Phishing and social engineering techniques 3.0
This is the third part of the phishing and social engineering techniques series. In the first article we have discussed what phishing is and what the different types of phishing are and we made a demo of phishing attacks using email-spoofing method to convince our victims to click to our links and finally we had an overview about social engineering toolkit.
Please check out the earlier installments of this series to get all benefits.

What should you learn next?
In that last part of phishing and social engineering techniques, we discussed in detail the social engineering toolkit configuration which allows us to customize according to the attack scenario. So being familiar with the configuration options will give you a view about the full features of SET to use these features to launch attack against our victims to convince them to provide the attacker all information that the attacker needs for further attack.
Today we are going to talk about different type of attack vectors that social engineering toolkit support that a pen-tester could use to deceive their victims to get control over them.

For the people that don't know what is social engineering, Social engineering definition according to Wikipedia Social engineering definition according to Wikipedia
There are tons of phishing and social engineering techniques and tools as a consequence of we will discuss some of these techniques and tools.
Social engineer toolkit
The Social Engineer (SET) was created and written by David Kennedy (ReL1K). The Social Engineer (SET) is an open source python-driven tool, which focuses solely on attacking the weakest link in information security chain, which is the human element. The attacks built into the toolkit are designed to be targeted and focused attacks against a person or organization used during a penetration test.
The Social Engineer (SET) is included in the latest version of the most popular Linux distribution focused on security, Backtrack. It can also be downloaded through github using the following command:
git clone https://github.com/trustedsec/social-engineer-toolkit/
Social engineer toolkit usage
Social Engineer Toolkit (SET) is a menu driven based attack system which means it's not a command line tool; this decision had been taken because of how social engineer attacks occur where it requires multiple scenarios, options, and customizations.
To open Social Engineer Toolkit (SET) in Kali distribution, Go to Applications -> Kali Linux -> Exploitation Tools -> Social Engineering Tools ->se-toolkit
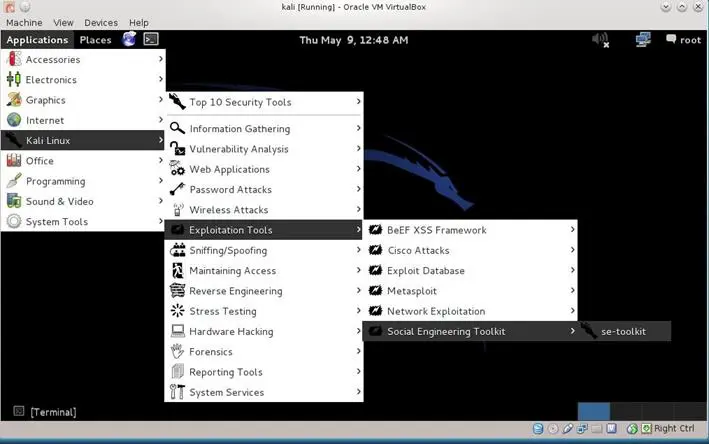
The SET will open in the terminal will look like the following screenshot (of course you have installed the latest version of SET).
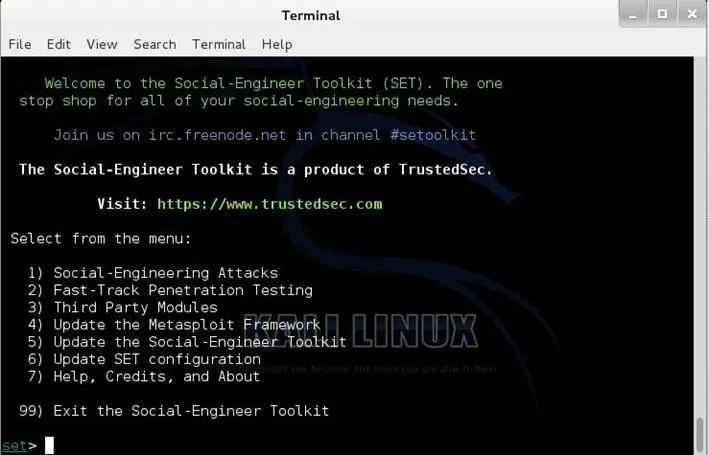
Now it's the time to step by the SET menu and take a quick and a brief walkthrough of most of these attack vectors.
- Social-Engineering Attacks
- Fast-Track Penetration Testing
- Third Party Modules
- Update the Metasploit Framework
- Update the Social-Engineer Toolkit
- Update SET configuration
- Help, Credits, and About
The most important item in this menu is Social Engineering Attacks which include all the attack vectors which we will focus on it. Most of these items in this menu are self-explanation like using fast track penetration testing framework, using third party modules, updating the Metasploit framework, updating the Social Engineer Toolkit (SET) itself and updating SET configuration because of that we will not dive through them.
Now let's select social engineering attacks from the menu. Once we choose this, we will get the sub menu list, which gives details about the further type of attack as shown below:
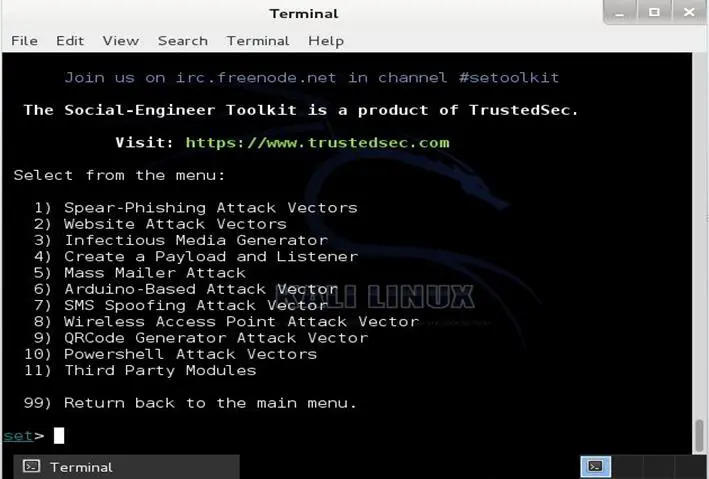
Now we will take an overview about each one of these items:
The spear-phishing attack vectors:
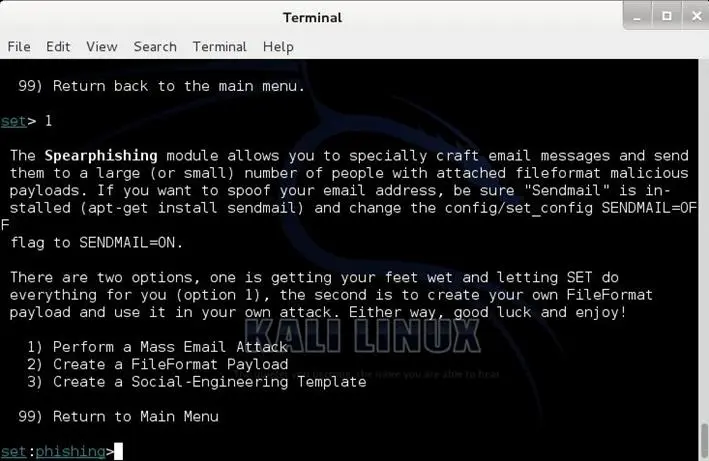
The Spear-phishing module allows you to specially craft email messages and send them to your targeted victims with attached FileFormatmalicious payloads for example (sending malicious PDF document which if the victim opens it, it will compromise the system). If you want to spoof your email address, be sure "Sendmail" is installed (apt-get install sendmail) and change the config/set_config SENDMAIL=OFF flag to SENDMAIL=ON.
There are two options for the spear phishing attack:
1) Perform a Mass Email Attack
2) Create a FileFormat Payload
3) Create a Social-Engineering Template
The first one is letting SET do everything for you (option 1), the second one is to create your own FileFormat payload and use it in your own attack.
The web attack vectors:
The web attack module is a unique way of utilizing multiple web-based attacks in order to compromise the intended victim. This module is used by performing phishing attacks against the victim in hopes they click the link. There is a wide-variety of attacks that can occur once they click on that link. We will dive into each one of the attacks later on.
Now let's select the web attack vectors from the menu. Once we choose the vector, we will get the sub menu list, which gives details about the further type of attack as shown below:
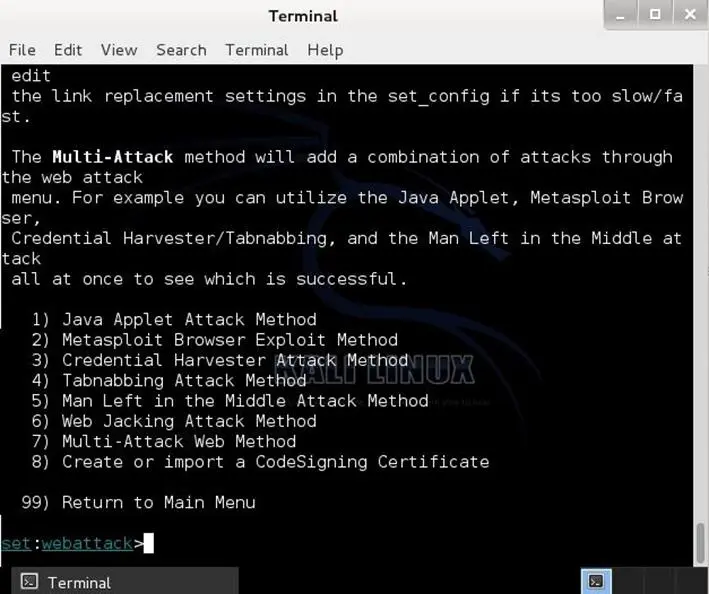
Infectious media generator:
The Infectious USB/CD/DVD module will create an autorun.inf file and a Metasploit payload. The payload and autorun file once burned or copied on a USB and when DVD/USB/CD is inserted in the victim's machine it will trigger an autorun feature (if autorun is enabled) and hopefully compromise the system. You can pick the attack vector you wish to use: fileformat bugs or a straight executable. There are the options for the Infectious Media Generator:
- File-Format Exploits
- Standard Metasploit Executable
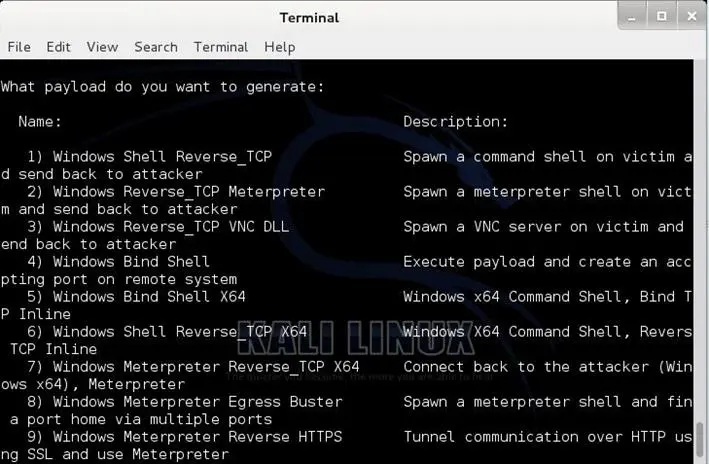
Create a payload and listener
The create payload and listener is the simple way to create a Metasploit payload, it will export the exe file for you and generate a listener. You would need to convince the victim to download the exe file and execute it to get the shell.
Mass mailer attack:
The mass mailer attack will allow you to send multiple emails to victims and customize the messages. There are two options on the mass e-mailer; the first would be to send an email to a single email address. The second option will allow you to import a list that has all recipient emails and it will send your message to as many people as you want within that list.
- E-Mail Attack Single Email Address
- E-Mail Attack Mass Mailer
Arduino-based attack vector:
Here is SET explanation for The Arduino-Based Attack Vector. This Attack Vector utilizes the Arduin-based device to program the device. You can leverage the Teensy's, which have onboard storage and can allow for remote code execution on the physical system. Since the devices are registered as USB Keyboard's it will bypass any autorun disabled or endpoint protection on the system. You will need to purchase the Teensy USB device; it's roughly $22 dollars. This attack vector will auto generate the code needed in order to deploy the payload on the system for you. This attack vector will create the .pde files necessary to import into Arduino (the IDE used for programming the Teensy). The attack vectors range from Powershell based downloaders, wscript attacks, and other methods. For more information on specifications and good tutorials visit: http://www.irongeek.com/i.php?page=security/programmable-hid-usb-keystroke-dongle To purchase a Teensy, visit: http://www.pjrc.com/store/teensy.html, This attack vector also attacks X10 based controllers, be sure to be leveraging X10 based communication devices in order for this to work.
SMS spoofing attack vector:
The SMS module allows you to send a crafted SMS messages to a person. You can spoof the SMS source. You can use a predefined template, create your own template or specify an arbitrary message. The main method for this would be to convince a user to click on a link in their browser and steal credentials or perform other attack vectors. You can send SMS to a single number or import a file that has a list of all numbers that it will send the SMS to them.
Wireless access point attack vector:
The Wireless Attack module will create a fake access point leveraging your wireless card and redirect all DNS queries to you. SET will create a wireless access point, dhcp server, and spoof DNS to redirect traffic to the attacker machine. You can run any SET attack vector you want, for example the attacker can run the Java Applet attack and when a victim that has been joined attacker's access point tries going to a website, the DNS spoof will redirect the victim to the attacker machine. For successful exploitation we need to install this software (AirBase-NG, AirMon-NG, DNSSpoof, and dhcpd3).
QRcode generator attack vector:
The QRCode Attack Vector will create a QRCode for you with whatever URL you want.When you have the QRCode Generated, select an additional attack vector within SET and deploy the QRCode to your victim. For example, generate a QRCode of the SET Java Applet and send the QRCode via a mailer.
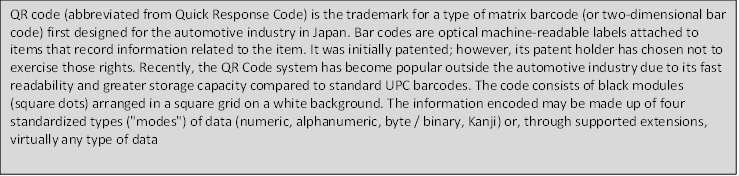
QRcode definition according to Wikipedia :
Powershell attack vectors:
The Powershell Attack Vector module allows you to create PowerShell specific attacks. These attacks will allow you to use PowerShell which is available by default in all operating systems Windows Vista and above. PowerShell provides a fruitful landscape for deploying payloads and performing functions that do not get triggered by preventative technologies.
- Powershell Alphanumeric Shellcode Injector
- Powershell Reverse Shell
- Powershell Bind Shell
- Powershell Dump SAM Database
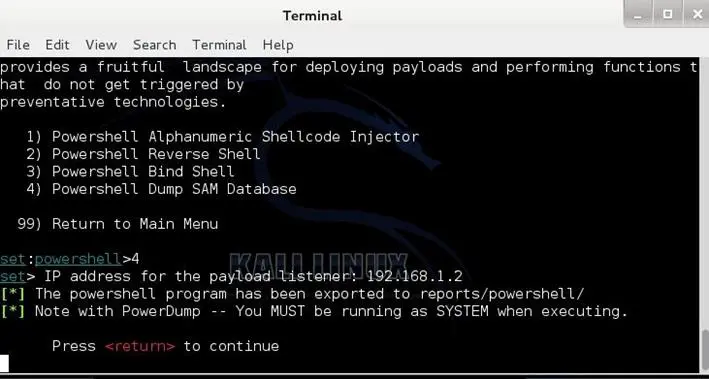
After the attacker chooses which shell will use, the shell will be exported to reports/powershell/ under SET directory. Now the attacker should coax the victim to run the code that located in the exported file or write a batch file to be easier for convincing his victim to run it.
Conclusion
Social engineering toolkit is a powerful tool that allows the penetration tester to use against his victims to convince his victims to provide him with the required information for further attack.
Free hour-long hacking course!
Learn how to hack and use AI in this free 1-hour course, led by Keatron Evans, 20-year cybersecurity veteran and VP of Portfolio Product and AI Strategy at Infosec!










