Handy Devices Revolution: Handy Pentesting & Hacking Part 1
A few weeks ago, I wrote an article entitled 'Transforming your Android Phone into a Network Pentesting Device' which is obviously about turning your Android phone into a very simple graphical network monitoring tool and network penetration testing arsenal by installing dSploit. And so it has come to my mind that I should make a follow-up article on other handy or pocket devices aside from your smartphone (but we first start off with the smartphone overview) that are used by some ingenious hackers, information security enthusiasts, programmers and developers out there for handy penetration testing and hacking.
Smartphones

What should you learn next?
We start off with the most common device in today's generation - the smartphone. There are a lot of smartphone systems that have revolutionized the market today like the iOS, Android, Blackberry, Symbian, Meego OS and Windows. Penetration testers however usually pick Android or iPhone devices not just because they are the two most popular ones, or that they have cool apps and functionalities, but because they are very handy for hacking and penetration testing.
The Metasploit 4, for example, has been tested fully for the iPhone 4S, and the official website of Offensive Security has detailed instructions on how to install it with your jailbroken iPhone, which can be found here.
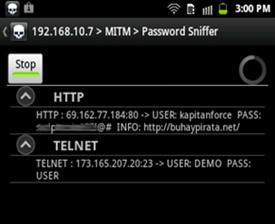
Then there are also a lot of Android apps today that can be used for ARP spoofing, sniffing, session hijacking, port scanning, vulnerability assessment, network monitoring, forensic analysis and other cool stuff. One such is the dSploit application which is a free Android Network Penetration Suite released by evilsocket. For me, dSploit totally rocks not only because it is free but because of its functionality and uniqueness.
Aside from penetration testing tools and arsenals, smartphones take pride in free applications for coding and editing or IDEs (Integrated Development Environment) that can be used for programming such as DroidEdit, AIDE, Terminal IDE, Android Java Editor, C4droid, and Code Peeker.
In some cases, other venturers boot their smartphones with BackTrack 5 Linux which is a popular penetration testing distribution. This is possible because there is an ARM version that can be downloaded here, although it is not really advisable booting it in your smartphone if your phone has a small memory and storage. To lessen the amount of used memory resources and prevent a hang up, just install free Android applications that can be used for penetration testing. Take note that you need a rooted phone if you plan on converting your phone into an arsenal.
Tablet Computers or PC's
In terms of size, tablets and PCs are larger than smartphones, but in terms of usability in the field of penetration testing, they just have the same functionality (although not totally). If it runs on Android, then you can install dSploit, Droidsheep, zAnti, and Netspoof. BackTrack 5 ARM version runs smooth on Samsung Galaxy S too; all you need to do is to have these prepared:
- A new microSD, 8 GB or more and you need to format it
- A rooted device
- Full Busybox Install (if you install titanium backup you get Busybox)
- Terminal Emulator for your Android
- A VNC client
Here is the link for the detailed tutorial on how to install BackTrack 5 ARM version in your Samsung Galaxy Tab.
If you have an iPad, then you can have Metasploit 4 installed too.
[caption id="" align="aligncenter" width="323"]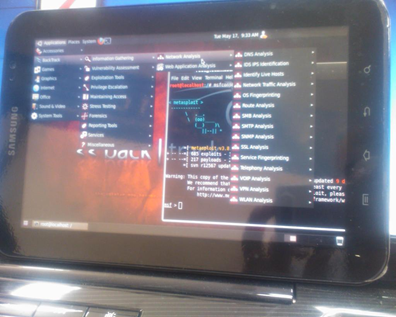 (Image courtesy of BackTrack's Forum Website)[/caption]
(Image courtesy of BackTrack's Forum Website)[/caption]
Working with IDEs in tablet computers is easier than working with your smartphone because the touch screen keyboard is larger than that of a smartphone's. Overall, it minimizes the hassle and frustration.
The difference between a smartphone and a tablet is that the tablet has a bigger screen and more RAM and system resources. It may be larger but it is still handier than your laptop.
Raspberry Pi
 Raspberry Pi is a ARM GNU / Linux box or a credit card size mini computer that can be plugged in to your TV using an HDMI cable and to your USB type keyboard. Aside from office work, programming, personal usage, and gaming, it is also used by enthusiasts out there as a penetration testing box by installing Ubuntu or Debian Linux and a couple of tools for information gathering, vulnerability assessment, exploitation, maintaining access, reverse engineering, social engineering, forensic analysis and VOIP analysis.
Raspberry Pi is a ARM GNU / Linux box or a credit card size mini computer that can be plugged in to your TV using an HDMI cable and to your USB type keyboard. Aside from office work, programming, personal usage, and gaming, it is also used by enthusiasts out there as a penetration testing box by installing Ubuntu or Debian Linux and a couple of tools for information gathering, vulnerability assessment, exploitation, maintaining access, reverse engineering, social engineering, forensic analysis and VOIP analysis.
There are also two known penetration testing distros suited for Raspberry Pi today, PwnPi and Raspberry Pawn from Pwnie Express.
PwnPi is a Linux-based penetration testing drop box distribution which has 181 network security tools pre-installed and uses Xfce as its window manager. Following is a list of the tools in PwnPi as categorized by the lead developer:
Information Gathering
- arping
- bing-ip2hosts-0.2
- chaosreader
- darkstat
- dmitry
- dnstracer
- dnswalk
- enum4linux
- frox
- ike-scan
- lynis
- metagoofil-blackhat
- netmask
- ngrep
- pscan
- SearchEngineAssessmentToolkit
- squid
- sslsniff
- sslstrip
- swaks
- tcpdump
- tcpflow
- tcpspy
- tcptraceroute
- theHarvester
Penetration
- ExploitDB
- Fasttrack
- S.E.T
- sqlbf
- inguma
- isr-evilgrade
- metasploit (with db_autopwn)
- msfencode
- msfpayload
- msfvenom
- mysqloit
- sqlbrute
- sqlmap
- sqlninja
- wfuzz
Radio Network Analysis
- airbase-ng
- aircrack-ng
- airdecap-ng
- airdecloak-ng
- airdriver-ng
- aireplay-ng
- airmon-ng
- airodump-ng
- airserv-ng
- airtun-ng
- besside-ng
- bluesmash
- bluetracker
- bluewho
- btscanner
- ghettotooth
- giskismet
- hcidump
- hcitool
- ivstools
- kismet
- makeivs-ng
- obexftp
- packetforge-ng
- prismstumbler
- reaver
- setbtaddr
- ussp-push
- wash
- wavemon
- weplab
Privilege Escalation
- bkhive
- chntpw
- dsniff
- etherape
- ettercap
- fcrackzip
- john
- medusa
- netsed
- ophcrack
- packeth
- packit
- pdfcrack
- pw-inspector
- samdump2
- ssldump
- tcpick
- tcpreplay
- thc-hydra
- wireshark
- yersinia
Network Mapping
- arp-fingerprint
- arp-scan
- fping
- hostmap
- hping3
- knocker
- nbtscan
- netdiscoverer
- nmap
- nmapsi4
- onesixtyone
- p0f
- pbnj
- pnscan
- scapy
- sslscan
- tcptraceroute
- thc-amap
- xprobe
- zenmap
VoIP Analysis
- fuzzer
- sipcrack
- sipdump
- sipp
- sipsak
- svcrack
- svcrash
- svmap
- svreport
- svwar
- torturer
- voiphopper
- voipong
Maintaining Access
- 6tunnel
- cryptcat
- dns2tcp
- ftp-proxy
- httptunnel
- iodine
- netcat
- openvpn
- proxychains
- ptunnel
- socat
- stunnel4
- tinyproxy
- udptunnel
- videlia
- vinetto
- wipe
Digital Forensic
- aimage
- chkrootkit
- foremost
- galleta
- magicrescue
- mboxgrep
- scalpel
- scrub
Vulnerability Identification
- bfbtester
- curl
- fimap
- flasm
- lsat
- netwox
- nikto
- openvas-client
- openvas-server
- ovaldi
- ratproxy
- skipfish
- smb-nat
- smbclient
- w3af
- wapiti
- wbox
Reverse Engineering
- dissy
- splint
Miscellanious
- ccrypt
- httrack
- ipcalc
- macchanger
- makepasswd
- otp
- pentbox-1.5
- sendemail
- u3-tool
- w3m
Stress Testing
- mz
- siege
Raspberry Pwn on the other hand includes the following penetration testing tools: SET, Fasttrack, kismet, aircrack-ng, nmap, dsniff, netcat, nikto, xprobe, scapy, wireshark, tcpdump, ettercap, hping3, medusa, macchanger, nbtscan, john, ptunnel, p0f, ngrep, tcpflow, openvpn, iodine, httptunnel, cryptcat, sipsak, yersinia, smbclient, sslsniff, tcptraceroute, pbnj, netdiscover, netmask, udptunnel, dnstracer, sslscan, medusa, ipcalc, dnswalk, socat, onesixtyone, tinyproxy, dmitry, fcrackzip, ssldump, fping, ike-scan, gpsd, darkstat, swaks, arping, tcpreplay, sipcrack, proxychains, proxytunnel, siege, sqlmap, wapiti, skipfish, and w3af.
For me, Raspberry Pi is an ideal box for handy penetration testing because you can buy it for just $25 USD or $35 USD.
Minipwner
[caption id="" align="alignright" width="468"]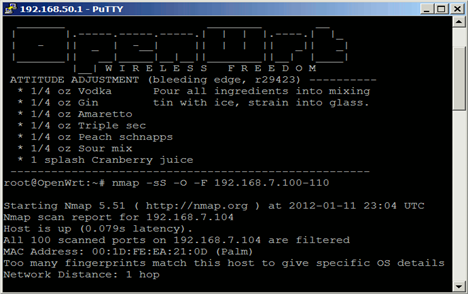 (Image courtesy of minipwner.com)[/caption]
(Image courtesy of minipwner.com)[/caption]
If you are into war driving and war walking, then Minipwner is for you. It is a customized TP-Link TL-WR703N router which has a 4GB flash drive in order to expand its storage capability. It includes 802.11n Wireless N and a Gig Ethernet port and runs on an OpenWRT flavor. It is also a penetration testing drop box which has the following pre-installed tools or software:
- Nmap - a network scanner
- Tcpdump - a sniffer
- Netcat - the hacker's Swiss army knife
- aircrack - used for wireless network analysis, auditing, and cracking
- kismet - used for network analysis
- perl - a Scripting language
- openvpn - Virtual Private Network (OpenVPN) Client and Server
- dsniff - a suite of sniffing and spoofing tools, including arpspoof
- nbtscan - NetBIOS Network Scanner
- snort - Sniffer, Packet Logger, Intrusion Detection System (IDS)
- karma - Wireless Sniffing Tool but it does not work well yet
- samba2-client - Windows File Sharing Client
- elinks - text-based web browser
- yafc - File Transfer Protocol Client
- openssh-sftp - Secure File Transfer Client
Overall, it is a small but cool war driving tool that can be easily carried in a pocket, hidden behind a telephone, jeans, or hanging from a jack by a short Ethernet cable.
Minipwner can be bought for $99 USD and can only be shipped to US purchasers (how sad) but you can actually build a customized one as long as you secure a TP-Link TL-WR703N router which costs $22.34 USD and follow the instructions which can be found here.
PwnPhone
[caption id="" align="alignleft" width="336"] (Image courtesy of pwnieexpress.com)[/caption]
(Image courtesy of pwnieexpress.com)[/caption]
I already mentioned that smartphones are handy devices that can be used for hacking and penetration testing but I think it's also a good thing to highlight PwnPhone, which is a mobile phone-based penetration testing platform from Pwnie Express. This platform includes tools like Aircrack-NG, Metasploit, Kismet, GrimWEPa, SET, Fasttrack, Ettercap, nmap, and many more.
This mobile phone has a built-in wireless chipset that supports packet injection, monitor mode, and promiscuous mode which means it can be used for wireless cracking.
This phone costs $995.00 USD.
Pwn Plug Wireless
 Some people may describe this device as an ordinary power plug or something that has got to do with the Internet connection (but not a router LOL). But beware; Pwn Plug Wireless is another product of Pwnie Express which is a known company for selling pen testing drop boxes.
Some people may describe this device as an ordinary power plug or something that has got to do with the Internet connection (but not a router LOL). But beware; Pwn Plug Wireless is another product of Pwnie Express which is a known company for selling pen testing drop boxes.
Pwn Plug Wireless is a commercial-grade penetration testing drop box that is pre-loaded with Debian 6, Metasploit, SET, Fast-Track, w3af, Kismet, Aircrack-ng, SSLstrip, nmap, Hydra, dsniff, Scapy, Ettercap, Bluetooth / VoIP / IPv6 tools, weevely, sqlmap, sqlninja, fimap, goohost, hping3, john, mdk3, and other known penetration testing tools. It also comes with a simple web-based administration interface called Plug UI.
Pwn Plug Wireless costs $695.00 USD though, so I would still vouch for a Raspberry Pi.
WiFi Pineapple
 WiFi Pineapple is a hot spot honeypot penetration testing platform that has the ability to perform Man-in-the-Middle attacks. Here is a brief specification and functionality of WiFi Pineapple as described by the device's official website:
WiFi Pineapple is a hot spot honeypot penetration testing platform that has the ability to perform Man-in-the-Middle attacks. Here is a brief specification and functionality of WiFi Pineapple as described by the device's official website:
- Fast Linux Kernel 3.2-based Jasager firmware (built on OpenWRT)
- Built on the Atheros AR9331 SoC running at 400 MHz (2x speed of previous models)
- 802.11 b/g/n 150 Mbps wireless
- 2x Ethernet, one with PoE (Power-Over-Ethernet)
- USB 2.0 for expanded storage, WiFi Interfaces and Mobile Broadband
- Six common stealth deployment scenarios for secure remote target monitoring
- MITM attack tools: Karma, DNS Spoof, SSL Strip, URL Snarf, Ngrep and more
- Wireless cracking and deauth attacks with the Aircrack-NG suite
- Autostart service like karma and reverse SSH for instant attack on power-up
- Simple Mobile Broadband, Android Tethering, and Reverse SSH setups
- Hands-off deployment of locally hosted payloads in standalone mode
- Community-built modules add functionality with web interfaces for additional tools:nmap, tcpdump, java attacks, WiFi Jammer, bandwidth monitor, sslstrip, dynamic DNS, site survey and many more.
- Stealth Access Point for Man-in-the-Middle attacks
- Mobile Broadband (3G USB) and Android Tethering
- Manage from afar with persistent SSH tunnels
- Relay or Deauth attack with auxiliary WiFi adapter
- Web-based management simplify MITM attacks
I am planning to buy WiFi Pineapple but sad to say, it is only available to US buyers. Even though its fourth hardware version has been released, this device still costs $99.99 USD which is manageable for all enthusiasts. I just wish that the Philippines would soon have these kinds of drop boxes.
Final Words for Part One
There are still a lot of penetration testing drop boxes and microcontrollers for hacking that are not included here since this is just part one of my article. I will be including Arduino in my next article along with other products of Pwnie Express.
The point of this article is to show how brilliant the ideas of modern hackers and developers who revolutionized handy hacking and pentesting are, and also to invite enthusiasts to contribute to these projects and try these ideas. So guys, I leave you hanging for this first article about Handy Devices Revolution. More coming soon.
References:
http://www.offensive-security.com/offsec/metasploit-4-on-iphone-4s-and-ipad-2/
http://techtips.salon.com/difference-between-iphone-smartphone-20068.html
http://android.appstorm.net/roundups/developer/15-apps-for-programming-on-android/
http://www.youtube.com/watch?v=ipU2h1u5Ehw
http://blog.pwnieexpress.com/post/24967860602/raspberry-pwn-a-pentesting-release-for-the-raspberry
http://www.minipwner.com/index.php/f-bomb-pwnie-wifi-pineapple
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.










