Doxing: The Dark Side of Reconnaissance

Introduction:
Doxing is a coin with two sides. Doxing can be used for security, research and collecting proof for investigation in one hand but in other hand, it can be used for cyber harassment and other serious cyber issues. But here, after lots of research, I learned that Doxing is a part of Reconnaissance, which generally focuses on its dark side. So before entering into the dark side, let's first understand the bright side i.e. Reconnaissance.
Define: Reconnaissance
Reconnaissance is also known as foot printing or information gathering. It is the first step to any penetration testing. The main objective is to gather as much as information possible about the target.
Define: Doxing
According to urban dictionary, "Doxing is a technique of tracing someone or gathering information about individual using sources on the internet. Its name is derived from 'Documents' or 'Docx.' The Doxing method is based purely on the ability of the hacker to recognize valuable information about his target and use this information to his benefit."
It's also based around the idea that, "The more you know about your target, the easier it will be to find his/her flaws."
Though I understood the concept, still it's a little confusing. If Doxing is all about gathering a valuable piece of information and using it to the attackers benefit then how does it differ from Reconnaissance? Why it is called Doxing?
After lots of research I found that Doxing is a two-step process.
Step1: Collecting information about an individual from publicly available sources such as social networks, chat forums, blogs, articles etc. from a limited initial source of information such as name, email id or screen name in any site. This is Reconnaissance.
Step2: Intentionally disclosing it in any group, forum, site, or anywhere in public for some kind of personal benefit that may be rage, revenge or enmity for harassing or humiliating the target.
What I concluded is that Doxing consist of two stages. If a Hacker collects all the information about a target and does nothing than, that's not Doxing but simply Information Gathering. When this Information is posted publicly, that's exactly what we call Doxing.
What information is needed when Doxing?
There is no such format or any particular structure for Doxing. It may be any information related to the target. The information must be private and important. If you think from an attacker point of view we can say Doxing might contain real names, real pictures, ages, genders, primary email id, and if different email ids are used for different social sites than those ids with respect of sites. Social network profile links (Facebook, Twitter, LinkedIn), websites, owned blogs, address, phone number, education details, Bank account details and such similar or more important information.
Where to Start?
As we know the first step of Doxing is gathering information. And to gather information about someone we need some or any small piece of information to start with. That information may be name, email, screen name or some/all of these.
Let's think about real time scenario.
In a social network site, a user is disturbing another user. In this case our victim wants to Dox the attacker. But the problem is the attackers profile looks fake, not one bit of information looks genuine. So where to start? The answer is, start with the username.
How to start?
Let's say the name is John. We know that John is a very common name and if you search in Google as "John" you will get thousands of results. So what to do?
You have to find some other information about John in that social network site. But as we know that it's a fake profile we don't know whether to rely on any of the information or not. In this case, search for some other info like signature. For example if he/she put signature as "h4xor". You can continue searching using "John h4xor". This will reduce the Results.
Sometimes your target person registered in multiple forums, websites or social networks. So while searching, you will get results of registered websites for him/her using that username or other info. Let's say you found some other accounts which looks fake with the same signature, then compare those accounts and see what information and which users are mutual, Read each post of target persons, he might have left some more information about him in any of the forums or websites.
This is just an example of how to collect information from nothing and end up with Doxing.
Search Methods:
Google
It's a powerful search engine which comes with different advance search options. Use its special notations, operators or a combination of both to find an effective result.
There are several special notations like
-
+ include
-
Exclude
-
-
| OR
-
.. range
-
~ synonym
-
"" string
-
*Wild card
Bing
Bing is also a powerful search engine. Having its own specialties, it's social search feature helps users to search for and retrieve real-time information from social networks.
Looking for profile of a person
Peek You
Is an interesting site to gather information. It asks about the first name or last name. After entering first name and last name it provides interesting information such as social account details, possible location, possible relatives, email addresses (Partial shown in result) and also arrest records if any.
Nothing to worry if you don't know the first name and last name of the target. You can even search just using the username and also using email addresses of the target.
Lullar
This is also quite similar to peek you. You can search using first name, last name, user name and also with an email id. It gives results of all the websites that may have the entered user.
Check Usernames
This is actually made to find out if a user wants to use a particular username in a social networking site than whether it is available or not. But we can use the same to check if our target is using other social networking sites or not. It's quite simple you just have to add the target's username and search. The site will search through 160 different social sites and give you the result. Check for the sites are not available, that means the particular username is already registered in the site and may be another account of your victim as shown in image1.
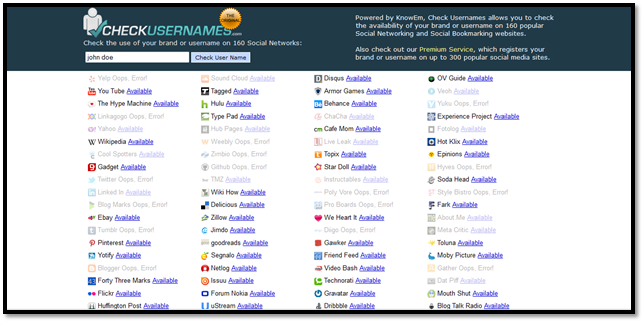
Image1: Check Usernames Result
Pipl
You can search using name, email, username or phone number (location is optional). It provides links of the social networking sites along with the profile picture used to verify the target easily.
123 People
It is also similar to Pipl but it only allows you to search using first name last name and location (You can use world if you don't know about the targets country).The results provide social networking site links with profile picture and interestingly it provides related people details also.
Webmii
You need to search using first name and last name. If you don't know the region of the target, use international to search. In the result you will find pictures of the target and also blog posts. If the target posts any articles in public you can find it in the results.
Socialmention
You need to search using name, email id, username or any related keywords. Social mention searches the entered keyword and provides you results if the keyword is mentioned in any social networking site such as Facebook, YouTube and Wiki. It also provides you the usernames which mentions that particular keyword you entered.
Whostalkin
You need to search using name, email id, username or any related keyword. Whostalking searches the entered keyword in many different web sources and provides you the link where the particular keyword is mentioned.
Recordedfuture
This is the one I like most. This can be used for different purposes such as Cyber intelligence, Corporate Security, Competitive intelligence, Financial Services etc. but you can use this for Reconnaissance also.
The best thing regarding this application is that you can set the timeline in which you want to search.
You can search for people, places, time and events. In our case we are interested in collecting information about a person.
You need to register first to use this application but I must say you will find worth of it. After registration login to your account and click on ANALYZE. You will find a search bar in top right. Enter the name you want to search. Adjust the timeline in bottom. And click on search. It will show the links and details of the name mentioned anywhere in the internet. It also shows the summary on the right hand side of the page. As shown in Image2.
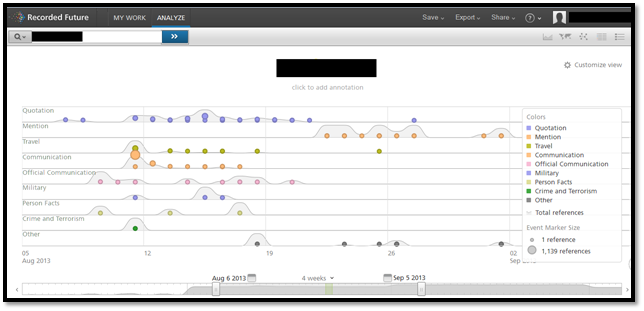
Image2: Recorded Future Timeline (Courtesy: RecordedFuture.com)
You can see the results in different forms such as timeline, map (As shown in Image3), network, table, feed, and tree map format.
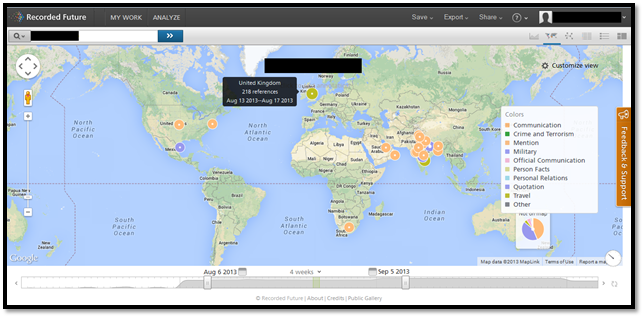
Image3: Recorded Future Event Map (Courtesy: RecordedFuture.com)
The result contains dates, link where the name is mentioned and some part of the post. It also minutely differentiates the results such as organization, person, product and many other. The Network view (As shown in Image4) shows how different results are connected to each other.
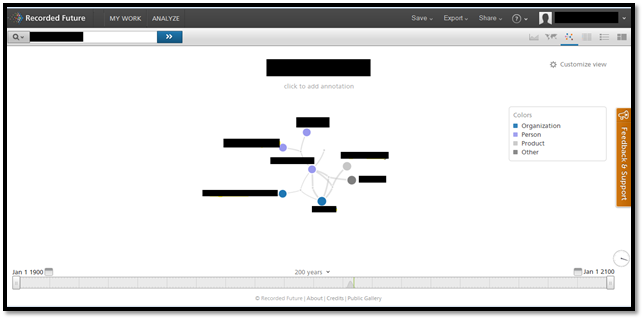
Image4: Recorded Future Event Network (Courtesy: RecordedFuture.com)
This application will provide information related to
-
Who is the first to report about the person you search for?
-
Which sources are reporting about the person you search for?
-
Quotes about the person you search for.
-
Who is mentioned together with the person you search for?
-
What else is associated with the person you search for?
-
Where is the person you searching for is travelling?
…and many more.
It's so interesting to get all this information in an organized manner. And it provides you the feature to customize your view according to group by event type, person, Location, First source and many more.
There are loads of features present in this application. You just need to explore.
Search information using image
Google image
If you want to search someone using image, what will be the best solution other than a powerful search engine. Just go to Google than click on images. In the right corner of the search bar you will find a camera icon. Click on that and it will ask you to paste image URL or upload image. Do any of these two and you will get not only similar image but also best match images in result.
https://www.google.co.in/imghp?hl=en&tab=wi
Tin Eye
Search for someone using image. You need to either provide the link of an image or simply download the profile picture of the target and upload to search. This site provides the links where same picture is used and also the links of the best match pictures. As shown in Image5.
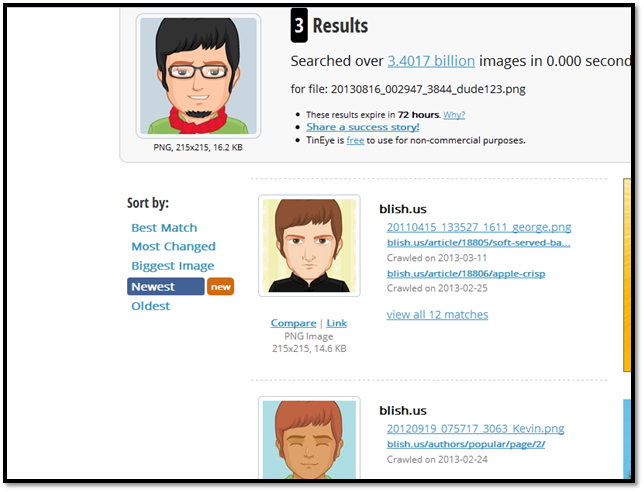
Image5: Tineye Result
Search information using address or telephone number
White pages
If you know the exact address of the target than use it to find the neighborhood. If you know the partial address than use it to find more details of that area. You can also search for information using telephone number.
http://www.whitepages.com/reverse_address
http://www.whitepages.com/reverse_phone
Search information using a post or discussion
Omgili
Sometimes people discuss about a particular topic in different forums or social networking sites. If you want to find information related to any of the posts of your target, you can use this site. It allows you either enter the detailed post or at least the keywords of the post to search weather any other forum or site has similar discussion.
Search information using IP address
IP address does not provide much information but still it will help to collect some information. I am not going to cover how to collect IP address (You can collect it using email). If you are having the IP address of the target then you can use any IP look up tool to collect the information such as http://whatismyipaddress.com/ip-lookup . It will provide you details such as ISP name, country, state, city, longitude and latitude.
Search information using Domain names
Sometimes domain names help us to find out important information such as address, email id and phone number. Just enter the domain name in http://whois.domaintools.com and click on lookup.
Tools
We came across different cases and how to collect information in that particular scenario manually but there are certain tools which will automate the process for you and provide information using web resources.
The Harvester
The Harvester is an open source intelligence tool (OSINT) for obtaining email addresses, sub domains, hosts, employee name, open ports and banners from public sources such as search engines. It's a simple python tool which is easy to use and contains different information gathering functions.
http://www.edge-security.com/theharvester.php
Generally we need a domain name or company name to collect information but we can use keyword also to collect related information. We can specify our search, such as to search from Google or Google-profiles or linked or all the web resources used by the harvester.
Collecting information using Google as a source (As shown in Image6).
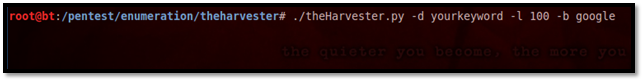
Image6: The Harvester Command
-d= Generally, domain name or company name but for our case it is for keyword
-l= Number of result limits to work with
-b= Specifying the data source
Collecting information using LinkedIn as source
#./theHarvester.py –d yourkeyword –l 100 –b linkedin
Collecting information using all the web resource
#./theHarvester.py –d yourkeyword –l 100 –b all
This tool provides you email addresses, hosts, virtual hosts etc. (As shown in Image7). This tool is useful when you know the company of your target or the domain owned by the target, then you can collect related information.
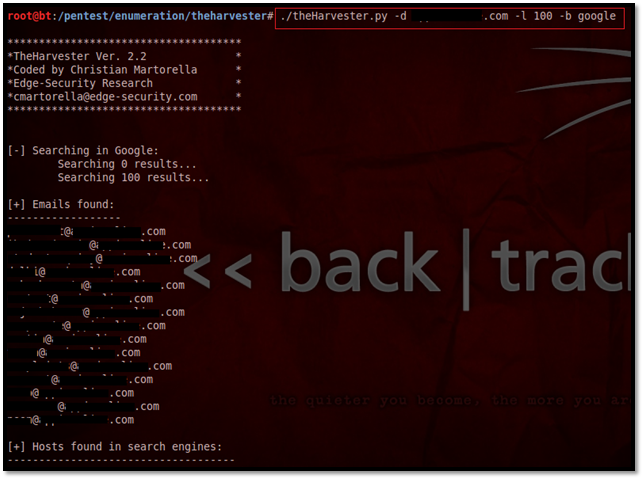
Image7: The Harvester Result
Maltego
Maltego is also an open source intelligence tool (OSINT). It's a little complex yet very effective tool. It collects information from different web sources and provides you with a relationship graph for link analysis and data mining. It helps you in analyzing real-world relationships between people, groups, websites, domains, networks, internet infrastructure etc. I like this tool, because it provides an overview of the entity relationship in a mind map manner.
http://www.paterva.com/web6/products/maltego.php
To use Maltego you need to register yourself first. It provides you a wide range of options to start with such as IP address, domain name, URL, location, name, email id etc. Start with any of these but in our case we will start with name.
Drag the Person entity to the center and in the property view edits its first name and last name. Right click and run different transformations. According to the information fetch from web resources Maltego will co relate among that information and will provide you with a relational network diagram (As shown in Image8). If you don't know which transformation to choose then run all transformations. It will provide all the result.
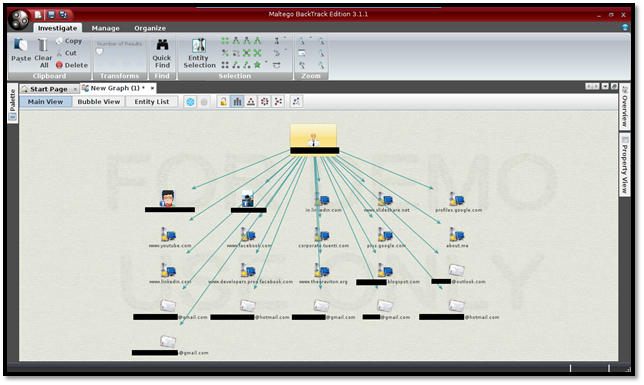
Image8: Maltego Result Main View
You can switch in to different types of views to see your result. You can insert, edit and delete the entities and its relationships. It's a tool with lots of features. Play with it more to find new possibilities.
Keeping track of all the information collected
CaseFile
Sometime it's better to keep track of all the information collected manually. But isn't it better to have a tool which will simplifies the process. And there comes CaseFile, a data visualization tool.
http://www.paterva.com/web6/products/CaseFile.php
CaseFile is another fine product of Paterva also known as Maltego CaseFile. It helps you build information map with tons of new features included such as attaching photos, documents, graph merging etc (As shown in Image9). It provides you simple interface to add, link and analyze data quickly and effectively.
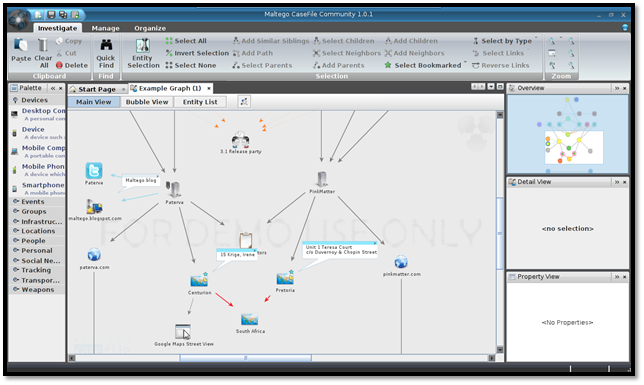
Image9: CaseFile Result
Why Dox Someone?
The intention behind Doxing someone is never good because the target has to face serious consequences. It can be done for many different reasons as I stated some of the motives earlier in the definition of Doxing. It is generally used for accepting challenge, taking revenge on someone, or simply harassing the enemy in public.
What are the consequences?
As Doxing discloses all the private information in public, it's a serious privacy concern. Apart from that it affects the virtual identity (Online Reputation), it can break the target mentally, it can be a threat to health and life, and it will affect the employment, business and social life. It might lead to identity theft. And in the worst scenario may be a reason for suicide. These are some of the serious consequences but it can be worse in real life.
You can be a victim
As internet became an essential part of our life. We started living dual life. One is the online life, where we have different usernames, different aliases, and different profile pictures in different places and other the offline life our physical life. As the definition of being social changed from meeting people outside to doing Google hang out and being online in different social networking sites. We started sharing information intentionally or unintentionally in internet. If you ask me personally how many sites you're registered in. I can't answer exactly. Because internet changed so rapidly and we also changed ourselves, in the mean while we forgot about those sites or thing we used to do earlier in internet. I think this is the case for most internet user. And taking benefit of this ignorance any attacker can collect our information from different sources of internet which makes each one of us vulnerable to be a victim of Doxing.
Help yourself not to be a victim
-
Don't provide all the personal information in any site if it is not mandatory.
-
If you provide personal information anywhere than make that profile private.
-
Use different user credentials for different sites.
-
Use different aliases in different sites.
-
Don't share your image in any profiles.
-
Don't show off too much in social sites.
-
Don't challenge any one.
Conclusion:
This can be utilized for good. As social media plays a huge role in everyone's life now days, it is one of the fastest media and covers all age group audience. We can use this technique to protest against social evils and disclose them totally in public media for greater good.
Reference:
https://www.ethicalhacker.net/columns/andress/doxing-and-anti-doxing-part-i
http://www.irongeek.com/i.php?page=security/doxing-footprinting-cyberstalking

FREE role-guided training plans










