ESET Rule the Code - CrackMe Challenge Part 1: The Unpacking Process
1. Presenting the Problem
The CrackMe challenge was first observed on the ESET CrackMe web page, which looked like the the picture below:

What should you learn next?

What should you learn next?
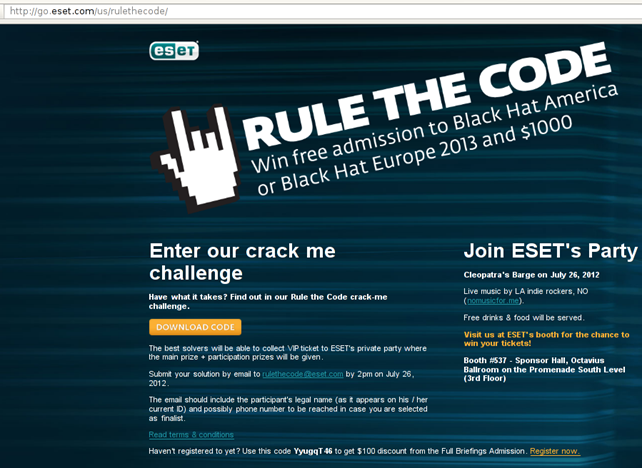
On the web page we can observe that the challenge is being held at Black Hat 2012. The winner will receive free entry into one of the conferences, either Black Hat America or Black Hat Europe, in 2013, plus a thousand dollars.
We can also see the download link where the crackme.exe program can be downloaded. The program is still accessible on their web page, so you can also try to download and crack it.
2. Unpacking the Program
Upon downloading the program crackme.exe, we can normally run it without any problems. The program looks like the picture presented below:
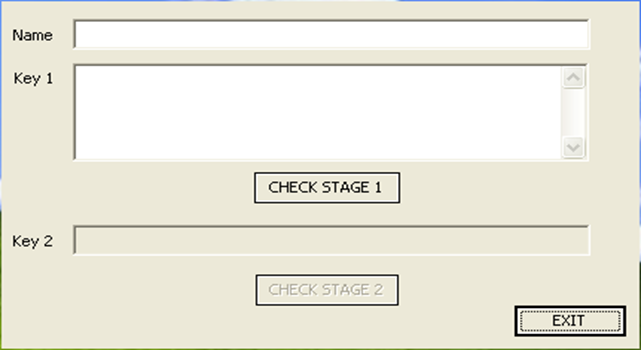
We can see that at first we need to enter the Name and Key 1 for the Key 2 to become available, which must also be filled in correctly.
If we try to run the program with OllyDbg debugger, we can quickly see that our program crackme.exe is encoded. We can see the warning message that Ollydbg presented in the picture below:
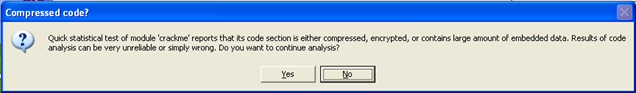
This could greatly complicate our debugging, so it's better to decode the program first before trying to debug it. We could debug the encoded version of the program, but it could present complications, maybe even premature termination of the program.
So the first thing to do is to download a program that is able to detect most commonly used packers or encryptors, the PEiD tool. After opening our crackme.exe program with PEid, we can see what the picture below presents:
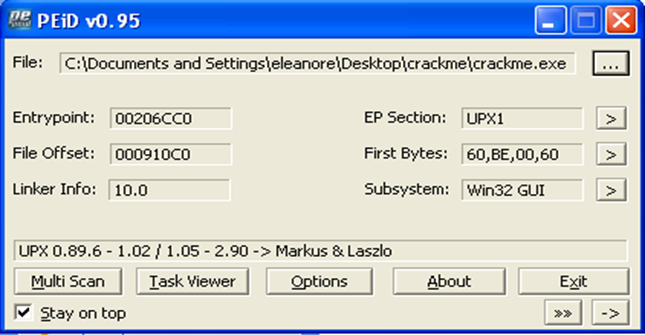
We can immediately see that the program is encoded with a standard ultimate packer for executables named UPX. This is an open source packer and can be easily downloaded and installed. When we download and run upx.exe we get the default help page presented in the following section:
C:Documents and SettingseleanoreDesktopupx308w>upx.exe
Ultimate Packer for eXecutables
Copyright (C) 1996 - 2011
UPX 3.08w Markus Oberhumer, Laszlo Molnar & John Reiser Dec 12th 2011
Usage: upx [-123456789dlthVL] [-qvfk] [-o file] file..
Commands:
-1 compress faster -9 compress better
-d decompress -l list compressed file
-t test compressed file -V display version number
-h give more help -L display software license
Options:
-q be quiet -v be verbose
-oFILE write output to 'FILE'
-f force compression of suspicious files
-k keep backup files
file.. executables to (de)compress
Type 'upx --help' for more detailed help.
UPX comes with ABSOLUTELY NO WARRANTY; for details visit http://upx.sf.net
It's clear that we need to use the option -d to decompress the compressed executable. To decompress the executable we must run the following command:
> upx.exe -d -o main.exe crackme.exe
Ultimate Packer for eXecutables
Copyright (C) 1996 - 2011
UPX 3.08w Markus Oberhumer, Laszlo Molnar & John Reiser Dec 12th 2011
File size Ratio Format Name
-------------------- ------ ----------- -----------
2064384 <- 1041920 50.47% win32/pe main.exe
Unpacked 1 file.
The new unpacked executable file is named main.exe and is put into the same directory as crackme.exe. If we run OllyDbg with our new main.exe, the Olly doesn't complain anymore and starts normally.
3. Conclusion

Get your guide to the top-paying certifications
With more than 448,000 U.S. cybersecurity job openings annually, get answers to all your cybersecurity salary questions with our free ebook!

Get your guide to the top-paying certifications
With more than 448,000 U.S. cybersecurity job openings annually, get answers to all your cybersecurity salary questions with our free ebook!
In this part of the tutorial we've looked at the unpacking process of the crackme.exe program. In the next tutorials we'll try to analyze the first challenge, where we need to enter the right Name and Key 1 value.










