resource for security experts dealing with malware and botnet operators that are using certificates in their operations.
Abuse.ch isn't the only entity active in the prevention of illicit activities of certificates. Google is very active in the prevention of any abuse of stolen or unauthorized digital certificates. Earlier this year, the company has its Certificate Transparency Project, a sort of a public register of digital certificates that have been issued.
"Specifically, Certificate Transparency makes it possible to detect SSL certificates that have been mistakenly issued by a certificate authority or maliciously acquired from an otherwise unimpeachable certificate authority. It also makes it possible to identify certificate authorities that have gone rogue and are maliciously issuing certificates," states the official page of the project.
Unfortunately, many certificate authorities still aren't providing logs to the public.
Sources
- Digital Certificate
- 2011 CAs are under attack
- Certification authority breached
- Cybercrime avoid control lets digitally sign malware
- SSL breach update
- Rise of digitally signed malware
- Adobe code signing certificate
- Stolen digital certificates
- How attackers steal private keys digital certificates
- How digital certificates used and misused
- Hacked stolen digital certificates
- SSL mitm
- Cyber weapons usage
- Security response
- Son of Stuxnet in the wild
- Stuxnet signed certificates FAQs
- Certificate authority issues dangerous certificates
- Weblog Archives
- Second dutch security firm hacked









