Windows Phone Digital Forensics I
Abstract
Abbreviated as WP, Windows Phone is a new Smartphone operating system developed by Microsoft in order to succeed the old Windows Mobile, and this "new" operation system will be potentially the major mobile's platform in next few years. Windows Phone stills young proprietary mobile operating systems which mean its digital forensics is still not very advanced.
This article will take a look at Windows Phone 7 from a forensics' perspective; we will see how to explore SMS, Facebook and Whatsapp messages, how to extract emails, contact pictures… I'll try to show you the basics and try to extract as much information as I can from a Windows Phone based Smartphone.
All tests will be done on an unlocked Nokia Lumia 710 / Windows Phone 7.5 but theoretically this should work with any with Windows Phone device.
Introduction
Windows Phone 7 has a security model based on the least privilege principle, a set of privileges that is given to a certain process starting from lowest access rights given to Windows Phone developer , Standard rights given to native application, Highest access right and is not allowed to change rights then highest access right which is allowed to change rights; In addition to this, every user application is running in a kind of sandbox - which means it runs in a restricted environment and is not allowed to directly access the operating system internals.
Data acquisition approach depends on the kind of the smartphone we want to investigate (unlocked or not) and in general we need to install an application that will gain "a root" privilege, grab data then send it back to a connected computer, but technically this may bring some change to the "original stat" of the smartphone which may result in a small change of evidence. And even if we accept this fact, a full unlocked phone is needed to deploy an application on a Windows Phone 7.
Personally, I always opt for the "dirty" old school way: Always do it by hand! I will suppose that your Windows Phone is fully unlocked, this would be necessary for any investigation process (as there is a non-working anymore, method to bypass the marketplace procedure for installing an application, like the use of ChevronWP7).
I assume that you are targeting a fully unlocked phone, and if so we can proceed by installing either "Windows Mobile Device Center" which stills compatible with Windows Phone, or "Windows Phone Device Manager", technically those tools are aimed to combine an efficient business-data synchronization platform and can be used to transfer "all kind of data" between the connected device and your computer.
And both Windows Mobile Device Center and Windows Phone Device Manager need Zune software 4.8 or later to be installed on the computer.
In this article I will use both of these tools.
Windows Phone Device Manager Installation
Instructions
Requirements
All links for downloading necessary files are on reference section.
Extracting data
After connecting the phone to your computer and lunching "Zune" you can run Windows Phone Device Manager which will automatically install TouchXperience on your Windows Phone as previously said. The interfaces of both applications are quite user friendly and need no presentation.
Use "Explores File and Folders" to navigate into your Windows Phone files. The data acquisition methodology may differ depending on how we conceive it; you can just make a full copy of the connected mobile and work on it or just investigate files directly from the phone.
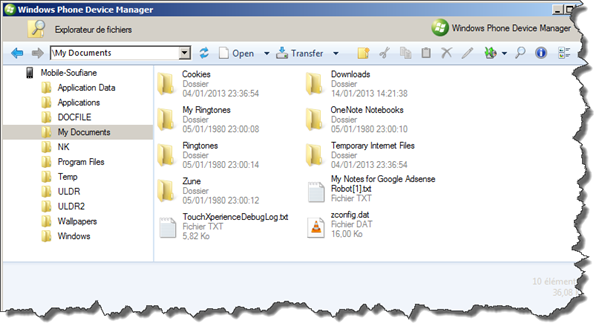
As you can probably guess, the Windows Phone file system is arranged the way a normal desktop windows based file system, just like Windows XP or Windows 7… and it's structured with usual directories reachable from the root directory.
The most important directories to investigate are:
- Application Data, contains Internet Explorer, Outlook, Maps and all data related to installed applications on the phone
- Applications, contains the isolated storage for every application in addition to all application installed by the user
- My Documents, contains some configuration files, Microsoft Office files, music and videos…
- Windows, contains the core files of the operating system.
In this paper I'll talk neither about the registry nor about active tasks.
Extracting SMS
All SMS's are stored in one single file located in the directory "rootApplication DataMicrosoftOutlookStoresDeviceStore", the file is "store.vol" and cannot be directly handled (you cannot copy or edit it) since it's always in use by the operating system, the tip is to rename the file this way a copy of the original is instantly made by the operating system:
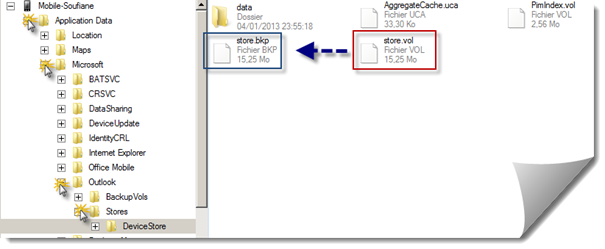
Let's now see the content of this file using any text or hexadecimal editor. I always use a hexadecimal editor because it may make you aware of some details that you won't see with normal text editor. Vol file seems to be actually Windows CE database and I had no enough time to search for a desktop way to explore them, as it should be so, we will do it by hand:
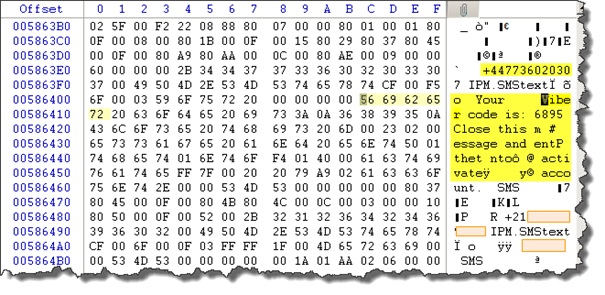
As you can see "Your Viber code is: 6895…" sent from "+44773602030", all SMS's either sent or received start by "IPM.SMStext" which can make it easy finding them or maybe automating the process of extracting them.
Extracting Emails
Since we are talking about a Windows based operating system, it seems logical that a Windows Phone uses Outlook as its standard email client which means that the user can synchronize it with the service he wants like Yahoo or Gmail…
Outlook data is stored in the directory ApplicationDataMicrosoftOutlookStoresDeviceStoredata and its subdirectories. All these subdirectories are numerated and each of them contains different data:
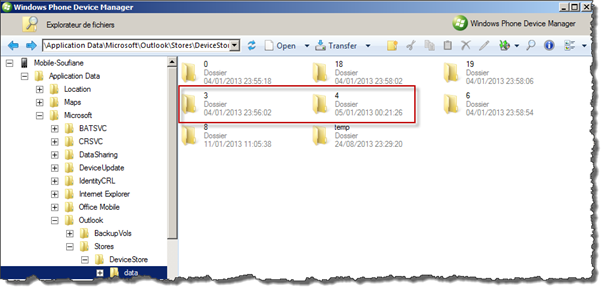
We will focus on number 3, 4 and 19 as for the other folders; I don't know why they are empty!
All files contained on these subfolders are ".dat" files, but if you can deal with basic file craving you can easily find that folder "3" and "19"contain basically JPEG files and folder "14" contains HTML files!
Let's see how it works:

I will open the first file with a hexadecimal editor and see how it looks:
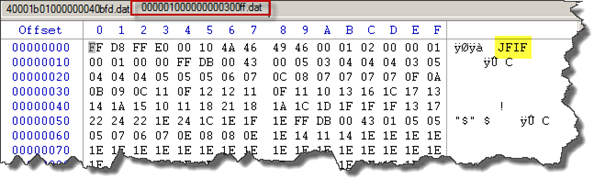
This file contains a valid JPEG file header, so let's just rename the file to something.jpeg and see:
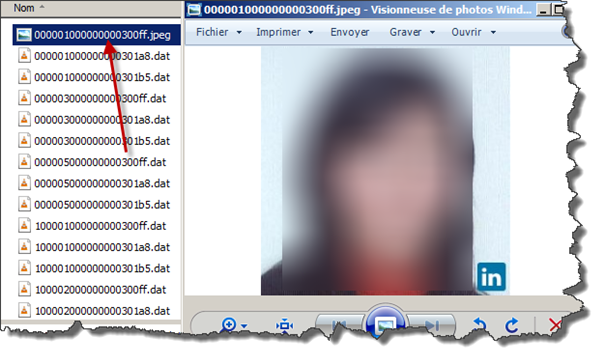
This is one of my contact's photo and in addition to this now I know that the phone I am investigating is "in principle" synchronized with LinkedIn too so I can go this way as well and push my investigation more in depth.
Let's now see what folder "4" has to tell us:

This file contains HTML tags; renaming it to something.html will just give us a working web page that you can easily open:
Extracting Facebook data
Every application on a Windows Phone has its own ID which will identify it on the marketplace, and as said earlier in this article, the folder "Applications" contains (between many other things) all applications installed on the phone, each one is installed on a separate directory having the unique application's ID as name under "Application/Data" directory:
The unique Facebook Application ID is "82A23635-5BD9-DF11-A844-00237DE2DB9E" and after Facebook installation, the application creates many folders as "Cookies", "History" and "IsolatedStore".
These folders can contain much useful information especially "IsolatedStore":
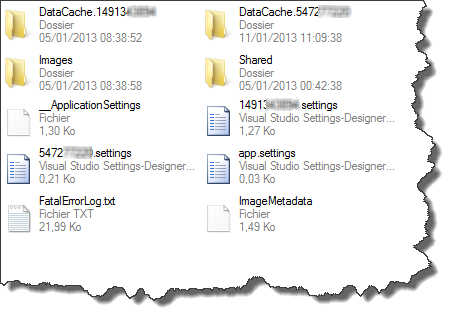
DataCache.userID , contains almost everything you need to know about the Facebook user having that ID (in this case 14913XXXX is mine, and the one starting with 5472 is probably a friend who connected to Facebook using my phone) this folder may contain the user's friends with some details about them like birthdays, link to their profile pictures…, friend requests, incoming and outgoing messages, recent Facebook feeds, user's notes and may even contain the last user's location if the option was enabled… and ALL data is not encrypted and can be easily parsed!
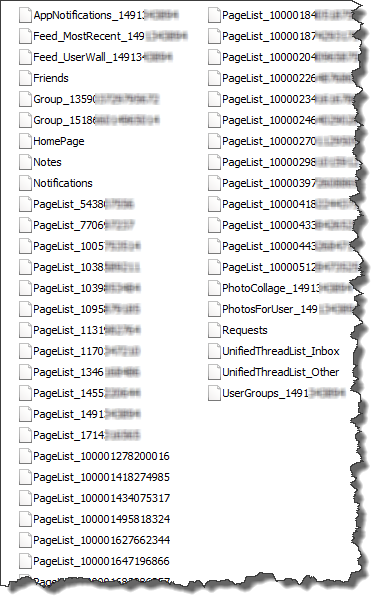
Example of some latest user's feeds:
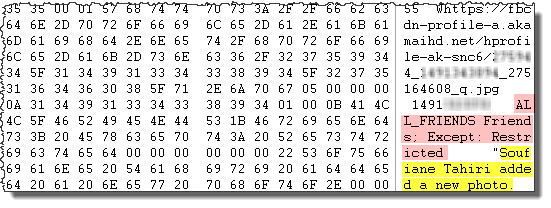
The user (me, Soufiane Tahiri) added a new photo that was shared with all friends except restricted ones with a direct link to the image.
All users' friends are listed with their FULL names, birthdays and direct link to their respective Facebook profile pictures:
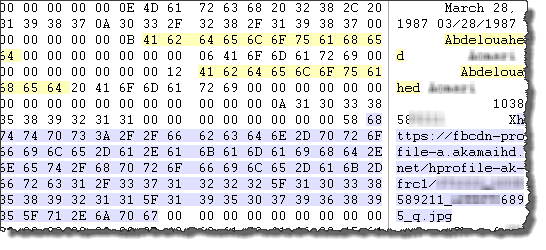
Full Name: Abdelouahed XXXXX, birthday March 28, 1987 and the link to his profile picture.
All messages sent or received, even spams are listed (as seen below):

Images folder contains all images viewed by the user on Facebook using this Facebook application, all you need to do is add ".jpeg" as an extension to the file name:
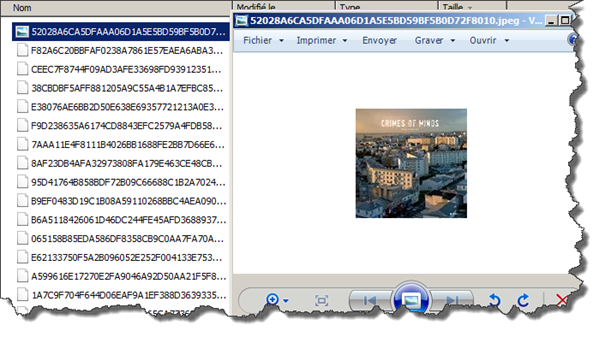
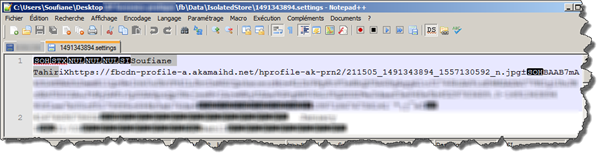
The file userID.setting contains the user's Facebook profile name, a link to that profile and a direct link to the user's picture profile:
I think I'm done with Facebook, just explore every single file and be sure that you will get more information than you ask!
Extracting Whatsapp data
Just like any other application all you need to know is the application ID to find where Whatsapp is installed, and Whatsapp application ID is 218A0EBB-1585-4C7E-A9EC-054CF4569A79.
By navigating to ApplicationsData218A0EBB-1585-4C7E-A9EC-054CF4569A79Data you can find two folders: PlatformData containing all picture captured and sent by the user and IsolatedStore containing almost everything you want to extract!
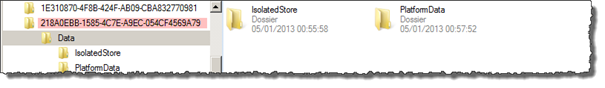
The IsolatedStore of Whatsap is arranged this way:
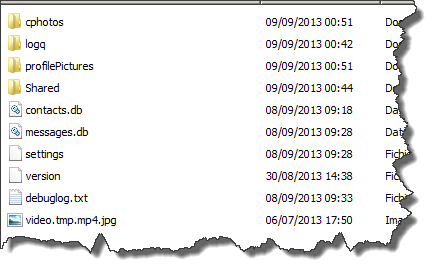
Cphotos folder, contains all current contact photos, all you have to do is to add ".jpeg" to their respective names.
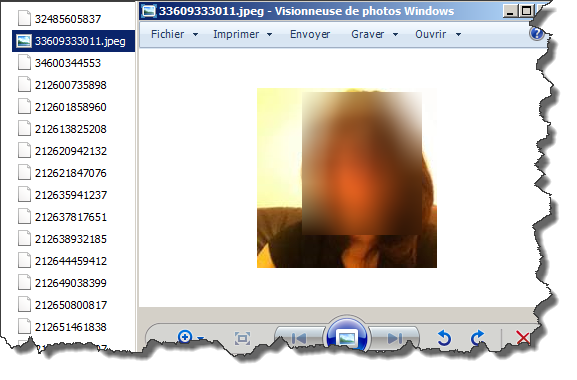
profilePictures folder contains all previous photos used by all your contacts, a kind of "profile pictures history" and you have just to add ".jpeg" as well.
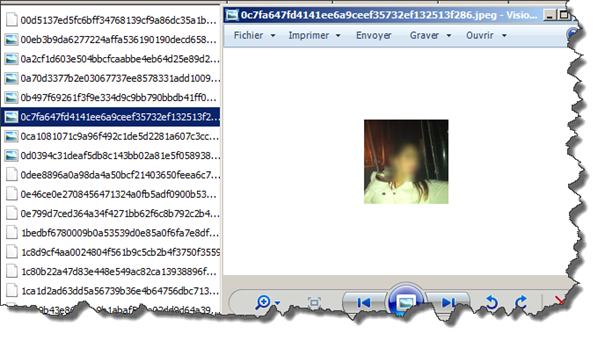
Shared folder contains three subdirectories but the most interesting one is "Transfers" where you can find every single file sent or received via Whatsapp, and guess what! Even files you have deleted are still there. (I was quite surprised when I discovered this.)
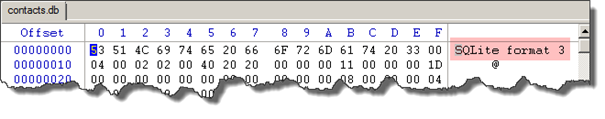
Then two interesting files "contacts.db" and "messages.db". Obviously these are SQLite databases as seen here:
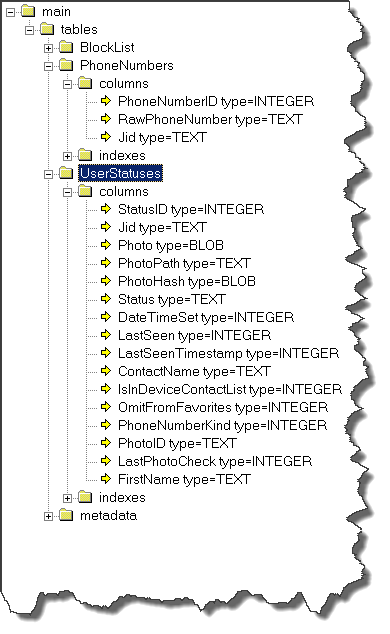
And they can be easily explored using any SQLite browser. What is interesting with these files is the fact that you can see every contact's phone number, name… every single detail:
Here is the schema of contacts.db file and some of its content:
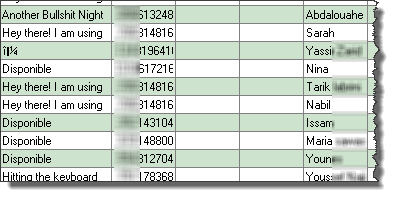
You can find all conversations via Whatsapp stored in clear on the "messages.db" file.
Actually this folder can be really interesting for investigation and maybe I'll write an article only about Whatsapp on Windows Phone, but to limit the size of this article I will not go further.
In fact and by continually analyzing how things are done on a Windows Phone I found that every installed application can be easily investigated, Tango, Viber, LinkedIN… So every single message, email or file sent or received is just stored in clear you just have to read it. This was just so intriguing to me and I decided to install a Paypal application and give it a try!
Extracting PayPal data
Once connected Paypal application stores everything you need to know about Paypal owner in one and single file called "__ApplicationSettings" which can be found under "ApplicationsData75738196-1DB2-49D9-AFB1-D66A34D19FB6DataIsolatedStore" the file is actually an XML file.
The file contains full user's address, user's email, user's phone number, recent transactions, currency used, payments received and sent from whom to whom with amounts … really everything you need to know and all data is stored in clear:
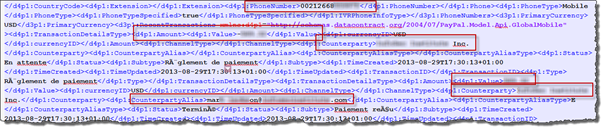
Extracting Maps data
Maps data and user location is in general stored in "Application DataMaps" folder, "MapsDataSet.dat" contains the lasts know locations of the phone (in my case I found last two addresses) which were very accurate and given by address not by GPS coordinate:

Summary
Analyzing a Windows Phone was very interesting since almost every single piece of data was cached or stored in clear, you can easily investigate Internet Explorer history, recent open tabs, see every file exchange, every email attachments… actually the only challenge was reaching the right of acceding data, since Windows Phone devices give limited access rights to the user, but this limitation can be bypassed by many methods already available tested and fully working. This article was just an initial test of my own phone and all this process can be automated to get even more in-depth analysis of any extracted file.
Downloads
- Windows Phone Device Manager : http://www.touchxperience.com/windows-phone-device-manager/
-
Windows Mobile Device Center : http://www.microsoft.com/en-us/download/details.aspx?id=14










