Cyber Weapon of Mass Destruction- The Blackhole Exploit Kit
Recent security advisories reveal that the web exploit kits like the Blackhole Exploit Kit are responsible for the vast majority of web attacks and malware infections taking place over the World Wide Web. So, the question arises what are these exploit kits that we are talking about? These exploit kits are a type of malicious toolkit used to exploit security holes in software applications, which are generally installed on a computer. The Blackhole Exploit kit is a set of PHP scripts all protected with ionCube encoder to secure the code from miscreants trying to steal the code.
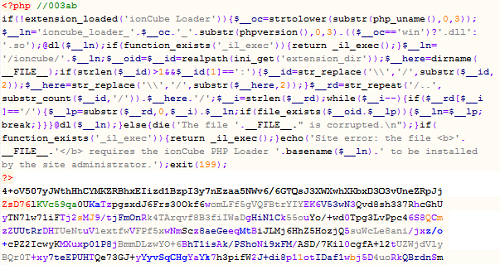
IonCube encoding on the Blackhole Exploit PHP scripts
These kits are specifically designed to target vulnerabilities in unpatched system that may be in Java, Adobe Reader or an unpatched installation of Flash.
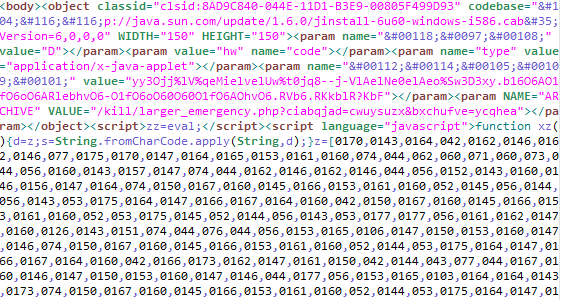
Blackhole Exploit kit obfuscated Javascripts targeting vulnerabilities
Functional Analysis
Now the question arises, what makes these kits exploit and compromise our systems? The procedure is fairly simple. Firstly, a victim visits a malicious website hosted on hacker-owned machine, which gives him the freedom to play with the security of the website. Once a victim visits this malicious website, he is redirected through various intermediary servers and finally lands on a malicious server hosting the exploit kit. Then follows a scanning phase by the exploit kit on the victim's system to scan for known vulnerabilities. Once a vulnerability is found, an exploit/payload effecting that particular vulnerability is downloaded on the victim's machine and executed in the background.


Let us take a very simple example of a machine having windows XP version with the SMB service running. The exploit kit will simply detect this vulnerable service and drop a payload like a reverse TCP on the victim's machine. The payload will be executed in the background and yay! We have a reverse connection to the victim's system. To have better understanding of this technique, I would suggest you to try out the Netapi exploit on Windows XP using Metasploit —also known as ms08_067_netapi.
How it all started
The roots of software exploitation start a long time ago. The techniques were made better over time and now it is offered as a package of exploits known as the Exploit Kit. These exploit kits are available on the underground market (Deep Web) or in some instances on the World Wide Web. The black hats, script kiddies particularly, and criminals use these exploits to compromise thousands of people, maybe setup a botnet spreading malware, or just for the fun of it. A report by Kaspersky Labs states that MPack was one of the first publicly available exploit kits in 2006 made by the Russian cyber-warriors. This was basically a collection of PHP scripts aimed at exploiting simple vulnerabilities that may be present in the client software. There was a boom in the number of compromised systems just after this kit went viral.

Price Model for Blackhole v1.0.0
Coming back to our modern day exploit kits, the trend has certainly improved and these kits have become more difficult to detect just due to the antivirus evasion techniques they use. Nowadays, these exploit kits come in an easy to use interface in which the user does not need to work hard to actually learn how to use it. It is as simple as a click-click scenario, and you are good to go! These kits usually have a web interface that gives a view of how the kit is functioning and the statistics of infections. There have been kits that offer customer support on its license for six months to a year. Major developments to these kits occur in the underground cyber-market of China and Russia.
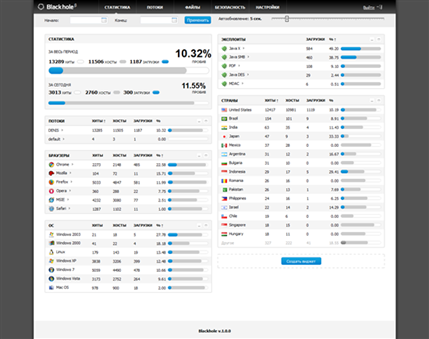
Blackhole Exploit Kit Interface
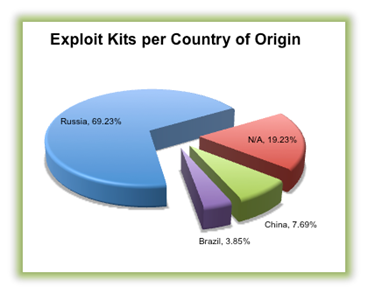
Back to the Blackhole Exploit kits. Symantec recently had a security advisory in which they published the functional analysis of this kit. It was stated that the Blackhole used an obfuscation technique to muddy the exploits. The page contains a large array inside the <textarea>. When decoded, the array results in various exploits for popular vulnerabilities such as PDF, JAVA, HCP, MDAC, etc.
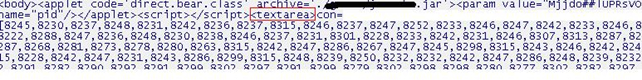
This array is turn decoded by a code as shown
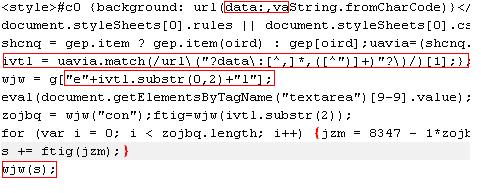
The variable "ivtl" contains the string "url(data:,va…." after the ".match()" method. The String "wjw = g["e"+ivtl.substr(0,2)+"l"];" results in "eval" as "ivtl.substr(0,2)" evaluates to "va". String "s," which contains the decoded script, is passed to "wjw" to be executed. Now the redirection takes place through a malicious code that redirects a user to download a payload. This is an example of a jar file code referenced from the Symantec security advisory.

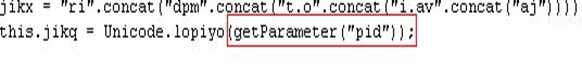
Often these redirects, due to code injections, do not link directly to the Blackhole Exploit Kits. Instead, a reference to the server is created from where the request is bounced to the exploit site. This approach allows the user traffic to be sold as a commodity. Such a remote server is often known as the Traffic Directing Server, which may also lead to other exploits other than the Blackhole. It was also reported that this traffic redirection was being abused to earn money through affiliate advertisement schemes and finally redirecting it to the Blackhole site.
The decoded string has the pattern "d.php?f=[0-9]{1,2}&e=[0-9]{1,2}". This URL is then used to perform other malicious downloads. This URL was analyzed to download Trojan.Carberp that posts a unique id to the command and control server, which is used during a transaction between the Trojan and the command server. The URL has the pattern "/set/task.html" and posts all the running processes from the victim's computer to the command server. The URL has the pattern "set/first.html" and the data posted has the pattern "id=(Unique number posted on /set/task.html)&os=(Name-version of OS)&plist=(List of all running processes)"

This Trojan then downloads three malicious modules:
- stopav.plug – This module disables the antivirus installed on the victim's computer.
- miniav.plug – This checks for the presence of other Trojans, such as Zeus, and if found, the Trojan deletes its competitor(s).
- passw.plug – This hooks the export table of a number of WININET.dll and USER32.dll functions and logs every username/password combination that is typed, as well as any URLs visited.
The command server sends the download command to the Trojan that downloads these payload files and executes them silently in the background. As an end result, our system is compromised and backdoored with this Trojan.
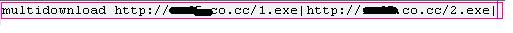
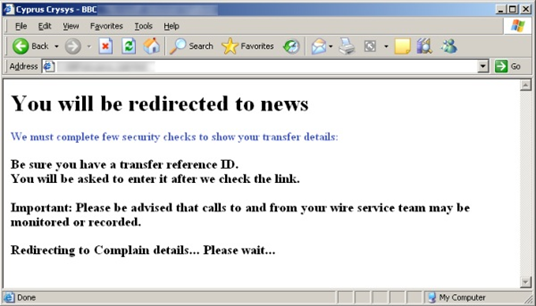
There has also been a spur in the spam message campaigns based on Blackhole Exploit Kits that send messages to compromised legitimate sites and again utilize the attack vector using Blackhole Kit exploitation techniques. These spam messages look like authentic messages from Facebook, or Linkedin. These are all spoofed. It was also reported that messages spoofed as fake news alerts from the BBC and CNN news channels further added to the havoc. The messages have a subject line that lures a victim into opening these messages and clicking on the link. In turn, malware is downloaded. There you go again, you are owned baby!
Some of the spoofed messages with malicious links:
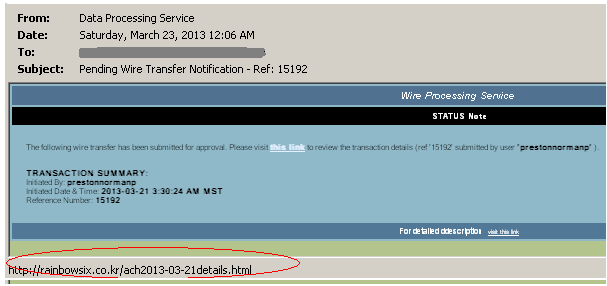
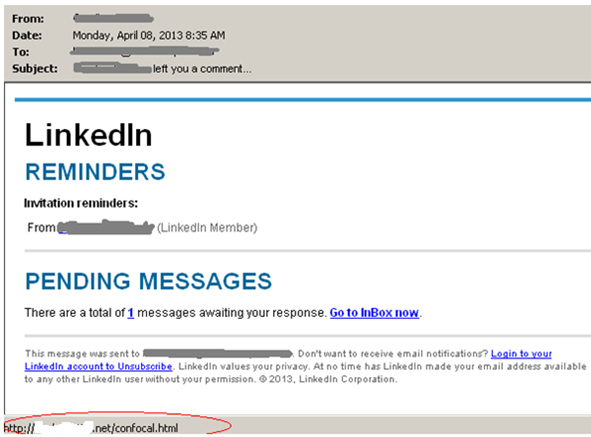
The links marked in red are actually the malicious links that have payloads embedded. Once a user clicks on it, game over!
The Blackhole kit is known to exploit zero day vulnerabilities recently reported like the CVE-2013-0431, CVE-2013-0422. The malicious payload downloads and executes JAVA_ARCAL.A (a Java Trojan) from a specific page after checking the Java version of the infected system. JAVA_ARCAL.A then downloads and executes TSPY_FAREIT.MEX by using command.exe in the PATH %user% in a specific URL. Similarly, for Adobe reader we have vulnerabilities like CVE-2010-0188, CVE-2009-0927, CVE-2009-4324 which are being exploited by the kit.

List of some vulnerabilities targetted by Blackhole Exploit kit
The Blackhole hosting sites move on rapidly changing domains quickly and freshly hosted domains are used to host the kit. A few of the domains hosting the Blackhole kit are:
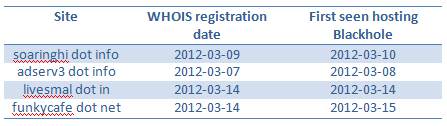
As expected, the lifetime of these domain names is very short and host names fail to resolve after around a period of 72 hours. This is due to a technique known as domain name flux, which is being used which allows the continuous allocating and updating multiple domain names to the same IP address. This has largely been placed as a URL filter evasion technique for bypassing firewall and intrusion detection systems. An example of flux used on Blackhole exploit kit IP is
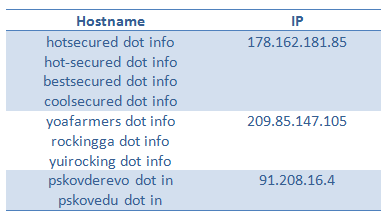
Domain Name Flux on Blackhole Exploit Kits
We also have cases of abuse for free domain registration services by Blackhole. Some examples here:
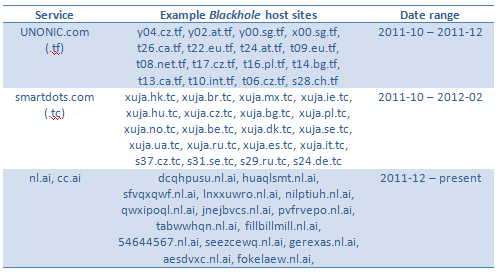
There has been recent news of legitimate sites being compromised and being used for hosting this exploit kit. The landing page is typically located in a folder named 'Home ' or 'Index' and additional files are stored within this folder. There is also a recent incident that happened with LA times as reported by KrebsOnSecurity where a sub-domain of LA Times (offersanddeals.latimes.com) was redirecting visitors to a malicious website hosting the Blackhole Exploit Kit. According to Alexa Rankings this particular sub-domain received around .12 percent of the total traffic which around is 18 million visitors per month. You may already have a picture as to how many visitors would have been redirected to the Blackhole exploit and being compromised. The issue was patched quickly as soon it was known to the LA Times security team but till that time the damage had been done.
Conclusion
We discovered a wide mechanism of how the Blackhole exploit kit actually functioned with in depth analysis of its attack vector. According to recent reports, a lot of traffic is being redirected to these Blackhole hosted servers. The bad guys have taken every step to keep the control to themselves and encode the code through private encoding schemes. They then offer these servers for rent to the criminals. The encoding prevents the bad guys from copy pasting the code and using it on their own. Given to the high standards of evasion there have been few weaknesses as well like the URL paths, filenames, query string structures. These parts of the Exploit Kit lack evasion and obfuscation.
Hence, in the past year or so, the Blackhole Exploit Kit was highly prevalent, and had the major number of system compromises. In the coming years, we may even witness distributed control over these kits. If there is legal intervention then it may shut down the centralized server for these Trojans, thereby stopping the effect. The best prevention techniques to protect users from getting infected is to properly patch software with updates, have updated antivirus systems installed, prevent the use of pirated software, never click unknown links, and have a general sense on security and its current trends.
References
http://nakedsecurity.sophos.com/2012/12/05/web-exploit-kits-whitehat/
http://blog.malwarebytes.org/intelligence/2013/02/tools-of-the-trade-exploit-kits/
http://www.symantec.com/connect/blogs/blackhole-theory
http://blogs.mcafee.com/mcafee-labs/blackhole-exploit-kit-spam-campaigns-disguised-as-top-service-brands
http://www.google.co.in/url?sa=t&rct=j&q=blackhole%20exploit%20kit%20mcafee&source=web&cd=3&cad=rja&ved=0CDoQFjAC&url=https%3A%2F%2Fkc.mcafee.com%2Fresources%2Fsites%2FMCAFEE%2Fcontent%2Flive%2FPRODUCT_DOCUMENTATION%2F23000%2FPD23826%2Fen_US%2FMcAfee_Labs_Threat_Advisory_Blackhole.pdf&ei=9opvUfv7G4KKrgeHr4DQCQ&usg=AFQjCNGFmtvQe_98Mj2q5t9kmmdpZ4H0AQ&bvm=bv.45368065,d.bmk
http://www.symantec.com/connect/blogs/blackhole-exploit-kit-takes-advantage-cypriot-financial-crisis
http://blog.trendmicro.com/trendlabs-security-intelligence/blackhole-exploit-kit-run-adopts-controversial-java-flaw/
http://nakedsecurity.sophos.com/exploring-the-blackhole-exploit-kit-15/
http://nakedsecurity.sophos.com/exploring-the-blackhole-exploit-kit-17/
http://nakedsecurity.sophos.com/exploring-the-blackhole-exploit-kit-19/
http://community.websense.com/blogs/securitylabs/pages/black-hole-exploit-kit.aspx
http://nakedsecurity.sophos.com/2012/12/05/web-exploit-kits-whitehat/
http://nakedsecurity.sophos.com/exploring-the-blackhole-exploit-kit-3/
http://nakedsecurity.sophos.com/exploring-the-blackhole-exploit-kit-5/
http://krebsonsecurity.com/2013/02/exploit-sat-on-la-times-website-for-6-weeks/#more-18881
http://krebsonsecurity.com/tag/blackhole-exploit-kit/










