Are open-source security tools secure? Weighing the pros and cons
Introduction
There is a myth that good security solutions are necessarily expensive, but the truth is that there are many options, not only at low cost, but even excellent free tools that can be employed to protect most businesses.
A good example of this is OWASP's list of free for Open Source Application Security Tools, which includes solutions for static, dynamic and interactive application security testing, and static code quality tools. Even though some of the solutions listed also have paid versions, for most use cases they are free, including their use in open-source projects.
Security solutions do not necessarily have to be expensive, at least not in terms of licensing. But does it make sense to protect your business using a tool with few or no mandatory updates or even a timely fix of known vulnerabilities?
Before opting for a free security solution, a question needs to be answered: Are open-source security tools really secure? Or is it necessary to invest in a paid solution from a recognized brand to obtain a higher level of protection? To answer this question, we will assess the pros and cons of some of the leading open-source security software, including possible risks and how to adopt good practices to reduce costs without giving up a well-protected environment.
Open-source firewalls
Firewalls are one of the most basic security tools. They are essential for every organization and for most home users who need to protect their network from cybersecurity threats. With technological developments far beyond the basic filtering of incoming and outgoing network traffic, firewalls have gained the ability to function as VPN concentrators, web filters and even function as a network antivirus.
Corporate solutions known as next-generation firewalls include features such as application recognition/control, identity control by user or group, integrated Intrusion Prevention System (IPS), use of external intelligence to improve blocking decisions (i.e., "reputation services "), anti-malware features and SSL inspection capabilities.
In terms of open-source firewall solutions, there are several alternatives, such as IPtables, Untangle NG Firewall and OPNsense Firewall. One of the most used solutions is pfSense, based on FreeBSD, with a custom kernel that you can install on your own hardware or virtual machines.
In addition to the basic functionalities of a firewall, pfSense also allows you to completely disable packet filtering (thus functioning as a pure router), translate network addresses (NAT), operate in high availability (HA) mode, perform load balancing, dynamic DNS, create a captive portal to control and manage the users in public and private networks, function as DHCP server and DHCP relay and even perform graphical and log monitoring.
But in terms of security vulnerabilities, how does pfSense compare to one of the world's largest cybersecurity companies, such as Palo Alto Networks?
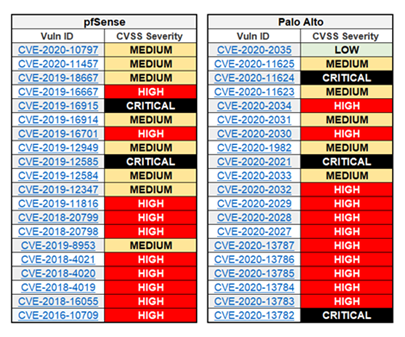
Using the NIST’s National Vulnerability Database (NVD) as a basis, both vendors had significant security flaws over the last couple of years. Taking into consideration the CVSS severity for the last 20 reported items, pfSense had at least two critical and 10 high vulnerabilities, while Palo Alto had at least three critical and 11 high security flaws.
Figure 1: Vulnerability statistics pfSense vs Palo Alto (source: NVD)
Considering the number and severity of the latest vulnerabilities, and the fact that most of Palo Alto’s flaws are from the current year while pfSense’s go all the way back to 2016, the first point goes to the open-source team.
Open-source SIEM
With the ever-increasing number of attacks and other cybersecurity-related events, monitoring the corporate environment is another essential task for most companies that want to avoid or even need to address security incidents.
By using a SIEM (Security Information and Event Management) solution, it is possible to implement real-time monitoring and correlation of events, notifications and alerts from different views, in addition to providing intelligence when analyzing and reporting collected data. High costs are usually associated with a SIEM implementation, since this type of technology is known to consume many resources (both in terms of hardware and time from the security or IT staff) required for periodically monitoring and adjusting SIEM rules to ensure that it is functioning properly.
The basic functions of a good SIEM solution should include at least data aggregation, event correlation and alerting, as well as capabilities for creating dashboards and reports. There are several good open-source solutions, such as OSSIM, OSSEC, Splunk Free, Snort and Elasticsearch.
In terms of functionality, the main open-source SIEM solutions are very good, however (yes, there is always a catch!), there are restrictions that can hinder or even prevent their use in larger environments. Splunk, for example, is recognized as one of the best SIEM options and its free/open-source version offers most of the features of the premium version, including universal data collection/indexing capabilities, monitoring and alerting, dashboards and reports, research and analysis, event annotation and more. Unfortunately, all of this is limited to a maximum daily data indexing volume of just 500 MB. To be clear: in larger IT environments, this limit can be reached in minutes.
OSSIM is another very popular solution. OSSIM is an open-source SIEM developed by AlienVault which has no limitations on the volume of indexed data and has interesting features such as asset discovery and inventory, vulnerability assessment, intrusion detection, behavioral monitoring and event correlation.
However, there are several limitations when compared to the commercial solution. These are things such as log management restrictions, no AWS and AZURE cloud monitoring and no cloud application security monitoring. This is in addition to not having official phone or email support, limiting problem solving to community volunteers in the official forum.
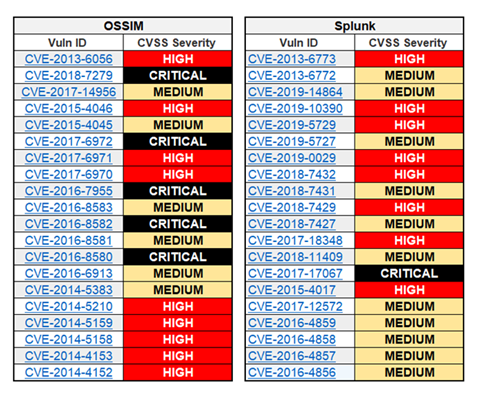
And again, in terms of vulnerabilities, let’s use NIST’s National Vulnerability Database and compare the 20 most recent OSSIM security flaws with Splunk, a SIEM product that for many years has been named as one of the leaders in the Gartner's magic quadrant.
And this time it is a point for Team Commercial Solutions. Over the last couple of years, Splunk had only one critical and eight high severity security flaws reported, while OSSIM had five critical and nine high severity vulnerabilities over a similar period.
Figure 2: Vulnerability statistics for OSSIM vs Splunk (source: NVD)
Open-source vulnerability scanners
Vulnerability scanners are tools that can perform practical tests focused on discovering vulnerabilities such as a weakness in the design, implementation or operation of security controls that can expose an information asset to all types of threat sources such as hackers and cybercriminals.
In addition to automating the identification of vulnerabilities, this type of technology usually also provides a risk assessment of identified problems and basic recommendations on how to mitigate each situation, and can produce security gap reports. In general, every organization should conduct a periodic (if not continuous) vulnerability assessment.
Amongst the many open-source options we have Wireshark, a well-known open-source network protocol analyzer, that is able to help in certain tasks related to the verification of vulnerabilities; the famous Nmap, a top choice of network administrators for basic manual vulnerability management; and Qualys Community Edition, one of the most accurate and comprehensive platforms for automatic discovery of IT assets and their vulnerabilities, with the option of detailed reporting.
Another excellent solution is the OpenVAS (Open Vulnerability Assessment Scanner), a complete vulnerability scanner capable of executing both unauthenticated and authenticated tests, using various high-level and low-level Internet and industrial protocols, featuring performance tuning for large-scale scans and a powerful internal programming language to implement any type of vulnerability test.
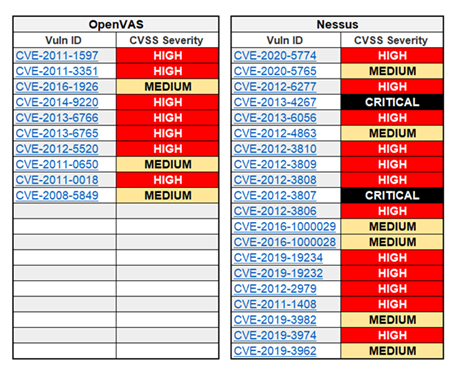
OpenVAS is probably the most widely used open-source vulnerability scanner, being a fork of the renowned (and expensive) Nessus that has now become a proprietary product. So how does it compare to its paid big brother?
For our final round, OpenVAS scores another point for team open source, with only 10 vulnerabilities reported at NIST’s National Vulnerability Database, including three medium and seven high-severity security flaws. Nessus not only has more vulnerabilities, but in terms of CVSS severity, it also has two critical items.
Figure 3: Vulnerability statistics for OpenVAS versus Nessus (source: NVD)
Conclusion
The question of deciding between using commercial or open-source solutions is complex, but it is not a new one, much less exclusive to information security products. While not having to spend on licensing seems like the obvious choice, it is important to remember that for every complex question, there is always an easy answer, which is usually wrong.
In terms of vulnerabilities, it is quite clear that over the years, both open-source and commercial solutions have had their share of security flaws, including critical vulnerabilities that could expose an entire company. The chance is that we will continue to discover new weaknesses in free and paid solutions, so what is the best approach for a secure environment? That depends on how much your company is willing to rely on the goodwill of volunteers to quickly discover, respond to and fix newly identified security flaws.
There is no doubt about the appeal of open-source security solutions, especially the fact that any argument towards cost reduction and customization capabilities resonates very well with the wishes of the C-suite. But for this strategy to work, it is vital to consider the fact that even if you do not pay a licensing fee, it is still necessary to invest in training your team and pay special attention to who is supporting the solution. Relying exclusively on the help of a community of volunteers for a tool that can become critical to your business is never a good idea.
Open-source security solutions have matured at a fast pace, implementing patches and new features at a speed and with a level of competence that often surpasses commercial products. Especially for small businesses and startups, where functionalities’ limitations are probably not as impactful, this may be the best strategy, providing the organization well-developed products with reliable, preferably paid support.
Even for larger businesses, adopting open-source security can be a smart choice — but in this case, there is no way to give up paid support, and you must carefully consider whether limitations such as the lack of basic functionality will not expose your business to unnecessary risks.
As the 218th Rule of Acquisition states: "Sometimes what you get free costs entirely too much, so the best option is always know what you're buying." This surely is the best option for security tools, open-source or not.
Sources
Free for Open Source Application Security Tools, OWASP
Rules of Acquisition, Memory Alpha

Get your guide to the top-paying certifications
With more than 448,000 U.S. cybersecurity job openings annually, get answers to all your cybersecurity salary questions with our free ebook!