Penetration testing of web services with CGI support
This article shows hands-on penetration testing using an Apache server with CGI access; it identifies some vulnerabilities and performs exploits attacking these vulnerabilities, then further patches it to mitigate these known threats.

FREE role-guided training plans
APACHE
Apache can also be referred to as the Apache HTTP Server. It is a standard that is established for allocating services for websites. It is a free platform for a web server that is being used by most websites. The server is used by most operating systems, e.g., Unix, Linux, Window, Microsoft Windows, Mac OS, etc., but it was originally designed for Unix.
Apache can be referred to as a "patchy" server because of the patches that are attached to the NCSA HTTPD 1.3 codebase. The open source community (Apache Software Foundation) developed the Apache web servers and regularly add important features to the web server in order to make it secure and in compliance with the most recent HTTP standard.
The Apache server is created with a lot of modules that allow the server to run scripts and other content. Apache is capable of doing many things, e.g., running the common gateway interface (CGI), which is a protocol used to create a communication between external application software and the web server, and SSI (server side includes), which is a server-side script language. Examples of other Apache modules are CGI scripts execution, URL redirection, user home directories, and content negotiation.
COMMON GATEWAY INTERFACE (CGI)
CGI can be defined as a rule that allows scripts and programs to run on the web server. It gives details of information communicated between the web server and web browser and how it was transmitted. CGI is used by web servers to carry out external programs, referred to as CGI scripts. It is a way for a CGI script to run on the server and send results from the program to the server.
The root folder of every web server includes the cgi-bin directory; scripts that are placed in the cgi-bin directory compile according to the CGI rule. CGI is supported by most web servers, e.g., Windows server and Apache. CGI scripts can be written in various programming language, including Java, C++, and Perl. In CGI, user inputs are always submitted via HTML.
Steps in installing APACHE server
The first is to install the Apache package; the command below will install the httpd package along with the dependencies.
[plain]
[root@localhost ~] yum install httpd
[/plain]
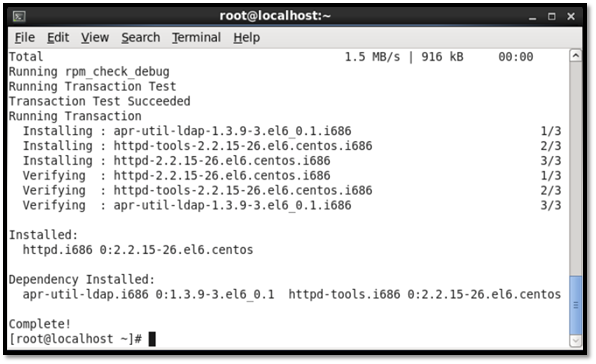
The next step is to open the "/etc/httpd/conf/httpd.conf" configuration file and edit the server name so as to point the Internet Protocol (IP) address to the httpd server; the following command was input.
[plain]
[root@localhost ~] vim /etc/httpd/conf/httpd.conf
[/plain]
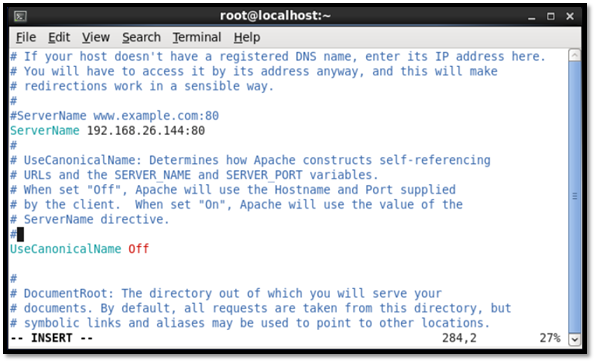
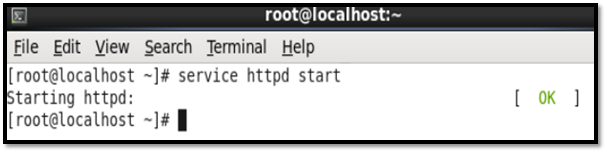
To start the httpd service, the following command was input:
[plain]
[root@localhost ~] service httpd start
[/plain]
In order for the httpd service to start when the system is booted, the following command was input:
[plain]
[root@localhost ~] chkconfig –- levels 235 httpd on
[/plain]
To test that the Apache web server is running, we input the IP address 192.168.26.144 on the web browser to check the configurations previously implemented.
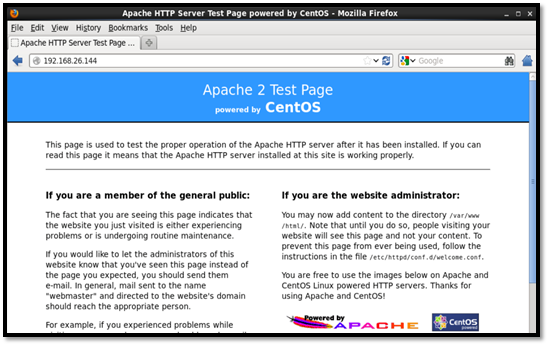
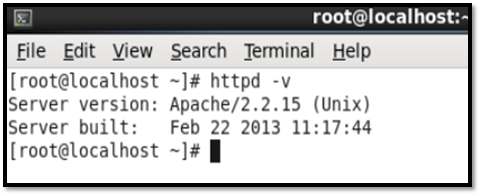
The version of Apache installed is seen below:
Steps in configuring the CGI-script and PERL installation
The following command was input to install Perl:
[plain]
[root@localhost ~] yum –y install mod_perlperlperl-CGI
[/plain]
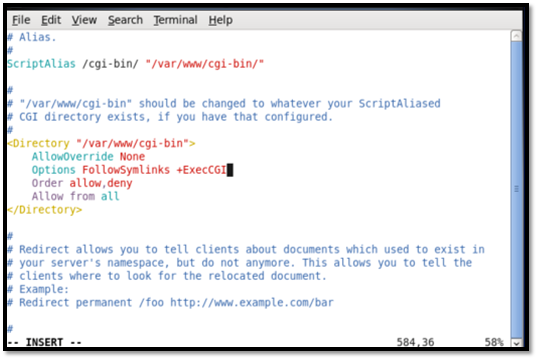
The next step is to configure the cgi-bin directory to allow the Apache server to recognize that directory in order to allow easy execution of commands from within that directory. The following commands were input:
[plain]
[root@localhost ~]mkdir /usr/lib/cgi-bin
[root@localhost ~] chmod755 /usr/lib/cgi-bin
[root@localhost ~]chownroot.root /usr/lib/cgi-bin
[root@localhost ~]vim /etc/httpd/conf/httpd.conf
[/plain]
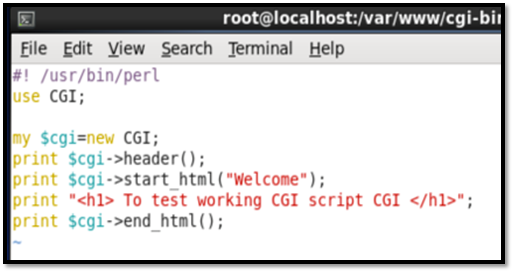
Next we need to configure a new file with a Perl script under the var/www/cgi-bin directory:
[plain]
[root@localhost ~]cd /var/www/cgi-bin
[root@localhost ~]vim test.pl
[/plain]
Now we need to test the CGI script on the web browser to find out whether the CGI script is working with the Apache server.
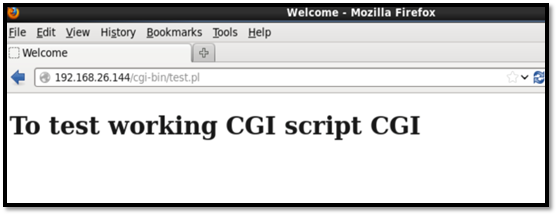
To install all other dependencies for Perl scripts, the following commands were input:
[plain]
[root@localhost ~] yum -y install perl-ExtUtils-MakeMakerperl-Digest-SHA perl-Net-DNS perl-NetAddr-IP perl-Archive-Tar perl-IO-Zlibperl-Digest-SHA perl-Mail-SPF perl-IP-Country perl-Razor2 perl-Net-Ident perl-IO-Socket-INET6 perl-IO-Socket-SSL perl-Mail-DKIM perl-DBI perl-Encode-Detect perl-HTML-Parser perl-HTML-Tagsetperl-Time-HiResperl-libwww-perl
[/plain]
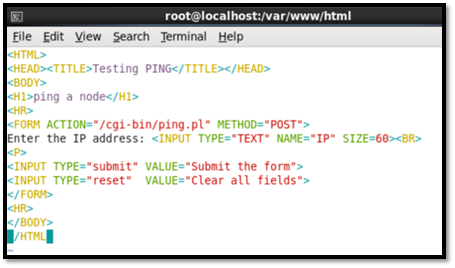
The next step is to test the CGI script by running HTML code that will ping a remote host and also the CGI script written in Perl. The "var/www/html" directory was edited and configured. The following commands were used:
[plain]
[root@localhost ~]cd /var/www/html
[root@localhost ~html] vim index.html
[/plain]
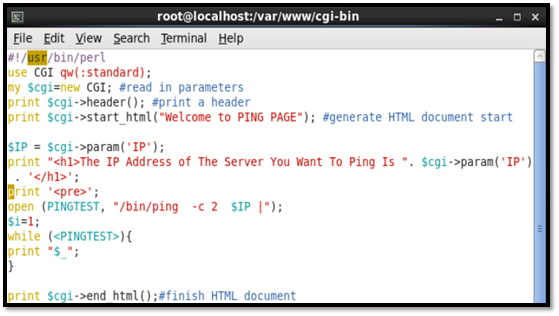
Now we have to configure the Perl script in order to receive the form passed from the html code; to configure the CGI access, we use the following commands:
[plain]
[root@localhost ~html]cd /root
[root@localhost~] cd /var/www/cgi-bin
[root@localhost ~cgi-bin]vim ping.pl
[/plain]
To test the CGI script running on the Apache server, which we will be attacking, we test that the script is working well.
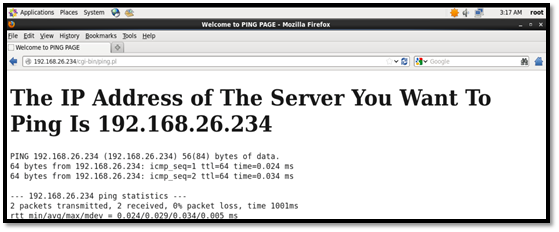
Demonstrating vulnerability
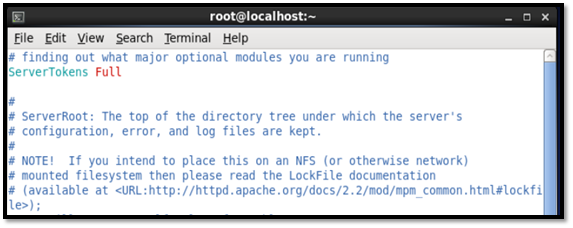
First test: foot printing
By default the server's token is set to full.
[plain]
vim/etc/httpd/conf/httpd.conf
[/plain]
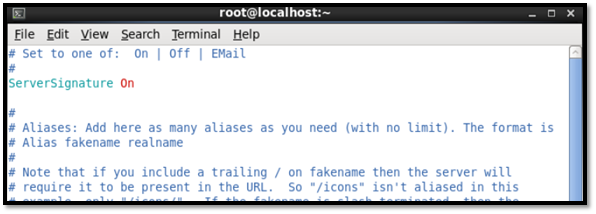
By default, ServerSignature is turned on.
From attacker
[plain]
[root@bt ~] nc 192.168.26.234 80
[/plain]
HEAD / HTTP/1.0
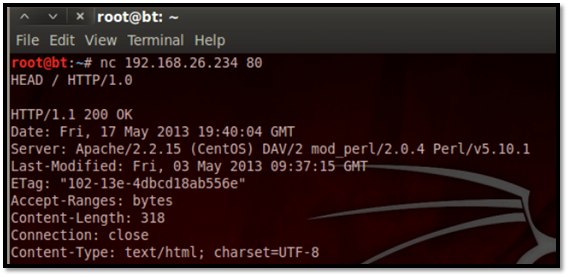
This gives the attacker the operating system that is running and also the kind of web service, with the version number running on it, allowing a possible attack with the information displayed.
Prevention of foot printing
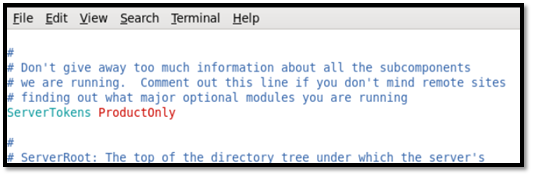
ServerTokens was changed to ProductOnly.
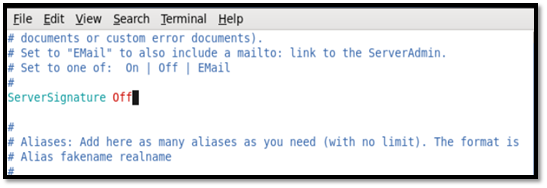
ServerSignature was changed to off.
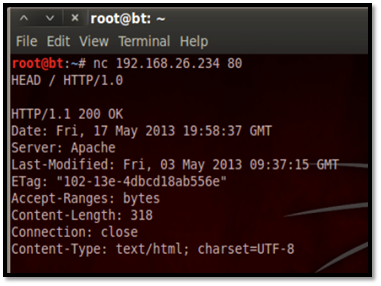
The operating system and Apache version were not displayed after the httpd configuration file was edited.
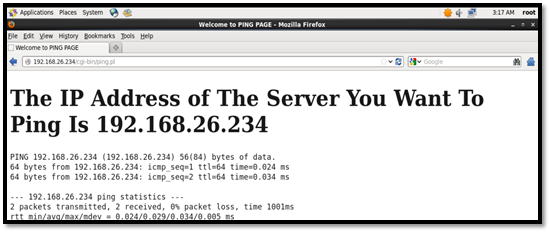
Second Test: Denial of service of a CGI script running on Perl. The CGI script is used to ping the remote host, as seen below.
To test the vulnerability on the Apache server, the Slowloris post script https denial service is used on Backtrack 5 to stop running services by opening too many connections and holding them open, which disallows users from accessing this service; once the connection ends it opens a new connection to keep the services still running.
This attack will be launched on the
http://192.168.26.234/index.html
The following procedures and commands were used on Backtrack.
The Perl postscript slowloris.pl was downloaded to the desktop.
The following commands were input to launch the attack:
[plain]
[root@bt ~]cd Desktop#
[root@bt~]/Desktop#
root@bt~/Desktop# perl slowloris.pl –dns<a href="http://192.168.26.234/index.html">http://192.168.26.234/index.html</a>
[/plain]
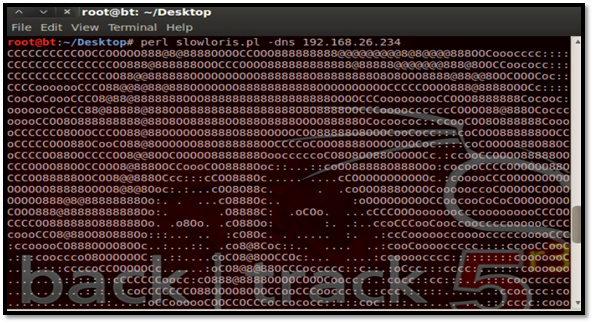
Slowloris in action
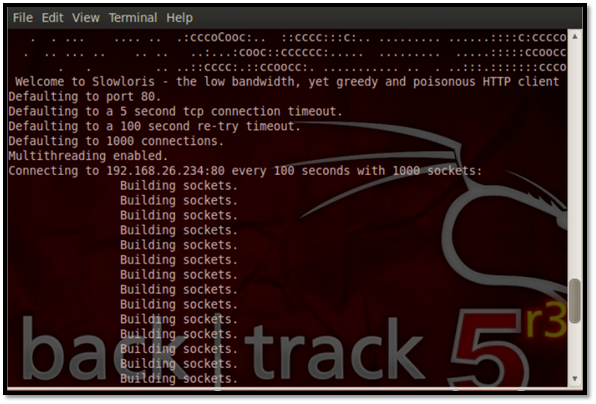
Result
The result below shows that the service was denied due to the excess packets sent by the Slowloris attack's initiating multiple connections, thereby flooding the Apache server.
Prevention of Slowloris
In order to prevent this attack on Apache, we reduce the number of connections on the Apache server by implementing firewalls using iptables.
This will in turn allow normal traffic and mitigate the full effect of the Slowloris denial of service attack through the Perl script.
[plain]
[root@localhost~] vim /etc/rc.local
[root@localhost~]chmod u=rwx,g=rwx,o=x /etc/rc.local
[/plain]
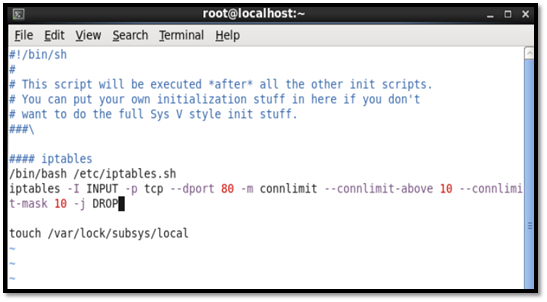
Third test: command injection on CGI script
Command injection allows an attacker to inject and execute arbitrary code on the remote web server via a remote CGI script.
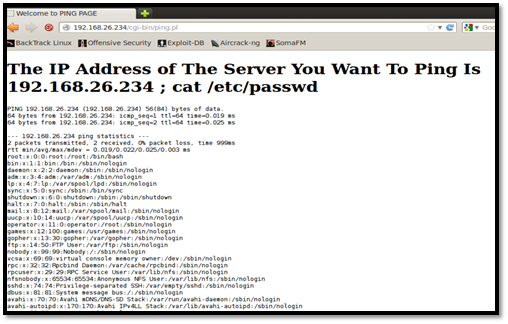
The command injection technique was used to dump the user database file on the web server. The following injection vector was used:
[plain]
192.168.26.234 ; cat/etc/passwd
[/plain]
Here, the ";" character is used to execute the cat /etc/passwd command, which is interpreted as a separate command and is executed by the ping.pl CGI script.
The vulnerability indicates that the CGI script allows attackers to perform command techniques, such as accessing /etc/password, which holds essential information about usernames and passwords of accounts created on the Apache server.
Prevention of command injection
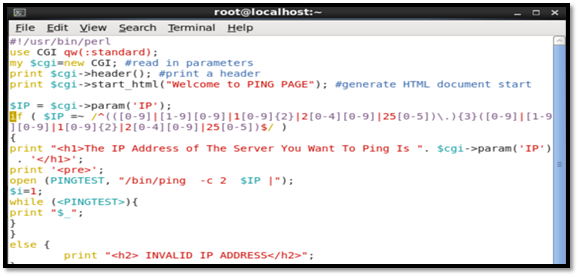
The CGI script is sanitized by allowing only valid IP address, through the following regular expression:
(([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5]).){3}([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])$
The updated script looks like the following:
[plain]
[root@localhost~]vim /var/www/cgi-bin/ping.pl
[/plain]
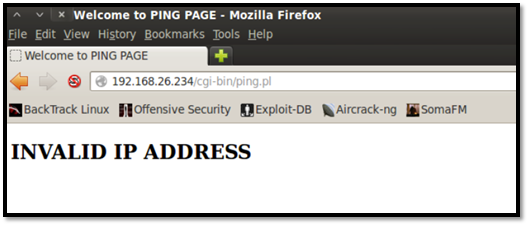
The output below shows that command injection on the CGI script was not successful after regular-expression-based filtering to the CGI parameter called $IP was address-implemented.

Get your guide to the top-paying certifications
With more than 448,000 U.S. cybersecurity job openings annually, get answers to all your cybersecurity salary questions with our free ebook!
Conclusion
This article shows an exploit on CGI script running on Apache server exploiting its vulnerabilities using command injection and also using a well-known exploit, known as Slowloris denial of service, and further identifying ways an attacker can use foot printing on Apache server through its banner, then preventing the same.










