Dictionary attack using Burp Suite
Nowadays internet usage is growing dramatically because of this, a vast majority of companies and individuals that provide services have a website so customers can know about the service(s) that is available to them. These companies and individuals usually have an access portal that will ask their customers to enter a chosen username and password, If the credentials are valid, customers will be redirected to the home page of that particular user. Moreover, the access portal is an administrative access portal which if you have successfully logged in, you will have full access on that application. From this point of view we can assume that choosing a password is a critical issue and everyone should be aware while choosing their password.
Today we are going to talk about attacking these portals to gain access to the administrative panel using a password brute-forcing technique called Dictionary attack.

FREE role-guided training plans
A password is a secret word or string of characters used for authentication to prove a particular user's identity, or access approval to gain entry to a resource (example: an access code is a type of password), which should be kept secret from those not allowed access.
A typical computer user has passwords for many purposes: logging into accounts, retrieving e-mail, accessing applications, databases, networks, web sites, and even reading the morning newspaper online.
Dictionary attack
Dictionary attack definition according to Wikipedia is:
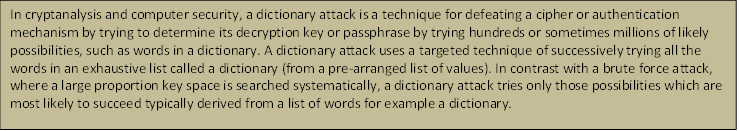
As you can see from the previous definition, Dictionary attack is just a technique that uses a file that has thousands of common, default and weak passwords and uses them against the login portal and tries all of them until one of these passwords allow the attacker to gain access to the private resources (for example an administration panel).
Burp suite tool
Burp Suite is an integrated platform for performing security testing of web applications. Its various tools work seamlessly together to support the entire testing process, from initial mapping and analysis of an application's attack surface, through to finding and exploiting security vulnerabilities. It's a java base web application, so it's multiplatform where you can use it in windows OS, Linux OS and any other operating system.
According to the Burp Suite website, Burp Suite contains the following key components:
- An intercepting Proxy, which lets you inspect and modify traffic between your browser and the target application.
- An application-aware Spider, for crawling content and functionality.
- An advanced web application Scanner, for automating the detection of numerous types of vulnerability.
- An Intruder tool, for performing powerful customized attacks to find and exploit unusual vulnerabilities.
- A Repeater tool, for manipulating and resending individual requests.
- A Sequencer tool, for testing the randomness of session tokens.
- The ability to save your work and resume working later.
- Extensibility, allowing you to easily write your own plugins, to perform complex and highly customized tasks within Burp.
Burp suite usage
For downloading Burp Suite tool, you can download it form here, in this tutorial we will focus on a burp intruder component that we will use it as a brute force tool.
Burp intruder tool can be used as a fuzzer and a tool for performing brute force attacks, and many other purposes.
Burp intruder has four attack types which are sniper, battering ram, pitchfork and cluster bomb. It's set to Sniper by default, according to Burp's documentation.
Dictionary attack demo
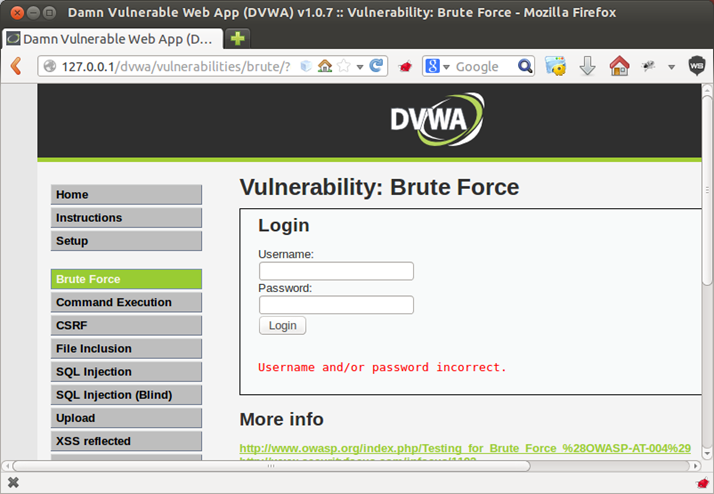
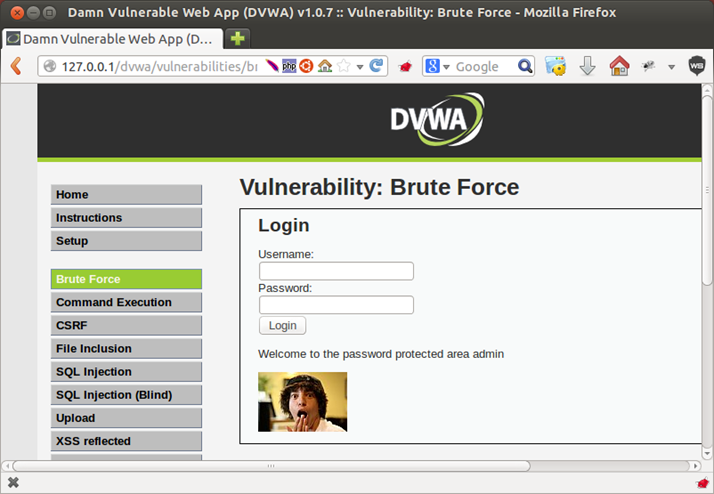
In this demo, we will use Damn Vulnerable Web Application (DVWA) as our target application. So we will browse the application and click on the brute force tab, then we will enter any username/password, making sure sure that we are intercepting the traffic using Burp Suite, then click on Login.
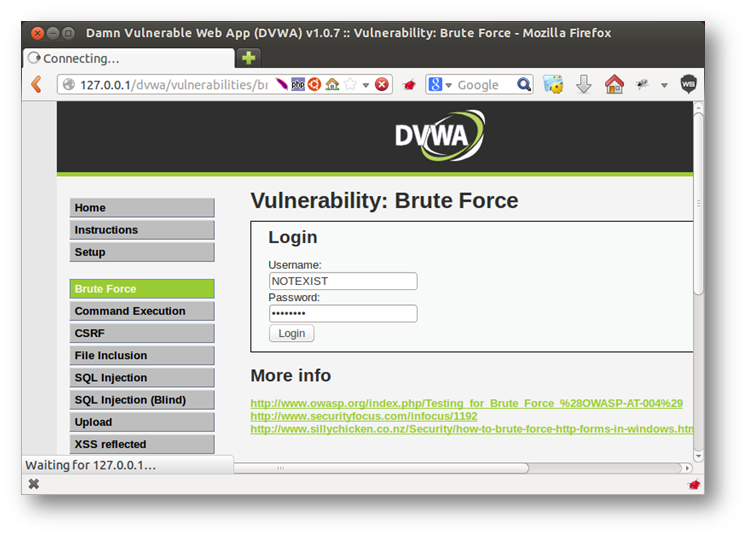
After clicking the login button, the request will be intercepted by Burp Suite, so right click on the request and click on send to intruder.
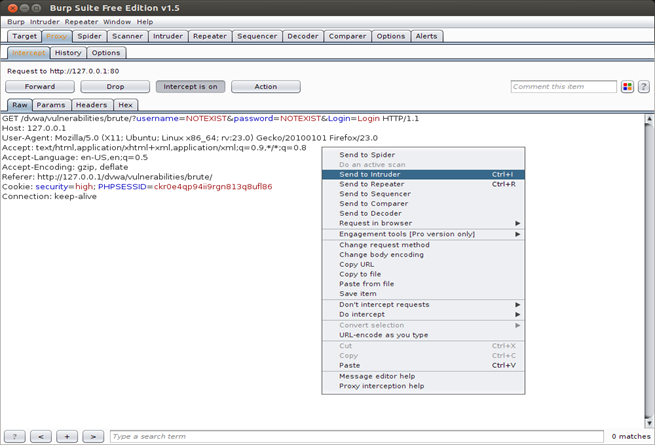
Now let's go to the Intruder tab, we will have to configure Burp Suite to launch our attack. Under the target tab, we can see that it has already set the target by looking at the request host and port.
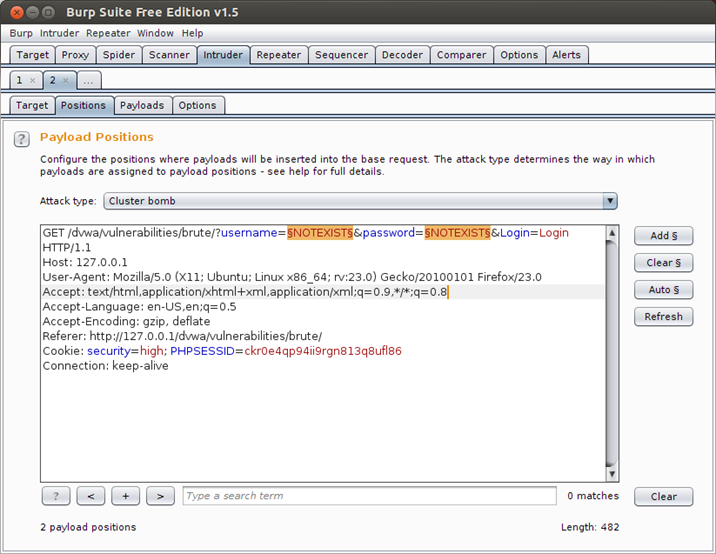
Now let's go to the positions tab , As you can see there are somethings highlighted in the request. The highlighted parameters are just a guess by Burp Suite to help you to figure out what parameters you can attack.
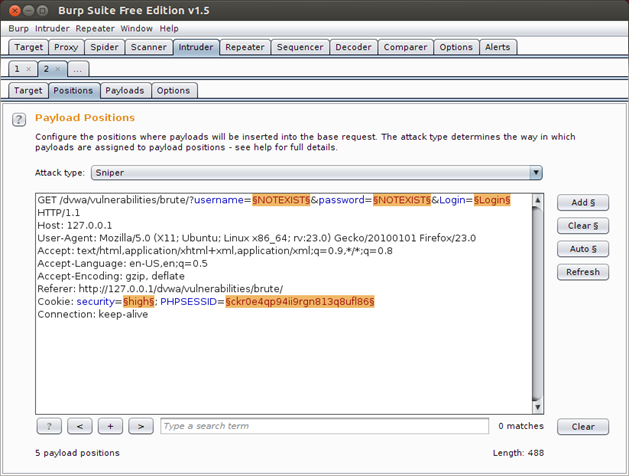
But according to our attack scenario we need to change the values of username and password only with each request. So click on the clear button, this will remove all the highlighted text. Now to configure Burp to change only username and password, we need to highlight the username parameter value in our case ("NOTEXIST") then click add and do the same thing with the password parameter value, In addition as you can see the default attack type is Sniper, So we will change it to Cluster Bomb.
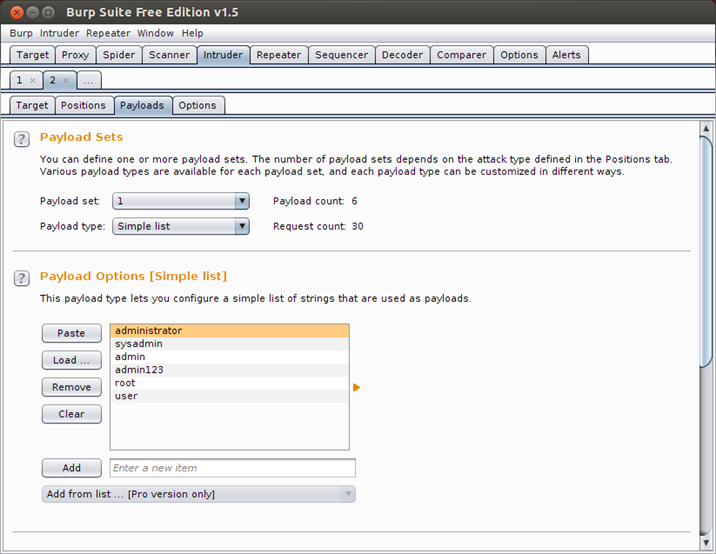
It's the time to set the payload for each attack parameter, so lets go to the payload tab, then select payload set 1, click on load and load the file containing a list of usernames. For demonstration purposes we will use a small list of usernames and passwords.
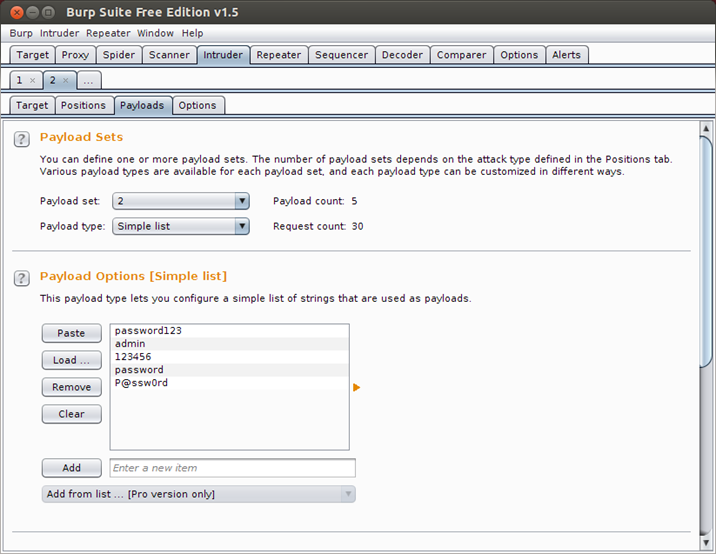
Also select payload set 2, click on load and load the file containing a list of passwords.
Now let's go to the options tab, this tab is the most important tab because we will use it to configure the rules that will help us to figure out which request is successful.
Normally when we enter wrong credentials, the application will show the following error message "Username and/or password incorrect"
And if we enter the right credentials, it will show the following message "Welcome to the password protected area admin"
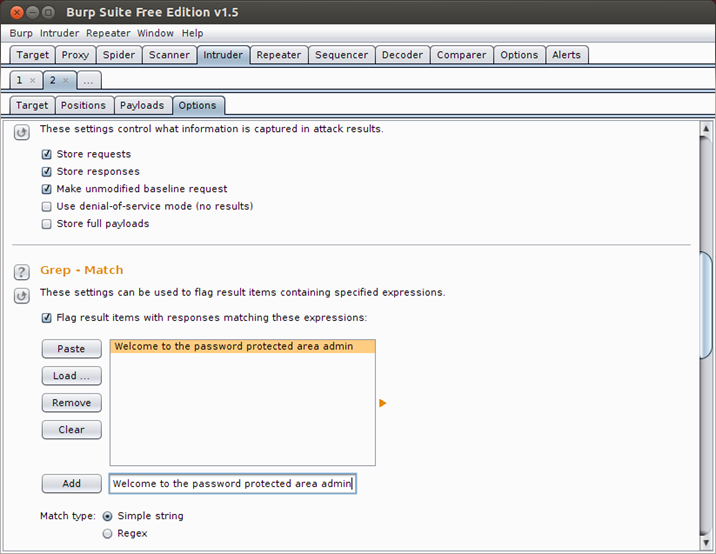
In the options tab, go to grep – match and remove all string patterns and add the following pattern "Welcome to the password protected area admin" which will indicate that the credentials are valid. Finally click on the "Intruder" tab on the top left and click "start attack". We will see a window pop up with all the requests being made.
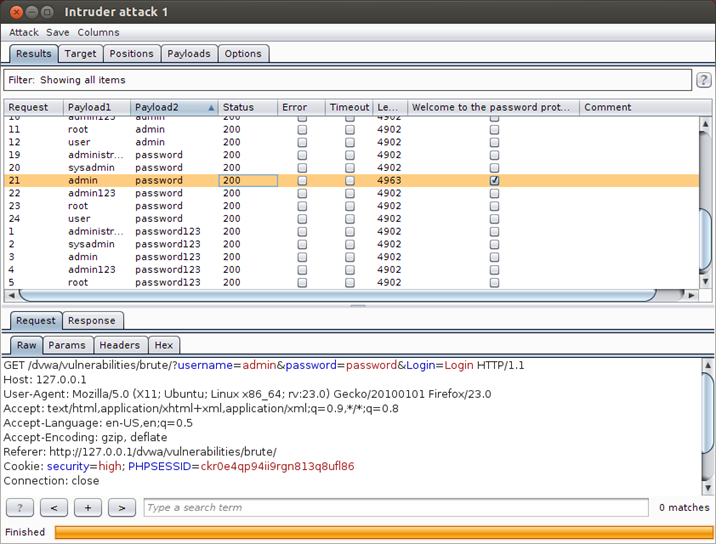
Now the Intruder will use all possible tries form the two lists, and you will find a tab called "Welcome to the password protected area admin", If this tab is checked, It means that the credentials used in this request are valid
Now let's take a look at the response:
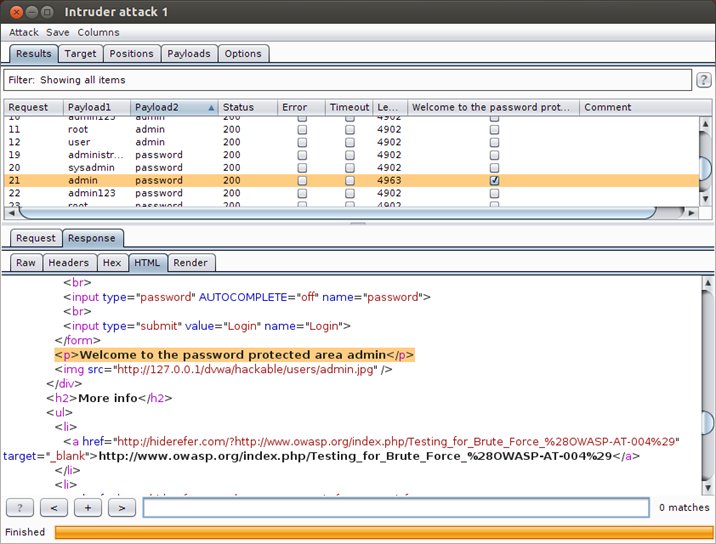
Another way to know if the credentials are valid or not is that a successful request will have a different response than an unsuccessful request or will have a different status response. As you can see from the previous screenshot that the successful request length 4963 and the unsuccessful request length 4902.

What should you learn next?
Conclusion
Dictionary attack is a very common technique, that is often used by the attackers to gain access on private and forbidden resources and it's become easier by using a powerful tool as like Burp Suite.










