Digital footprints and privacy concerns

"It is too difficult to give exact statistics on the amount of data people leave, but confirmed every time we perform an online action, we are contributing to our digital footprint. Out digital footprint are more public than we would ever imagine."

What should you learn next?
– Rob Livingstone, IT Consultant
Digital footprints (aka cyber shadow or digital shadow) are the trail and traces on the Internet that we leave behind us as a result of our Web activities. Web sites collect information as you use them, with or without the knowledge of the user. Anytime a user visits and enters data into a Web site they should be aware that the data they enter could be stored, shared or used by the Web site. The data can be anything from surfing Webpages, phone calls, online shopping, updates and uploads on Facebook, Twitter, emails, to word searches on search engines such as Google, Bing and Yahoo. In the cyber world, everything we do, places we visit, and online contents that we read and write are in some way stored and can be traced back to find the activities of the individual.
This information is used for targeting individuals for services and products. It opens up a lot of doors for researching any individual's backgrounds, characters, interests, activities, behaviors, likes and dislikes. From the perspective of a company, it is going to help them in targeted advertisements, recommendation engines, and to increase their customer base. But unfortunately, hackers and cyber criminals are taking advantage of the same trend. They can access personal and private information of an individual if they are not careful, which eventually leads to identity theft and loss of money.
Cyberpsychology
The amount of time we spend online increases every year, and more information about us appears on the Web each time. In this digital era of a technology-dependent community, we have created two personalities of our own now. They can be differentiated as follows:
- Online or digital personality
- Offline personality
This differentiation has created a study of its own, termed as 'Cyberpsychology'. It is the study of human mind and its behavior in the context of human interaction and communication of both man and computer. It's about online identity, online relationships, personality types on cyberspace and digital addictions. A person's real world attitude and behavior may not be the same on the Web.
Though digital psychology is a relatively new discipline, many organizations have started adopting these techniques to influence customer behavior and increase online sales.
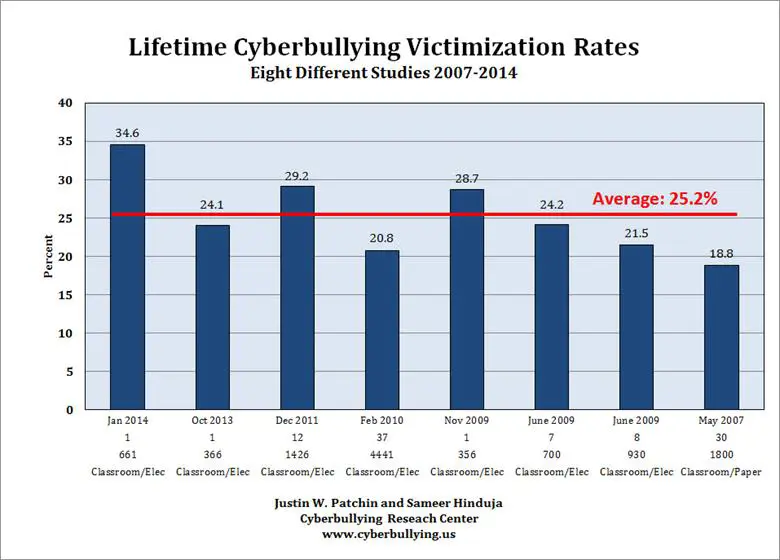
Cyber Bullying victimization graph (2004-2014)
The idea that nothing online is real and therefore nothing you do there "counts" is a fallacy. The self-deception is made much easier by hackers because they never have to see the faces or hear voices of their victim. Cyberstalkers and cyber bullying are also increasing drastically. Kids and teenagers are especially subject to social consequences from their digital footprints. Some don't realize that posts that they put on social media sites are there for everyone to see and that they are there indefinitely. Other people can post inappropriate pictures and other negative posts about them that lead to embarrassment or even worse.
Along with seeing what you post on social media sites, such as comments and pictures, your digital footprint can help a prospective employer validate your resume and find out other information about you. This means that you want your footprint to be clean and truthful.
Hackers can steal your money using your digital footprints
Most common Internet users are not aware of the extent of such issues. Imagine that with just one email, hackers can target or remotely control our systems. The IP address can be tracked from the header of the email IDs. There are various IP address locators available where one can get information about the ISP address to which the particular IP address belongs. Some additional information may be available that indicates the general area that an IP address might reside in. It is not necessary to hide yourself on the Internet; indeed this would be almost impossible. But it is wise to be careful about how you appear online, and to be conscious at all times of how you protect your online reputation.
You can also deliberately set about creating a positive online image. Identify how you want people to see you, now and in the future, and shape your online profile to reflect this. Publish photographs and blogs that present you in a good light and illustrate your values, skills, talents, interests, hobbies, and experiences. Our Internet activities are a cloud of data scattered on servers that are beyond our control. Our digital profiles are regularly bought and sold without our permission.
The trading of personal data by organized criminal gangs which is then used to commit fraud against individuals and corporate organizations has become one of the fastest growing crimes in the world. In the early days of identity fraud, concerns were focused on criminals gathering personal data through techniques including raiding bins, trading stolen passports and online phishing. Times have now changed, and although there are still methods through which personal data can be collected, people are now living their lives more mobile and online and leaving an increased digital footprint behind them. As a consequence, the main and wider threat now comes from two main sources:
-
Spyware - Malware being placed on PCs and laptops, silently collecting data and feeding it back to criminals.
-
Cyber Espionage - Hacking into major institutional databases, collecting thousands and sometimes millions of data records at a time.
These methods help criminals to build massive databases, slowly building up individual data profiles until they have enough information to successfully apply for financial credit under someone's identity or via a fake identity. While 2014 was "The Year of Data Breach", 2015 is off to a fast start with several prominent data breaches. As per statistics gathered by Breach Level Index, there were more than 2 million records per day that were breached in the year 2014, which means 32 records were breached each second.
Colin Holder, Director of Identity Intelligence, explains:
"Knowing the habits of these criminal data traders, how they interact and the methods through which they transact is the key to intercepting data that will at some point be used to commit fraud. Over the past 7 years we have been monitoring this criminal activity and have built up a database of over 500 million compromised data records, all of which have been, are currently or will be used to commit fraudulent transactions."
In recent years, consumers have been presented with Identity Theft Protection products that allow monitoring of credit reports to help them detect if their personal data is being used to create additional lines of credit for criminal use. However, the problem of data trading does not just create problems in credit line applications. The growing issue is the build up of hundreds of millions of personal data records being traded over and over again that can enable someone to take over many other aspects of an individual's life. As we live more of our lives via technology, sharing more data online through PCs and smartphones, these risks are set to compound. Rosemary O'Neil, Privacy Product Innovation Manager at Assurant Solutions says:
"We face a growing problem and constant battle to stay as close to the shadow economy as we can. The best form of personal defence against this problem is early detection of your data having been compromised and then support in understanding what to do about it. The breadth of intelligence that is required just to keep up with the criminals is immense."
Solving the privacy concern
According to a recent global study by Microsoft, most cyber surfers "still don't feel they are completely aware of the information that's being collected about them." According to Robin Wilton, identity and privacy director for the Internet Society, every day businesses are finding new ways to use this collected intel. The cyber data collection includes:
- Authorized collection or active data traces- Data you provide by consent when you register with a Website, such as name, email, phone number and preferences.
- Unauthorized collection or passive data traces - Data taken without your explicit knowledge or consent from your computer and browsing history, location specific data, search keywords and use of smart television.
Create a healthy digital footprint
Inputs to digital footprint include location, time, search results and keywords, content created and consumed, and digital activity and data from server and from the user's social crowd. Some data can come from deep data extraction and Internet data, such as footprinting. While a digital footprint can be used to infer personal information without their knowledge, it also exposes an individual's private psychological sphere into the social sphere.
The most effective way to control your active digital footprint is to be careful about the information you share online, the platforms where you share the information (a Web forum, an email, a social network), and who you share information with (public, friends and family, an individual). Be particularly careful about publicly sharing any personal information.
User awareness
As our digital lives continue to evolve, so will the ways in which we leave tracks through cyber space. Taking steps to manage you digital footprint can help ensure cyber criminals never pick up your trail.
If you use social networking sites such as Facebook, Twitter and LinkedIn, or regularly post photos, videos, blogs and comments, make sure to manage your contributions carefully, since much of the information stored online becomes public by default. Unless you change your privacy settings, your social network pages will come up on a Web search. Anyone who finds out enough about you could potentially impersonate you, so be careful about the personal information you make publicly available. Potential employers have also been known to reject applicants on the basis of information discovered online.
User awareness and employee training about digital footprints will help people to know how data about them are collected and shared. For example, a persistent browser based cookie can be easily detected and deleted by a user. But a new type of browser cookie called super cookie is designed to permanently store data on a user's computer. These are more difficult for the users to detect and delete. They can contain any information from browser history to ad-targeting data.

The digital world has become a very integral part of our life. Properly analyzing each data and word that we share online will help to frame our personality and individuality.

Get your guide to the top-paying certifications
With more than 448,000 U.S. cybersecurity job openings annually, get answers to all your cybersecurity salary questions with our free ebook!









