Social Networking Forensics with Bulk_Extractor
Bulk_Extractor quick overview and Installation
bulk_extractor is a computer forensics tool that scans a disk image, a file, or a directory of files and extracts useful information without parsing the file system or file system structures.
bulk_extractor is distinguished from other forensic tools by its speed and thoroughness. Because it ignores file system structure, bulk_extractor can process different parts of the disk in parallel. In practice, the program splits the disk up into 16MiByte pages and processes one page on each available core. bulk_extractor can be used for law enforcement, defense, intelligence, and cyber-investigation applications.
bulk_extractor can be used on Windows, Linux, and Macintosh OS X platforms. When it came to Linux, all that you have to do is to wish! Linux has many distributions that are dedicated to forensic matters, for instance, CAINE-Live distribution shipped with a ton of tools and bulk_extractor is one of them,

Fortunately, the installation on Windows is pretty straight forward. First, you need to have Python compiler
Installing Python 2.7 on Windows
Download link for MSI installer: https://www.python.org/download/releases/2.7/


Installing B_e on Windows 7
Download link for B_e 1.5.5 Windows installer: http://digitalcorpora.org/downloads/bulk_extractor/


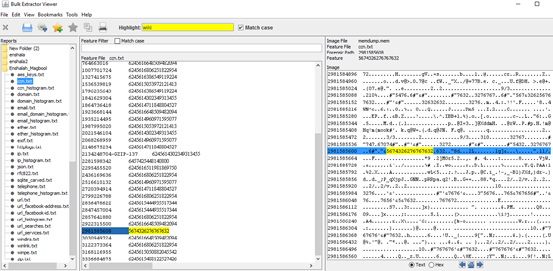
Bulk_Extractor Interface and Importing Disk Image/ Memory Dump

1: generated XML reports
2: highlight a keyword within the feature file and the parsed disk image
3: Filter among feature files
4: output of scanned image with correlated image address (byte offset from the beginning of the image in which it was found)
5: output of B_e scanner in .txt format (feature files)
Now to import disk image to be analyzed, go to Tools > Run Bulk Extractor
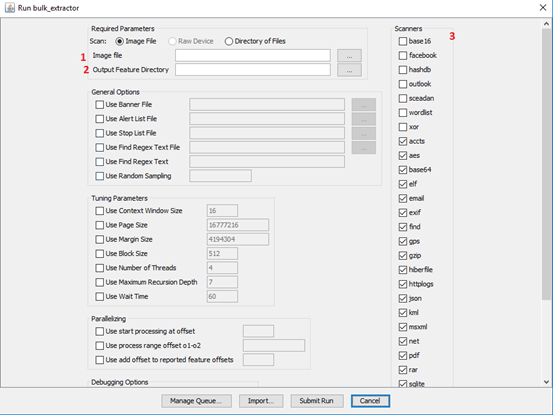
Then you should see the above interface where:-
1: To import the disk image
2: Save the output which contains the XML and feature files (.txt)
3: List of available scanners
*Note: make sure to check Facebook scanner during the Facebook exercise.
Bulk extractor supports multiple image formats like (.raw .img .vmdk , …)
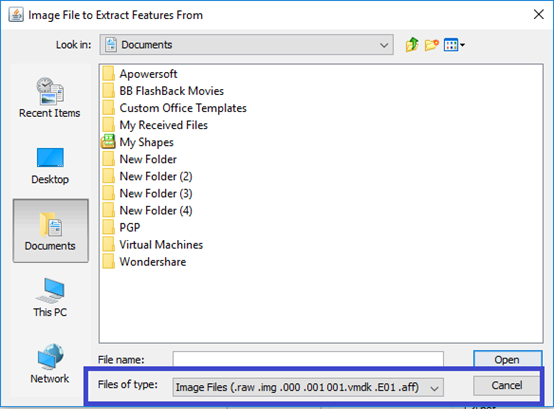
So basically, if you are working on Vmware platform, all that you have to do is to point your .vmdk and run the bulk_extractor. On the other hand, if you are working with Virtual box, the virtual disk has an extension of (.vdi) which also can be imported and recognized by B_e as we can see
Another option is to import a memory dump. Taking a memory dump is quite easy, and a lot of free tools are out there, I will be using FTK Imager tool during this lab, once you install the tool and open its interface, there's a little icon to capture the memory, when you click on it and …

After selecting the destination folder, you can capture the memory dump and export it in .mem format

Now all what you have to do is to import the dump into Bulk Extract to the let fun begin J
https://www.dropbox.com/s/rcyfjuc7i85m3th/memdump.mem?dl=0

What were you Googling?
In this task, we will prove that someone was actively looking for some terrorist groups and viewed one of the searching results.
So assuming that someone has gone to Google and searched for terrorist groups

Then he clicked on the Wikipedia result

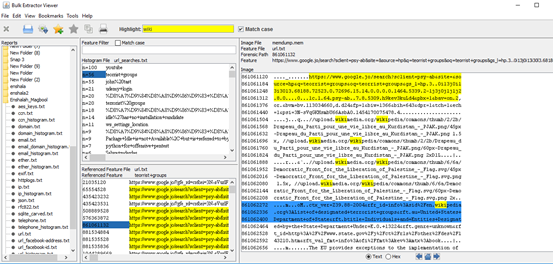
After importing the memory dump from the suspect machine, B_e will generate its report and a list of correlated features files. One of them called URL_Searches.txt, and it's to responsible for tracking your searching activities, and it's obvious that our suspect has searched for "terrorist" and when we highlight for "wiki" keyword, we see that his visited the Wikipedia for " List_of_designated_terrorist_groups"
Detecting Facebook Activities – Searching within FB and Viewing Videos
We've seen that we could capture Google search but what about the search within the Facebook, clicking and viewing on some videos. Well, even though those activities can be captured. Let's find out if we can grab this info using B_e.
So our suspect was looking for a kickboxing academy and …
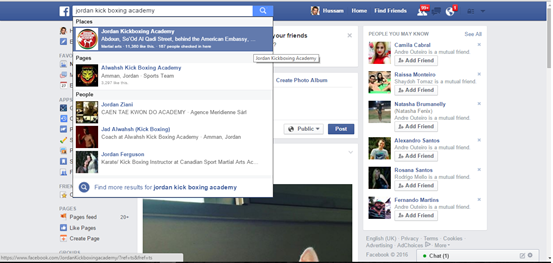
Once he landed on the Fan page, he clicked and watched one of the videos that have been uploaded

Thankfully, Bulk_extractor makes our life much easier by addressing such activities in clear format inside "URL_facebook-addresses."
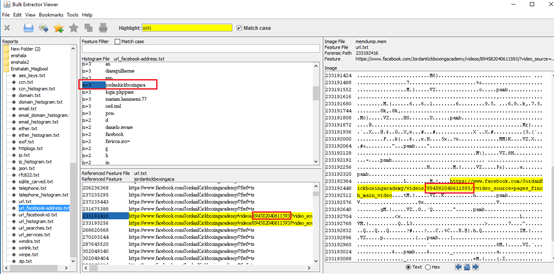
If we pay some attention to memory dump, we can see the following lines
1421147776 muh=30905&lh=Ac9SZQPUONZx-CiFCz.....u.https://www.facebook.com/J
1421147840ordanKickboxingacademy/videos/894582040611593/?video_source=page
1421147904 s_finch_main_video&theaterC6....
After cleaning the above, we can reassemble it into a direct link pointing to video that the suspect has been watching
https://www.facebook.com/JordanKickboxingacademy/videos/894582040611593/
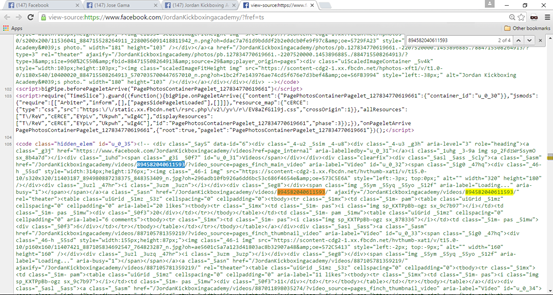
Another side note, the number 894582040611593 which is the video ID, can be seen as well if viewed the source page of the facebook page
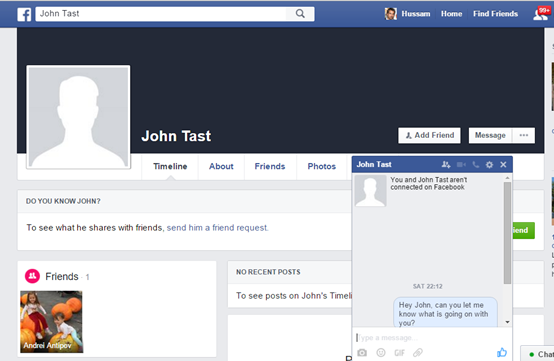
Detecting Facebook Activities – Viewing Profiles
Once again, one of the activities that could be detected is viewing other's profiles, here "John Tast" profile has been viewed by our suspect.

And that action was logged, and we can easily pick it up with quick searches in URL_facebook-id.txt

Detecting Facebook Activities – Sending Private Messages
Now here, our suspect has made one step forward and sent a message to John. Even though our suspect was not friend with John, there are enough logs to charge them.
These types of activities are linked to the profile ID, so if we looked again in URL_facebook-id.txt, obviously we could see what was sent in the private message (highlighted in blue color).

Capturing Credit Cards!
B_e may return a false positive result like, 5674326276767632 as it is not a valid credit card. However any valid credit card can be captured by bulk extractor can be found in cnn.txt
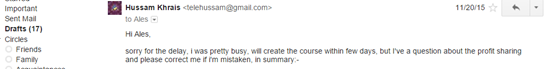
Capturing Gmails Communications!
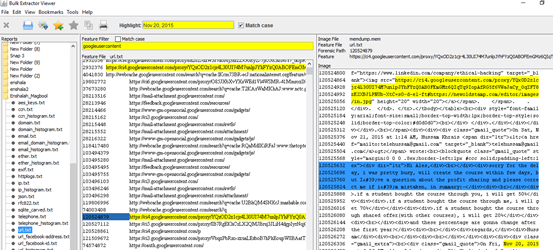
Last but not least, B_e is capable not only of capturing social media events, but also any sensitive information like credit cards. In this task a private Gmail emails, in the below snapshot we see an email sent from "Hussam Khrais" to "Ales" on Nov, 20th 2015, and we can see the message body as well.
Now within quick search in URL.txt and filter on "googleusercontent," we were able to recover the message along with the sent date as we can see down below.