Network Forensics Tools
Various tools are available for Network forensics to investigate network attacks. In this article, we will discuss tools that are available for free. First, we will begin by understanding how we can use tcpdump and Wireshark to capture and analyze network traffic. We will then discuss a tool called Network Miner. Finally, we will discuss Snort, which acts as an IDS and Splunk which is a popular network traffic indexing and analysis tool.
Learn Network Forensics
Network Forensics Tools
In this section, let us go through the Network Forensics tools mentioned earlier.
tcpdump
Tcpdump is a popular command line tool available for capturing and analyzing network traffic primarily on Unix based systems. Using tcpdump, we can capture the traffic and store the results in a file that is compatible with tools like Wireshark for further analysis. Tcpdump can either be used to do a quick packet capture for troubleshooting or for capturing traffic continuously in large volumes for future analysis. It is worth noting that tcpdump can be used to capture both layer 2 and layer 3 data. The latter may cause disk space problems as the size of the resulting capture file can grow depending on the volume of the network traffic. In addition to the ability to capture large amounts of traffic, tcpdump also supports the use of filters to avoid capturing unnecessary traffic or to capture only the traffic we are interested in. One should be extra cautious with this feature, as applying filters can lead to missing potential evidence. So, it is recommended to capture as much traffic as possible and filter out the unnecessary traffic during analysis later.
The following excerpt shows the help output of tcpdump command line tool.
tcpdump version 4.9.3
libpcap version 1.9.1 (with TPACKET_V3)
OpenSSL 1.1.1g 21 Apr 2020
Usage: tcpdump [-aAbdDefhHIJKlLnNOpqStuUvxX#] [ -B size ] [ -c count ]
[ -C file_size ] [ -E algo:secret ] [ -F file ] [ -G seconds ]
[ -i interface ] [ -j tstamptype ] [ -M secret ] [ --number ]
[ -Q in|out|inout ]
[ -r file ] [ -s snaplen ] [ --time-stamp-precision precision ]
[ --immediate-mode ] [ -T type ] [ --version ] [ -V file ]
[ -w file ] [ -W filecount ] [ -y datalinktype ] [ -z postrotate-command ]
[ -Z user ] [ expression ]
Following is the simplest tcpdump command to capture packets on a specific interface (eth0 in this case) and write them to a file named packet.pcap
The packets saved can then be used for further analysis using tools like Wireshark or NetworkMiner.
Wireshark
It would be a surprise if someone worked in the Cyber Security field and not heard of the tool Wireshark. Wireshark is an open-source tool available for capturing and analyzing traffic with support for applying filters using the graphical user interface. On the system, where Wireshark is running one can choose the interface on which traffic needs to be captured.
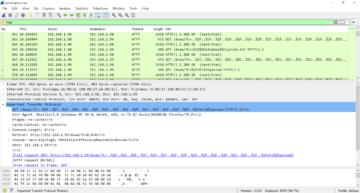
The following figure shows a sample of Wireshark with the packets captured by tcpdump.
Network Miner
According to the official website netresec.com, “NetworkMiner is an open source Network Forensic Analysis Tool (NFAT) for Windows (but also works in Linux / Mac OS X / FreeBSD). NetworkMiner can be used as a passive network sniffer/packet capturing tool in order to detect operating systems, sessions, hostnames, open ports etc. without putting any traffic on the network. NetworkMiner can also parse PCAP files for off-line analysis and to regenerate/reassemble transmitted files and certificates from PCAP files.
NetworkMiner makes it easy to perform advanced Network Traffic Analysis (NTA) by providing extracted artifacts in an intuitive user interface. The way data is presented not only makes the analysis simpler, it also saves valuable time for the analyst or forensic investigator.
NetworkMiner has, since the first release in 2007, become a popular tool among incident response teams as well as law enforcement. NetworkMiner is today used by companies and organizations all over the world”.
NetworkMiner also comes as a professional version.
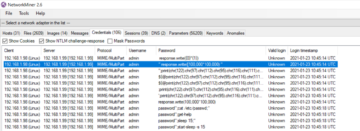
The following figure shows Network Miner being used on Windows to analyse a packet capture.
Splunk
Splunk is a proprietary, portable, highly extensible log aggregation and analysis tool. Splunk performs capturing, indexing, and correlating the real time data in a searchable container and produces graphs, alerts, dashboards and visualizations. When it comes to network forensics, splunk plays a crucial role in providing evidence from various sources. While Splunk is a popular commercial tool, a free version is offered with limited features. It comes with an easy to use Graphical User Interface.
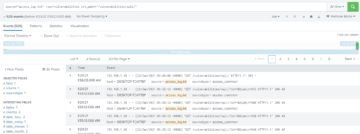
The following figure shows a sample search result of web access logs from Splunk.
Snort
Snort is one of the most popular network Intrusion Detection Systems available for free. There is a commercial version of Snort available, which is currently offered by Cisco. Snort is highly configurable, which allows the users to add custom plugins called preprocessors. In addition to it, it comes with a great set of output options. At its core, Snort provides alerts based on rulesets provided to it. The Snort administrator needs to feed the rules as the default installation doesn't come with any rules by default. However, Snort website provides rulesets that can be fed into Snort. In addition to these rules, one can write custom alert rules.
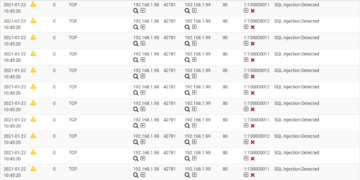
The following figure shows a sample alert from Snort, which shows that there is an SQL Injection attempt.
Learn Network Forensics
Conclusion
Network forensic investigations revolve around evidence collection, indexing and analysis. Investigators must rely on good tools that can extract the evidence and assist in analysis. This article has provided a short list of tools that can come handy in network forensics.
Sources
- Network Forensics by Ric Messier - https://www.amazon.com/Network-Forensics-Ric-Messier/dp/1119328284
- Internet Forensics by R Jones - https://www.amazon.com/Internet-Forensics-Digital-Evidence-Computer/dp/059610006X
- Network Forensics by Sheriff Davidoff, Jonathan Ham - https://www.amazon.com/Network-Forensics-Tracking-Hackers-Cyberspace/dp/0132564718