The importance of cyber hygiene in cyberspace
The drastic increase in the frequency of cyber attacks on financial systems and the healthcare industry (both large and small scale industries) have raised concerns about security at every level of organizations. A recent Australian Securities and Investments Commission (ASIC) "Cyber-resilience health-check" report says that industry feedback will further tighten the financial services and other regulated sectors. Organizations need to be better-prepared to respond, adapt to and recover from unprecedented cyber-attacks. These attacks are escalating across the data-driven, mobile, Internet and cloud-based services' sectors, says ASIC. Cyber criminals and hackers are trying different types of malware based attacks on their victims. Recently, ransomware, a type of malware has been making rounds as a popular hacker trick to take over a victim's computer and blackmail for cash.Crypto-ransomware has become a popular way to extract money from victims who inadvertently download the malware. These new variants of malware allow cyber criminals to launch multiple types of attacks on individuals and organizations.

What should you learn next?
Defining cyber hygiene
In the era of the digital age, we rely extensively on the Internet and storage devices for many aspects of our lives, so the need to be proactive and vigilant to protect against cyber threats has never been greater. To achieve security within the domain, we need to adapt a good cyber hygiene strategy, that is, making sure we are protecting and maintaining systems and devices appropriately and using cyber security best practices for anything and everything that connects to the web. It includes organizing security in hardware, software and IT infrastructure, continuous network monitoring, and employee awareness and training. The Center for Internet Security (CIS) and the Council on Cyber Security (CCS) defines cyber hygiene as a means to appropriately protect and maintain IT systems and devices and implement cyber security best practices.
CIS and CCS introduced the Cyber Hygiene Campaign, with the vision of providing a low-cost program for enabling immediate and effective defenses against cyber attacks. The campaign's top priorities address the vast majority of known cyber threats:
- Count: Know what's connected to and running on your network
- Configure: Implement key security settings to help protect your systems
- Control: Limit and manage those who have administrative privileges for security settings
- Patch: Regularly update all apps, software, and operating systems
- Repeat: Regularly revisit the Top Priorities to form a solid foundation of cyber security
Lack of security controls in a modern information system which eventually increases the likelihood of a cyber risk or a data breach can be termed as a cyber mess. Cyber mess can be classified into two categories focusing on technical and non-technical issues. A technical cyber mess can occur because of absence of the following:
- AAA – Authentication, Authorization and Accounting
- Access Controls – Data Level and Function Level Access Controls
- Monitoring – Security Monitoring and Security Intelligence
- Plan – Incident Response Plan
- Security Patches and Remediation process – Vulnerability Management
- Managed Cyber Risks – Continued Risk Assessments
Non-technical issues mainly concentrate on absence of employee training, security awareness, organization policies and social engineering awareness.
Companies should adopt the necessary best practices and apply continuous monitoring and mitigation to achieve immediate and effective defenses against cyber-attacks. Yaacob Ibrahim, Singapore's Minister of communication and Information says, "We need individuals to practise good cyber hygiene and safe surfing habits at work and at home, and we need all organizations to take ownership of your systems' cyber security and play your part."
Lack of cyber hygiene is leading to cyber attacks and cyber threats
Ransomware is a type of malware which restricts access to data or a computer system that it infects, and demands a ransom paid to the hacker. It infiltrates a computer right after a user clicks on a link or attachment in an email. It can also attack when a user visits a website. It encrypts and locks up internal files of the system and makes them impossible to use. It can also lock up a network of computer systems if it infects a server.
CryptoLocker appeared several years ago, and made files like word processing, documents and photographs inaccessible to users unless they paid a ransom of $500 - $700. Due to the length of the key employed by CryptoLocker, experts considered it practically impossible to use a brute-force attack to obtain the key needed to decrypt files without paying. A similar 2008 trojan Gpcode.AK used a 1024-bit key that was believed to be large enough to be computationally infeasible to break without a concerted distributed effort, or the discovery of a flaw that could be used to break the encryption.
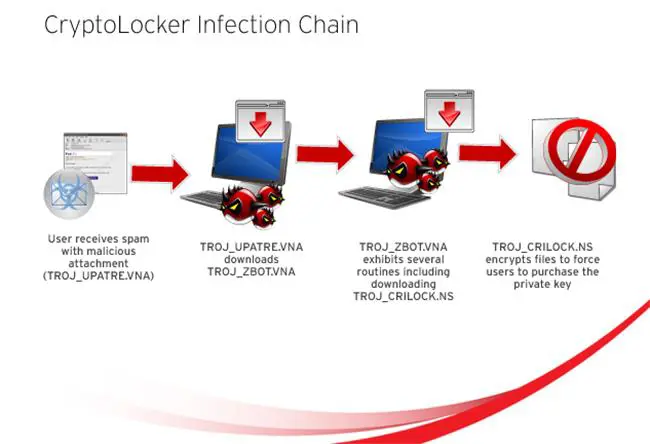
The majority of ransomware go unreported for the reason that persons or companies are embarrassed about having been hacked or paid a ransom. Cybercriminals behind these threats make use of online payment methods such as Ukash, PaySafeCard, MoneyPAK or Bitcoin as a way for users to pay the ransom.
Ransomware continues to evolve and target a large number of organizations. During January 2015, CryptoWall 2.0, a new type of ransomware, was discovered. It utilized Tor to obfuscate the command and control channel. These ransomware variants encrypt the user's data, thus making it unusable until a ransom is paid to retrieve the decryption key. The dropper and downloaded Cryptowall binary actually incorporate multiple levels of encryption. One of the most interesting aspects of this malware is its capability to run 64 bit code directly from its 32 bit dropper. Under the Windows 32-bit on Windows 64-bit (WOW64) environment, it is indeed able to switch the processor execution context from 32 bit to 64 bit. Similarly in CryptoWall 3.0, the dropper is encrypted with a custom algorithm three times. CryptoWall are mostly used as the payload of spammed messages. While other crypto-ransomware variants have a graphical user interface (GUI) for their payment purposes, CryptoWall relied on other means, by opening a Tor site to directly ask for payment or opening the ransom note in Notepad, which contained the instructions to access a payment page via a Tor browser.
These days, many ransomwares are not using Tor for their command and control servers. CryptoWall 3.0 uses hardcoded URLs. Admittedly, using Tor can be seen as an advantage for the anonymity offered. But the disadvantage is that system admins could easily block Tor network traffic or even the Tor application itself if there is no need for it. The hardcoded URLs are heavily obfuscated so threat researchers wouldn't extract them easily. Since URL blocking is reactive, there is a delay before the blocking can be implemented. During this "window," the malware could have already communicated with the command and control server and acquired the RSA public key to be used for file encryption. The command and control server is different from its payment page. The malware still uses Tor for its payment page so that transactions wouldn't be hindered if authorities try to bring down their payment servers. And perhaps as a "precautionary measure," CryptoWall 3.0 deletes the system's shadow copies to disable restoring files to their previous state, rendering victims with no other options for saving their files.
Cyber criminals are also targeting the government and police departments. Recently, the Chicago police department also agreed to pay a $500 ransom in February 2015. "Because the backups were also infected, the option was to pay the hacker and get the files unencrypted," says Calvin Harden, an IT vendor working with the police department to overcome crypto-ransomware. In almost all cases of malware infections, phishing has been one of the most common tricks, and opening a malicious email attachment by a victim that unleashed the crypto-malware onto the system.
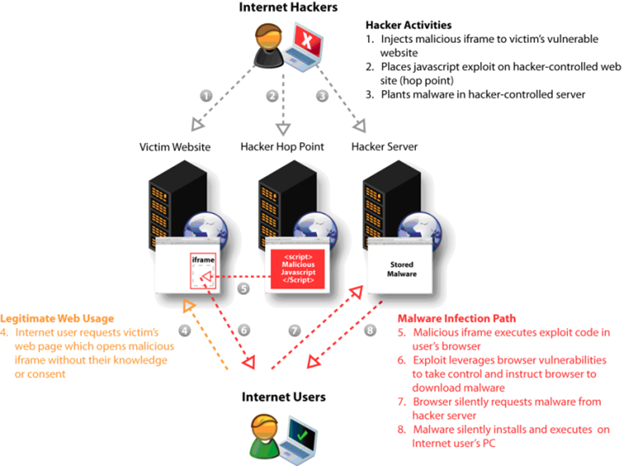
Malware injection through web applications includes following stages:
- Hacker identifies the vulnerable entry point in the application.
- Injects malicious iframe to victim's website.
- Constructs and plants JavaScript exploit on hacker's website.
- Malware is planted at the hacker's server.
- Internet user requests the victim's website, which initiates the iframe to execute the exploit code in the user's browser without their knowledge.
- The browser is then silently instructed to download a malware from the attacker's server.
- This malware is then installed and executed in the victim's PC.
Finding and securing the weakest link
A layered security approach is the best method to identify and stop cyber attacks and malware infections. Cyber criminals are always on the lookout for the weakest link in the security chain. The cyber hygiene principle emphasizes breaking any step in the cyber attack chain, which will successfully prevent the attack. Therefore, blocking the initial phishing emails, blocking network connections to known malicious content, as well as stopping malicious process activity are critical to combating cyber threats.
The real challenge is translating complex, technical cyber data into practical information that can be easily understood by the business as well as security pros. Many variables come into play when it comes to understanding cyber risk: industry sector, infrastructure, company size, supply chain, location, your online presence, data storage techniques, and many more factors. Cyber hygiene can include basic steps like patching vulnerable systems, mitigating known threats in application, hardening servers and network sensors.
Social engineering has been one of the most popular methods in attacking the weakest link in the security chain. Even well-equipped and security aware companies have been a victim of data breach that resulted from attackers exploiting employees or company vendors. Attackers may make emails appear to come from someone that the target knows, a source they would trust, or contain information that would be relevant to the target's professional role. Simple security awareness training is not an effective method to train employees on cyber threats. Effective real-world training and actively testing the employees can be the best approach to educate the workforce. This approach of securing the weakest link would reduce the surface to a large extent. Not just humans, even a weak spot in software systems can be an alarming reason for a cyber attack.
Best practices in cyber hygiene
Individuals and organizations must adopt procedures and policies to identify the weakest links and security loopholes. Implementing security at every level from application development, infrastructure hardening, network monitoring, Bring Your Own Device (BYOD) policies, to employee awareness is a crucial part in solving the security problem.
Identify: Identifying every device that is connected to the Internet. Any device that is connected to the Internet is vulnerable to cyber attack. It creates an attack surface and an entry point for the cyber criminals.
Prioritize: Ranking and categorizing devices and applications based on sensitivity and data exposure. Prioritizing tasks, risks and response plans will reduce the workload for the security engineers and system administrators.
Security Hardening: Devices, systems and applications must be hardened to secure and reduce the entry point for a cyber-attack. It includes encryption of data at rest and data at transit, two-factor authentication, password policies, secure configuration audits and vulnerability assessments.
Security Patches: Implementing patch and vulnerability management in all devices and systems.According to a Verizon 2015 data breach investigation report, many existing vulnerabilities remain open, primarily because security patches that have long been available were never implemented. In fact, many of thevulnerabilities are traced to 2007, a gap of almost eight years.
Backup: Companies must implement a good backup policy. Regular backup of important data is part of a good backup strategy for data security. It is the last defense against data loss or data theft. Incorporating a data recovery process will ensure that you can actually recover data from your backup.
Effective training: Training is one of the most cost-effective controls. Because people are the weakest link in cyber security, training should start with employees and higher management. But it is also a good idea to extend it to your customers through a customer education program. Ensure staff are educated in good computing practices and how to spot threats. Educate employees on real-life cyber security problems. According to the European Network and Information Security Agency, "Awareness of the risks and available safeguards is the first line of defense for the security of information systems and networks."

What should you learn next?
Sources
Financial services face cyber attacks
Implement good cyber hygiene with continuous network monitoring
Social engineering attacking the weakest link









