Clickjacking, Strokejacking or UI Redress
Introduction
Clickjacking was first publicized by Jeremiah Grossman and Robert "Rsnake" Hansen in 2008. Clickjacking is an attack that is possible only by the use of iframes. Iframes are the HTML components that are used to load a webpage in a frame. Their height and width can be set to any size depending on the requirements of the designers. Iframe has an attribute named opacity to make the iframe opaque or even transparent, depending on the requirement. Clickjacking is possible because of the <iframe> tag and an attribute offered by HTML, which is "opacity".
Clickjacking is a combination of two independent words: Click and Hijacking. Here, Click refers to "mouse clicks" and Hijacking refers to "forcing a victim to click". Clickjacking means forcing a victim to click on a page on which the attacker wants him to click to perform the desired malicious activity, without his willingness to click.
There are a lot of attacks discovered these days that have clickjacking working in the backend, just to raise the popularity of the site, stealing one's session, or stealing a victim's confidential information such as credit card information, etc. Now in this article we will discuss identification of a clickjacking vulnerable site, different ways to perform clickjacking, its preventions, and real world examples of clickjacking.
Visualization
All of you are well familiar with the concept of stacking – here, in clickjacking, an iframe is stacked on top of the genuine site, and the iframe on top has the attacker's malicious site. As the iframe is set to be transparent with the help of the opacity feature, the victim will have no idea that instead of clicking on the site he is willing to, he is clicking on an attacker's malicious site.

In this image, you can easily visualize that on top of a genuine page there exists an iframe, i.e. partially visible for you to visualize, but in reality it will be invisible.
Whenever a victim clicks on the play button, then the event that will fire is actually the one that is in the opaque iframe. This is how a victim's clicks are hijacked to do whatever he doesn't want to do but the attacker wants him to do.
Exploitation
Basic ingredients to prepare for a clickjacking attack are:
-
Iframe – This is a frame in HTML that frames a webpage in it.
-
Z-index – decides the iframe index in the stack.
-
Opacity – makes the iframe transparent.
-
Position: Absolute – lines up the iframe with the dummy page.
Sample Code to test a website for Clickjacking:
[html]
<html>
<a href="#">Play Now!!!</a>
<h1 style="text-align:center">Play Game</h1>
<script>
window.onbeforeunload = function()
{
return " Do you want to leave click.site?";
}
</script>
<body>
<p style="font-size: 38px;"align=center>Best Game of the season</p>
<div style="z-index:10; opacity:0.4; position:absolute; top:0px; left:200px; ">
<iframe scrolling="no" style=" width:800px; height:500px;" src="http://www.torrentz.eu/"> </iframe>
</div>
<div style="top:0px; left:200px;">
</div>
</body>
</html>
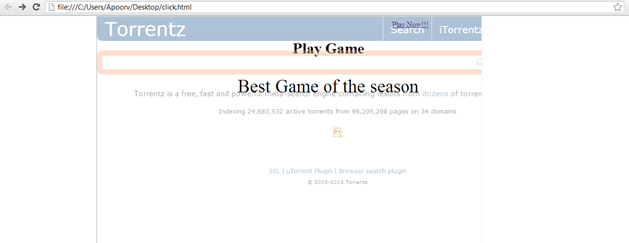
On clicking the Play Now!!! button, the victim will be redirected to the torrentz search page.
Preventions
Client Side Protections:
- No script Web Browser Plug-ins
-
Frame Busting
Frame Busting is a piece of code that is embedded in the webpage to prevent loading of any webpage in the sub frame.
Example frame busting code is:
[plain]
If ( top.location != location )
top.location = self.location;
[/plain]Frame Busting code generally consists of a conditional-statement and a counter-action.
Ways to Bypass Frame Busting are:
Double Framing:
The parent.location parameter works well in the frame busting code if victim's page is framed by only one frame. But if the attacker encloses the victim's page by two or more frames then parent.location violates security.
Exploiting the XSS Filter:
Victim's frame busting code:
[plain]
<script>
if ( top != self ) {
top.location=self.location;
}
</script>
[/plain]Attacker's inserted code:
[html]
<iframe src=" http:/ /www.attackersite.com/?v=<script >if ' '>
[/html]This code inserted by the attacker will block the frame busting code because XSS filters will match the regular expression starting with "<script> if" and filter out all the javascript code starting with "<script> if", hence the attacker's frame will beloaded.
IE Restricted Zone:
Mostly the frame busting techniques rely on JavaScript. If JavaScript is disabled then the frame busting code will not work. To sort out this problem, IE included an attribute named security="restricted" to identify frames coming from restricted zones and allowing them restricted access to the client's browser, i.e. such frames cannot load JavaScript and they cannot access cookies stored on the browser, thus session riding becomes difficult.
Example:
[html]
<iframe src=" http://www.attackersite.com" security=" restricted ">
</iframe>
[/html]OnBeforeUnload Event:
This is used to bypass frame busting code in the case when frame busting code wants to destroy the iframe and loads the source defined in the iframe as an entirely new web page.
[plain]
<script>
window.onbeforeunload = function()
{
return " Do you want to leave fictitious.site?";
}
</script>
Server Side Protections
HTTP X-Frame Options
HTTP X-Frame Options are the best defence against Clickjacking attacks. HTTP X-Frame Options allow or disallow the pages of victim domain to be rendered in an iframe on an attackers site. This Option is allowed in the HTTP Response Header.
For example: Rendering the Facebook's Like button in an invisible iframe just above the Click Here button on the attaker's evil page was the most popular example of a Clickjacking attack. This is also abbrievated as Likejacking. Facebook protected itself from this attack by using the HTTP X-Frame Options on every page of the Facebook website that is not to be rendered in any iframe on any other domain.
Options available in HTTP X-Frame Header Options:
- SAMEORIGIN: The document will be rendered in the iframe only if the iframe content and the iframe containing site has the same origin, i.e. same domain.
- DENY: The document or webpage will not be rendered in an iframe, even at the parent site.
- ALLOW-FROM URI:The document or webpage can be rendered in the iframe only at the domains that are specified in the ALLOW-FROM option. This ALLOW-FROM option does not include wild card characters and multiple entries. Google Chrome and Safari browsers do not support this option.
Apache Server Configuration Modification
To configure Apache to send the X-Frame Options header for all pages, add this to your Apache web server's configuration file:
[plain]
Header always append X-Frame-Options <OPTION>
Prohibited use of HTTP X-Frame Options
HTTP X-Frame should not be used this way, because browsers can ignore the header if specified in the <meta> tag. So this way of implementing HTTP X-Frame option should be ignored:
[plain]
<meta http-equiv="X-Frame-Options" content="deny">
CONCLUSION
The severity caused by Clickjacking attacks is very high, but it is very simple to prevent the attacks. As discussed above, we can easily prevent clickjacking attacks by the use of HTTP X-Frame Options on all those pages that the victim doesn't want to render in any attacker's iframe. This prevention is widely supported by all the latest web browsers.

Get your guide to the top-paying certifications
With more than 448,000 U.S. cybersecurity job openings annually, get answers to all your cybersecurity salary questions with our free ebook!
The frame busting technique has several flaws in it, but it is also appreciated for older browsers such as IE 7 or older that don't support HTTP X-Frame Options.










