Sources of network forensic evidence
One of the key aspects of any successful forensic investigation is the evidence collection phase. Identifying the sources of evidence while investigating an attack is crucial for the investigation to be successful. Once the sources are identified, the evidence such as logs should be collated and used for further analysis. This article provides an overview of various sources of network forensic evidence an investigator may be interested in.
Learn Network Forensics
Sources of evidence
Depending on the type of attack being investigated, a complex network may have several places where evidence can be collected from. Let us discuss some of the common sources where we may find evidence during an investigation.
Application and OS logs
There are various logs that will be generated in different locations depending on the events occurring. Application logs such as access logs and database logs, event logs generated by the operating systems in use(Windows event logs and Linux syslog), logs from network devices such as firewalls and routers are some examples of various log locations to look at.
When it comes to Windows event logs, there are three major categories of logs that can be found in Windows event logs.
Application: The Application logs contain the logs of the events generated by the applications running on the Operating System.
Security: As the name indicates, security logs contain events related to security. This includes logs such as valid and invalid logon attempts.
System: System logs contain events logged by system components. This includes events such as operating system reboot due to a system failure or crash.
When it comes to event logs on Linux based systems such as Ubuntu, most of the events can be seen in a single location and the location may vary depending on the Linux flavor. In case of Ubuntu, authentication logs, kernel logs, system logs and even some application specific logs such as Apache logs will be available in /var/log/ directory.
Following is an excerpt showing Apache server access logs from /var/log/apache2/access.log
192.168.1.92 - - [24/Nov/2020:23:12:39 +0800] "POST /site/idor/ HTTP/1.1" 302 1094 "http://192.168.1.90/site/idor/" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_4) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.198 Safari/537.36"
192.168.1.92 - - [24/Nov/2020:23:12:39 +0800] "GET /site/idor/home.php HTTP/1.1" 200 919 "http://192.168.1.90/site/idor/" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_4) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.198 Safari/537.36"
192.168.1.92 - - [24/Nov/2020:23:12:40 +0800] "POST /site/idor/home.php HTTP/1.1" 200 941 "http://192.168.1.90/site/idor/home.php" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_4) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.198 Safari/537.36"
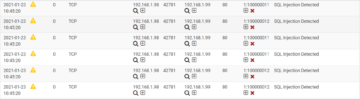
Intrusion Detection System/Intrusion Prevention System (IDS/IPS) alerts
Many investigations begin from an alert from IDS or IPS. These logs from IDS or IPS usually include alert data such as an identifier that has caused the alert and the description of the alert. In addition to it, we may find packet headers and payload in the alert. Depending on the tool being used, these logs may be extracted from various locations such as a file on the disk, web gui or email. The following figure shows alerts from Snort IDS being run in pfSense.
Routers, Firewalls and proxy logs
Routers are used to route the traffic from one network to another and they are the most commonly used devices in enterprise networks and they often contain many features that are of interest during a network forensic investigation.
Firewalls perform packet filtering based on a predefined ruleset. For example, let us assume that a rule has been defined to block any incoming traffic on port 3389. Any firewall will be able to do this as specified in the firewall rules. Modern firewalls can do much more than just packet filtering. They are often termed as Next Generation Firewalls and come with additional features such as VPN, Intrusion Prevention Systems, Intrusion Detection Systems, Anti Virus, Web Application Firewalls and more. Often, the goal of these modern firewalls is to effectively monitor the content within the packets and determine whether to allow the packets or not and thus they contain logs of our interest.
In addition to the routers and firewalls, web proxies in enterprise environments contain interesting logs at a large scale. Web traffic constitutes the major share of an enterprise’s network traffic. Employees browsing activities in an enterprise environment almost always get recorded in web proxies. So, Web proxies can be a goldmine for investigators.
Learn Network Forensics
Captured Network traffic
When an alert is generated by tools like IDS/IPS, a packet capture can be recorded and saved for further analysis in many tools. Most of these captures can be analysed using tools like Wireshark later. Additionally, in the event of suspicion of an ongoing attack, tools like tcpdump for Wireshark can be used for packet capturing and analysis.
Sources
- https://ubuntu.com/tutorials/viewing-and-monitoring-log-files
- Network Forensics by Ric Messier - https://www.amazon.com/Network-Forensics-Ric-Messier/dp/1119328284
- Internet Forensics by R Jones - https://www.amazon.com/Internet-Forensics-Digital-Evidence-Computer/dp/059610006X
- Network Forensics by Sheriff Davidoff, Jonathan Ham - https://www.amazon.com/Network-Forensics-Tracking-Hackers-Cyberspace/dp/0132564718