Email forensics: desktop-based clients
Emails are the most commonly used technology for exchanging messages between people/businesses using electronic media. With every technology, there comes a risk. This medium of message exchange has been used the most by cybercriminals for manifesting different crimes. Hence email forensics plays a very important role in any cybercrime investigation. There are a lot of different providers who offer email clients eg: outlook, thunderbird etc.
Before getting into forensics, it's worth understanding some of the basic components of an email.
Mail User Agent (MUA): Mail User Agent, is the mail user agent which is used as a client-side application running on a computer for sending and receiving emails. Example: Microsoft Outlook, ThunderBird,
Mail Transfer Agent (MTA): Mail Transfer Agent accepts messages from a sender and routes it to the destination. Example of MTA is postfix, Sendmail , Microsoft exchange etc.
MUA communicates with MTA using different protocols like IMAP & POP3 to download the messages intended for the receiver. Use of IMAP over POP3 enables the message to be on the server so that the mailbox can be consistent across multiple devices.
Sender Policy Framework (SPF): Sender policy framework can be used by an organization to specify a server or a list of servers to send or receive the email on behalf of the domain. The information is published in the DNS as a txt record. If an email fails in SPF check it can be detected as spam.
You can use the below command to find the SPF record for any website.
> nslookup -type=txt google.com
Server: UnKnown
Address: 192.168.1.254
Non-authoritative answer:
google.com text = "v=spf1 include:_spf.google.com ~all"
google.com text ="docusign=05958488-4752-4ef2-95eb-aa7ba8a3bd0e"
google.com text ="facebook-domain-verification=22rm551cu4k0ab0bxsw536tlds4h95"
google.com text ="docusign=1b0a6754-49b1-4db5-8540-d2c12664b289"
google.com text = "globalsign-smime-dv=CDYX+XFHUw2wml6/Gb8+59BsH31KzUr6c1l2BPvqKX8="
Domain keys identified mail (DKIM): Domain keys identified mail provides a cryptographic method of verifying a received email, if it originated from the sending domain or not.
Now that we have understood some basic components of an email, let's get into the forensics part.
An introduction to outlook forensics:
Microsoft Outlook provides the capability to store all its email messages and attachments as a record in an encoded or compact format. The complete set of emails of a specific user gets saved in PST format(personal storage table)/Data file. This helps a user to retrieve all the deleted messages with the use of the “Deleted Item” folder. But if the malicious insider has performed “hard deletion” by deleting the emails from the PST file permanently, this will result in the forensic investigation scope.
So is it possible to extract the evidence from the PST file after hard deletion?
The outlook PST files reside in %AppData%\Local\Microsoft\Outlook location on the drive. If the PST file has been deleted recently and the memory location of the drive has not been overwritten then it is possible to retrieve the deleted PST files. In this scenario, the investigator first takes a full image of the entire hard disk in the dd (raw) format and tries to identify the memory location allotted to the PST file. Once identified they can retrieve the file by using tools to retrieve data from the specific memory locations. Microsoft provides an inbuilt tool to repair corrupt or inaccessible PST files called scanpst.
PST files can be password protected and one should recover the password first to be able to analyze the PST file. Passware is a tool that may help to achieve this.
What is OST?
Offline Storage Table (.ost file) is an offline Outlook data file that stores an offline copy of Outlook data item that exists on the server. OST file allows users to work even in the absence of the server connection. Users can edit the data, save emails in the draft, adding and deleting etcetera. Whenever the user works in the absence of the server, a carbon copy of the mailbox is created by MS Outlook and stored locally on the users’ system.
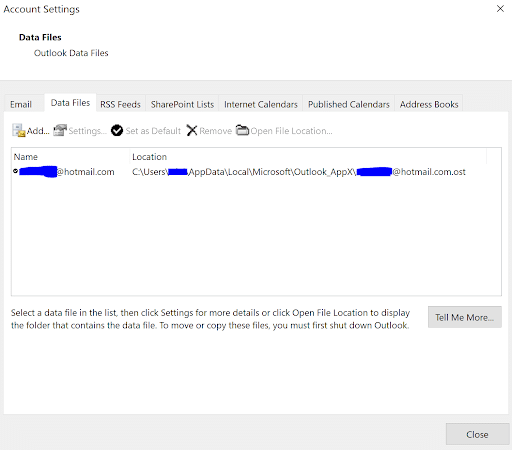
Navigating to File | Account Settings | Data Files will show the location of the OST file created by outlook. The following figure shows how to find the location of the OST file.
Even when users use desktop-based clients, it is possible that they receive fake emails and it is important to know how we can retrieve the raw email from these desktop clients for further analysis of the received email.
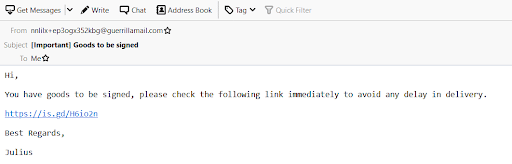
The following section shows this using Mozilla Thunderbird email client. Open the email to be analyzed and the following is the email in this case.
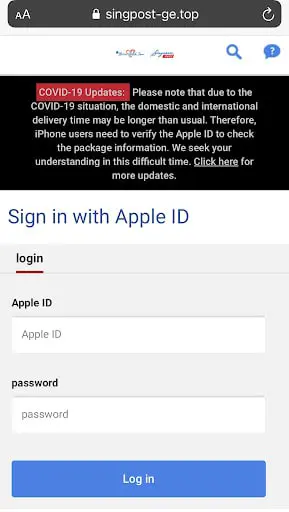
As we can see in the preceding figure, the source email doesn't look legit. In fact, guerrillamail.com is a website that allows anyone to send anonymous emails. The email also contains a short form link. Opening this link shows the following.
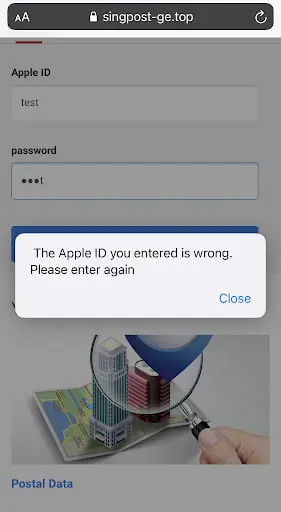
Clearly, the website looks like a phishing site as the URL is appearing fake with the word singpost in it and it is requesting apple credentials. Singpost is Singapore's postal service and the official website’s URL is different from what is shown in the preceding figure. Once if the user enters any credentials, he will be greeted with the following message.
At this point, the user won't be navigated anywhere and needs to close the browser.
To be able to view the raw email, we can navigate to More | View Source as shown in the following figure.
Once the email has been retrieved this can be used for further analysis to trace the sender using the email headers. The following is an excerpt from the raw email retrieved.
Delivered-To: receiver@gmail.com
Received: by 2002:a4a:c544:0:0:0:0:0 with SMTP id j4csp3885249ooq;
Sun, 31 Jan 2021 20:35:10 -0800 (PST)
X-Received: by 2002:a05:600c:2a4b:: with SMTP id x11mr12960093wme.58.1612154110309;
Sun, 31 Jan 2021 20:35:10 -0800 (PST)
X-Google-Smtp-Source: ABdhPJyhbQFn9Ctv2EPrpFbP4iNJS4aNI14fqa6lBpfEJMVVwyTQZp2OC4YzxElWAjA0KqOeN6cM
X-Received: by 2002:a05:600c:2a4b:: with SMTP id x11mr12960035wme.58.1612154108930;
Sun, 31 Jan 2021 20:35:08 -0800 (PST)
ARC-Seal: i=1; a=rsa-sha256; t=1612154108; cv=none;
d=google.com; s=arc-20160816;
.
.
.
.
Authentication-Results: mx.google.com;
dkim=pass header.i=@guerrillamail.com header.s=highgrade header.b=cmFJcdA2;
spf=pass (google.com: domain of nnlilx+ep3ogx352kbg@guerrillamail.com designates 2a01:4f8:251:657::2 as permitted sender) smtp.mailfrom=nnlilx+ep3ogx352kbg@guerrillamail.com;
dmarc=pass (p=REJECT sp=REJECT dis=NONE) header.from=guerrillamail.com
Received: by 168.119.142.36 with HTTP; Mon, 01 Feb 2021 04:35:07 +0000
MIME-Version: 1.0
Message-ID: <75a7e317b8633f7e5b86bc7b9dc8b6ab014@guerrillamail.com>
Date: Mon, 01 Feb 2021 04:35:07 +0000
To: "receiver@gmail.com" <receiver@gmail.com>
From: <nnlilx+ep3ogx352kbg@guerrillamail.com>
Subject: [Important] Goods to be signed
X-Originating-IP: [219.75.35.74]
Content-Type: text/plain; charset="utf-8"
Content-Transfer-Encoding: quoted-printable
X-Domain-Signer: PHP mailDomainSigner 0.2-20110415 <http://code.google.com/p/php-mail-domain-signer/>
DKIM-Signature: v=1; a=rsa-sha256; s=highgrade; d=guerrillamail.com; l=344;
.
.
Hi,=0A=0AYou have goods to be signed, please check the following link immed=
iately to avoid any delay in delivery.=0A=0Ahttps://is.gd/H6io2n=0A=0ABest =
Regards,=0A=0AJulius=0A=0A=0A=0A=0A=0A----=0A
The headers can be investigated for the authenticity of the message in case the email appears to have come from a different source than what it claims to be. In this case, the email has originally originated from nnlilx+ep3ogx352kbg@guerrillamail.com and the from address shows the same. The fact that the sender cannot be identified and the link leads to a phishing site concludes that the user has received a malicious email and credentials might have been compromised if he/she entered any credentials by clicking the link.
Sources