Hotspot honeypot
The Hotspot Honeypot is an illegitimate Wi-Fi access point which can appear as an authorized and secure hotspot. Despite appearances, it is actually set up by black-hat attackers or malicious hackers to steal your bank and credit card details, passwords and other personal information.
Many of us fall victim to the Honeypot. It tricks the wireless users into connecting their laptops or mobile phones to these fake hotspots by masquerading as a legitimate one. Once the victim has connected, the cyberattacker may launch man-in-the-middle attacks which allows him to record all of your Internet activities in an effort to steal your bank details by using a spoofed website.

What should you learn next?
The Hotspot Honeypot is one of the commjacking (cyberthreat) methods which are now being used on a large scale. The primary reason for this is that it can be set up easily by anyone, with minimal hardware requirements.
How hackers use hotspot honeypot
There are two types of hackers: ethical (white-hat) hackers and unethical (black-hat) hackers. The former uses their skills to find security breaches in their own companies and organizations like the government and the police department. The latter use their skills to steal personal information from other organizations and using it for their own good. This is often done by using access points or man-in-the-middle attacks
In this article, we will demonstrate how the Hotspot Honeypot works by setting up a basic Wi-Fi Honeypot and forcing the clients to connect to it instead of the network they desire.
When a device is running, it is regularly sending out signals to wireless access points to which it has connected before. This device also looks out for other wireless networks to connect with also. We will now emulate a wireless network that is in the client’s range, such as one that might be found at Starbucks, Panera Bread or other gathering spots with Wi-Fi available.
Setting up a honeypot
Here are the tools that you will you need in order to accomplish this task:
- A laptop
- An ALFA Wi-Fi card
- An Aircrack suite
- An unsuspecting victim
1.First of all, you need to find the public networks that our victim intends to connect to. We have to put the ALFA card into a monitor mode by running “ifconfig” and finding the interface. In this case, it is wlan2.
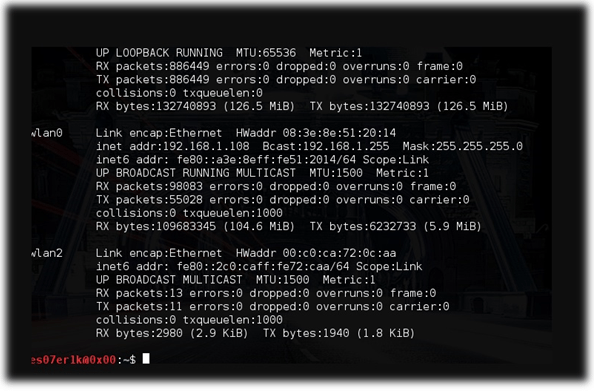
Figure 1: Interface (wlan2)
2.Next, we actually put the wlan2 interface into the monitor mode by running the command “sudo ‘airmon-ng start wlan2.” This will create an interface mon0.
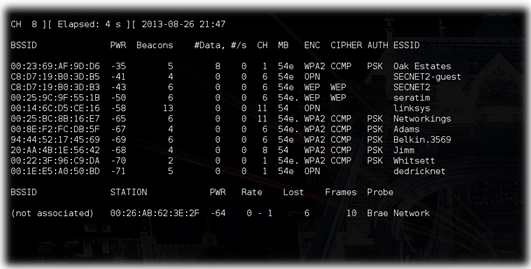
Figure 2: Execution of the “sudo airodump-ng mon0.” command
3.Next, we attempt to find some networks people are trying to connect to. This can be done using the command “sudo airodump-ng mon0.” This is illustrated in the screenshot above.
After executing this command, you will see a Wi-Fi network and the clients which are attempting to connect to them. We can attack the clients associated with the network as well as those clients that are not associated with it.
In this scenario, we have the open access point (AP) named SECNET2 (running with a test network for lab work). We are now going to create a Honeypot for this AP.
4.The fake AP can be created by using the command “sudo airbase-ng --essid "SECNET2" -c 2 mon0.” Now if anyone comes who has already connected to this network before, they will automatically connect to this Honeypot, because the SSID is the same as that of an already-trusted wireless access point on the device.
If we want clients that are connected to the legitimate networks to connect to our fake AP in turn, we send false de-authentication messages. Then, when they re-authenticate, they will connect to our AP. A de-authentication message is a type of message sent by an access point to force a client machine off of the network. This is used to force the user off of their trusted network before tricking them into connecting to the Honeypot.
5.The steps up above describe how a simple Wi-Fi Honeypot can be set up. Once this has been accomplished, the potential to commit various cybercrimes is quite high, such as:
- Hacking into bank accounts
- Launching ransomware attacks
- The theft of personal and confidential information/data
- Launching BEC attacks
Some ways to protect yourselves from hotspot honeypots
The following are a few methods that can be used to protect your information and increase your security:
Turn Off the Wi-Fi
If your Wi-Fi is not turned on, there is no security or privacy risk whatsoever. We can instead use a 3G or 4G USB stick. On laptops, we can also use a wired Ethernet connection.
Avoid Open Wi-Fi Networks
If you care about the safety of your personal information, you should avoid open Wi-Fi networks altogether. This is suggested by most cybersecurity specialists. If you are still going to use open networks, then use WPA-encrypted networks instead.
Use a VPN
If you still wish to use an open network, you should use what is known as a Virtual Private Network (VPN) to give yourself an additional layer of security. But even if you do use a VPN, the attacker might intervene with the Wi-Fi connection by sending a fake de-authentication frame.
Change Your Wi-Fi settings
Changing your Wi-Fi settings also helps in protecting your personal information and data. If your computer or smartphone no longer remembers the network it has connected to, this will also help protect your privacy. On the OS X, go to “network settings,” and under “advanced,” turn off "Remember networks this computer has joined.”
Conclusion
We should care for our own security and protect our personal information by being aware of how such cybercrimes actually exist. These instances are increasing because of the ease of the availability of resources and the cheap price that comes with them.
In this article, I have explained a commjacking method known as Hotspot Honeypot, and how to set one up was also reviewed. Various strategies into how we can secure our information are also included in the article. You can use the best-suited method that works for you, but it is highly-recommended that you not use public networks for conducting financial transactions or any other related activities.

FREE role-guided training plans
There are many other ways in which commjacking can occur, such as through MAC spoofing, misconfigured APs, man-in-the-middle attacks, Distributed Denial of Service (DDOS) attacks, client misassociations and so on. The world today depends upon the usage of wireless technology on a large scale. Securing these networks should be made a top priority.










