8570 Certification and the Way Ahead to 8140 Certification
Background on DoD 8570
Before certifications, the only measurement of someone knowing what they said they know was through an educational degree or an impressive resume. The military was always used to training its members when they entered into the service. They provided some On the Job Training (OJT) while in the service, but nothing very formal like a certification class. The military believes in an approach where the higher in rank, the less actual wrench turning is accomplished. This unfortunately means missed opportunities and missing out on learning of new technologies. The DoD 8570 program brought this idea back to keep security of Information Systems in the forefront of everyone's mind at least every couple of years.
The DoD 8570 was published in 2005 to address the concern of having unqualified personnel performing very critical cyber functions. This directive required all personnel that had access to any information system and performed any security function. This included system administrators, computer repair technicians, help desk technicians, information security managers, and directors of information security shops. This guideline allowed for a big change in the government. By establishing this guideline, units were able to request funds to train current personal to the level needed to complete their jobs. It also allowed for the type of training to change before new military members were assigned to Information Assurance (IA) jobs. This movement helped make it a requirement that military members be qualified before deploying to a combat environment. Using this standard, the Department of Defense was able to raise the standards of their professional and the industry. The 8570 was broken down into categories, certifications, and helped define the standards that have been needed for a long time. Let's examine how the 8570 program broke down Information Security into different categories.
Categories of 8570
To correctly evaluate an IA task force, all computer-related jobs had to be separated into categories. The five (5) main categories are Information Assurance Technician (IAT), Information Assurance Manager (IAM), Computer Network Defense (CND), Information Assurance System Architecture & Engineering (IASAE), and Computing Environment (CE). Each of these main categories have sub categories or levels defined in them. Each category also has distinctive theme to them that relate to the overall idea of how that category's progress would happen through their career.
IAT, IAM, and IASAE is broken into three (3) levels that are based on job level and skills. All Level 1 jobs are centered around computer/system assets. Level 2 involves network level equipment and the architecture to support it. Level 3 includes all the previous levels and includes enclave or enterprise server environments. Levels help define responsibilities, job related tasks, and ensure that a clear path of progress was established. This allowed for job announcements, contracts, and training requirements to be better defined than before. Figure 1, 2, and 3 show IAT, IAM, IASAE levels respectively.
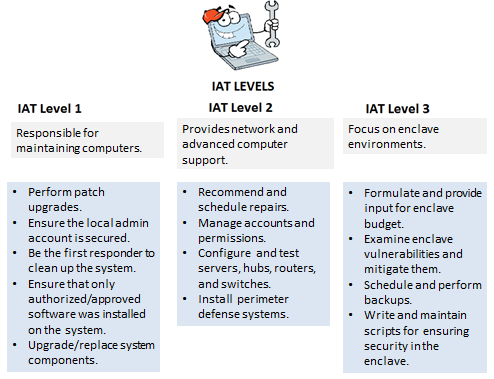
Figure 1: IAT Levels
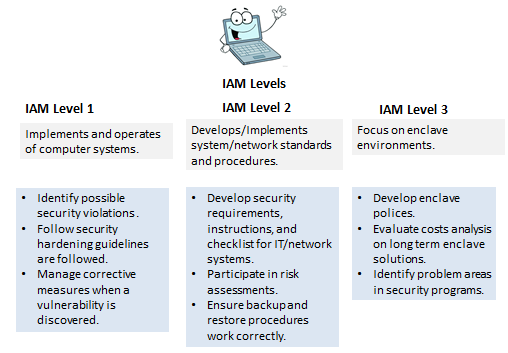
Figure 2: IAM Levels
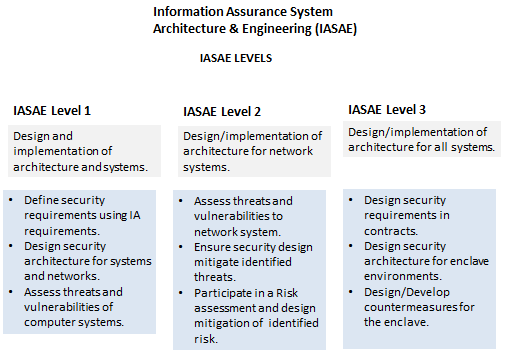
Figure 3: IASAE Levels
The CND and CE categories were broken into more detailed jobs/skills. The CND category has five (5) jobs: Analyst, Infrastructure Support, Incident Responder, Auditor, and Service Provider Manager. The CE contains two (2) jobs: Windows and Linux. These are more specialized jobs that require different skills than the other general categories. Figures 4, 5, 6 show the CND and CE categories.
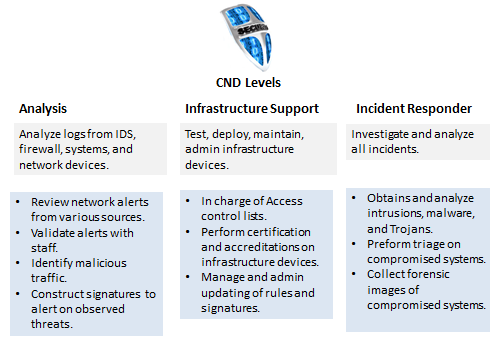
Figure 4: CND Category Part 1
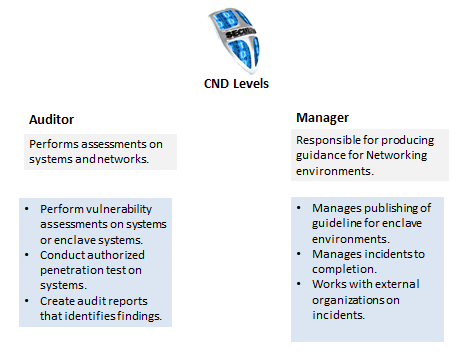
Figure 5: CND Categories Part 2
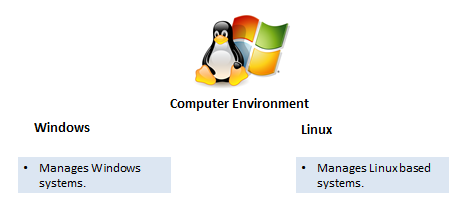
Figure 6: CE Categories
Certifications that qualify the category
Certifications were assigned to the levels of job requirements. The certifications match up mostly to the right categories. Some certs are also qualified in multiple categories. Certifications ensure that someone is qualified to an industry standard. Most of the certifications also require continuing education credits and a recertification fee. This helped ensure that knowledge was not lost after a period of time.
The 8570 program accepted the certifications from CompTIA, SANS, ISC2, ISACA, and EC-Council. As mentioned previously some certifications would span multiple levels in a category. For example, GIAC Security Leadership (GSLC) would qualify at any level of IAM. So someone in that position could just keep that certification current and they would still meet the job requirement. This also applies the the Certified Ethical Hacker (CEH) for most of the CND jobs in that category. The list of certifications have been updated from the original list in 2005. CompTIA Advanced Security Practitioner was added to the approved certifications. Figure 7, 8, and 9 shows the certifications each level requires.
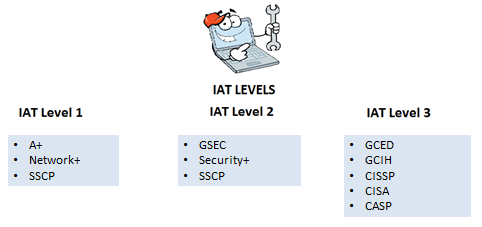
Figure 7: IAT Certifications
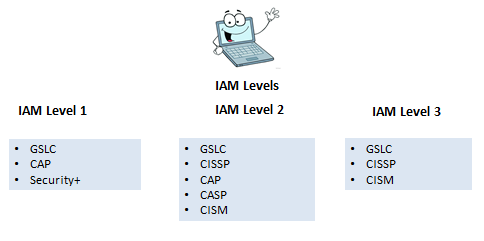
Figure 8: IAM Certifications
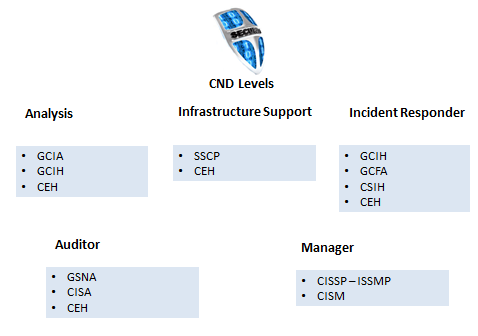
Figure 9: CND Certifications
How does 8750 have a positive effect on the information security industry?
By the government requiring certifications, industry awareness was raised to require certifications to be in a certain jobs. This movement also required contractors who worked with the government to be held to the same standards as everyone in the military. Commercial companies raised their standards to match what the government had put in motion on their own. This also created jobs by creating certifications shops. This movement also allowed an individual to separate themselves from others by the certifications they accomplish.
The future is 8140 and why the move to it
Although 8570 was a great framework, it was used incorrectly to write up job requirements that were classified under incorrect categories. Jobs like software programmers for example did not fall into any one of the defined categories. This would lead to a job being over or under classified and not having the correct tasks assigned to it. A variety of career fields also needed more detailed initial training and follow on training to complete tasks assigned to them. The technology that accessed DoD networks has changed drastically from 2005 to now include smart phones, web servers, cloud, and wireless.
Background on DoD 8140
This standard was originally planned to be implemented by the beginning of January 2013. The move to 8140 is a big change. More categories were added and some redefined. Also the amount of tasks were more than doubled. This big of a movement requires that all the contracts (current and future), job requirements, training, and evaluations include the new requirements.
The DoD 8140 model is based on National Institute of Standard and Technology (NIST) National Initiative for Cybersecurity Education (NICE) standard. This model defines categories and even job titles very clearly. This standard also defines tasks that would be associated within a category. Civilian job titles are described in this standard to better facilitate writing job requirements. The common types of work that fall under the main categories are known as "Special Areas". The 8140 standard also breaks up into categories to structure work tasks together.
Categories of 8140
As with the 8570, the 8140 had to be broken into main categories and further broken down into tasks or special areas. This breakdown helps better define jobs, skills, training, and focus areas. There are seven (7) main categories that have tasks or special areas of their own. The main categories are Security Provision, Operate and Maintain, Protect and Defend, Analyze, Operate and Collect, Oversight and Development, and Investigate. The new framework allowed for many different classes, certifications, and formalized training to now qualify an individual as "certified" in that task. Having different avenues of training allows individuals to obtain inexpensive training and still be qualified in a task. This list is not set in stone and changes often as new classes can be submitted. Figure 10 shows the categories in 8140.
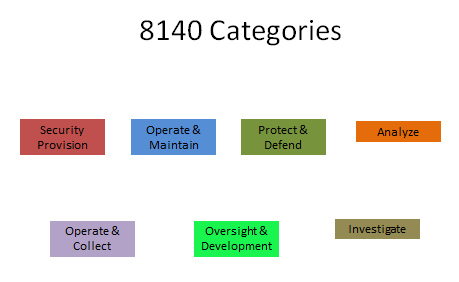
Figure 10: Categories of 8140
Security Provision
This category has seven (7) different special areas assigned under it. The jobs assigned to this category are centered around architecture and engineering. The special areas that fall under this category are Information Assurance Compliance, Software Assurance and Security Engineering, Systems Development, Systems Requirements Planning, Systems Security Architecture, Technology Research and Development, and Test and Evaluation. Certificates/Classes in this category consists of Project Management (PMP), A+ Certification, Sharepoint Management, and Server Administration. Figure 11 shows the special areas in this category.
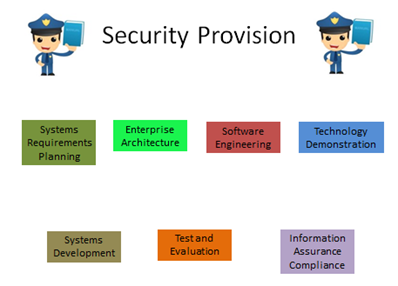
Figure 11: Special Areas of the Security Provision Category
Operate and Maintain
Seven (7) different special areas are assigned under this category also. The jobs assigned in this category are centered around the daily operation and maintenance of computer, network, and enclave systems. The special areas in this category are Customer Service and Technical Support, Data Administration, Knowledge Management, Network Services, System Administration, and Systems Security Analysis. Some of the certificates/classes in this category include A+, Advanced Data Warehousing, Basic Network Traffic Analysis, and Cisco Certified Network Associate (CCNA). Figure 12 shows the special areas in this category.
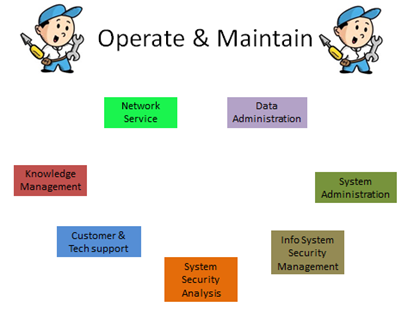
Figure 12: Special Areas of the Operate & Maintain Category
Protect and Defend
The category has five (5) different special areas assigned under it. These jobs center around securing and defending against cyber-related attacks. Computer Network Defense Analysis, Computer Network Defense Infrastructure Support, Incident Response, and Vulnerability Assessment and Management are the special areas in this category. Some of the certificates/classes in this category include A+, Systems Security Certified Practitioner (SSCP), Advanced PCAP Analysis and Signature Dev, and Android Security and Exploitation. Figure 13 shows the special areas in this category.
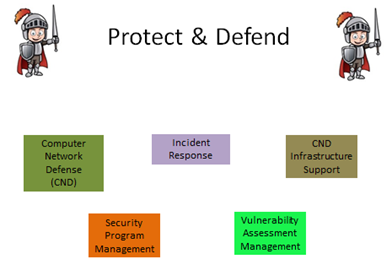
Figure 13: Special Areas of the Protect & Defend Category
Analyze
This category has four (4) different special areas assigned under it. These jobs analyze networks, systems, and exploitations to provide signatures and mitigation strategies. The special areas in this category are All Source Intelligence, Exploitation Analysis, Targets, and Threat Analysis. Some of the certifications/classes in this category include Certified Ethical Hacker (CEH), Certificate in Oracle Database Administration, Counterintelligence for IT Professionals, and Cryptography and Public Key Infrastructure. Figure 14 shows the special areas in this category.
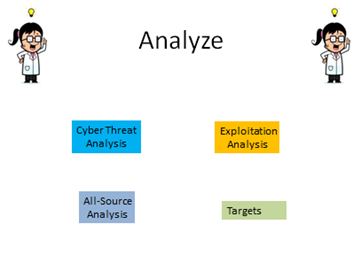
Figure 14: Special Areas of the Analyze Category
Operate and Collect
This category has three (3) different special areas assigned under it. These jobs are centered around cyber operations and planning. Collection Operations, Cyber Operations, and Cyber Operations Planning are the special areas in this category. Some of the certifications/classes in this category include Arm Assembler Programming Language, Business Execution: Crafting a Business Strategy the Executes, Security+, and Digital Photography for Law Enforcement. Figure 15 shows the special areas in this category.
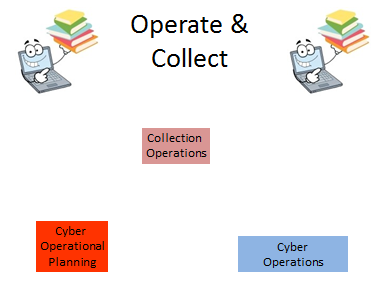
Figure 15: Special Areas of the Operate & Collect Category
Oversight and Development
This category has three (3) different special areas assigned under it. These jobs look at the legal aspect, the planning, and education/training that needs to take place. The special areas in this category are Education and Training, Legal Advice and Advocacy, Strategic Planning and Policy Development. Some of the certifications/classes in this category include Business Law Basic Concepts, Certified Information Systems Security Professional (CISSP), Certified Information Security Manager (CISM), and Cloud Computing Executive Overview. Figure 16 shows the special areas in this category.
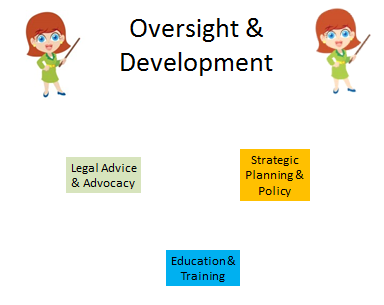
Figure 16: Special Areas of the Oversight & Development Category
Investigate
This category has two (2) special areas assigned under it. These jobs look deeply at investigation and forensics of computer assets. Digital Forensics and Investigation are the special areas under this category. Some of the certifications/classes in this category include Basic Imaging and Extraction Course, Basic Network Traffic Analysis, CompTIA Linux+ Certification Prep, CompTIA Network+, and Computer Incident Responders Course. Figure 17 shows the special areas in this category.
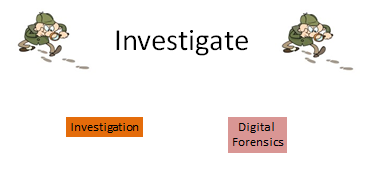
Figure 17: Special Areas of the Operate & Collect Category
References:
Army. (2013, Feb 1). Training and Certification Newsletter. Retrieved March 26, 2014, from Army CIO/G6, Cybersecurity Directorate: https://atc.us.army.mil/iastar/news.php?module=attachment&id=34
Department of Defense. (2012, January 24). Information Assurance Workforce Improvement Program. Retrieved March 26, 2014, from Information for the Defense Community: http://www.dtic.mil/whs/directives/corres/pdf/857001m.pdf
Education, N. I. (n.d.). Framework Categories. Retrieved March 26, 2014, from Nation Initiative for Cybersecurity Careens and Studies: http://niccs.us-cert.gov/training/tc/framework/categories
The Armed Forces Communications and Electronics Association. (2013, January). Cyberspace Workforce. Retrieved March 26, 2014, from http://www.afcea.org/events/west/13/documents/CyberspaceWorkforceKeith.pdf







