How to hack mobile communications via Unisoc baseband vulnerability
The Chinese company UNISOC, founded as Spreadtrum, is one of the world’s largest chipmaker firms and the biggest in China over the last 20 years. The firm produces low-cost chipsets for Android devices compatible with 2-5G technology, smart TVs and other products.
Because researchers have not tested their products before, the CheckPoint team decided to analyze part of the protocol messages used, known as NAS, and found a vulnerability (CVE-2022-20210) that can be abused to disrupt the device’s radio communication via a malformed packet causing a DoS condition. This vulnerability allows attackers can neutralize communications in a specific location.

What should you learn next?
Learning about vulnerability (CVE-2022-20210)
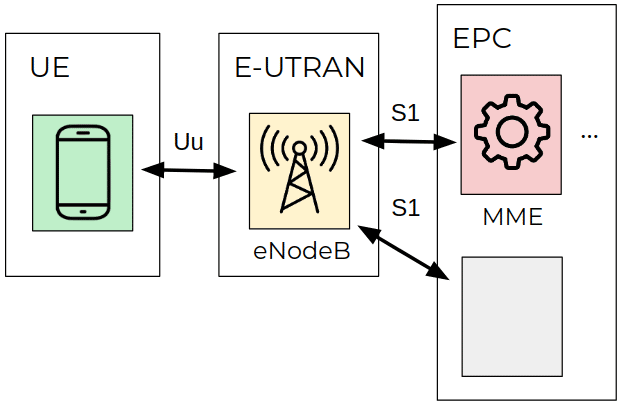
The LTE network should be scrutinized to understand the basic concepts and how to exploit this vulnerability. The long-term evolution (LTE) network comprises some protocols and components. The 3GPP Group created the evolved packet system (EPS), an LTE technology composed of three parts:
- The user equipment (UE)
- Evolved UMTS terrestrial radio access network (E-UTRAN)
- Evolved packet core (EPC)
Figure 1: High-level diagram of EPS architecture of the LTE network (source).
In detail, the E-UTRAN component is formed of one single stack called the “eNodeB” station. This station is responsible for controlling radio communications between the UE and EPC components. Notice that a UE device can communicate with a unique eNodeB only in a single communication.
The ECC is divided into four parts, one of which is the mobility management entity (MME). This component is responsible for sending signaling messages associated with security control, management of tracking areas and mobility maintenance.
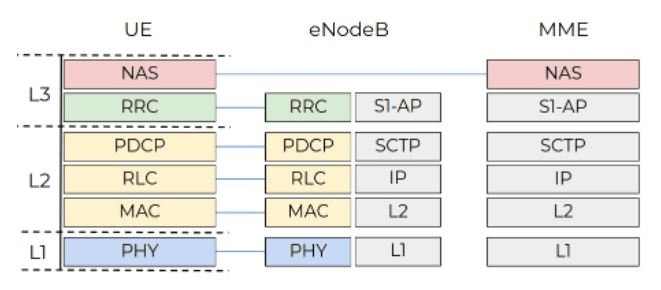
The investigation was carried out using a UNISOC modem and communications between the MME component and the UE stack (an Android device). Figure 2 shows the protocol stack of the modem; the no-access stratum (NAS) level hosts EPS and EMM signaling messages.
Figure 2: High-level diagram illustrating the LTE protocol stacks (source).
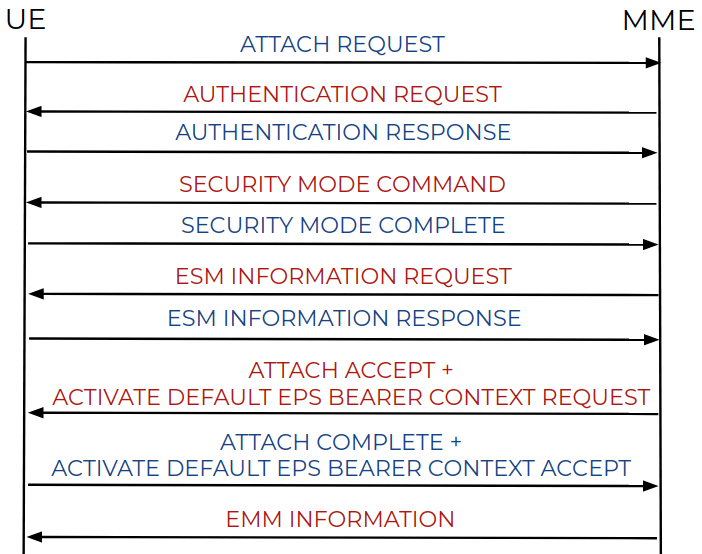
Some exchange messages between the UE device and the MME component are shown below.
Figure 3: Message exchange scheme (source).
The NAS protocol must be highlighted (see Figure 3) because it operates over high-level structures. An adversary can create specially malformed packets and send them to the target device to crash it or execute remote code.
Digging into the vulnerability details
In this sense, the vulnerability tracked as CVE-2022-20210 relies on the exploitation of the NAS arguments, namely:
- output filter — the object structure
- NAS message blob; and
- blob offset
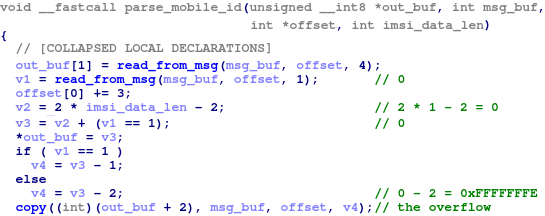
By fuzzing the implementation of the NAS function via AFL and QUEMU approaches, the team identified some interesting functions such as liblte_mme_unpack_mobile_id_ie of srsRAN being used to extract the mobile identity from the NAS message. This identity starts with a number; the value consists of a 2-byte length to represent the international mobile subscriber identity (IMSI).
The crash happens when this value is copied to the output buffer as the IMSI number. If the length of the value is zero, 0-2 = 0xFFFFFFFE bytes are transferred to the heap memory, and a DoS condition is triggered.
Figure 4: Code block responsible for crashing the device (source).
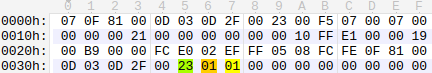
As a result, a malformed NAS message is created. As observed below and described by CheckPoint, “the highlighted 0x23 value indicates that the following data is the message identity block, where the first 0x01 is the length and the second 0x01 is the IMSI type.”
Figure 5: Malformed NAS message (source).
This message crashes the device and opens doors to more sophisticated payloads that can lead to remote code execution scenarios.
Free hour-long hacking course!
Learn how to hack and use AI in this free 1-hour course, led by Keatron Evans, 20-year cybersecurity veteran and VP of Portfolio Product and AI Strategy at Infosec!
Final thoughts
In this article, we observed how the LTE protocol and malformed NAS messages could affect the operation of smart devices, even leading to an interruption or neutrality of devices.
Google has addressed all bugs to protect millions of devices around the world. The patch comes with the June bulletin 2022 by Google, and users can now protect their smart devices against this vulnerability.
Sources:
UNISOC baseband vulnerability, CheckPoint