Awesome modules of Recon-ng used for Web Recon testing
In my previous article, I wrote an introduction to the Recon-ng Framework and its basic usage, which is primarily used for automatic information gathering and web reconnaissance. In this write-up, we will still talk about Recon-ng and will focus on the modules that are used for web recon testing purposes. Web recon testing is very vital for penetration testers in order to check for the flaws in the website or system and gather some information like the basic functionality of the website, accessibility, browser compatibility, performance, and the web technologies that are used by the website.
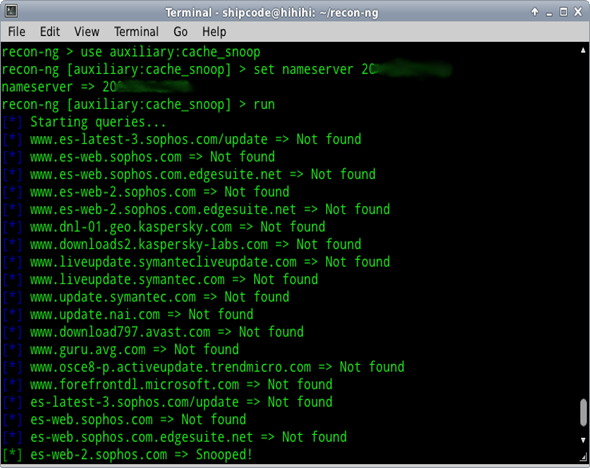
DNS cache snooper

FREE role-guided training plans
This auxiliary module is contributed by thrapt and is used for checking a name server's visited domains by using a technique called DNS cache snooping (Scraping). It makes non-recursive queries to the client's DNS servers with the use of known Antivirus update site domains so that we can check possible antivirus vendors that are used on a client's network. Below are the sites included in the Recon-ng Framework for the auxiliary:cache_snoop module which can be found under data/av_domains.lst:
www.es-latest-3.sophos.com/update
www.es-web.sophos.com
www.es-web.sophos.com.edgesuite.net
www.es-web-2.sophos.com
www.es-web-2.sophos.com.edgesuite.net
www.dnl-01.geo.kaspersky.com
www.downloads2.kaspersky-labs.com
www.liveupdate.symantecliveupdate.com
www.liveupdate.symantec.com
www.update.symantec.com
www.update.nai.com
www.download797.avast.com
www.guru.avg.com
www.osce8-p.activeupdate.trendmicro.com
www.forefrontdl.microsoft.com
es-latest-3.sophos.com/update
es-web.sophos.com
es-web.sophos.com.edgesuite.net
es-web-2.sophos.com
es-web-2.sophos.com.edgesuite.net
dnl-01.geo.kaspersky.com
downloads2.kaspersky-labs.com
liveupdate.symantecliveupdate.com
liveupdate.symantec.com
update.symantec.com
update.nai.com
download797.avast.com
guru.avg.com
osce8-p.activeupdate.trendmicro.com
forefrontdl.microsoft.com
Thus, if you happen to know other antivirus update site domains, you can just simply add one on the av_domains.lst file or even contribute to this project by making a pull request.
WhatWeb web technologies scan
This auxiliary module is contributed by thrapt and it leverages WhatWeb.net to recognize web technologies that are being used by the target like its Content Management System (CMS), JavaScript libraries, web servers, embedded devices, email addresses, account IDs, web framework modules, SQL errors, Google Analytics, blogging platforms, plugin versions, etc…
Sample Usage:
[plain]
recon-ng> use auxiliary:whatweb
recon-ng [auxiliary:whatweb] > set source infosecinstitute.com
source => infosecinstitute.com
recon-ng [auxiliary:whatweb] > run
https://www.infosecinstitute.com [301] HTTPServer[Apache/2.2.23],
RedirectLocation [https://www.infosecinstitute.com/],
Apache [2.2.23],
IP [216.92.251.5],
Title [301 Moved Permanently],
Country[UNITED STATES][US]
https://www.infosecinstitute.com/ [200] X-UA-Compatible[IE=EmulateIE7],
HTTPServer [Apache/2.2.23],
Google-Analytics [UA-146509-2],
Apache[2.2.23],
IP[216.92.251.5],
JQuery, Title[InfoSec Institute - Information Security Training and IT Boot Camps],
Country[UNITED STATES][US]
[/plain]
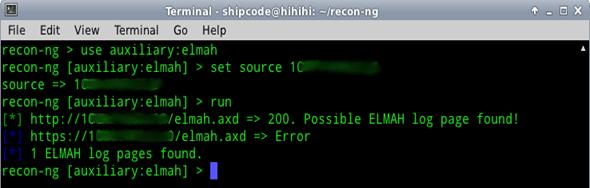
ELMAH log scanner
This module is one of the first auxiliary modules started by Tim Tomes a.k.a LaNMaSteR53, the main author of the Recon-ng Framework. This scanner checks for the 'elmah.axd' log page, an error logging module and handler that can be dynamically added to a running ASP.NET web application, or even to all ASP.NET web applications on a machine, without theneed for re-compilation or re-deployment. But there is a problem with this page –it can possibly be used by attackers for ASP.NET session hijacking because of the .ASPXAUTH cookie.
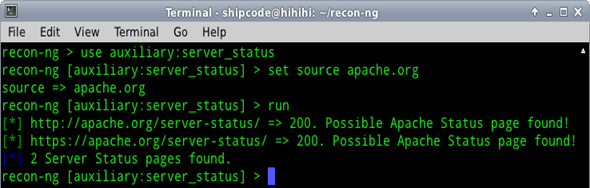
Apache server-status page scanner
This auxiliary module checks if a certain website has an Apache server-status page which allows administrators to check if the server of their website is doing well. The page shows the Server Version, CPU Usage, Active Connections, Child Server number generation, some OS process ID's, and other details which are related to the Apache Server. A security researcher named Daniel Cid said, "probably not a big deal by itself (well, if you don't have an unprotected admin panel), but that can help attackers easily find more information about these environments and use them for more complex attacks."
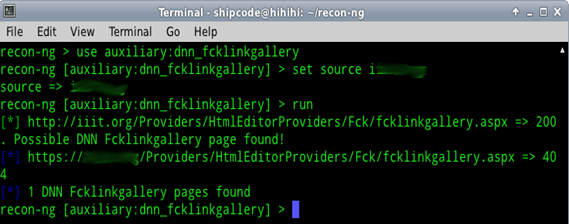
Dot Net Nuke (DNN) remote file upload vulnerability checker
This is the module that I contributed and was recently added by the main author of the Recon-ng Framework to the main repository. This auxiliary module checks for a Dot Net Nuke (DNN) fcklinkgallery.aspx page which is possibly vulnerable to Remote File Upload and allows other viewers to browse through the files that were uploaded to the web server. In most cases, you can see ASP backdoor shells and text files uploaded by some exploiters. This is an old vulnerability but there are still a lot of web administrators that haven't upgraded their DNN version and patched this vulnerability yet on their website.
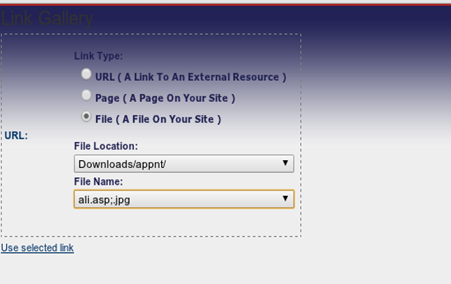
By replacing the URL in the browser with javascript:__doPostBack('ctlURL$cmdUpload',''), it allows the attacker to upload a text or an image file.
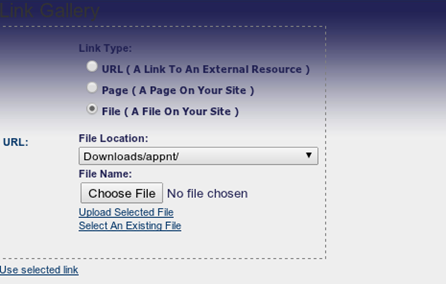
Below is the source code of this module:
[plain]import framework
# unique to module
class Module(framework.module):
def __init__(self, params):
framework.module.__init__(self, params)
self.register_option('source', 'db', 'yes', 'source of module input')
self.register_option('verbose', self.goptions['verbose']['value'], 'yes', self.goptions['verbose']['desc'])
self.classify = 'active'
self.info = {
'Name': 'Dot Net Nuke Remote File Upload Vulnerability Checker',
'Author': 'Jay Turla (@shipcod3)',
'Classification': '%s Reconnaissance' % (self.classify.title()),
'Description': 'Checks the hosts for a DNN fcklinkgallery page which is possibly vulnerable to Remote File Upload.',
'Comments': [
'Source options: db, <hostname>, <path/to/infile>',
'http://www.exploit-db.com/exploits/12700/',
]
}
defdo_run(self, params):
if not self.validate_options(): return
# === begin here ===
self.check_for_dnnfcklink()
defcheck_for_dnnfcklink(self):
verbose = self.options['verbose']['value']
hosts = self.get_source(self.options['source']['value'], 'SELECT DISTINCT host FROM hosts WHERE host IS NOT NULL ORDER BY host')
if not hosts: return
# check all hosts for DNN fcklinkgallery page
protocols = ['http', 'https']
cnt = 0
for host in hosts:
for proto in protocols:
url = '%s://%s/Providers/HtmlEditorProviders/Fck/fcklinkgallery.aspx' % (proto, host)
try:
resp = self.request(url, redirect=False)
code = resp.status_code
except KeyboardInterrupt:
print ''
return
except:
code = 'Error'
if code == 200 and '> Link Gallery' in resp.text:
self.alert('%s => %s. Possible DNN Fcklinkgallery page found!' % (url, code))
cnt += 1
else:
if verbose: self.output('%s => %s' % (url, code))
self.output('%d DNN Fcklinkgallery pages found' % (cnt))
[/plain]
Hosting history
The Hosting History is an auxiliary module contributed by thrapt which checks for the hosting history of the given target by using Netcraft.
Sample Usage:
[plain]recon-ng> use auxiliary:netcraft_history
recon-ng [auxiliary:netcraft_history] > set source infosecinstitute.com
source => infosecinstitute.com
recon-ng [auxiliary:netcraft_history] > run
[*] URL: http://uptime.netcraft.com/up/graph?site=infosecinstitute.com
[*] Setting cookie...
[*] URL: http://uptime.netcraft.com/up/graph?site=infosecinstitute.com
OS | Server | Last Changed | IP Address | Owner
-----------------------------------------------------------------------------------------
| FreeBSD | Apache/2.2.23 | 10-Feb-2013 | 216.92.251.5 | pair Networks
| FreeBSD | Apache/2.2.23 | 27-Nov-2012 | 216.92.251.5 | pair Networks
| FreeBSD | Apache/2.2.22 | 22-Sep-2012 | 216.92.251.5 | pair Networks
| FreeBSD | Apache/2.2.22 | 25-Jul-2012 | 216.92.251.5 | pair Networks
| FreeBSD | Apache/2.2.22 | 07-May-2012 | 216.92.251.5 | pair Networks
| FreeBSD | Apache/2.2.21 | 15-Dec-2012 | 216.92.251.5 | pair Networks
| FreeBSD | Apache/2.2.19 | 16-Jul-2011 | 216.92.251.5 | pair Networks
| FreeBSD | Apache/2.2.17 | 11-Apr-2011 | 216.92.251.5 | pair Networks
| FreeBSD | Apache/2.2.17 | 06-Mar-2011 | 216.92.251.5 | pair Networks
| FreeBSD | Apache/2.2.10 | 22-Jul-2009 | 216.92.251.5 | pair Networks
[/plain]
robots.txt/sitemap.xml Finder
This auxiliary module checks the host for a robots.txt, sitemap.xml and sitemap.xml.gz file. Its classification is Active Reconnaissance and is authored by thrapt.
Sample Usage:
[plain]
recon-ng> use auxiliary:robots
recon-ng [auxiliary:robots] > set source google.com.ph
source => google.com.ph
recon-ng [auxiliary:robots] > run
[*] http://google.com.ph/robots.txt => 301
[*] http://google.com.ph/sitemap.xml => 301
[*] http://google.com.ph/sitemap.xml.gz => 301
[*] https://google.com.ph/robots.txt => 200. robots.txt found!
[*] https://google.com.ph/sitemap.xml => 503
[*] https://google.com.ph/sitemap.xml.gz => 503
[*] 1 files found.
[/plain]
Server side enumerator
This auxiliary module is authored by Tim Tomes and Kenan Abdullahoglu. It is used for analyzing response headers, cookies, and errors to determine which server-side technology is being used (PHP, .NET, JSP, CF, etc.).
Sample Usage:
[plain]
recon-ng> use auxiliary:server_enum
recon-ng [auxiliary:server_enum] > set host apache.org
host => apache.org
recon-ng [auxiliary:server_enum] > run
----------------------START-----------------------
[*] ORIG_URL: http://apache.org
[*] DEST_URL: http://apache.org
---------------------HEADERS----------------------
[*] CONTENT-LENGTH: 37073
[*] ACCEPT-RANGES: bytes
[*] EXPIRES: Sun, 10 Feb 2013 10:45:37 GMT
[*] VARY: Accept-Encoding
[*] SERVER: Apache/2.4.3 (Unix) OpenSSL/1.0.0g
[*] LAST-MODIFIED: Sun, 10 Feb 2013 09:10:24 GMT
[*] CONNECTION: close
[*] ETAG: "90d1-4d55b29aae09c"
[*] CACHE-CONTROL: max-age=3600
[*] DATE: Sun, 10 Feb 2013 09:45:37 GMT
[*] CONTENT-TYPE: text/html; charset=utf-8
---------------------COOKIES----------------------
-----------------------END------------------------
URL: http://apache.org
SERVER: Apache/2.4.3 (Unix) OpenSSL/1.0.0g | Apache |
ERROR: 404 (/ynkqixawzs.kyw) | Apache |
[/plain]
Host discovery
There are hostname enumerator modules under the Host category that allows you to check for additional subdomains of your target. Here are the modules that you can use for host discovery:
- hosts:baidu–Baidu Hostname Enumerator
- hosts:bing– Bing Hostname Enumerator
- hosts:brute_force– DNS Hostname Brute Forcer
- hosts:google– Google Hostname Enumerator
- hosts:netcraft–Netcraft Hostname Enumerator
- hosts:shodan–Shodan Hostname Enumerator
- hosts:yahoo– Yahoo Hostname Enumerator
Sample Usage with Google Hostname Enumerator:
[plain]
recon-ng> use hosts:google
recon-ng [hosts:google] > set domain infosecinstitute.com
domain => infosecinstitute.com
recon-ng [hosts:google] > run
[*] URL: http://www.google.com/search?q=site%3Ainfosecinstitute.com&start=0&filter=0
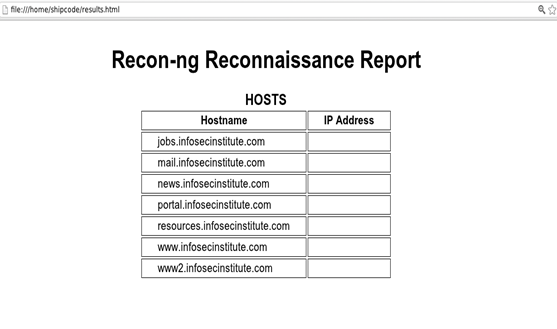
[*] www.infosecinstitute.com
[*] jobs.infosecinstitute.com
[*] resources.infosecinstitute.com
[*] Sleeping to Avoid Lock-out...
[*] URL: http://www.google.com/search?q=site%3Ainfosecinstitute.com+-site%3Awww.infosecinstitute.com+-site%3Ajobs.infosecinstitute.com+-site%3Aresources.infosecinstitute.com&start=0&filter=0
[*] news.infosecinstitute.com
[*] portal.infosecinstitute.com
[*] www2.infosecinstitute.com
[*] mail.infosecinstitute.com
[*] Sleeping to Avoid Lock-out...
[*] URL: http://www.google.com/search?q=site%3Ainfosecinstitute.com+-site%3Awww.infosecinstitute.com+-site%3Ajobs.infosecinstitute.com+-site%3Aresources.infosecinstitute.com+-site%3Anews.infosecinstitute.com+-site%3Aportal.infosecinstitute.com+-site%3Awww2.infosecinstitute.com+-site%3Amail.infosecinstitute.com&start=0&filter=0
[*] Final Query String: http://www.google.com/search?q=site%3Ainfosecinstitute.com+-site%3Awww.infosecinstitute.com+-site%3Ajobs.infosecinstitute.com+-site%3Aresources.infosecinstitute.com+-site%3Anews.infosecinstitute.com+-site%3Aportal.infosecinstitute.com+-site%3Awww2.infosecinstitute.com+-site%3Amail.infosecinstitute.com&start=0&filter=0
[*] 7 total hosts found.
[/plain]
The Recon-ng Framework has modules to extract the results in a CSV format or in an HTML file. In my case, I used the output:htmlfile module to generate an HTML report, as seen below:
[plain]
recon-ng> use output:htmlfile
recon-ng [output:htmlfile] > set filename /home/shipcode/results.html
filename => /home/shipcode/results.html
recon-ng [output:htmlfile] > run
[*] Report generated at '/home/shipcode/results.html'.
[/plain]
Free hour-long hacking course!
Learn how to hack and use AI in this free 1-hour course, led by Keatron Evans, 20-year cybersecurity veteran and VP of Portfolio Product and AI Strategy at Infosec!
Sources
Recon ng framework automated information gathering
DNS scraping for corporate av detection










