Android forensic logical acquisition
The following is a demonstration of how we will create an Android Emulator; then we will go through needed steps to acquire a logical image of the system and how we can start forensically analyzing it.
In mobile forensic world (depending on the OS, the OS version, and the device) there are in general three main acquisition techniques:
- Direct acquisition
- Logical acquisition
- Physical acquisition
The direct acquisition technique can be performed if the seized device is either not locked or the PIN/Password/Pattern lock is known by the investigator, this way every data available to the user is available to the examiner via the usual user interface(UI). The only "disturbing" point is that if relying on only this method, system files, systems logs or system partition is not accessible.
The logical acquisition is a bit-by-bit copy of a given logical storage, (the storage may refer to user data partition as well as system data partition), and this acquisition method produces, in general, a relatively manageable file which can be analyzed and parsed by forensic tools. A full device backup, for instance, can be considered as a logically acquired image.
Physical acquisition acquires data directly from hardware by direct access to a given disk or flash memory. Physically acquiring a device is usually a headache but if successfully done, the produced copy can be used to recover deleted fragments and allows the examiner to put his hands on data remnants. Physical acquisition always starts by a dumping phase then a decoding phase.
This lab will be covering logical acquisition of Android emulator using Santoku Linux
Requirements
In this exercise we will use Santoku (https://santoku-linux.com) a dedicated to mobile forensics, analysis, and security, Linux distribution packaged in an easy to use, Open Source platform.
Get started with Android emulator in Santoku
After login in into your Santoku machine, Navigate to your Android SDK Manager: Santoku –> Development Tools –> Android SDK Manager
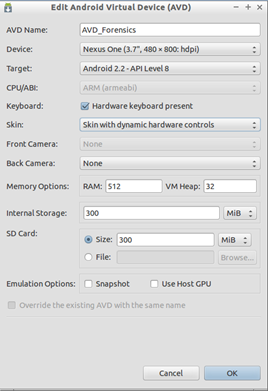
Select Tools –> Manage AVDs. Click "Create…" Enter a name for your Android Virtual Device (AVD_Forensics). Choose a device (Nexus One) then the OS (API Level 8) of your new AVD from the "Target" drop-down list. Allocate RAM (512 Mib), Internal Storage (300 Mib) and SD card size (300 Mib) then click OK:
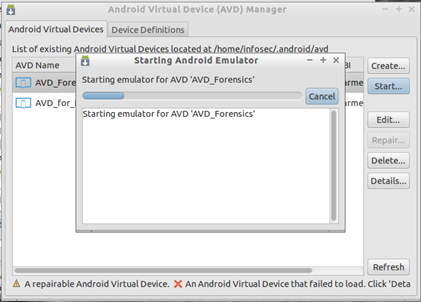
From AVD manager select your created emulator and click on "Start", Select applicable options on the next screen and click on "Launch".
Once the virtual device is launched we can proceed by creating some evidence:
- Simulate SMS/GSM Calls
The Android emulator mimics all of the hardware and software features of a typical mobile device, except that it cannot place actual phone calls/SMS, but we can simulate them using Telnet
In a terminal window (CTRl+ALT+T) type in the command telnet localhost 5554 (5554 is the port opened by the emulator)
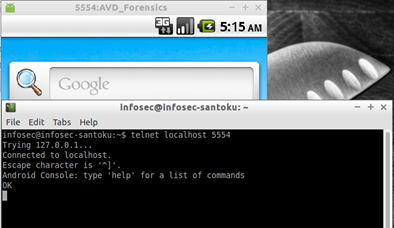
Once connection is established, send SMS using the command: sms send <sender_s_phone_number> <message text> as follows (you can replace <sender_s_phone_number> with any fake number) :
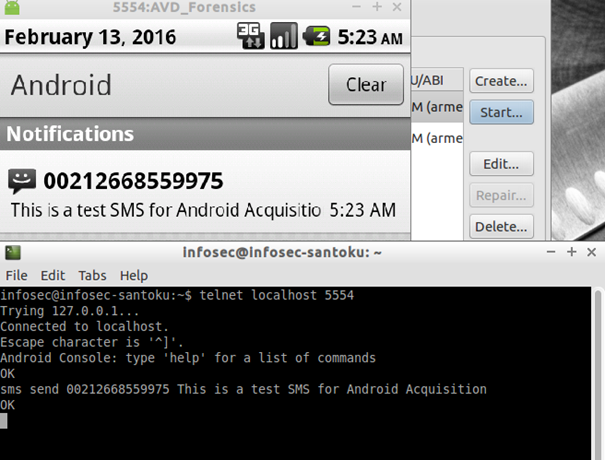
And now reply the incoming SMS to make more evidence:
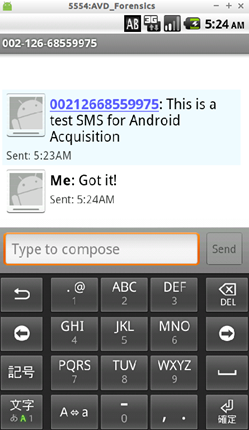
Always on the opened telnet terminal we can simulate GSM call using the command gsm call <phonenumber>
The emulator will show incoming call user interface (UI) as follow:
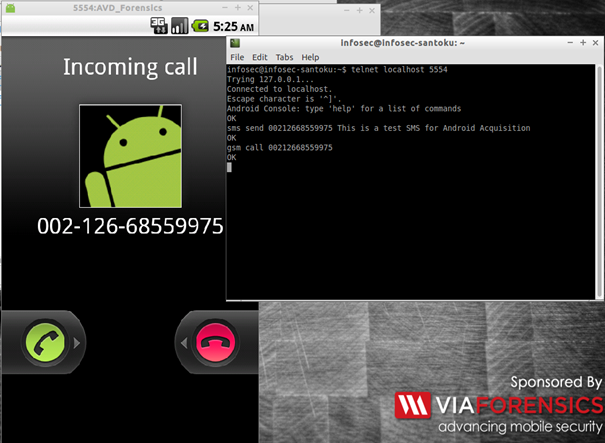
Figure 1 - Simulated Incoming Call
The gsm command supports the many parameters but the most interesting in our study are:
- Call <phonenumber>: Simulate an inbound phone call from <phonenumber>.
- Accept <phonenumber>: Accept an inbound call from <phonenumber> and change the call's state "active".
- Busy <phonenumber>: Close an outbound call to <phonenumber> and change the call's state to "busy".
- Cancel <phonenumber>: Terminate an inbound or outbound phone call to/from <phonenumber>.
The full list can be found at https://developer.android.com/tools/devices/emulator.html
So to accept the previously simulated phone call we can execute the command gsm accept <phonenumber>:
Once command executed the Incoming call user interface will switch to hang up UI:
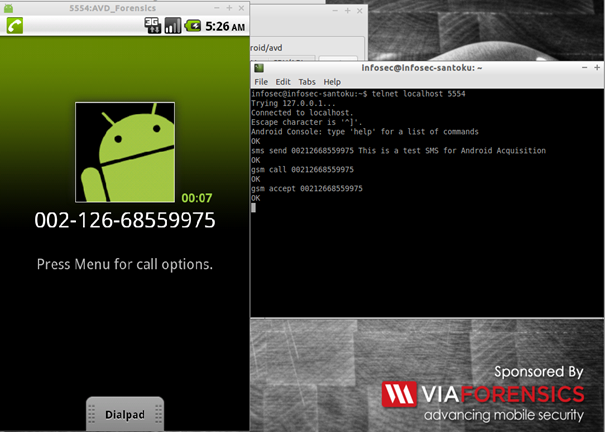
Figure 2- Simulated accepted call
To simulate a missed call we can make a gsm call then cancel it:
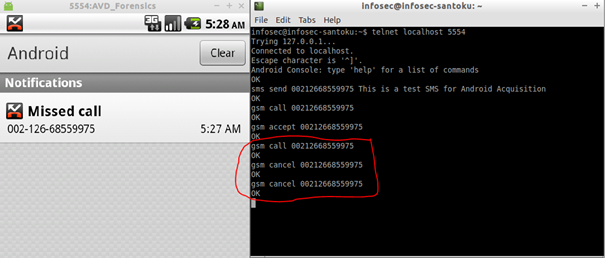
- Create phone book entries
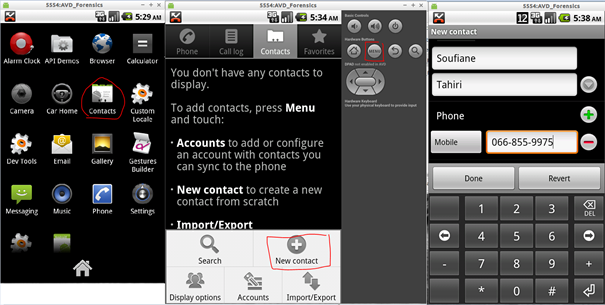
Creating a contact on an emulator is the same as creating one on an actual device. From the menu, click on "contacts." If your phone book is empty (which must be the case if your emulator is freshly created) click on "Menu" from the simulated keyboard then "New contact" fill-in contact info then press "Done":
Logical acquisition
Open a terminal window and type in adb shell this will let us issue commands without entering the adb remote shell on the emulated device (or the device if using a real one). Once shell gained type in "mount" command, this command will attach the filesystem found on the device to one file tree:
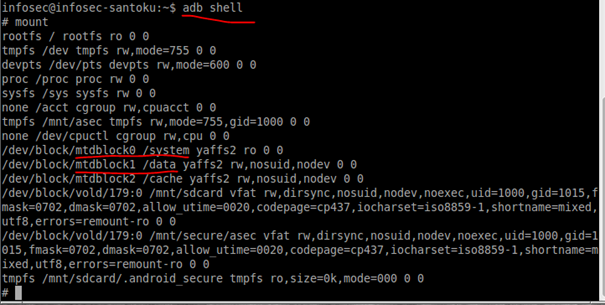
As highlighted in the screenshot above, the /data partition is at /dev/block/mtdblock1, you can execute "df" command to displays the amount of disk space available on this partition:
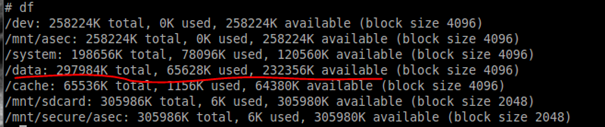
Type exit to exit out from the adb shell:
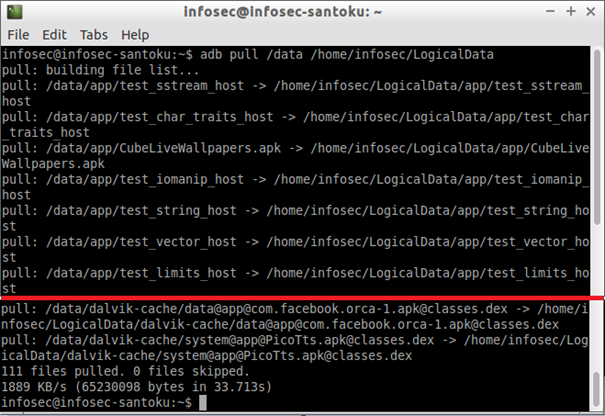
ADB provides a pull command that can be used to extract any filesystem (file or folder) to the examiner's computer. The logical acquisition is opening files in the file browser.
To pull a file or a directory the command is adb pull file /dest/file assuming that all user's data is stored in /data/ partition we can simply extract all user /data partition by typing adb pull /data /path/to/store/files on a new terminal window (you can see what will be extracted by typing ls /data on your shell window):
Now you can start to explore all folders pulled directly using the OS Explorer:
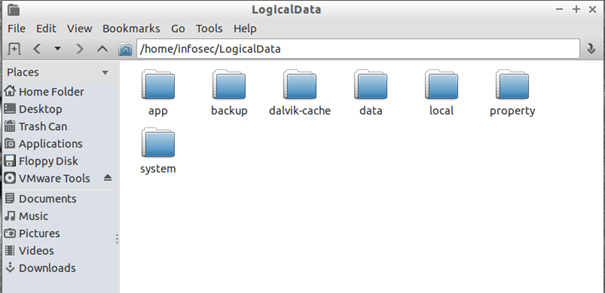
Note that all installed applications are under /data/data folder.
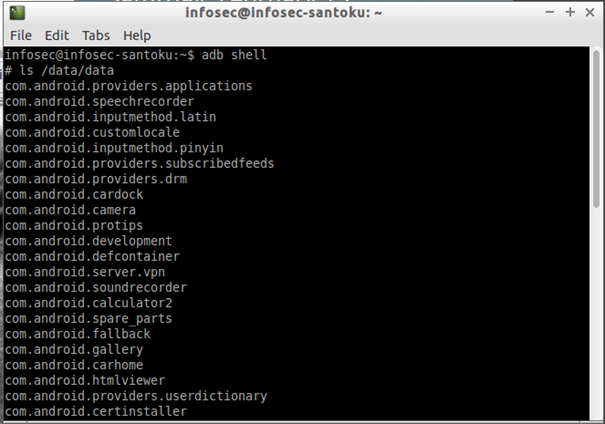
If you want to extract a single application folder you can execute the command as adb pull /data/data/<packagename> /path/packagename. To see the full list of installed packages you can type ls /data/data in shell window:
- 1-Type adb shell to get back to shell environment
- 2-Type ls /data/data to get list of installed packages
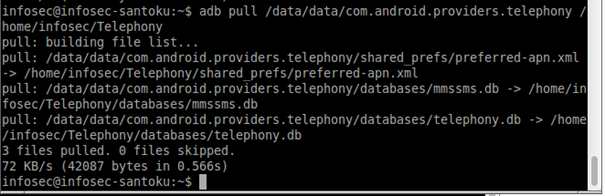
After exiting shell environment by typing exit command, you can extract SMS for example by pulling the package name com.android.providers.telephony. The command will be adb pull /data/data/ com.android.providers.telephony /path/Telephony/
You can change /path/Telephony/ to the path where you want to store extracted data (in the following example the path /home/infosec/Telephony was used)
And then using different utilities we can start to explore files within extracted directory (ex. Sqliteman included with Santoku)
To browse to this directory click on the icon of File Manager PCManFM then double click on Telephony folder:
Moreover, by exploring databases folder, we can see mmssms.db which contains everything related to the SMS/MMS as suggested by their tables name You can open it by right-clicking on the database and selecting "Sqliteman":
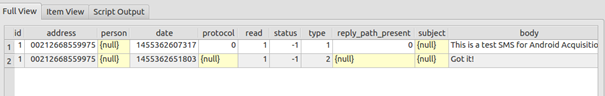
By querying, for example, the SMS table (double click on the table to view it), we can find all SMS (and using other tables and columns we can correlate IDs to make solid evidence). The following is the SMS we've sent previously:
In addition to ADB, Santoku comes with AFLogical which provides a basic framework for extracting data from Android devices using Content Providers and then saves the data to the SD Card of the device including:
- Contacts
- Call Logs
- SMS
- MMS
- MMS Parts
- Device info
In order to use this tool, open a terminal window and type in: aflogical-ose (ose stands for Open Source Edition) once asked to enter root password [sudo] password for infosec: type in the password you used to log into Santoku (root password is infosec458$%*) then wait until you get Press enter to pull /sdcard/forensics into ~/aflogical-data/
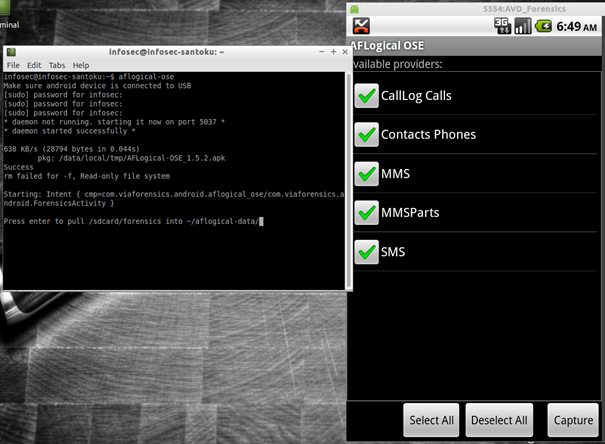
Before continuing, on your emulator, select the data you want to extract and click "Capture" then "OK" after data is extracted correctly:
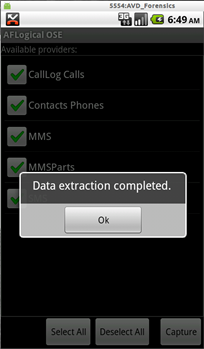
On the terminal windows press enter to continue:
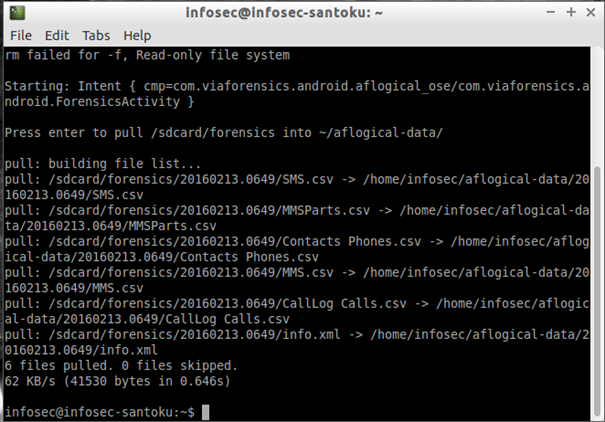
This will pull the data from SDCard to the location "~/aflogical-data". Santoku will automatically pull all the data recovered from the emulator to that location:
To view the data, open a terminal window and type: cd ~/aflogical-data/ then ls to see created folder:
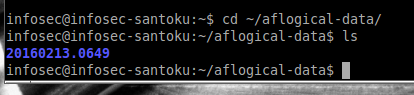
Now you can browse any images as well as the extracted data (such as contacts, call logs, MMS/SMS, and device info) in CSV format:
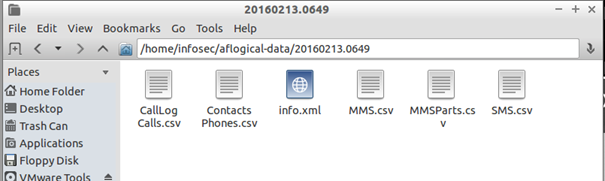
If you open SMS, for example, you will be able to see our previously simulated sms send
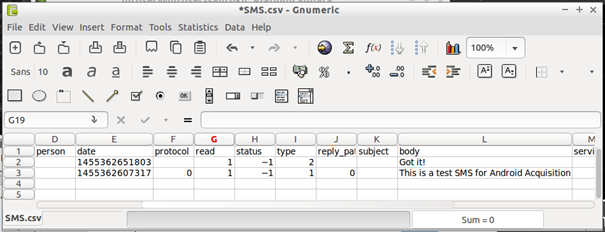
Most valuable information is usually stored in SQLite databases:
The following is the extraction of the database holding phonebook using adb pull:
You can also browse SQLite dbs by invoking Sqliteman utility from command line using: sqliteman database.db as follow:
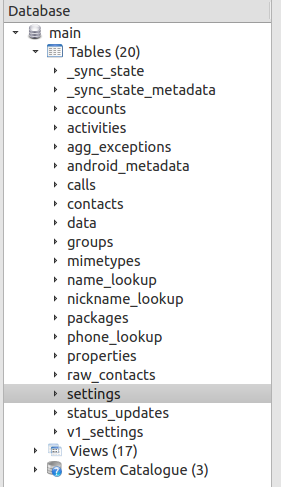
As you can see this database contains 20 tables:
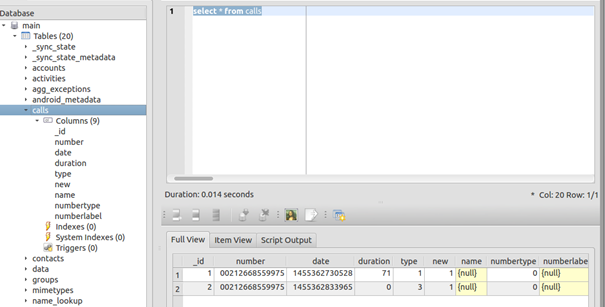
Moreover, by querying each table you can get very useful information such as calls history: (select * from calls)