Mobile forensics: Investigation process model
From the newly-published Mastering Mobile Forensics by Soufiane Tahiri.
Smartphone forensic is relatively new and quickly emerging field of interest within the digital forensic community and law enforcement, today's mobile devices are getting smarter, cheaper and more easily available for common daily use.
Mobile forensic is a set of scientific methodologies with the goal of extracting digital evidence (in general) in a legal context, extracting digital evidence means recovering, gathering and analyzing data stored within the internal memory of a mobile phone. Mobile forensic is a continuously evolving science which involves permanent evolving techniques and presents a real challenge to forensic community and law enforcement due to the fast and unstoppable change of technology.
To investigate the growing number of digital crimes and complaints, researchers put lot of efforts to bring the most affordable investigative model; in this chapter we will put the point on the importance of paying real attention to the growing market of smartphones and the efforts hold in this way from a digital forensic point of view in order to bring the most comprehensive investigation process.
This chapter will be also oriented toward the importance of smartphone forensics in our continuously growing digital world then will describe some smartphone forensic models and how they evolved through history, we will as well be pointing out challenges that face today's investigators in smartphone forensics evidence acquisition process.
Why mobile forensics?
The promptly evolving mobile phone industry reaches some unimaginable peak and smartphones will definitely replace computers for lot of people since those tiny devices are becoming as powerful as personal computers.
On a daily basis use, each smartphone is a huge repository of sensitive data related to its owner. Nowadays, smartphones are used to do almost any task we need to do, starting from "traditional" tasks involving sending and receiving calls, short text messages, and emails to more complex ones like geolocation, balance checking, making bank transaction, and managing tasks and reminders. Given the pace at which development progress, needs of forensic examination does as well. Data contained within modern devices is continuously becoming more riche and more relevant, which is in part due to the exploding growth and use of mobile application and social networks. In addition to this, all mobile phones are now capable of storing all kind of personal information and usually even unintentionally.
According to ABI Research (https://www.abiresearch.com/market-research/product/1004938-smartphone-technologies-and-markets/) (a technology market intelligence company), at the time of publishing this book there is more than 1.4 billion smartphone that will be in use, more than 798 million of them are under Android, more than 294 million are running Apple's iOS and more than 45 million are running Windows Phone, which represents a growth rate of 44% for 2013 according to the same source.
Cisco says in its report (http://www.cisco.com/c/en/us/solutions/collateral/service-provider/visual-networking-index-vni/white_paper_c11-520862.html ) that an average smartphone user will make 5 video calls and download 15 applications each month.
If we refer to data given by Nielsen Informate Mobile Insights (http://www.nielsen.com/us/en/insights/news/2014/smartphones-so-many-apps--so-much-time.html
) and given only US Android and iPhone users spend 30 hours, 15 minutes using apps on their smartphones in Q4 213 and this amount of time is not decreasing as shown in the chart below:
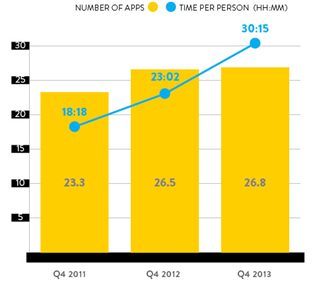
Figure 1 - In the Q4 2013, users used 28.8 applications and spent 30 hours, 15 minutes on them.
All this advancement has lot of benefits for sure, but with no doubt it represents new challenges to law enforcements, since the growth of cybercrimes and digital complaints evolve proportionally, this was raised by the Federal Bureau of Investigation (FBI) and the Internet Crime Complain Center (http://www.ic3.gov/media/annualreport/2014_IC3Report.pdf). In 2014, the total complaints received is 269,244 and all statistics are pretty huge as shown below
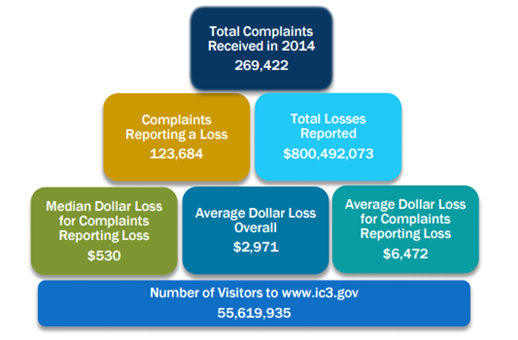
Figure 2 - Total digital complaints and digital complaints loss as given by the FBI Internet Crime Complaint Center
So why is mobile forensics important? Simply because acquiring a smartphone means acquiring a person's everyday life in term of data, and some proactive acquisition approaches are gaining place in a crime context and not only after a crime, but also when people violate in place regulations and laws as for preventing terrorist attempts, crimes against states and pedophilia.
Today's smartphones can contain all kind of evidences stored as heterogeneous data generated from the hardware and the software constituting the device, categorizing these data is quit important in order to produce some kind of evidence classification and only a well driven mobile forensic approach can help to make the correct correlation between data , data type and evidence type. (Refer to Chapter 7: [Mobile forensics – The best practices] for more details)
The importance of mobile forensics is established and cannot be deniable in our information age where every single byte matter.
Smartphone forensics models
Given the pace at which mobile technology grows and the variety of complexities produced by today's mobile data, forensics examiners face serious adaptation problem, developing and adopting standards makes sense.
Reliability of evidence depends directly on adopted investigative processes, choosing to bypass or bypassing accidentally a step may (and will certainly) lead to incomplete evidence and increase the risk of rejecting them in the court of law.
Today, there is no standard or unified model adapted to acquiring evidences from smartphones. The dramatic development of Smart devices suggests that any forensic examiner will have to apply as many independent models as necessary in order to collect and preserve data. There is a pretty big number of proposed forensic models and reviewing every of them will be a colossal task; in the following paragraphs I'll be presenting some of them without pretending that the selected models are the best. The following models are sorted chronologically starting from the earliest model established.
Computer forensic investigation process
Historically and back to 1984, the FBI and many other law enforcement agencies began modeling the examination of digital evidence based on early versions of computers and the first digital forensic process model was Computer Forensic Investigation Process (CFIP) presented in 1995 by M. M. Pollitt (M. M. Pollitt, (1995) "Computer Forensics: An Approach to Evidence in Cyberspace"), this first model focuses exclusively in the result, in other words the model focuses principally in data acquisition and how reliable and legally accepted this data is.
Computer Forensic Investigation Process model is conducted in 4 stages:

Figure 3 - CFIP model
Acquisition is a technical problem which is not free from the legal aspect, and data acquired must answer 3 main questions: what can be sized, from whom and from where it maybe sized. This means that digital evidence must be acquired in acceptable manner with necessary approval from concerned authorities. This stage is followed by Identification phase, as in this model, this phase is subdivided in 3 step process: defining the physical form of data, defining data logical position then placing this data (evidence) in its correct context. Digital evidence follows the path below:
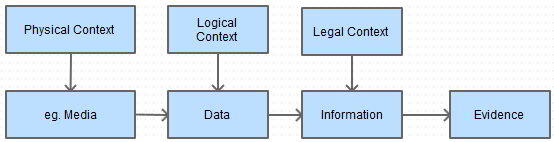
Figure 4 - Digital evidence Identification process
The Evaluation stage consists on placing the gathered data in its proper context and this is as legal as technical task, meaning that at this point of the forensic process we can determine either the acquired information is relevant and can be described as legitimate evidence in the case being investigated or not. Finally Admitting the extracted data as legal evidence and presenting it the court of law.
Digital forensic research workshop
In 2001, the first Digital Forensic Research Workshop (DFRWS) (http://www.dfrws.org/2001/dfrws-rm-final.pdf ) this workshop effort was held to produce and define a scientific methodology to drive digital forensic to produce a reliable Framework (dubbed Investigative Process for Digital Forensic Science) to drive the majority of digital investigation cases, the result was a 6 stages linear process. Each step or stage is defined as category or class and each class are candidate methods belonging to that category.
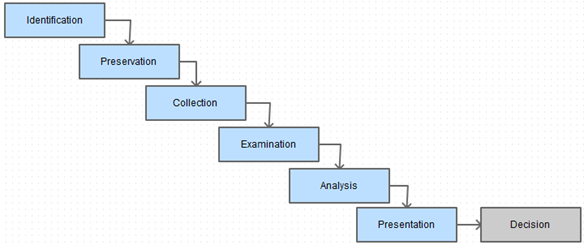
Figure 5 - Investigative Process for Digital Forensic Science (DFRWS)
As seen in figure above, DFRWS model starts with the Identification stage, which is subdivided to tasks like event detection, signature resolving, profile detection, anomalous detection, complaints, system monitoring and audit analysis; This stage is followed by Preservation which is candidate to 4 tasks that are setting up a case management, managing technologies, ensuring a chain of custody and time synchronization. Collection comes next as the third phase in which data is collected according to approved methods, using approved software / hardware and under legal authority; this phase is also based on lossless compression, sampling, data reduction and data recovery techniques. After collection, comes Examination directly followed by Analysis phases where very important tasks are performed and evidence are traced, validated and filtered. Data mining, timeline analyses are done as well. At this stage hidden and encrypted data is discovered and extracted. The stage that comes after is Presentation in which documentation, clarification, expert testimony, mission impact statement and recommended countermeasure are presented. However, this model is open to criticism regarding the use of stages collection and preservation and if one is an actual subcategory of the other.
Abstract digital forensics model
Being a more generic framework, DFRWS inspires researchers at US Air Force in 2002 to present the Abstract Model of the Digital Forensic Process (M. Reith, C. Carr & G. Gunsh, (2002) "An Examination of Digital Forensics Models") (or Abstract Digital Forensics Model – ADFM) which is meant to be an enhanced DFRWS model by adding three more stages to the existing process: Preparation, Approach Strategy, and Returning Evidence leading to a nine phases:
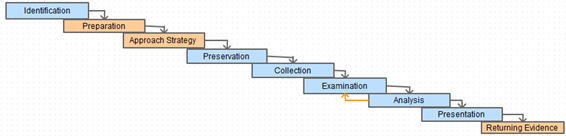
Figure 6 - Abstract Digital Forensics Model
The actual added value of this model is the introduction of pre/post-investigation approaches, meaning that before any exercise and after Identifying type of the incident Preparing tools, techniques and searching warrants and securing management support, followed by the Approach Strategy which is meant to dynamically establish an approach to collect the maximum amount of evidence without impacting the victim, however this phase is criticized for being a duplication of the second stage since preparing to respond to an incident will likely ends on preparing an "approach strategy". Lastly Returning Evidence shows the importance to safely store evidence removed from the scene in order to return them back to the owner.
The Abstract Digital Forensics Model ignored the importance of chain of custody but authors of this model assume that a chain of custody is obviously maintained trough any investigation process and is implied in any forensics model.
Integrated digital investigation process
In 2003, Carrier, B., & Spafford, E. H (Carrier, B., & Spafford, E. H. (2003). Getting Physical with the Digital Investigation Process. International Journal of Digital Evidence) introduced an Integrated Digital Investigation Process (IDIP) which is an integration of digital forensic to physical investigation, it's a framework based on available processes of physical crime scene investigation.
The main idea of this model is considering a digital crime scene as a "virtual crime scene" and applies adapted crime scene investigation techniques. This model is macroscopically composed of 5 stages consisting microscopically in 17 stages.
The figure bellow shows the 5 macroscopic stage of IDIP model:
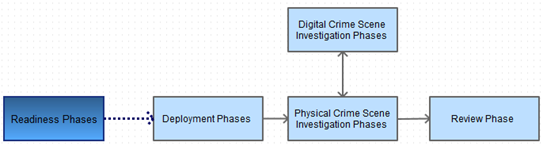
Figure 7 - The five macroscopic stage of IDIP model
Physical and Digital crime scenes are processed together and digital forensics are fed into physical investigation.
The Readiness Phases ensure that human competences and technical infrastructures are able to fully carry the whole investigation process; this stage is subdivided to two phases:
Operation Readiness: involves the preparation of adequate training and equipment for the personnel that will investigate the crime scene.
Infrastructure Readiness: this phase aims to ensure data stability and integrity as long as investigation process takes, this phase may include for example hashing files, securely storing evidence and maintaining a change management database
The first stage is followed by Deployment phases, the goal of this stage is to provide a mechanism to detect and confirm an incident, and this stage is also subdivided to two phases:
Detection and notification: concretely, this phase triggers the start of the investigation process where incident is detected and appropriate people are notified.
Confirmation and Authorization: once a crime or incident is confirmed, at this phase authorization must be received to fully investigate the-digital- crime scene.
Physical Crime Scene Investigation phases which come after are when the investigation itself begins with the goal of collecting and analyzing the physical evidence to reconstruct actions that firstly took place. This stage is subdivided to 6 phases that are typical to real cases post-physical crime investigation process and described in the figure below:
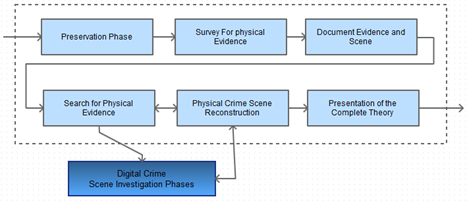
Figure 8 - Physical Crime Scene Investigation
This stage is followed by a quite similar one but in a digital context focusing on digital evidence within a "virtual" digital environment, the Digital Crime Scene Investigation Phases follow the same previously presented path considering any smartphone (or other digital device) a separate crime scene:
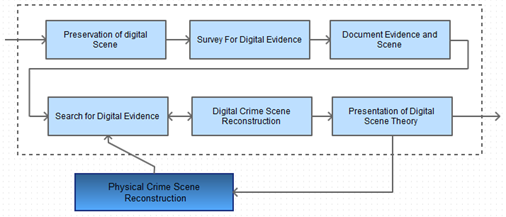
Figure 9 - Digital Crime Scene Investigation
Preservation: at this phase, the investigator must pay intention to keeping data integrity, meaning at this level, the digital scene must be secured in order to avoid any external interference that could alter evidence.
Survey for Digital Evidence: depending on the case being investigated this phase aims to collect the obvious evidence related to that case, and should be occur in a controlled environment (Forensic Lab for instance) using a replica of the original crime scene.
Document Evidence and Scene: the documentation phase involves documenting every acquired evidence during the conducted analysis, using cryptographic hashing techniques like MD5 or SHA-1 Is recommended to keep trace of evidence integrity. This phase does not substitute the final forensic report.
Search for Digital Evidence: the collection phase involves a deeper digging and more in-depth analysis of what was found in the previous phase and focuses on more specific and low-level analysis of the digital device activities. Deleted file recovering, file carving, reverse engineering and encrypted file analysis are some examples of techniques that could be applied at this stage.
Digital Crime Scene Reconstruction: all digital evidences acquired are put together in order to define at what point we can trust or reject collected evidence and to determine if further analysis is required and Search for Digital Evidence should be resumed in the case of missing parts of the hole puzzle.
Presentation of Digital Scene Theory: this phase documents and presents the findings to the physical investigation team in the case the investigation was not performed by the same team.
The final stage of the whole model is Review Phase is a kind of self-criticism in which the whole process is reviewed to determine how well the investigation process went right or wrong and to detect improvement points.
This model presents many similarities with previously presented models and can easily be considered as an enhanced model of the both, nevertheless IDIP model is way too abstract and the interaction between physical and digital investigations may be in many cases not applicable.
End-to-end digital investigation process
By the same year, that is, 2003, Peter Stephenson (Stephenson, P. (2003). A Comprehensive Approach to Digital Incident Investigation.) reviews the DFRWS framework and translated it into a "more" practical investigative process dubbed End-To-End Digital Investigation process (EEDI) by extending the existing process into nine stages; End-to-end because Stephenson in his model considers that "every digital crime has a source point, a destination point and a path between those two points".
The model itself is schematized as follow:

Figure 10 - The basic End-to-End Digital Investigation process
EEDI can be considered as a layer applied to the DFRWS model, depending on cases the whole EEDI process is applied to each class of the DRFWS model (Figure 5). This model defines critical steps to do in order to correctly preserve, collect and analyze digital evidence. In the phase Collection of Evidence,
primary and secondary evidences are collected and taken in their respective contexts. The context here is more related to events time sensitivity, which brings us to the second step of this process, Analysis of Individual events, each individual event is isolated and analyzed separately to determine how it can tie with other events and the potential value it can add or they can add to the overall investigation. This is followed by Preliminary Correlation step in which individual events are linked with each other to determinate a primary chain of evidence in order to determine what happened, when, and which devices was involved.
Event Normalization is a step that mainly aims to remove redundancy in evidentiary data assuming that the same events could be reported separately from different sources using multiple vocabularies. As an extension to the normalization, whatever how and from where they was reported, the same evidentiary events are combined into one evidentiary event in the Event Deconfliction step; at this stage all events and evidentiary events are refined and a Second-Level Correlation can be performed. The previously outlined steps result in timeline which is defined in the Timeline Analysis step, the timeline analysis is an iterative task which lasts as the investigation lasts. The Construction of a Chain of Evidence can begin based on the result of timeline of events, theoretically, a coherent chain is developed when each evident will lead to the other and this is what is meant to be done in this step. The last phase of this model is Corroboration, where digital investigator support, strengthen and confirm each evidence, within the chain of evidence previously developed ,with other independent or traditional events and evidence collected in the case of conducted digital forensic investigation is in support of a group of investigators outside the digital forensic unit.
Systemic digital forensic investigation
In 2004, 4 models were developed: Enhanced Integrated Digital Investigation Process, invented by Baryamureeba & Tushabe and contains 21 phases; Séamus Ó Ciardhuáin presented an Extended Model of Cybercrime Investigation with 13 activities to follow; followed by a 6 phases Hierarchical, Objective-based Framework that was invented by Beebe & Clark. The same year, Carrier & Spafford announced the Event-based Digital Forensic Investigation Framework and detailed 16 phases to follow.
Approximately, each year at least one more forensic model is developed and regarding the pace at which the digital world rises, researchers keep on trying to give birth to "the perfect" forensic model.
Considering space allocated to this chapter, I jump directly to 2011; A. Agarwal, M. Gupta, S. Gupta, and S. C. Gupta came up with Systemic Digital Forensic Investigation (SRDIFM) model (A. Agarwal, M. Gupta, S. Gupta, and S. C. Gupta, "Systematic digital forensic investigation model,"). This model as most of previously presented models has common phases and some specific phases adapted to the model requirement. SRDIFM is composed by 11 phases: Preparation, Securing the scene, Survey and Recognition, Documentation of the Scene, Shielding, Volatile and Non-volatile evidence Collection, Preservation, Examination, Analysis, Presentation, Result and Review.
The figure bellow schematizes the model:
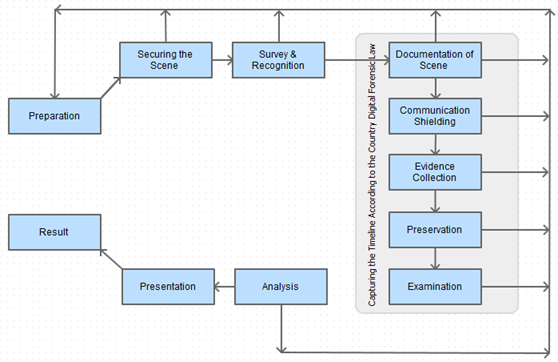
Figure 11 - Phases of Systematic Digital Forensic Investigation Model (SRDFIM)
The first step of this model is Preparation, its prior the process of investigation, and involves obtaining prior legal authorization, an initial understanding of the case that will be investigated in order to prepare the adequate human and technical resources before going any further in the process of investigation. It's followed by Securing the Scene phase; this phase aims principally to keep data integrity intact and to minimize as much as possible data corruption. The Survey and Recognition phase comprises of tasks to elaborate an initial plan for collecting and analyzing evidences, potential sources of evidences must be identified even sources other than the main Smart device itself, for example the presence of a personal computer in the scene means that there are chances to find smartphone related data synchronized with it. The next phase is known as Documenting the Scene, in which a kind of crime-scene mapping is done, every electronic device within the scene must be documented; the device itself, its power adaptor, external memory cards, cradle… everything related to the device must be documented too. Before starting evidence collection, Communication Shielding is important in order to be sure there is no risk to damage current evidence, RF isolation, Faraday Shielding or Cellular Jammers are usually used to isolate devices from interacting with environment. Evidence Collection comes after; differentiating volatile and non-volatile collection is important and requires proper guidelines, at this phase for example investigators must maintain the device turned on if it's running out of battery otherwise imaging the device memory must be done quickly and properly using appropriate tools. Next is Preservation phase, whereby, evidence is securely stored, device is properly packaged and transported. The collected evidences are analyzed and filtered; the integrity of data must be guaranteed too and the use of hashing function to confirm this is conducted in Examination step. The Analysis phase comes just after to be a kind of examination extension, in this phase more technical review is conducted based on the result of the previous phase, at this stage more advanced researches are done such as hidden data analysis, data recovery and file decryption. The result of this phase must be documented to help in the achievement of the final reports that will summarize the whole process in the Presentation phase. Finally, the Result and Review just like in IDIP model, this phase is meant to be an open door to review the result of the whole process in order to find point of improvements.
The SRDIFM model is interesting as it's more practical and presents some flexibility not necessarily found within other models, however, by adding more phases, the model increases the timeline of the process and its complexities.
Smartphone forensics challenges
Unlike traditional computer forensics investigation, mobile forensics skills become much solicited in today's investigations because of many facts that make gathering digital evidence from a smartphone a more painful task due to the great changeability of mobile based operating systems, the diversity of standards, technology of data storage and procedures of data protection; In contrast to computers investigation, mobiles investigation can hardly be standardized and each (or almost) single device model and according to services it makes available to its owner, a quite big range of evidence categories is distinguished in mobile forensic.
Storage and the wide range of daily growing functionalities make today's smartphones a rapidly changing and challenging environment to forensic investigators.
The most challenging aspects of smartphone forensics are discussed in the following sections.
Operating systems variety and changeability
In contrast to computers, major smartphone operating systems can vary significantly from a smartphone to another, each Android, iOS, WP, Blackberry version might be found in any of the wide range of types of smartphones and tablets in the market. Operating System updates are very frequent among vendors and major updates are usually released every quarter. The main issue regarding this is keeping with pace at which this environment changes thing accentuated by the fact that major OS and forensic tools developers consider their respective development trade secret and do not release information regarding the low level working of their codes.
In addition to this, the growth of "less common" operating systems like Windows Phone requires lot of forensic experience.
Important hardware variations
By definition a smartphone is a portable device and is meant to have a wide set of functionalities, the hardware architecture of smartphones is significantly different from computers and most important from mobile manufacturer to another.
Smartphone device is typically composed by microprocessor, main board, RO and RA memories, touch screen and or keyboard, radio module and/or antenna, a display unit, microphone and speakers, digital camera, GPS device ; the operating system is stored in general in a Read Only Memory and can be flashed or updated according to hardware or operating system.
The same manufacturer usually produces highly customized operating systems to fit hardware specification. Depending on phone providers, manufacturers may customise even the same device to suit the demand. The replacement cycle for smartphone and customer's smartphone upgrades, forensic examiners must have hundreds of adapters and power cords based on the type of hardware.
Different file systems
Different Operating Systems and different hardware mean different way of storing data and running different file systems. The same application running under Android for example is way different from its similar application running under iOS.
A variety of file format and data structure is adopted depending on the manufacturer, this fact complicate significantly decoding, parsing and carving information.
This difference in file systems means that forensic tools are not able to process some files and must be kept to date very frequently in order to assume OS updates otherwise forensic examiners must process data and device images manually.
Built-in security
Smartphone built-in security features are present at many levels in order to protect user data and privacy. User locks in today's smartphones can vary from simple four-digit PINs to more complex and long passcodes as it may consist on pattern-locks, newest smartphone models can even be fingerprint-locked and uses biometrics to identify user, it's true that some commercially available tools offer password extraction or lock screens bypass, but this is fare from covering every device. Some smartphone (with or without the help of third party applications) can offer individual file, file type or directory password protection, in this case sensitive data as SMS, Emails and photos can be individually protected. Newer OS versions offer full-disk encryption which can be a real pain to decrypt in a scenario of data acquisition. Smartphone operating systems offer also application sandboxing, meaning that every individual application cannot directly access space allocated to another application or to system resources, thus each application is installed in its own sandbox directory this way data within this up is guaranteed some level of protection.
Encrypted data wiping
Data wiping is not data deletion, wiped data cannot be recovered or can be recovered with difficulties. Encrypted data can be wiped with a variety of methods, depending on smartphone configuration; data can be wiped via desktop managers or after entering a wrong password for predefined times. Encrypted data can be wiped remotely in most of modern smartphone, Blackberry devices can be remotely wiped via BlackBerry Enterprise Server, and iPhone devices via iCloud, Android devices can be wiped via Google Sync. and Windows Phone devices via Find My Phone service. At this point the isolation phase of mobile forensic is important.
Data volatility
Lot of important evidentiary data resides within a smartphone in a volatile way, which adds an important consideration while seizing a device. Smartphones add this constraint to forensic examiners; seized devices must be kept turned on and isolated to prevent data loss or overwriting present data.
The cloud
For the sake of memory, storage space saving or for back-up purpose, today's devices store lot of important data in the cloud, emails, photos, videos, files, notes... are not necessarily preserved within device internal memory, especially relatively old data.
Most vendors offer some gigabytes free of charge in order to achieve this, and data is in most of case automatically synchronized with some account in the cloud, Android data is sent to Google, iPhone data is sent to iCloud and Windows Phone data is synchronized with OneDrive. In addition to this some third party services are also offered to certain point free of charge just like Dropbox. In some cases, gathering evidence is not necessarily a technical task but also and above all a legal one in so far as demands must be addressed to cloud storage services to receive desired data.
Today's climbing necessity of advanced smartphone forensic skills is indisputable; smartphone investigation becomes more challenging, tools are rapidly outdated and the scope they cover is in each time smaller. Analysis, coding, and low level techniques understanding and handling are now a "must have" skills for today's smartphone investigators and are more important nowadays than ever.
Summary
There are a huge number of mobile device models in use today, and almost every five months new models are manufactured and most of them use closed operating systems making forensic process much harder. Our goal is to bridge the gap by giving to forensic community an in-depth sight at mobile forensics techniques by detailing methods on how to gather evidences from mobile devices with different operating systems and using appropriate model.
Seen the daily increasing use of smartphone, the unwilling-to-stop development of today's smartphone capabilities and giving the pace at which this development occurs, forensics professionals, law enforcement and researchers was and are still in need of producing a standardized framework to follow in order to assure a well driven investigation, researches in this scope are not yet done thus improvement are continually done to keep responding to permanent challenges offered by smartphone manufacturers and mobile operating systems vendors.In this chapter we showed the importance of smartphone forensic field and discussed some models and frameworks applied in order to correctly lead forensic investigation cases, this chapter discussed also major smartphone forensic challenges; In an effort to help bypassing some of the previously presented challenges at it happens when commercially available forensic tools cannot deal with some files or some file types, in next chapter we will see some low level techniques that can be applied to gather forensically important evidences independently of available forensics tools, operating system or device subjects to the eventual investigation.










