Common mobile forensics tools and techniques
Data acquisition is the process of gathering information from mobile devices and their associated media. This process reduces the chances of data loss due to damage or battery depletion during storage and transportation. Mobile device identification is necessary at the beginning of the forensic examination. The identification process includes understanding of the type of cell phone, its OS, and other essential characteristics to create a legal copy of the mobile device’s content.
There are many tools and techniques available in mobile forensics. However, the selection of tools and techniques during an investigation depends on the type of mobile device and its associated media.
How do you gather data from mobile devices?
The data can be gathered from mobile devices in two ways, namely, physical acquisition and logical acquisition.
Physical Acquisition, also known as a physical memory dump, is a technique for capturing all the data from flash memory chips on the mobile device. It allows the forensic tool to collect remnants of deleted data. Initially, the received data is in raw format and cannot be read. Later on, some methods are applied to convert that data into a human readable form.
Logical Acquisition, or logical extraction, is a technique for extracting the files and folders without any of the deleted data from a mobile device. However, some vendors describe logical extraction narrowly as the ability to gather a particular data type, such as pictures, call history, text messages, calendar, videos, and ringtones. A software tool is used to make a copy of the files. For example, iTunes backup is used to make a logical image of an iPhone or iPad.
What data types can you collect from a mobile device?
Students should understand data types before the collection of data from a mobile device. The common data types include contacts list, call log, SMS, images, audio, video, GPS data, and apps data. Also, both current and deleted data types can be extracted from a mobile device.
Call Detail Records (CDRs): Service providers frequently use CDRs to improve network performance. However, they can provide useful information to investigators, as well. CDRs can show:
- Call started and ended date/time
- The terminating and originating towers
- Whether the call was outgoing or incoming
- Call time duration
- Who was called and who made the call
Almost all service providers retain these important records for a certain time. The forensic specialist can collect these records if he requires. However, the collection of this information depends on the policies of the concerned state. Every state has different laws in this regard.
Global Positioning System (GPS): GPS data is an excellent source of empirical evidence. If the suspect has an active mobile device at the crime scene, GPS can pinpoint his location as well as his criminal acts. GPS also locates the movements of the suspect from a crime scene to the hideout. Furthermore, it helps in finding phone call logs, images, and SMS messages. Presently, a GPS system includes 27 satellites in operation.
App Data: Many apps store and access data the user is not aware of. In fact, many apps seek permission during the installation process to access these data. For example, photo or video editing apps request permission to access media files, camera, and GPS for navigation. This data can be a primary source of evidence to the court.
SMS: Text messaging is a widely used way of communication. Text messages leave electronic records of dialogue that can be presented in the court as evidence. They include the relevant information such as:
- Date/time of each message
- Phone number of sender and receiver
Photos and Videos as Evidence: They can be a tremendous source of evidence, but their relevance to crime and authentication is crucial.
What tools & techniques are commonly used in mobile forensics?
Forensic software tools are continually developing new techniques for the extraction of data from several cellular devices. The two most common techniques are physical and logical extraction. Physical extraction is done through JTAG or cable connection, whereas logical extraction occurs via Bluetooth, infrared, or cable connection.
There are various types of tools available for mobile forensic purposes. They can be categorized as open source, commercial, and non-forensic tools. Both non-forensic and forensic tools frequently use the same techniques and protocols to interact with a mobile device.
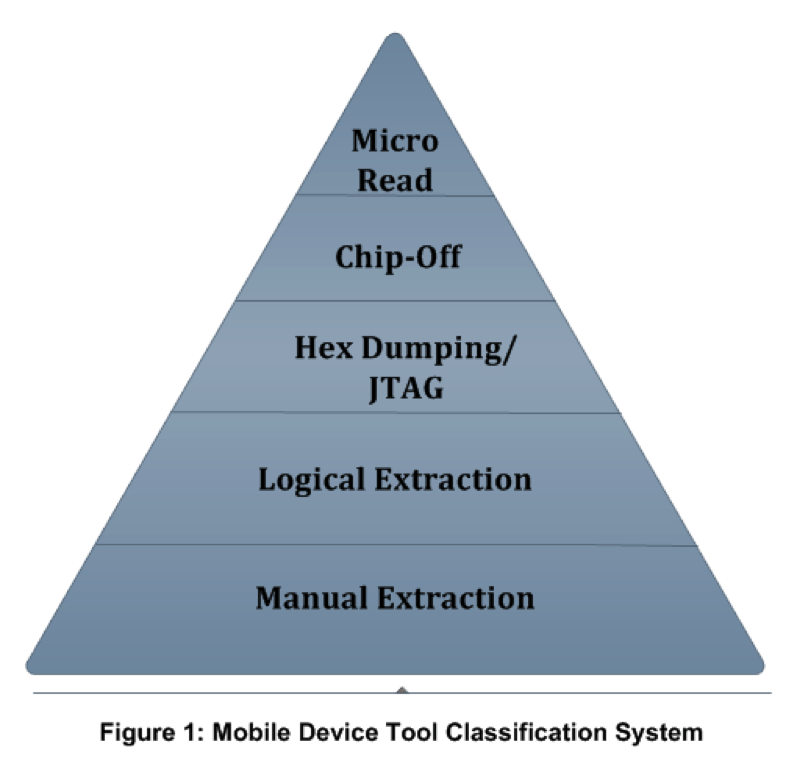
Tools Classification System: Forensic analysts must understand the several types of forensic tools. The tools classification system offers a framework for forensic analysts to compare the acquisition techniques used by different forensic tools to capture data. Figure 1 shows the system:
Manual extraction
The manual extraction technique allows investigators to extract and view data through the device’s touchscreen or keypad. At a later stage, this data is documented photographically. Furthermore, manual extraction is time-consuming and involves a great probability of human error. For example, the data may be accidentally deleted or modified during the examination.
Popular tools for manual extractions include:
- Project-A-Phone
- Fernico ZRT
- EDEC Eclipse
Logical extraction
In this technique, the investigators connect the cellular device to a forensic workstation or hardware via Bluetooth, Infrared, RJ-45 cable, or USB cable. The computer—using a logical extraction tool—sends a series of commands to the mobile device. As a result, the required data is collected from the phone’s memory and sent back to the forensic workstation for analysis purposes. The tools used for logical extraction include:
- XRY Logical
- Oxygen Forensic Suite
- Lantern
Hex dump
A hex dump, also called physical extraction, extracts the raw image in binary format from the mobile device. The forensic specialist connects the device to a forensic workstation and pushes the boot-loader into the device, which instructs the device to dump its memory to the computer. This process is cost-effective and supplies more information to the investigators, including the recovery of phone’s deleted files and unallocated space. The common tools used for hex dump include:
- XACT
- Cellebrite UFED Physical Analyzer
- Pandora’s Box
Chip-off
The chip-off technique allows the examiners to extract data directly from the flash memory of the cellular device. They remove the phone’s memory chip and create its binary image. This process is costly and requires an ample knowledge of hardware. Improper handling may cause physical damage to the chip and renders the data impossible to retrieve. The popular tools and equipment used for chip-off include:
- iSeasamo Phone Opening Tool
- Xytronic 988D Solder Rework Station
- FEITA Digital inspection station
- Chip Epoxy Glue Remover
- Circuit Board Holder
Micro read
This process involves interpreting and viewing data on memory chips. The investigators use a high-powered electron microscope to analyze the physical gates on the chips and then convert the gate level into 1’s and 0’s to discover the resulting ASCII code. This process is expensive and time-consuming. Also, it requires an ample knowledge of hardware and file systems. There is no tool available for micro read (Ayers, Brothers, Jansen, 2014).
Computer forensics boot camp course
Did you find this article very useful? Are you aspiring for the certified cyber forensics professional (CCFP) examination? Infosec offers a uniquely designed Authorized Computer Forensics Boot Camp Course for the students of CCFP and CCFE examinations. You can join this course to acquire a professional CCFP certification.
Infosec also offers thousands of articles on a variety of security topics.