The Evolution of a Technical Information Security Professional
During my years of work as a consultant and trainer in the information security world, I've noticed a few patterns that usually exist in those who do very well in the industry vs those who just make it by. I decided to draft this article to share some of the key elements and more importantly, give somewhat of a metric to gauge where you the reader currently sit.
Basically there seems to be 4 key levels that I consider to be different milestones or "levels of understanding" as related to this field. I originally heard a concept like this many years ago as it relates to music. Now I'm going to relate this more directly to penetration testing and exploit writing, but you can apply it to any area of specialization in information security.
Let's start with Level 1.
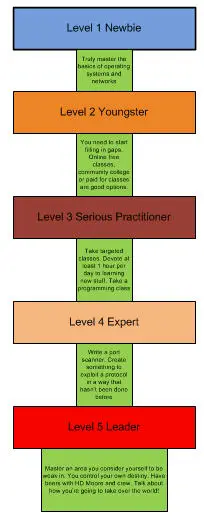
Level 1 – Interested Newbie – Unknowing and Unconscious
You don't know really how to learn these arts, plus you're unconscious of the fact that you don't know.
This level is where you've probably got your Security+ or you've gained the equivalent knowledge base by reading and "tinkering". You haven't learned how to exploit anything yet. You know what port scanning is, but you've never really done it. You're familiar with the terms Trojan, malware, rootkit, exploitation, etc. But you haven't actually had hands on with any of this, at least not knowingly **smile**.
Eventually you start playing with some tools. If you're a person who's said, "I downloaded Backtrack but I haven't figured out how to do anything with it yet," then you most likely fall into this category. Linux is still a big dark scary cloud for you (if you come from a Windows background), and vice versa if you're a Linux background person. You might have even taken a CEH class, and you feel like you saw a lot of cool stuff, but you can't really sit down and reproduce much of it.
Level 2 – Practicing Youngster (a year or two in) Knowing and Unconscious
You now know a little bit about how to learn these techniques but you're still unconscious of what you don't know.
You're still new to the field. You might have a job that requires you to work with firewalls a little or maybe support of some type. Your inner hacker curiosity has you spending lots of time tinkering with security tools and techniques even though it might not be part of your job. You can run some security tools. You are not "too" afraid of Linux anymore. You've been able to get Backtrack to communicate with your network. You've learned how to set IP addresses in Linux, and you're comfortable doing basic things from the shell. You have learned how to use Nmap somewhat. Additionally you've also found one or two forums which you like to visit and learn new things from.
The information in these forums end up being pretty basic, but at the level you're at right now, you've found the more advanced forums like the official Metasploit one to be too technical for you. You maybe visit your first Blackhat/Defcon conference. You leave there realizing for the first time how much you really don't know. You reach a point of information overload. You enjoy the conference and see lots of eye-popping demonstrations, but you don't really understand how it works or what the implications really are. You leave Blackhat with the gut punching realization that you lack the technical ability to demonstrate or recreate anything you've witnessed. And this is where you actually start to learn.
Level 3 – Serious Practitioner – Knowing and Conscious
At this point you know how to learn the skills, and you're conscious of the fact that there are limitless amounts of stuff you don't know, and additionally you have an idea about the many different aspects and fields within information security. You truly grasp that reverse engineering, exploit writing, and penetration testing are not one big blob of variations of the same thing. You realize that they can all complement each other but they're not the same. You have gained enough skills to be great one day, but you might not ever truly have the time, or invest the time required, to get to the next level.
It's been a couple of years or so since you went to Blackhat/Defcon the first time. Now you go back and you understand exponentially more than you did the first time. You're able to come back and duplicate most of what you've seen in the presentations. You also understand what you've seen well enough to demo and present it to others. If you've never learned to code you have at this point realized that it's going to hinder you at some point in your career. You've started to learn some scripting languages and you're pretty good with them (Perl, Python, etc). You're aggressively trying to learn C not C+, C++, C# or any of those, but just C. Why? Because a respected security professional told you that you really needed to learn it.
You're also trying to learn Assembly because you've been told that you really needed to know it to write exploits. You view exploit writing and reversing as the next thing you want to accomplish from a learning perspective. But you've realized you need to know programming concepts and constructs well to truly reverse and write exploits. You are able to follow exploit writing examples without problem, but your understanding of memory, calls, packing, etc. keeps you from doing it "for real". If someone gave you a Backtrack CD and a couple of Windows computers and asked you to demonstrate a client side exploit, a server side exploit, and how scanning works, you could do it with no problem. You know TCP and IP like you know your name. You can look at a packet capture and instantly pick out three-way handshakes and other session establishments. You still don't really know web applications that well, because you still don't know programming and applications that well. You can demonstrate fluently all of the OWASP top 10, but you still feel there's a lot missing.
Congratulations, you've reached the point where most security professionals stop or plateau.
Level 4 – Expert – Knowing and Unconscious
You are above most in both skill and knowledge. You know that there are things you don't know, but you learn them frequently. It's almost as if it's a drug to you. You sit with your laptop daily/nightly and plug into forums, YouTube videos, presentations, coding etc. Every night for you seems as if you've plugged your brain into the Matrix and had information dumped into it.
While you know there are things you want to learn, you don't even know or bother to figure out "how" you're learning them. Your skills are mature enough to where you just "do". You learn without knowing how. When you do present or demonstrate stuff to others, you're often told that you go way too fast and really, you assume that your audience understands more than they actually do.
There is no looking back now. The only thing that drives you really is learning more. You're also very much into finding new exploits, and finding new ways to use old exploits. While information security may or may not be your job, it is now your passion.
Level 5 – Leader - Unknowing and Unconscious
You are now at the very top of the field. Whether the rest of the world knows it or not is not relevant. You are not conscious of what you don't know because you simply don't care. You have obtained a body of knowledge that puts you in a position to where if you want to learn something, you simply learn it. Nothing about exploitation, or information security seems out of your reach. The only reason you don't learn something is because you don't want to. You are now a creator, a driver, and an industry shifter. You are one of the people who puts out what others must learn. The industry doesn't control what you need to know, you control what the industry needs to know. A few names come to mind for me: HD Moore, Dan Kaminsky and others. For example, Metasploit, the brainchild of HD Moore, literally changed exploitation and exploit development forever. Dan Kaminsky's DNS research a few years ago caused visible shifts in attention paid to infrastructure security as related to things like DNS.
Most people will never make it to this level. Not because people aren't smart enough. It's because maybe you won't be able to put the time in. Or maybe you won't have access to resources needed (some countries filter all Internet traffic). To say HD Moore accomplished what he has simply because he is smart would completely ignore all the obvious huge amounts of time and hard work he's put in over the years. I think one has to have certain proclivities to reach this level, but I also think the time investment is more important than anything else. Below I created a graphic to illustrate this better.