SANS investigate forensics toolkit—Forensics martial arts part 1
The SANS Investigate Forensic Toolkit (SIFT) is an interesting tool created by the SANS Forensic Team and is available publicly and freely for the whole community. It comes with a set of preconfigured tools to perform computer forensic digital investigations. This is based on Ubuntu and has a long list of tools for present forensic needs. We will have a walkthrough of some of the very famous tools used in forensic investigations.
You can download the SIFT iso from this link:
http://computer-forensics.sans.org/community/downloads
It supports evidence formats such as raw format (.dd), encase image file format (E01), and advanced forensics format (AFF).
Setup
There are a few things that you might need for booting this up, such as:
You can simply boot the SIFT iso as a bootable disk or choose to install it as a complete operating system. The default login credentials are: username—sansforensics and password—forensics.
This includes a long list of software, a few of which we would cover with a complete tutorial based on forensic analysis, such as:
- Autopsy
- DFF – Digital Forensic Framework
- EVTX – Event Log Viewer
- Maltego
- PTK
- Md5deep
- SANS Cheatsheets
- Volatility
We will start with the forensic analysis tutorials with this tools from SIFT. Currently I have with me a raw dd image for our forensic analysis:
Md5deep
This is a small command line utility in SIFT that may be used for calculating MD5 hashes, comparing hashes, and playing around with them. Suppose we want to check if the integrity of our file is maintained: We can simply hash it and check. Any changes made to the file will change its MD5 hash. So let's calculate an MD5 for our image file before doing the forensic analysis. You can see the MD5 calculated in the screenshot by our tool:
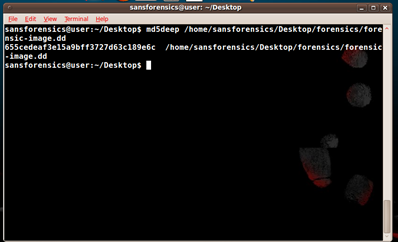
Similarly, we can calculate MD5 for recursive files and play with many more options. For more information and usage, simply use man md5deep. We similarly have utilities such as sha1deep and sha256deep for calculating sha1 and sha256 hashes for integrity checking.
Autopsy
Now we move to the actual analysis of our image using Autopsy. This tool is the GUI front end for the Sleuthkit. Let us have a look. It is found under Applications > Forensics
This what Autopsy looks like:
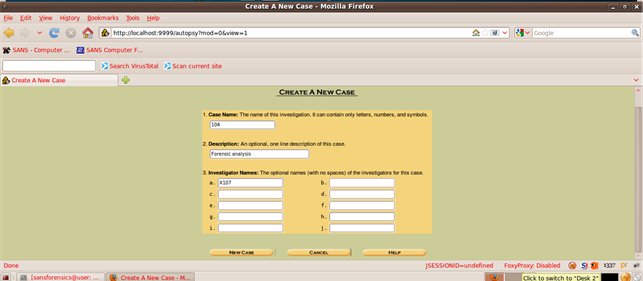
Let us open a new case by clicking "New Case." We have to fill in a few details to create a new forensic investigation case.
We have successfully created a new case; let us move on to the next step. We add more details about the case and move forward.
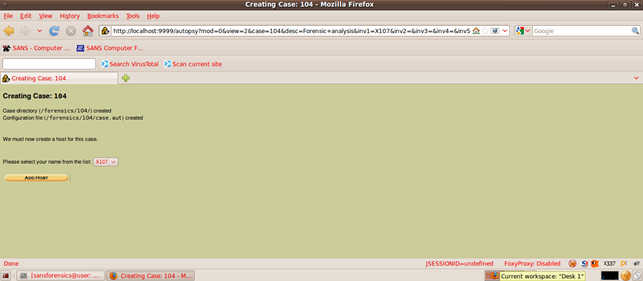
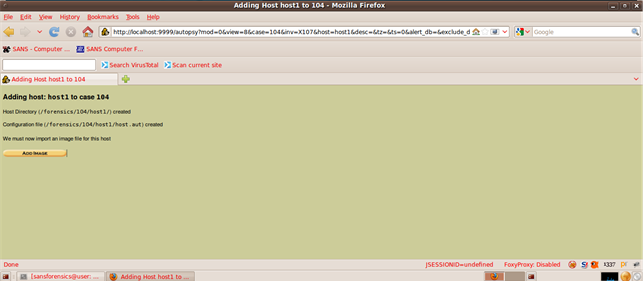
Now we move on to adding our image to the case for doing the forensic analysis. We give the location of the forensic image:
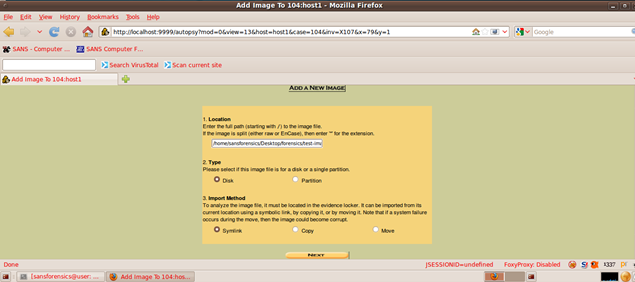
Next, we can calculate MD5 hashes, also using Autopsy:
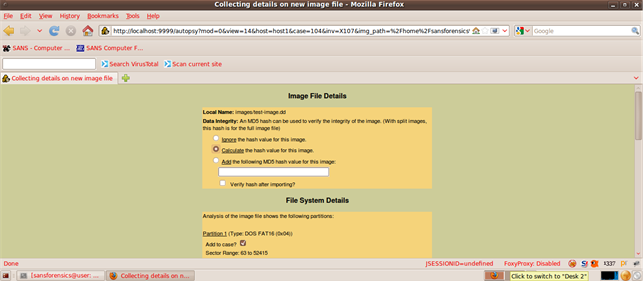
Autopsy lists all of the file system details and the mmls tool (command line) output for us:
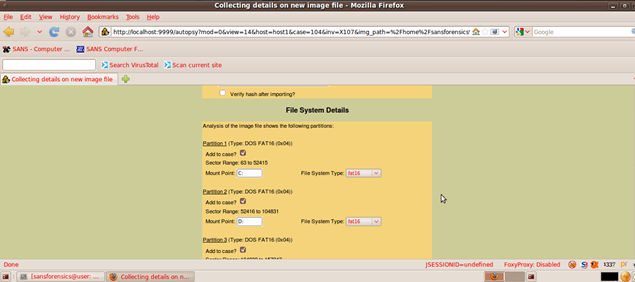
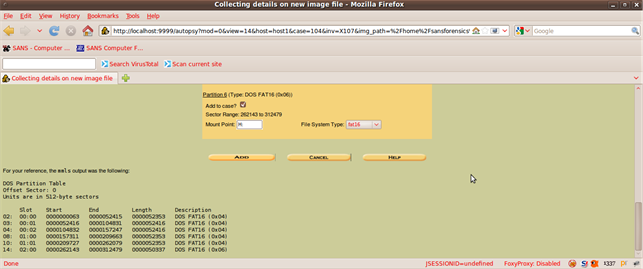
Now we move on to the analysis part; click on "Analyze."
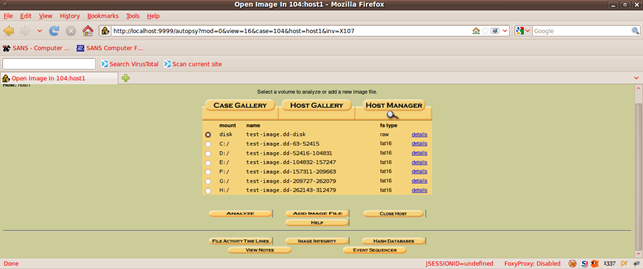
We do an analysis of the files in the C partition of the image:
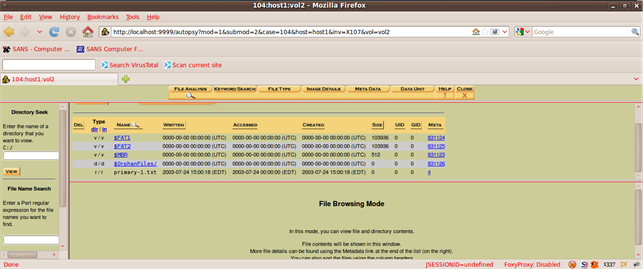
We can do a keyword search, metadata and view the contents of any sector in the file system.
DFF—Digital Forensic Framework
This is a really nice tool for doing digital forensic investigations, since it displays tons of information about the evidence. It is made of different modules based on Python that perform various steps in an investigation, such as file system module fatfs, ntfs to detect the file system. It has a viewer module to display text, images, etc. There are many more, such as Crypto, Hash, Databases, Statistics, etc. These are restricted to specific investigation; for example, the Hash module creates hashes for files to monitor file integrity and similarly the other modules.
This time we take another forensic test image for contrasting the results and views better for the understanding of the readers, since this image specifically has images, doc files, txt files, etc.
This is how DFF looks:
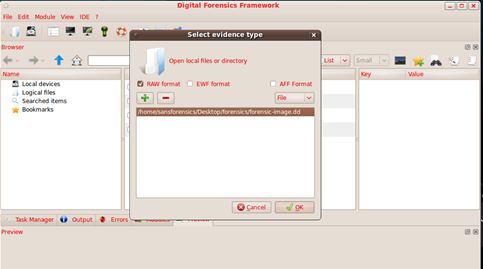
Now we add an evidence file, which is a raw dd image of a USB drive. For doing this go to File > Open Evidence File:
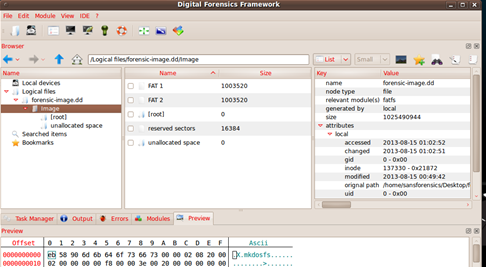
You can see that the evidence item has been added. Now we will simply try to analyze the file and the filesystem module automatically detects that it is a FAT file system and runs the fatfs submodule.
Once we apply the fatfs module we can see the files under "Logical Files." The files in red are the ones that were deleted from storage.
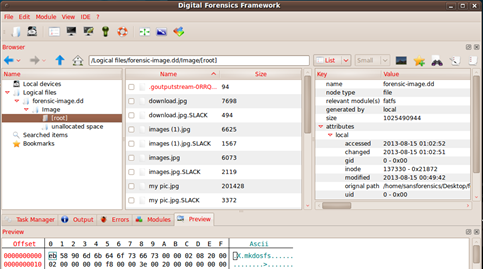
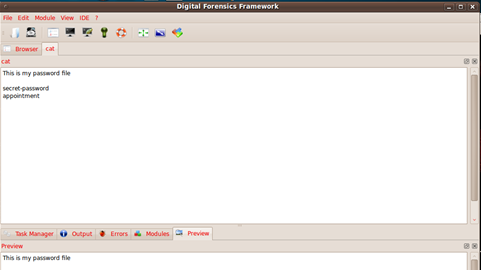
We notice that all the files have been listed under the root partition. Since we just have one partition in this image we can see that this partition has image files, text, and document files. Now, in order to further analyze them, suppose an image file: We use the picture module:
Similarly, we can use the module text to view our text files:
EVTX—Event Log Viewer
This is a really nice tool to audit Windows log files and forensically investigate them. Here I open an event log file extracted from Windows XP system in EVTX for my forensic investigation.
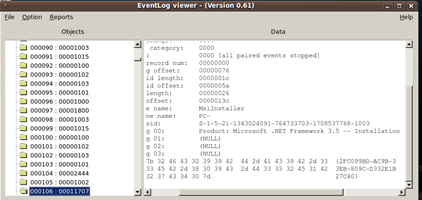
Here is an image showing the description of an event and more information about it. In the image below, we see that this is an informational event, a source from MsiInstaller, and the product that was installed is Microsoft .NET Framework 3.5. Similarly, we can investigate if a suspicious installation had been done or not:
In the next part we will cover the rest of the tools with SIFT.










